Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra ID must contain all the data (attributes) required to create a user profile when provisioning user accounts from Microsoft Entra ID to a line of business (LOB), SaaS app, or on-premises application. You can use directory extensions to extend the schema in Microsoft Entra ID with your own attributes. This feature enables you to build LOB apps by consuming attributes that you continue to manage on-premises, provision users from Active Directory to Microsoft Entra ID or SaaS apps, and use extension attributes in Microsoft Entra ID and Microsoft Entra ID Governance features such as dynamic membership groups or Group provisioning to Active Directory.
For more information on directory extensions, see Using directory extension attributes in claims, Microsoft Entra Connect Sync: directory extensions, and Syncing extension attributes for Microsoft Entra application provisioning.
You can see the available attributes by using Microsoft Graph Explorer.
Note
In order to discover new Active Directory extension attributes, the provisioning agent needs to be restarted. You should restart the agent after the directory extensions have been created. For Microsoft Entra extension attributes, the agent doesn't need to be restarted.
Syncing directory extensions for Microsoft Entra Cloud Sync
You can use directory extensions to extend the synchronization schema directory definition in Microsoft Entra ID with your own attributes.
Important
Directory extension for Microsoft Entra Cloud Sync is only supported for applications with the identifier URI API://<tenantId>/CloudSyncCustomExtensionsApp and the Tenant Schema Extension App created by Microsoft Entra Connect.
Create application and service principal for directory extension
You need to create an application with the identifier URI API://<tenantId>/CloudSyncCustomExtensionsApp if it doesn't exist and create a service principal for the application if it doesn't exist.
Check if application with the identifier URI
API://<tenantId>/CloudSyncCustomExtensionsAppexists:$tenantId = (Get-MgOrganization).Id Get-MgApplication -Filter "identifierUris/any(uri:uri eq 'API://$tenantId/CloudSyncCustomExtensionsApp')"For more information, see Get-MgApplication.
If the application doesn't exist, use the
$tenantIdvariable from previous step to create the application with identifier URIAPI://<tenantId>/CloudSyncCustomExtensionsApp:New-MgApplication -DisplayName "CloudSyncCustomExtensionsApp" -IdentifierUris "API://$tenantId/CloudSyncCustomExtensionsApp"For more information, see New-MgApplication.
Use the
$tenantIdvariable from previous step to check if the service principal exists for the application with identifier URIAPI://<tenantId>/CloudSyncCustomExtensionsApp:$appId = (Get-MgApplication -Filter "identifierUris/any(uri:uri eq 'API://$tenantId/CloudSyncCustomExtensionsApp')").AppId Get-MgServicePrincipal -Filter "AppId eq '$appId'"For more information, see Get-MgServicePrincipal.
If a service principal doesn't exist, use the
$tenantIdvariable from previous step to create a new service principal for the application with identifier URIAPI://<tenantId>/CloudSyncCustomExtensionsApp:New-MgServicePrincipal -AppId $appIdFor more information, see New-MgServicePrincipal.
Use the
$tenantIdvariable from previous step to create a directory extension in Microsoft Entra ID. For example, a new extension called 'GroupDN', of string type, for Group objects:$appObjId = (Get-MgApplication -Filter "identifierUris/any(uri:uri eq 'API://$tenantId/CloudSyncCustomExtensionsApp')").Id New-MgApplicationExtensionProperty -ApplicationId $appObjId -Name GroupDN -DataType String -TargetObjects Group
You can create directory extensions in Microsoft Entra ID in several different ways, as described in the following table:
| Method | Description | URL |
|---|---|---|
| MS Graph | Create extensions using Microsoft Graph | Create extensionProperty |
| PowerShell | Create extensions using PowerShell | New-MgApplicationExtensionProperty |
| Using cloud sync and Microsoft Entra Connect | Create extensions using Microsoft Entra Connect | Create an extension attribute using Microsoft Entra Connect |
| Customizing attributes to sync | Information on customizing, which attributes to synch | Customize which attributes to synchronize with Microsoft Entra ID |
Use attribute mapping to map Directory Extensions
If you extended Active Directory to include custom attributes, you can add these attributes and map them to users.
To discover and map attributes, select Add attribute mapping and the attributes become available in the drop-down under source attribute. Fill in the type of mapping you want and select Apply.
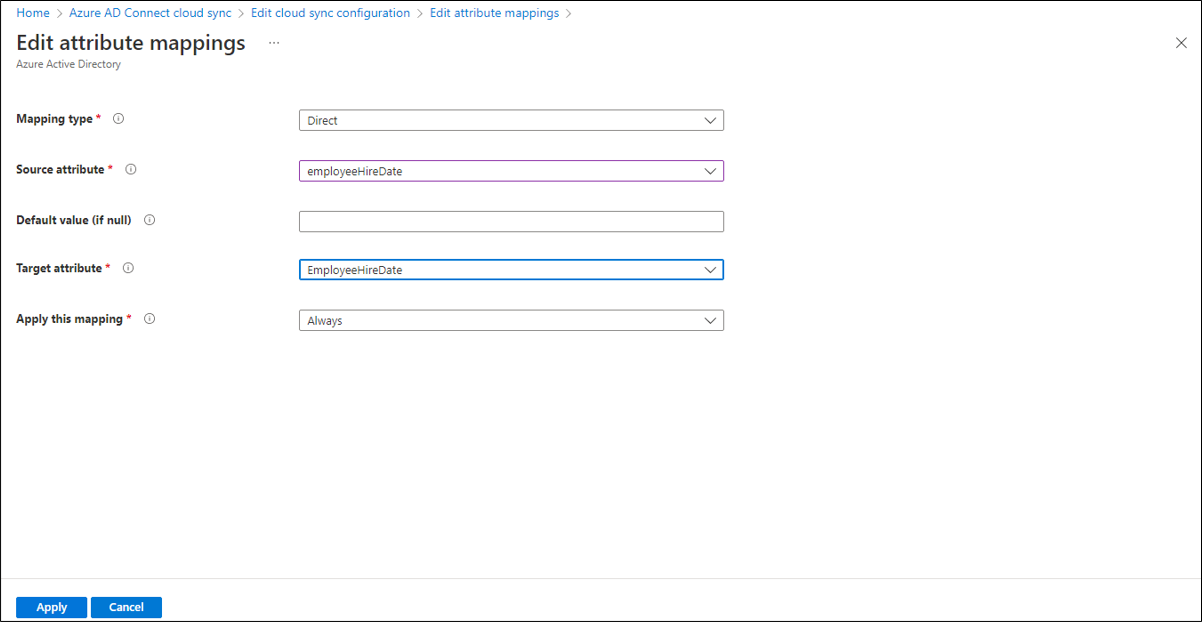
For information on new attributes that are added and updated in Microsoft Entra ID see the user resource type and consider subscribing to change notifications.
For more information on extension attributes, see Syncing extension attributes for Microsoft Entra Application Provisioning.