Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
In this tutorial, learn how to integrate Azure Active Directory B2C (Azure AD B2C) with Onfido, a document ID and facial biometrics verification app. Use it to meet Know Your Customer and identity requirements. Onfido uses artificial intelligence (AI) technology that verifies identity by matching a photo ID with facial biometrics. The solution connects a digital identity to a person, provides a reliable onboarding experience, and helps reduce fraud.
In this tutorial, you'll enable the Onfido service to verify identity in the sign-up, or sign-in, flow. Onfido results inform decisions about which products or services the user accesses.
Prerequisites
To get started, you'll need:
An Azure subscription
- If you don't have on, you can get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
- An Onfido trial account
- Go to onfido.com Contact us and fill out the form
Scenario description
The Onfido integration includes the following components:
- Azure AD B2C tenant – The authorization server that verifies user credentials based on custom policies defined in the tenant. It's also known as the identity provider (IdP). It hosts the Onfido client app, which collects the user documents and transmits them to the Onfido API service.
- Onfido client – A configurable, JavaScript client document-collection utility deployed in webpages. It checks details such as document size and quality.
- Intermediate REST API – Provides endpoints for the Azure AD B2C tenant to communicate with the Onfido API service. It handles data processing and adheres to security requirements of both.
- Onfido API service – The back-end service, which saves and verifies user documents.
The following architecture diagram shows the implementation.
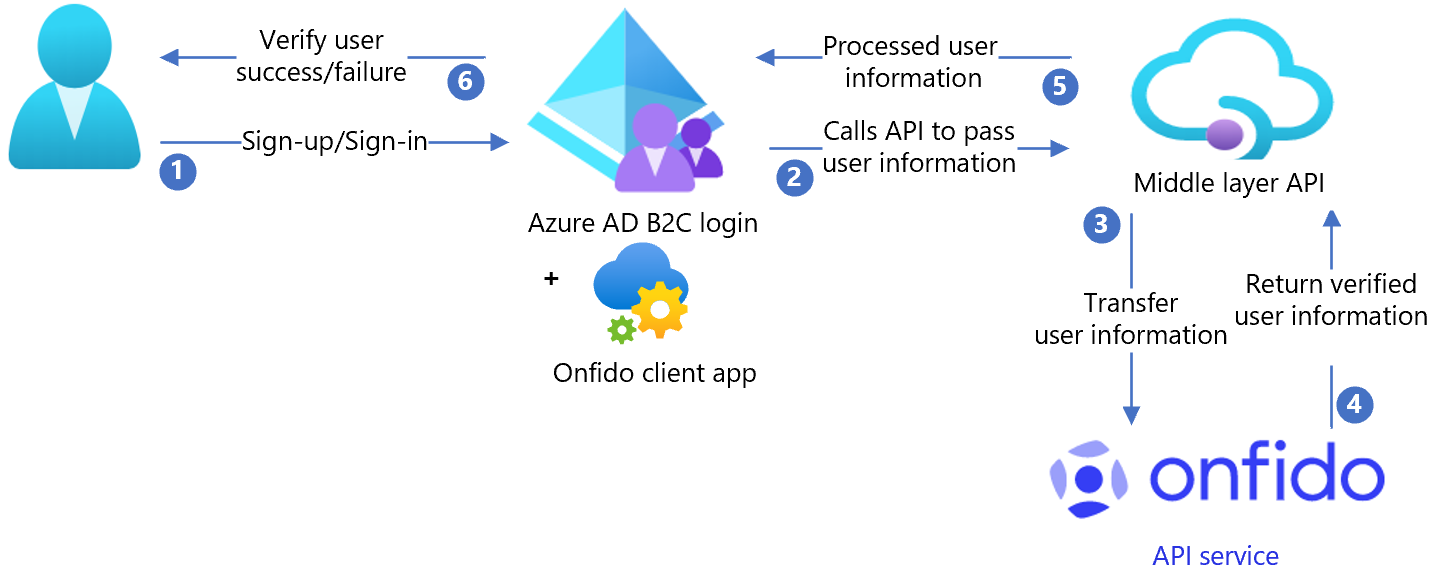
- User signs up to create a new account and enters attributes. Azure AD B2C collects the attributes. Onfido client app hosted in Azure AD B2C checks for the user information.
- Azure AD B2C calls the middle layer API and passes the attributes.
- Middle layer API collects attributes and converts them to an Onfido API format.
- Onfido processes attributes to validate user identification and sends result to the middle layer API.
- Middle layer API processes the results and sends relevant information to Azure AD B2C, in JavaScript Object Notation (JSON) format.
- Azure AD B2C receives the information. If the response fails, an error message appears. If the response succeeds, the user is authenticated and written into the directory.
Create an Onfido account
- Create an Onfido account: go to onfido.com Contact us and fill out the form.
- Create an API key: go to Get started (API v3.5).
Note
You'll need the key later.
Onfido documentation
Live keys are billable, however, you can use the sandbox keys for testing. Go to onfido.com for, Sandbox and live differences. The sandbox keys produce the same result structure as live keys, however, results are predetermined. Documents aren't processed or saved.
For more Onfido documentation, see:
Configure Azure AD B2C with Onfido
Deploy the API
- Deploy the API code to an Azure service. Go to samples/OnFido-Combined/API/Onfido.Api/. You can publish the code from Visual Studio.
- Set up cross-origin resource sharing (CORS).
- Add Allowed Origin as
https://{your_tenant_name}.b2clogin.com.
Note
You'll need the deployed service URL to configure Microsoft Entra ID.
Adding sensitive configuration settings
Configure app settings in the Azure App service without checking them into a repository.
REST API settings:
- Application setting name: OnfidoSettings:AuthToken
- Source: Onfido Account
Deploy the UI
Configure your storage location
- In the Azure portal, create a container.
- Store the UI files in /samples/OnFido-Combined/UI, in your blob container.
- Allow CORS access to the storage container you created: Go to Settings >Allowed Origin.
- Enter
https://{your_tenant_name}.b2clogin.com. - Replace your tenant name with your Azure AD B2C tenant name, using lower-case letters. For example,
https://fabrikam.b2clogin.com. - For Allowed Methods, select
GETandPUT. - Select Save.
Update UI files
- In the UI files, go to samples/OnFido-Combined/UI/ocean_blue.
- Open each html file.
- Find
{your-ui-blob-container-url}, and replace it with your UI ocean_blue, dist, and assets folder URLs. - Find
{your-intermediate-api-url}, and replace it with the intermediate API app service URL.
Upload your files
- Store the UI folder files in your blob container.
- Use Azure Storage Explorer to manage Azure managed disks and access permissions.
Configure Azure AD B2C
Replace the configuration values
In /samples/OnFido-Combined/Policies, find the following placeholders and replace them with the corresponding values from your instance.
| Placeholder | Replace with value | Example |
|---|---|---|
| {your_tenant_name} | Your tenant short name | "your tenant" from yourtenant.onmicrosoft.com |
| {your_tenantID} | Your Azure AD B2C TenantID | aaaabbbb-0000-cccc-1111-dddd2222eeee |
| {your_tenant_IdentityExperienceFramework_appid} | IdentityExperienceFramework app App ID configured in your Azure AD B2C tenant | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {your_tenant_ ProxyIdentityExperienceFramework_appid} | ProxyIdentityExperienceFramework app App ID configured in your Azure AD B2C tenant | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {your_tenant_extensions_appid} | Your tenant storage application App ID | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {your_tenant_extensions_app_objectid} | Your tenant storage application Object ID | aaaabbbb-0000-cccc-1111-dddd2222eeee |
| {your_app_insights_instrumentation_key} | Your app insights instance* instrumentation key | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {your_ui_file_base_url} | Location URL of your UI folders ocean_blue, dist, and assets | https://yourstorage.blob.core.windows.net/UI/ |
| {your_app_service_URL} | The app service URL you set up | https://yourapp.azurewebsites.net |
*App insights can be in a different tenant. This step is optional. Remove the corresponding TechnicalProfiles and OrchestrationSteps, if they're not needed.
Configure Azure AD B2C policy
See, Custom policy starter pack for instructions to set up your Azure AD B2C tenant and configure policies. Custom policies are a set of XML files you upload to your Azure AD B2C tenant to define technical profiles and user journeys.
Note
We recommend you add consent notification on the attribute collection page. Notify users that information goes to third-party services for identity verification.
Test the user flow
- Open the Azure AD B2C tenant.
- Under Policies select Identity Experience Framework.
- Select your previously created SignUpSignIn.
- Select Run user flow.
- For Application, select the registered app (example is JWT).
- For Reply URL, select the redirect URL.
- Select Run user flow.
- Complete the sign-up flow.
- Create an account.
- When the user attribute is created, Onfido is called during the flow.
Note
If the flow is incomplete, confirm the user is saved in the directory.