Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Legacy applications commonly use Header-based authentication. In this scenario, a user (or message originator) authenticates to an intermediary identity solution. The intermediary solution authenticates the user and propagates the required Hypertext Transfer Protocol (HTTP) headers to the destination web service. Microsoft Entra ID supports this pattern via its Application Proxy service, and integrations with other network controller solutions.
In our solution, Application Proxy provides remote access to the application, authenticates the user, and passes headers required by the application.
Use when
Remote users need to securely single sign-on (SSO) into to on-premises applications that require header-based authentication.
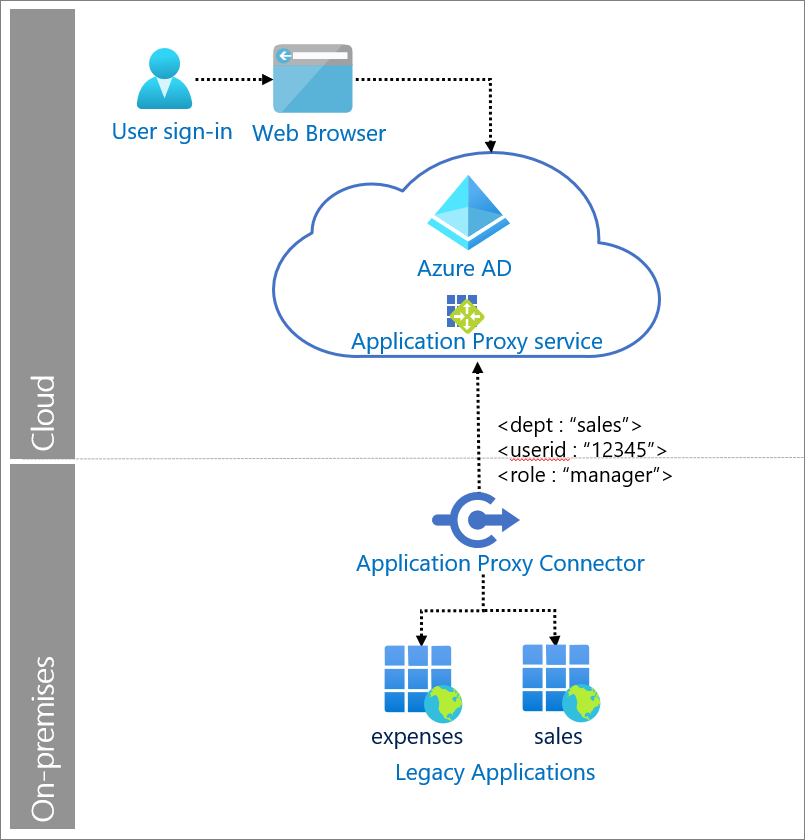
Components of system
User: Accesses legacy applications served by Application Proxy.
Web browser: The component that the user interacts with to access the external URL of the application.
Microsoft Entra ID: Authenticates the user.
Application Proxy service: Acts as reverse proxy to send request from the user to the on-premises application. It resides in Microsoft Entra ID and can also enforce any Conditional Access policies.
Private network connector: Installed on-premises on Windows servers to provide connectivity to the applications. It only uses outbound connections. Returns the response to Microsoft Entra ID.
Legacy applications: Applications that receive user requests from Application Proxy. The legacy application receives the required HTTP headers to set up a session and return a response.