Manage external access to resources with Conditional Access policies
Conditional Access interprets signals, enforces policies, and determines if a user is granted access to resources. In this article, learn about applying Conditional Access policies to external users. The article assumes you might not have access to entitlement management, a feature you can use with Conditional Access.
Learn more:
The following diagram illustrates signals to Conditional Access that trigger access processes.
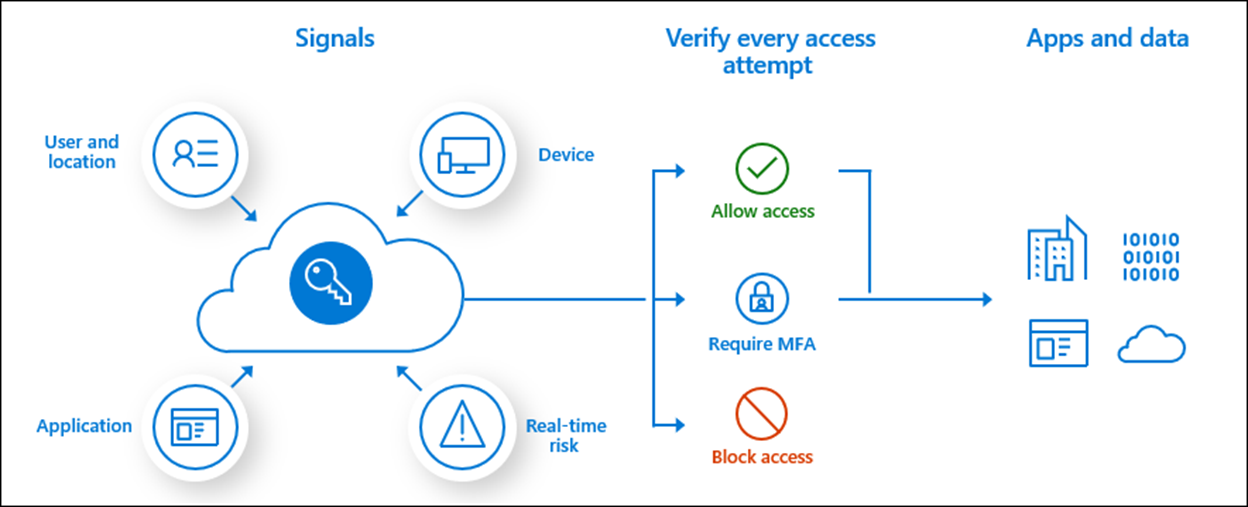
Before you begin
This article is number 7 in a series of 10 articles. We recommend you review the articles in order. Go to the Next steps section to see the entire series.
Align a security plan with Conditional Access policies
In the third article, in the set of 10 articles, there's guidance on creating a security plan. Use that plan to help create Conditional Access policies for external access. Part of the security plan includes:
- Grouped applications and resources for simplified access
- Sign-in requirements for external users
Important
Create internal and external user test accounts to test policies before applying them.
See article three, Create a security plan for external access to resources
Conditional Access policies for external access
The following sections are best practices for governing external access with Conditional Access policies.
Entitlement management or groups
If you can't use connected organizations in entitlement management, create a Microsoft Entra security group, or Microsoft 365 Group for partner organizations. Assign users from that partner to the group. You can use the groups in Conditional Access policies.
Learn more:
- What is entitlement management?
- Manage Microsoft Entra groups and group membership
- Overview of Microsoft 365 Groups for administrators
Conditional Access policy creation
Create as few Conditional Access policies as possible. For applications that have the same access requirements, add them to the same policy.
Conditional Access policies apply to a maximum of 250 applications. If more than 250 applications have the same access requirement, create duplicate policies. For instance, Policy A applies to apps 1-250, Policy B applies to apps 251-500, and so on.
Naming convention
Use a naming convention that clarifies policy purpose. External access examples are:
- ExternalAccess_actiontaken_AppGroup
- ExternalAccess_Block_FinanceApps
Allow external access to specific external users
There are scenarios when it's necessary to allow access for a small, specific group.
Before you begin, we recommend you create a security group, which contains external users who access resources. See, Quickstart: Create a group with members and view all groups and members in Microsoft Entra ID.
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Protection > Conditional Access.
- Select Create new policy.
- Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
- Under Assignments, select Users or workload identities.
- Under Include, select All guests and external users.
- Under Exclude, select Users and groups and choose your organization's emergency access or break-glass accounts and the external users security group.
- Under Target resources > Cloud apps, select the following options:
- Under Include, select All cloud apps
- Under Exclude, select applications you want to exclude.
- Under Access controls > Grant, select Block access, then select Select.
- Select Create to create to enable your policy.
Note
After administrators confirm the settings using report-only mode, they can move the Enable policy toggle from Report-only to On.
Learn more: Manage emergency access accounts in Microsoft Entra ID
Service provider access
Conditional Access policies for external users might interfere with service provider access, for example granular delegated administrate privileges.
Learn more: Introduction to granular delegated admin privileges (GDAP)
Conditional Access templates
Conditional Access templates are a convenient method to deploy new policies aligned with Microsoft recommendations. These templates provide protection aligned with commonly used policies across various customer types and locations.
Learn more: Conditional Access templates (Preview)
Next steps
Use the following series of articles to learn about securing external access to resources. We recommend you follow the listed order.
Determine your security posture for external access with Microsoft Entra ID
Discover the current state of external collaboration in your organization
Secure external access with groups in Microsoft Entra ID and Microsoft 365
Transition to governed collaboration with Microsoft Entra B2B collaboration
Manage external access with Microsoft Entra entitlement management
Manage external access to resources with Conditional Access policies (You're here)
Control external access to resources in Microsoft Entra ID with sensitivity labels
Convert local guest accounts to Microsoft Entra B2B guest accounts
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for