Block workload identity federation on managed identities using a policy
This article describes how to block the creation of federated identity credentials on user-assigned managed identities by using Azure Policy. By blocking the creation of federated identity credentials, you can block everyone from using workload identity federation to access Microsoft Entra protected resources. Azure Policy helps enforce certain business rules on your Azure resources and assess compliance of those resources.
The Not allowed resource types built-in policy can be used to block the creation of federated identity credentials on user-assigned managed identities.
Create a policy assignment
Tip
Steps in this article might vary slightly based on the portal you start from.
To create a policy assignment for the Not allowed resource types that blocks the creation of federated identity credentials in a subscription or resource group:
- Sign in to the Azure portal.
- Navigate to Policy in the Azure portal.
- Go to the Definitions pane.
- In the Search box, search for "Not allowed resource types" and select the Not allowed resource types policy in the list of returned items.
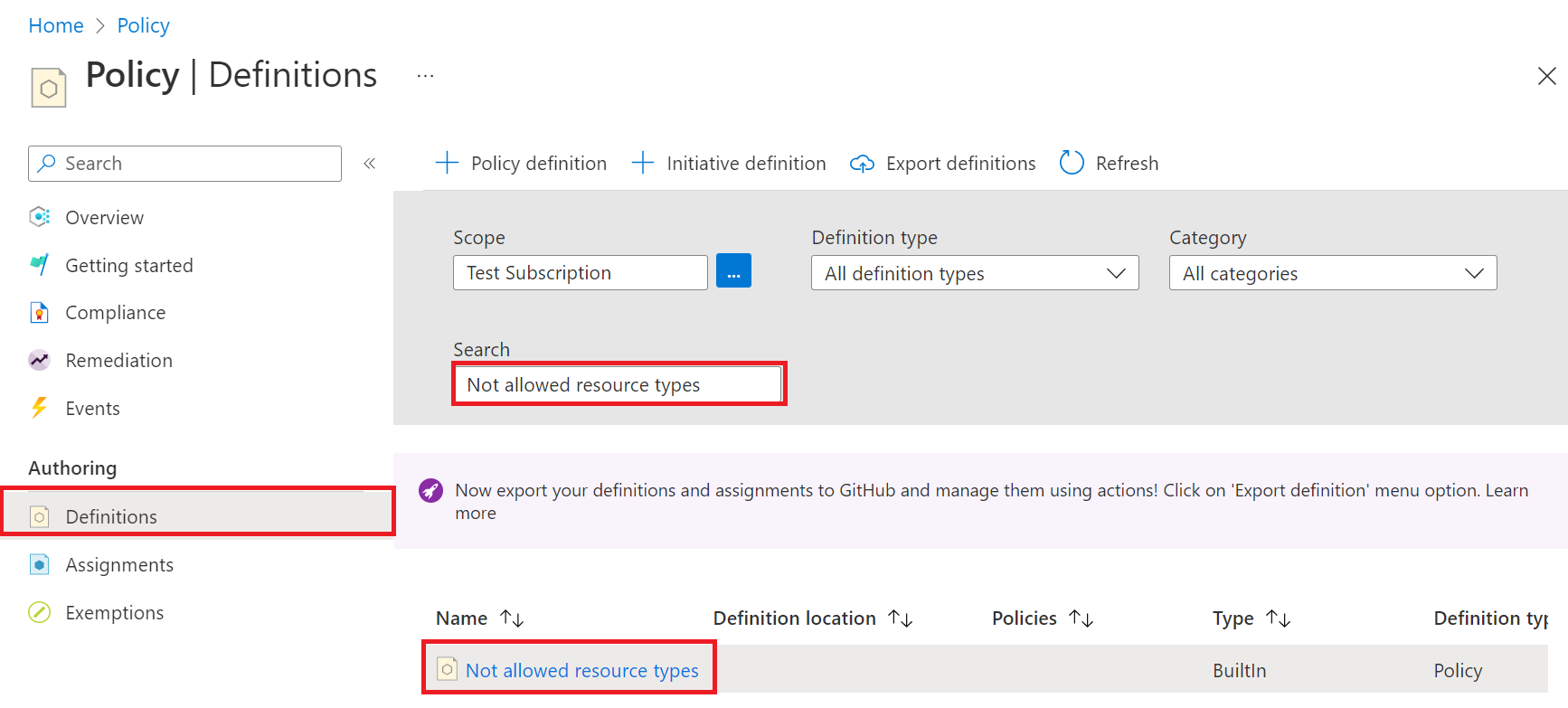
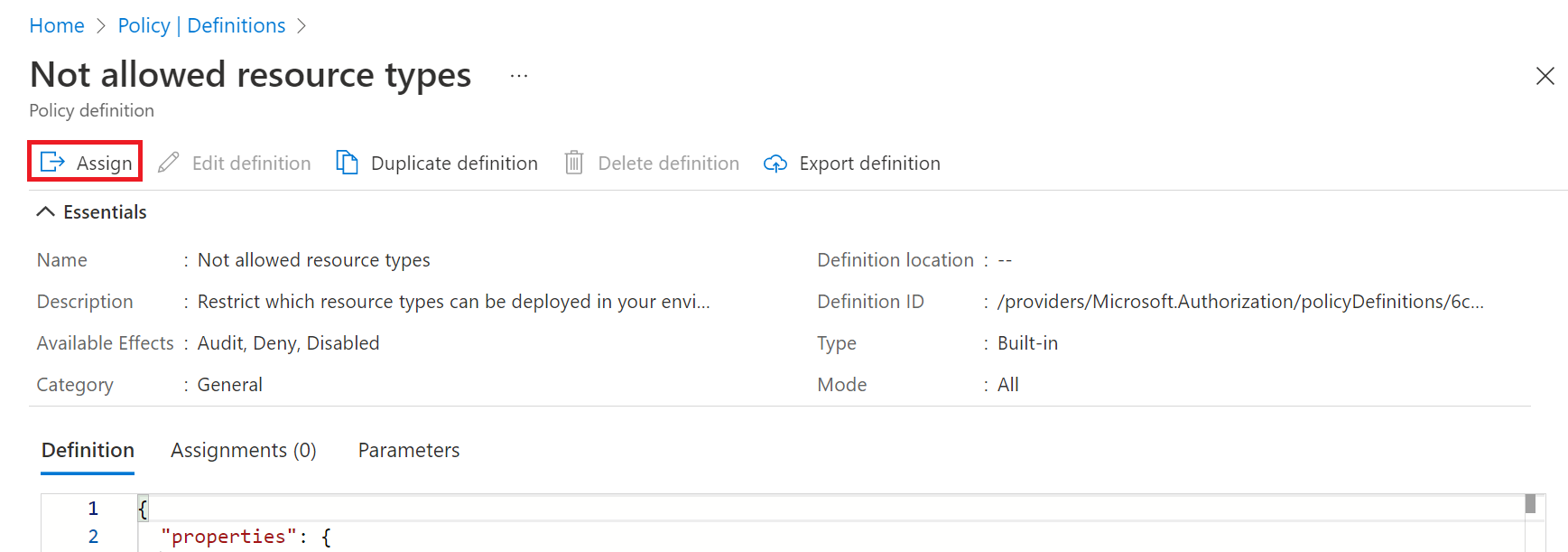
- After selecting the policy, you can now see the Definition tab.
- Click the Assign button to create an Assignment.
- In the Basics tab, fill out Scope by setting the Subscription and optionally set the Resource Group.
- In the Parameters tab, select userAssignedIdentities/federatedIdentityCredentials from the Not allowed resource types list. Select Review and create.
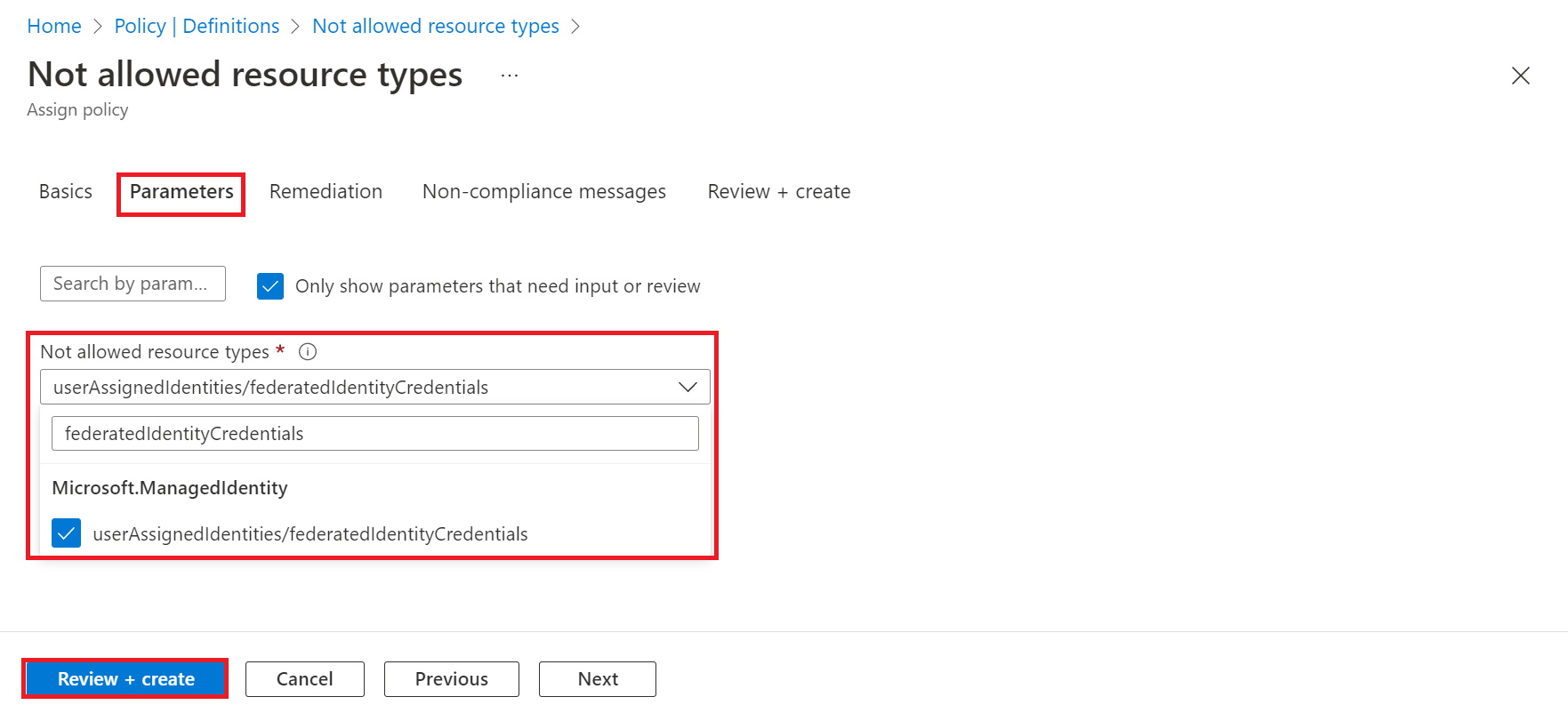
- Apply the Assignment by selecting Create.
- View your assignment in the Assignments tab next to Definition.
Next steps
Learn how to manage a federated identity credential on a user-assigned managed identity in Microsoft Entra ID.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for