Migrate from a classic policy
This article shows an example of how to migrate a classic policy that requires Multifactor authentication for a cloud app.
Tip
As of the August 2023 Intune service release (2308), classic Conditional Access policies are no longer created for the Microsoft Defender for Endpoint connector. If your tenant has a classic Conditional Access policy that was previously created for integration with Microsoft Defender for Endpoint, it can be deleted.
Warning
Once disabled a classic policy can't be re-enabled.
Open a classic policy
Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
Browse to Protection > Conditional Access > Classic policies.

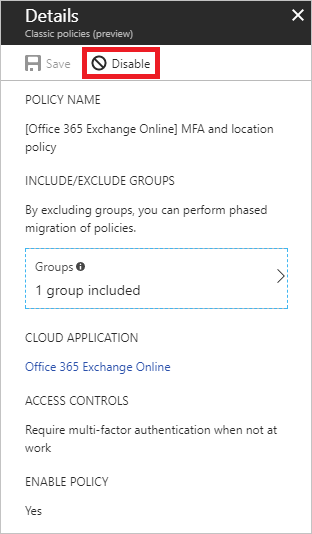
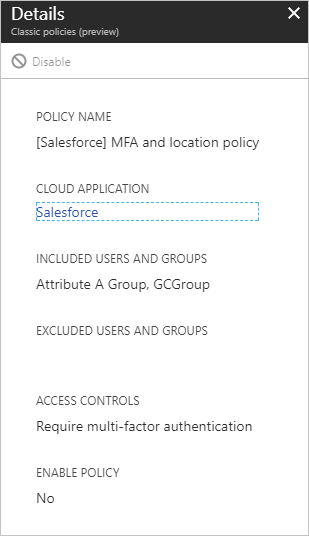
In the list of classic policies, select the policy you wish to migrate. Document the configuration settings so that you can re-create with a new Conditional Access policy.
For examples of common policies and their configuration, see the article Common Conditional Access policies.
Disable the classic policy
To disable your classic policy, select Disable in the Details view.
Warning
Once disabled a classic policy can't be re-enabled.