Using Application Gateway WAF to protect your applications
Add Web Application Firewall (WAF) protection for apps published with Microsoft Entra application proxy.
To learn more about Web Application Firewall, see What is Azure Web Application Firewall on Azure Application Gateway?.
Deployment steps
This article provides the steps to securely expose a web application on the Internet using Microsoft Entra application proxy with Azure WAF on Application Gateway.
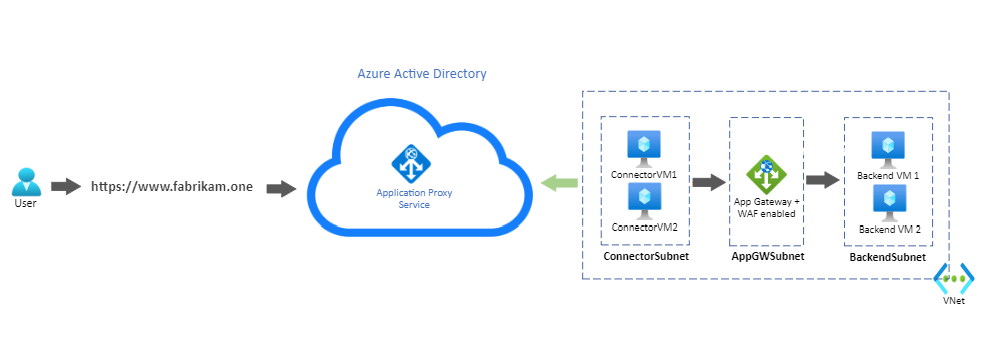
Configure Azure Application Gateway to send traffic to your internal application
Some steps of the Application Gateway configuration are omitted in this article. For a detailed guide on creating and configuring an Application Gateway, see Quickstart: Direct web traffic with Azure Application Gateway - Microsoft Entra admin center.
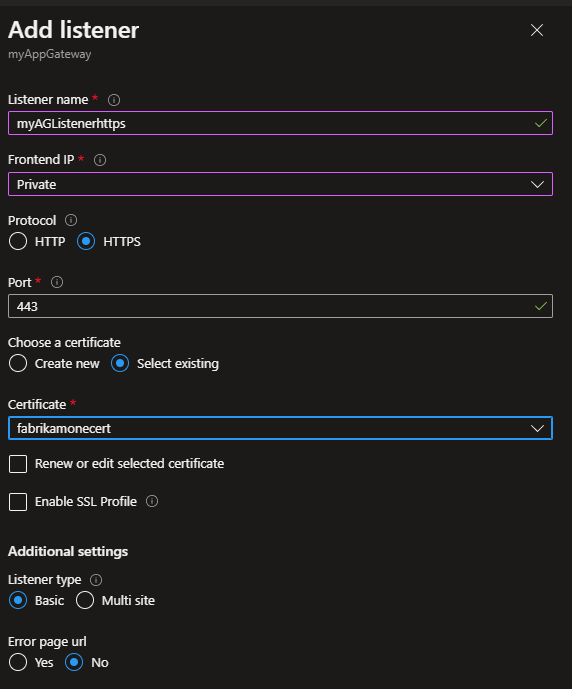
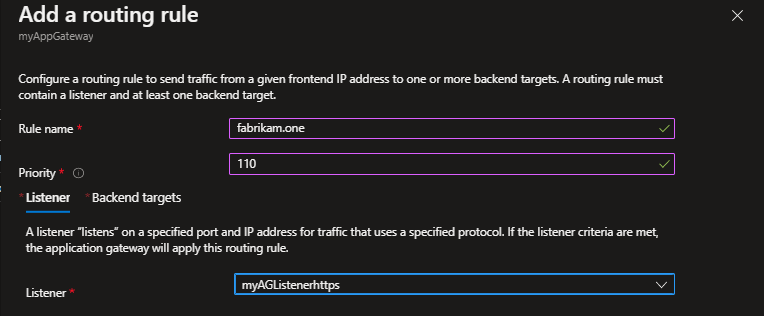
1. Create a private-facing HTTPS listener
Create a listener so users can access the web application privately when connected to the corporate network.
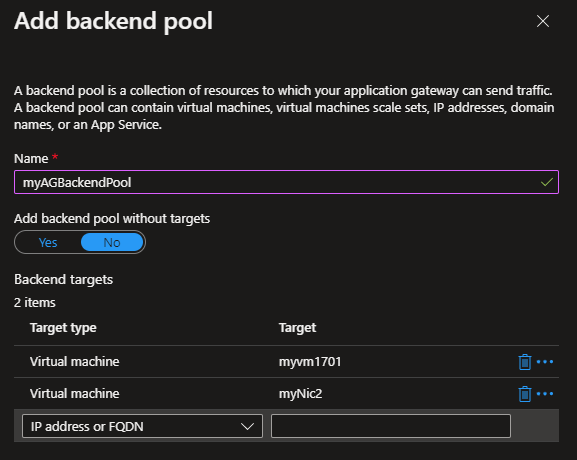
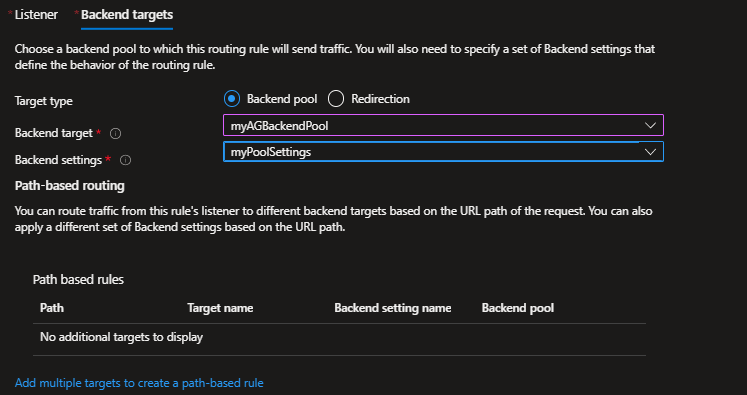
2. Create a backend pool with the web servers
In this example, the backend servers have Internet Information Services (IIS) installed.
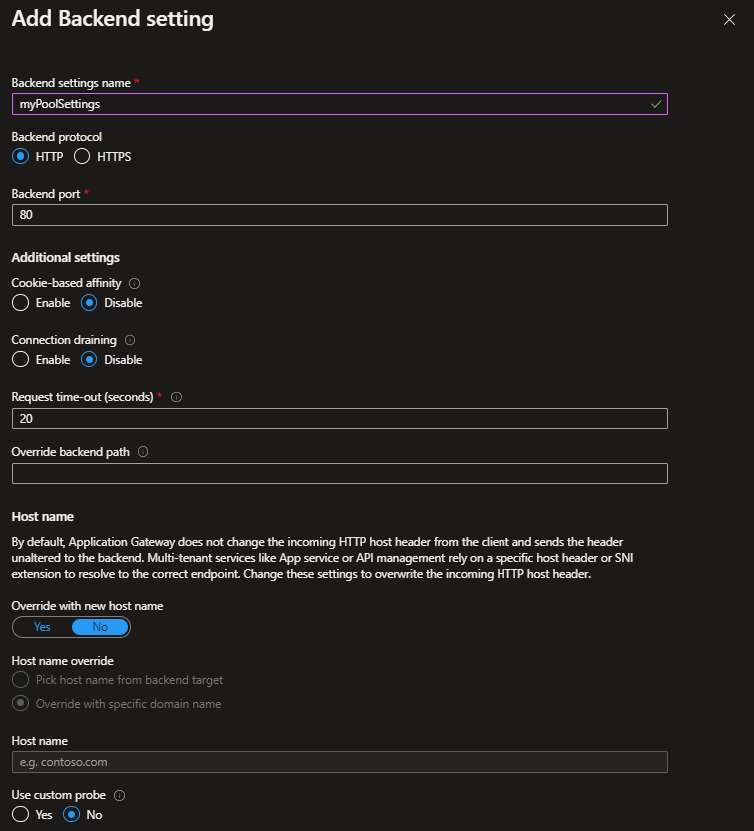
3. Create a backend setting
A backend setting determines how requests reach the backend pool servers.
4. Create a routing rule that ties the listener, the backend pool, and the backend setting created in the previous steps
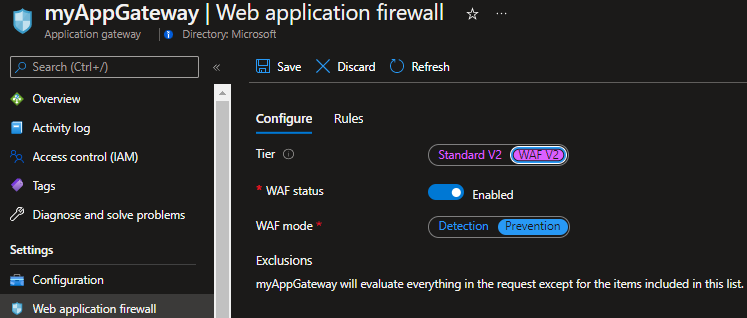
5. Enable the WAF in the Application Gateway and set it to Prevention mode
Configure your application to be remotely accessed through application proxy in Microsoft Entra ID
Both connector VMs, the Application Gateway, and the backend servers are deployed in the same virtual network in Azure. The setup also applies to applications and connectors deployed on-premises.
For a detailed guide on how to add your application to application proxy in Microsoft Entra ID, see Tutorial: Add an on-premises application for remote access through application proxy in Microsoft Entra ID. For more information about performance considerations concerning the private network connectors, see Optimize traffic flow with Microsoft Entra application proxy.
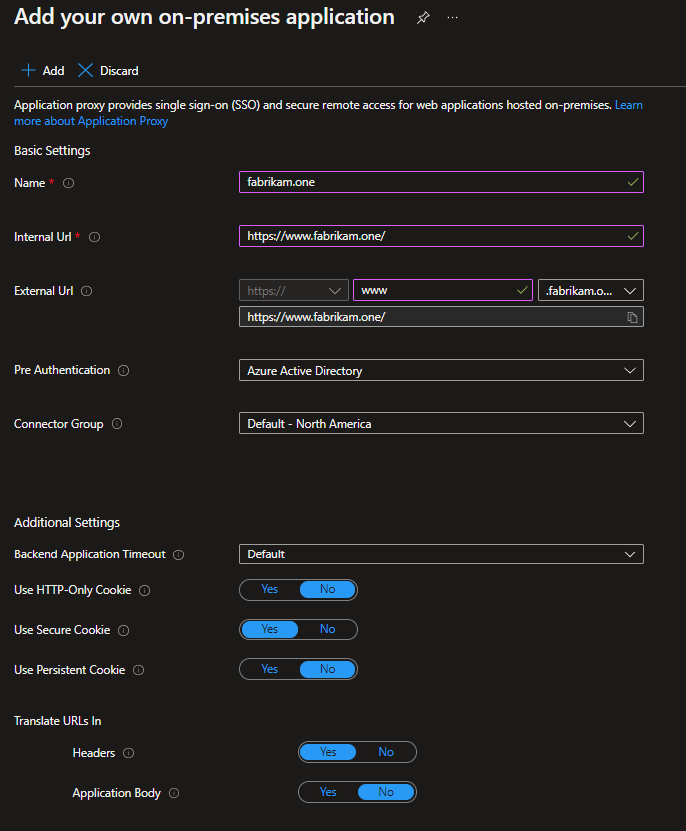
In this example, the same URL was configured as the internal and external URL. Remote clients access the application over the Internet on port 443, through the application proxy. A client connected to the corporate network accesses the application privately. Access is through the Application Gateway directly on port 443. For a detailed step on configuring custom domains in application proxy, see Configure custom domains with Microsoft Entra application proxy.
An Azure Private Domain Name System (DNS) zone is created with an A record. The A record points www.fabrikam.one to the private frontend IP address of the Application Gateway. The record ensures the connector VMs send requests to the Application Gateway.
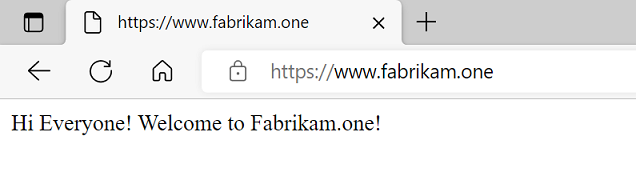
Test the application
After adding a user for testing, you can test the application by accessing https://www.fabrikam.one. The user is prompted to authenticate in Microsoft Entra ID, and upon successful authentication, accesses the application.
Simulate an attack
To test if the WAF is blocking malicious requests, you can simulate an attack using a basic SQL injection signature. For example, "https://www.fabrikam.one/api/sqlquery?query=x%22%20or%201%3D1%20--".
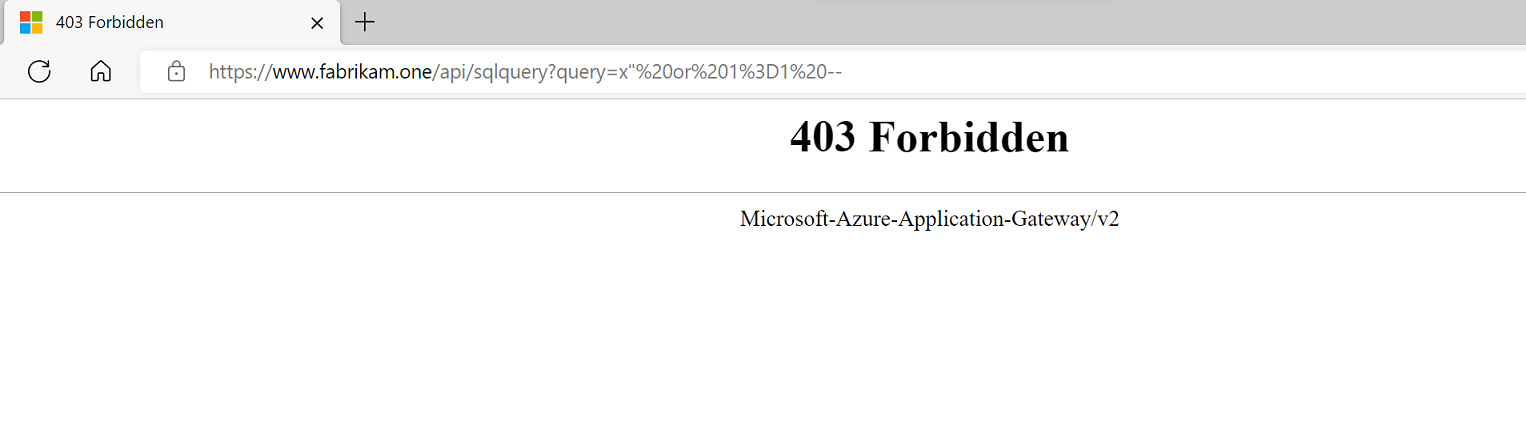
An HTTP 403 response confirms that WAF blocked the request.
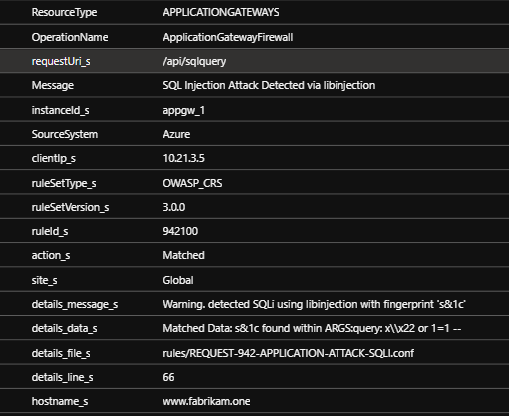
The Application Gateway Firewall logs provide more details about the request and why WAF is blocking it.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for