Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article is the fourth in a series of articles that provide guidance for configuring and providing user lifecycle management in Microsoft Entra multitenant environments. The following articles in the series provide more information as described.
- Multitenant user management introduction is the first in the series.
- Multitenant user management scenarios describes three scenarios for which you can use multitenant user management features: end user-initiated, scripted, and automated.
- Common considerations for multitenant user management provides guidance for these considerations: cross-tenant synchronization, directory object, Microsoft Entra Conditional Access, additional access control, and Office 365.
The guidance helps to you achieve a consistent state of user lifecycle management. Lifecycle management includes provisioning, managing, and deprovisioning users across tenants using the available Azure tools that include Microsoft Entra B2B collaboration (B2B) and cross-tenant synchronization.
Microsoft recommends a single tenant wherever possible. If single tenancy doesn't work for your scenario, reference the following solutions that Microsoft customers have successfully implemented for these challenges:
- Automatic user lifecycle management and resource allocation across tenants
- Sharing on-premises apps across tenants
Automatic user lifecycle management and resource allocation across tenants
A customer acquires a competitor with whom they previously had close business relationships. The organizations want to maintain their corporate identities.
Current state
Currently, the organizations are synchronizing each other's users as mail contact objects so that they show in each other's directories. Each resource tenant has enabled mail contact objects for all users in the other tenant. Across tenants, no access to applications is possible.
Goals
The customer has the following goals.
- Every user appears in each organization's GAL.
- User account lifecycle changes in the home tenant automatically reflected in the resource tenant GAL.
- Attribute changes in home tenants (such as department, name, Simple Mail Transfer Protocol (SMTP) address) automatically reflected in resource tenant GAL and the home GAL.
- Users can access applications and resources in the resource tenant.
- Users can self-serve access requests to resources.
Solution architecture
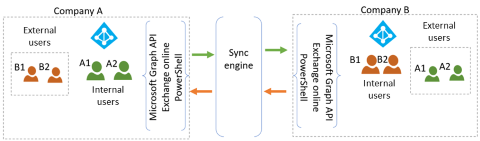
The organizations use a point-to-point architecture with a synchronization engine such as Microsoft Identity Manager (MIM). The following diagram illustrates an example of point-to-point architecture for this solution.
Each tenant admin performs the following steps to create the user objects.
- Ensure that their user database is up to date.
- Deploy and configure MIM.
- Address existing contact objects.
- Create external member user objects for the other tenant's internal member users.
- Synchronize user object attributes.
- Deploy and configure Entitlement Management access packages.
- Resources to be shared.
- Expiration and access review policies.
Sharing on-premises apps across tenants
A customer with multiple peer organizations needs to share on-premises applications from one of the tenants.
Current state
Peer organizations are synchronizing external users in a mesh topology, enabling resource allocation to cloud applications across tenants. The customer offers following functionality.
- Share applications in Microsoft Entra ID.
- Automated user lifecycle management in resource tenant on home tenant (reflecting add, modify, and delete).
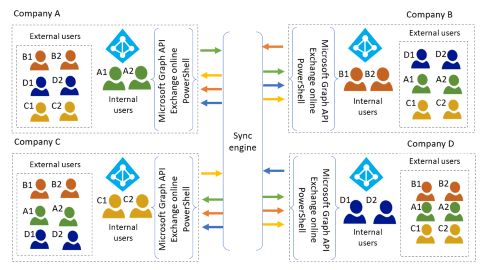
The following diagram illustrates this scenario, where only internal users in Company A access Company A's on-premises apps.
Goals
Along with the current functionality, they want to offer the following.
- Provide access to Company A's on-premises resources for the external users.
- Apps with Security Assertion Markup Language (SAML) authentication.
- Apps with Integrated Windows Authentication and Kerberos.
Solution architecture
Company A provides single sign-on (SSO) to on-premises apps for its own internal users using Azure Application Proxy as illustrated in the following diagram.
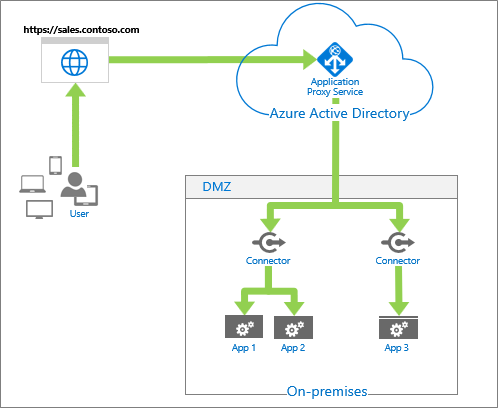
Diagram title: Azure Application Proxy architecture solution. On the top left, a box labeled `https://sales.constoso.com` contains a globe icon to represent a website. Below it, a group of icons represent the User and are connected by an arrow from the User to the website. On the top right, a cloud shape labeled Microsoft Entra ID contains an icon labeled Application Proxy Service. An arrow connects the website to the cloud shape. On the bottom right, a box labeled DMZ has the subtitle On-premises. An arrow connects the cloud shape to the DMZ box, splitting in two to point to icons labeled Connector. Below the Connector icon on the left, an arrow points down and splits in two to point to icons labeled App 1 and App 2. Below the Connector icon on the right, an arrow points down to an icon labeled App 3.
Admins in tenant A perform the following steps to enable their external users to access the same on-premises applications.
- Configure access to SAML apps.
- Configure access to other applications.
- Create on-premises users through MIM or PowerShell.
The following articles provide additional information about B2B collaboration.
- Grant B2B users in Microsoft Entra ID access to your on-premises resources describes how you can provide B2B users access to on-premises apps.
- Microsoft Entra B2B collaboration for hybrid organizations describes how you can give your external partners access to apps and resources in your organization.
Next steps
- Multitenant user management introduction is the first in the series of articles that provide guidance for configuring and providing user lifecycle management in Microsoft Entra multitenant environments.
- Multitenant user management scenarios describes three scenarios for which you can use multitenant user management features: end user-initiated, scripted, and automated.
- Common considerations for multitenant user management provides guidance for these considerations: cross-tenant synchronization, directory object, Microsoft Entra Conditional Access, additional access control, and Office 365.