Tutorial for configuring Jumio with Azure Active Directory B2C
In this tutorial, learn to integrate Azure Active Directory B2C (Azure AD B2C) with Jumio, an ID verification service that enables real-time automated ID verification to help protect customer data.
Prerequisites
To get started, you'll need:
An Azure subscription
- If you don't have one, you can get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
Scenario description
The Jumio integration includes the following components:
- Azure AD B2C - The authorization server that verifies user credentials, also known as the identity provider (IdP)
- Jumio - Verifies user ID details
- Intermediate REST API - Use it to implement Azure AD B2C and Jumio integration
- Azure Blob storage - Use it to obtain custom UI files for the Azure AD B2C policies
The following architecture diagram shows the implementation.
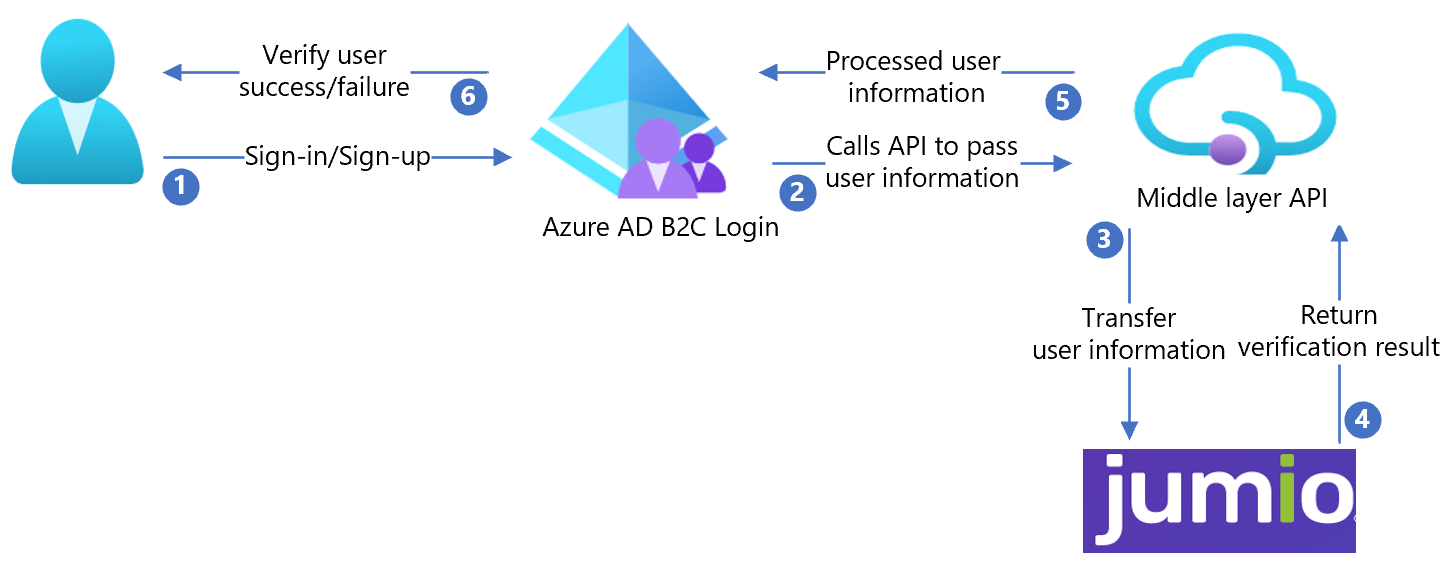
- The user signs in, or signs up, and creates an account. Azure AD B2C collects user attributes.
- Azure AD B2C calls the middle-layer API and passes the user attributes.
- The middle-layer API converts user attributes into a Jumio API format and sends the attributes to Jumio.
- Jumio processes the attributes, and returns results to the middle-layer API.
- The middle-layer API processes the results and sends relevant information to Azure AD B2C.
- Azure AD B2C receives the information. If the response fails, an error message appears. If the response succeeds, the user is authenticated and written into the directory.
Create a Jumio account
To create a Jumio account, go to the jumio.com Contact page.
Configure Azure AD B2C with Jumio
After you create a Jumio account, use it to configure Azure AD B2C.
Deploy the API
From samples/Jumio/API/Jumio.Api/, deploy the code to an Azure service. You can publish the code from Visual Studio.
Note
To configure Microsoft Entra ID, you'll need the deployed service URL.
Deploy the client certificate
A client certificate helps protect the Jumio API call.
Create a self-signed certificate by using the following PowerShell sample code:
$cert = New-SelfSignedCertificate -Type Custom -Subject "CN=Demo-SigningCertificate" -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.3") -KeyUsage DigitalSignature -KeyAlgorithm RSA -KeyLength 2048 -NotAfter (Get-Date).AddYears(2) -CertStoreLocation "Cert:\CurrentUser\My" $cert.Thumbprint $pwdText = "Your password" $pwd = ConvertTo-SecureString -String $pwdText -Force -AsPlainText Export-PfxCertificate -Cert $Cert -FilePath "{your-local-path}\Demo-SigningCertificate.pfx" -Password $pwd.The certificate is exported to the location specified for
{your-local-path}.To import the certificate to Azure App Service, see Upload a private certificate.
Create a signing/encryption key
Create a random string with a length greater than 64 characters (letters and numbers only).
For example:
C9CB44D98642A7062A0D39B94B6CDC1E54276F2E7CFFBF44288CEE73C08A8A65Use the following PowerShell script to create the string:
-join ((0x30..0x39) + ( 0x41..0x5A) + ( 0x61..0x7A) + ( 65..90 ) | Get-Random -Count 64 | % {[char]$_})
Configure the API
You can configure application settings in Azure App Service without checking them into a repository. You'll need to provide the following settings to the REST API:
| Application settings | Source | Notes |
|---|---|---|
| JumioSettings:AuthUsername | Jumio account configuration | N/A |
| JumioSettings:AuthPassword | Jumio account configuration | N/A |
| AppSettings:SigningCertThumbprint | The created self-signed certificate thumbprint | N/A |
| AppSettings:IdTokenSigningKey | Signing key created using PowerShell | N/A |
| AppSettings:IdTokenEncryptionKey | Encryption key created using PowerShell | N/A |
| AppSettings:IdTokenIssuer | Issuer for the JWT token (a GUID value is preferred) | N/A |
| AppSettings:IdTokenAudience | Audience for the JWT token (a GUID value is preferred) | N/A |
| AppSettings:BaseRedirectUrl | Azure AD B2C policy base URL | https://{your-tenant-name}.b2clogin.com/{your-application-id} |
| WEBSITE_LOAD_CERTIFICATES | The created self-signed certificate thumbprint | N/A |
Deploy the UI
- Set up a blob storage container in your storage account.
- Store the UI files from the /samples/Jumio/UI/ in your blob container.
Update UI files
- In the UI files, go to /samples/Jumio/UI/ocean_blue/.
- Open each HTML file.
- Find and replace
{your-ui-blob-container-url}with your blob container URL. - Find and replace
{your-intermediate-api-url}with the intermediate API app service URL.
Note
We recommend you add consent notification on the attribute collection page. Notify users the information goes to third-party services for identity verification.
Configure the Azure AD B2C policy
- Go to the Azure AD B2C policy in /samples/Jumio/Policies/.
- Use the instructions in Custom policy starter pack to download the LocalAccounts starter pack.
- Configure the policy for the Azure AD B2C tenant.
Note
Update policies to relate to your tenant.
Test the user flow
- Open the Azure AD B2C tenant.
- Under Policies, select Identity Experience Framework.
- Select your created SignUpSignIn.
- Select Run user flow.
- For Application, select the registered app (example is JWT).
- For Reply URL, select the redirect URL.
- Select Run user flow.
- Complete the sign-up flow.
- Create an account.
- After the user attribute is created, Jumio is called.
Tip
If the flow is incomplete, confirm the user is, or isn't, saved in the directory.