Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
Learn to integrate Azure Active Directory B2C (Azure AD B2C) with the Saviynt Security Manager platform, which has visibility, security, and governance. Saviynt incorporates application risk and governance, infrastructure management, privileged account management, and customer risk analysis.
Learn more: Saviynt for Azure AD B2C
Use the following instructions to set up access control delegated administration for Azure AD B2C users. Saviynt determines if a user is authorized to manage Azure AD B2C users with:
- Feature level security to determine if users can perform an operation
- For example, create user, update user, reset user password, and so on
- Field level security to determine if users can read/write user attributes during user management operations
- For example, a Help Desk agent can update a phone number; other attributes are read-only
- Data level security to determine if users can perform an operation on another user
- For example, a Help Desk administrator for the United Kingdom region manages UK users
Prerequisites
To get started, you need:
An Azure subscription
- If you don't have on, get an Azure free account
An Azure AD B2C tenant linked to your Azure subscription
Go to saviynt.com Contact Us to request a demo
Scenario description
The Saviynt integration includes the following components:
- Azure AD B2C – identity as a service for custom control of customer sign-up, sign-in, and profile management
- Saviynt for Azure AD B2C – identity governance for delegated administration of user life-cycle management and access governance
- Microsoft Graph API – interface for Saviynt to manage Azure AD B2C users and their access
The following architecture diagram illustrates the implementation.
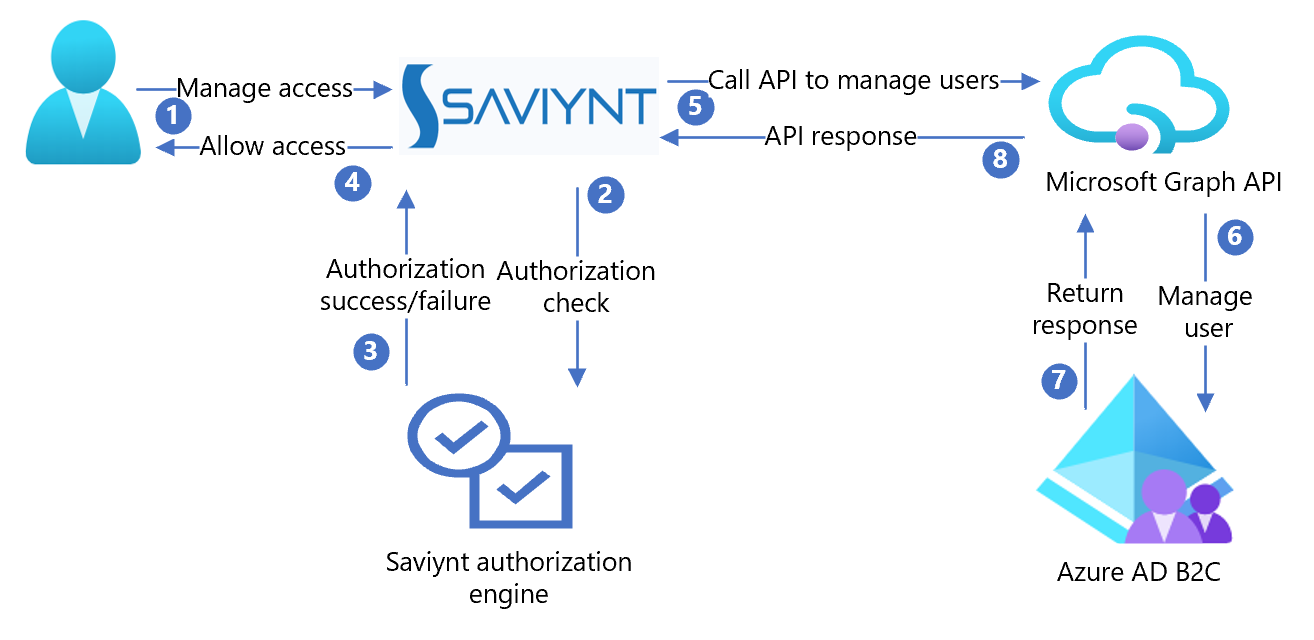
- A delegated administrator starts the Azure AD B2C user operation with Saviynt.
- Saviynt verifies the delegated administrator can perform the operation.
- Saviynt sends an authorization success or failure response.
- Saviynt allows the delegated administrator to perform the operation.
- Saviynt invokes Microsoft Graph API, with user attributes, to manage the user in Azure AD B2C.
- Microsoft Graph API creates, updates, or deletes the user in Azure AD B2C.
- Azure AD B2C sends a success or failure response.
- Microsoft Graph API returns the response to Saviynt.
Create a Saviynt account and create delegated policies
- Create a Saviynt account. To get started, go to saviynt.com Contact Us.
- Create delegated administration policies.
- Assign users the delegated administrator role.
Note
User administrator role will be required for a Service Principal Name (SPN) to integrate with Saviynt EIC system.
Configure Azure AD B2C with Saviynt
Use the following instructions to create an application, delete users, and more.
Create a Microsoft Entra application for Saviynt
For the following instructions, use the directory with the Azure AD B2C tenant.
Sign in to the Azure portal.
In the portal toolbar, select Directories + subscriptions.
On the Portal settings, Directories + subscriptions page, in the Directory name list, find your Azure AD B2C directory.
Select Switch.
In the Azure portal, search and select Azure AD B2C.
Select App registrations > New registration.
Enter an application name. For example, Saviynt.
Select Create.
Go to API Permissions.
Select + Add a permission.
The Request API permissions page appears.
Select Microsoft APIs tab.
Select Microsoft Graph as commonly used Microsoft APIs.
Go to the next page.
Select Application permissions.
Select Directory.
Select the Directory.Read.All and Directory.ReadWrite.All checkboxes.
Select Add Permissions.
Review the permissions.
Select Grant admin consent for Default Directory.
Select Save.
Go to Certificates and Secrets.
Select + Add Client Secret.
Enter the client secret description.
Select the expiry option.
Select Add.
The Secret Key appears in the Client Secret section. Save the Client Secret to use later.
Go to Overview.
Copy the Client ID and Tenant ID.
Save the Tenant ID, Client ID, and Client Secret to complete the setup.
Enable Saviynt to delete users
Enable Saviynt to perform user delete operations in Azure AD B2C.
Learn more: Application and service principal objects in Microsoft Entra ID
- Install the latest version of the Microsoft Graph PowerShell module on a Windows workstation or server.
For more information, see Microsoft Graph PowerShell documentation.
- Connect to the PowerShell module and execute the following commands:
Connect-MgGraph #Enter Admin credentials of the Azure portal
$webApp = Get-MgServicePrincipal –AppPrincipalId “<ClientId of Azure AD Application>”
New-MgDirectoryRoleMemberByRef -RoleName "Company Administrator" -RoleMemberType ServicePrincipal -RoleMemberObjectId $webApp.ObjectId
Test the solution
Browse to your Saviynt application tenant and test user life-cycle management and access governance use cases.