Risk-based access policies
Access control policies can be applied to protect organizations when a sign-in or user is detected to be at risk. Such policies are called risk-based policies.
Microsoft Entra Conditional Access offers two risk conditions: Sign-in risk and User risk. Organizations can create risk-based Conditional Access policies by configuring these two risk conditions and choosing an access control method. During each sign-in, Microsoft Entra ID Protection sends the detected risk levels to Conditional Access, and the risk-based policies apply if the policy conditions are satisfied.
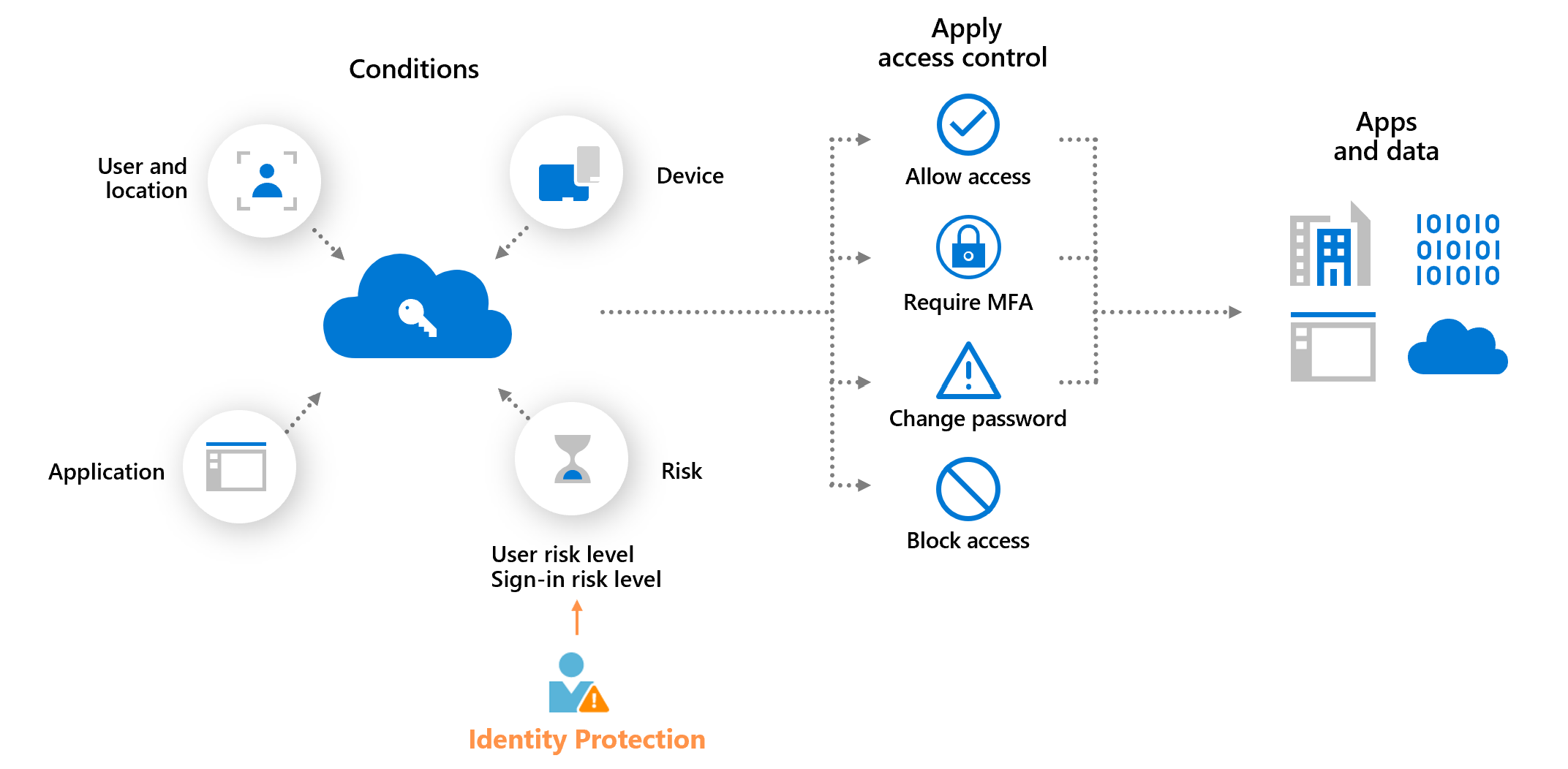
For example, if organizations have a sign-in risk policy that requires multifactor authentication when the sign-in risk level is medium or high, their users must complete multifactor authentication when their sign-in risk is medium or high.
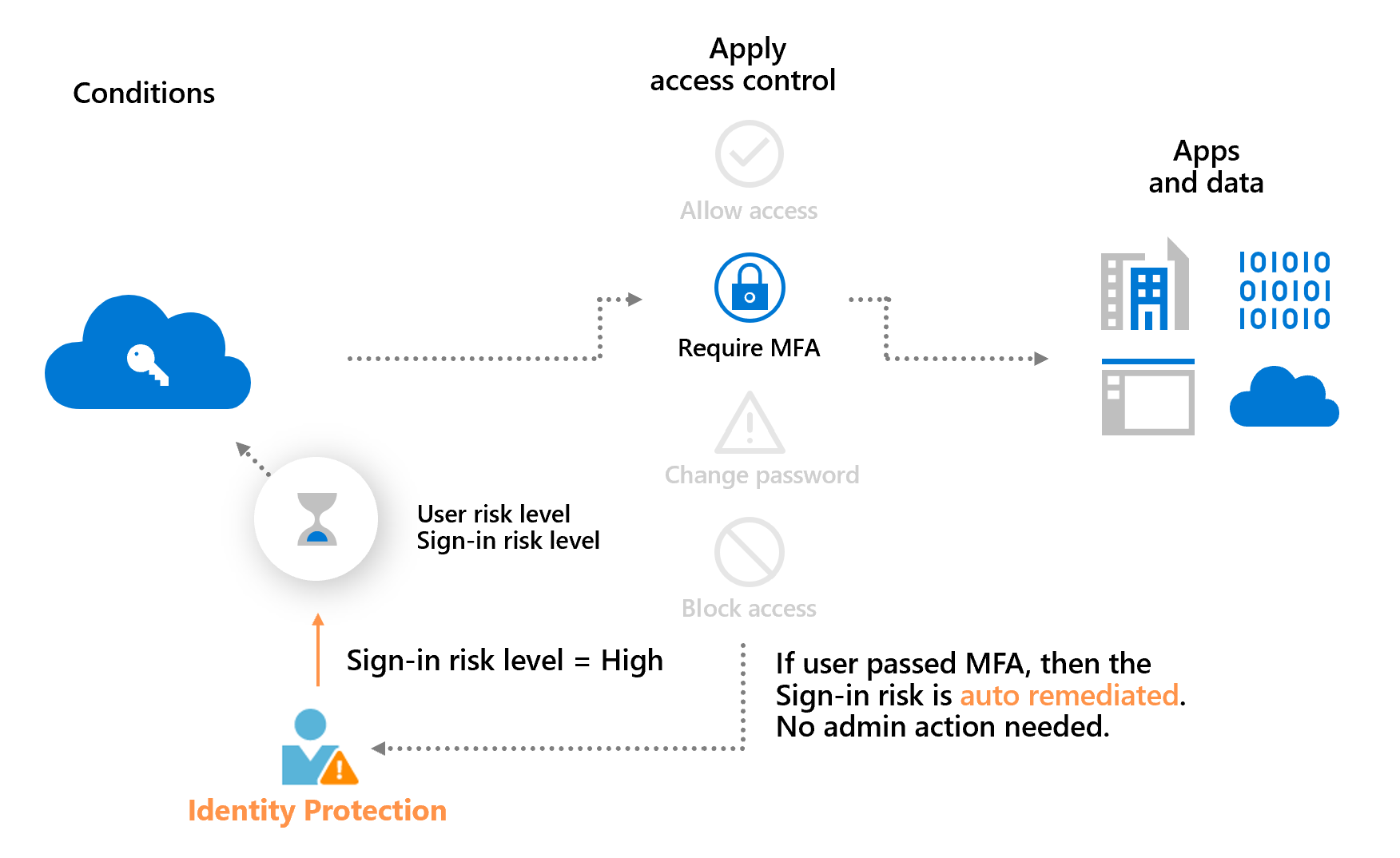
The previous example also demonstrates a main benefit of a risk-based policy: automatic risk remediation. When a user successfully completes the required access control, like a secure password change, their risk is remediated. That sign-in session and user account aren't at risk, and no action is needed from the administrator.
Allowing users to self-remediate using this process significantly reduces the risk investigation and remediation burden on the administrators while protecting your organizations from security compromises. More information about risk remediation can be found in the article, Remediate risks and unblock users.
Sign-in risk-based Conditional Access policy
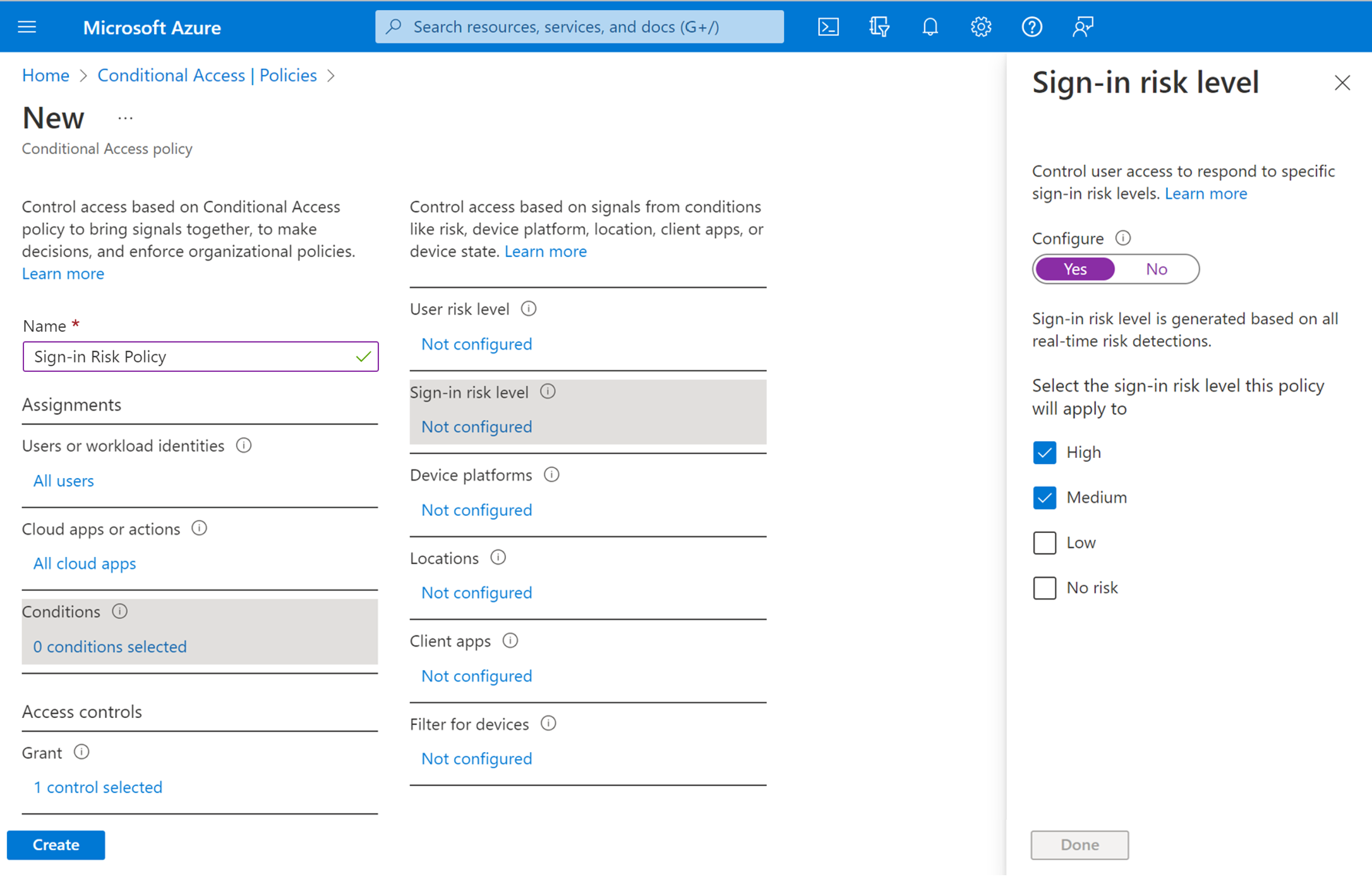
During each sign-in, ID Protection analyzes hundreds of signals in real-time and calculates a sign-in risk level that represents the probability that the given authentication request isn't authorized. This risk level then gets sent to Conditional Access, where the organization's configured policies are evaluated. Administrators can configure sign-in risk-based Conditional Access policies to enforce access controls based on sign-in risk, including requirements such as:
- Block access
- Allow access
- Require multifactor authentication
If risks are detected on a sign-in, users can perform the required access control such as multifactor authentication to self-remediate and close the risky sign-in event to prevent unnecessary noise for administrators.
Note
Users must have previously registered for Microsoft Entra multifactor authentication before triggering the sign-in risk policy.
User risk-based Conditional Access policy
ID Protection analyzes signals about user accounts and calculates a risk score based on the probability that the user is compromised. If a user has risky sign-in behavior, or their credentials leak, ID Protection uses these signals to calculate the user risk level. Administrators can configure user risk-based Conditional Access policies to enforce access controls based on user risk, including requirements such as:
- Block access
- Allow access but require a secure password change.
A secure password change remediates the user risk and close the risky user event to prevent unnecessary noise for administrators.
Migrate ID Protection risk policies to Conditional Access
If you have the legacy user risk policy or sign-in risk policy enabled in ID Protection (formerly Identity Protection), we invite you to migrate them to Conditional Access.
Warning
The legacy risk policies configured in Microsoft Entra ID Protection will be retired on October 1, 2026.
Configuring risk policies in Conditional Access provides benefits like:
- Manage access policies in one location.
- Report-only mode and Graph API support.
- Enforce a sign-in frequency of every time to require reauthentication every time.
- Granular access control by combining risk conditions with other conditions like location.
- Enhanced security with multiple risk-based policies targeting different user groups or risk levels.
- Improved diagnostics experience detailing which risk-based policy applied in sign-in Logs.
- Supported by the backup authentication system.
Microsoft Entra multifactor authentication registration policy
ID Protection can help organizations roll out Microsoft Entra multifactor authentication using a policy requiring registration at sign-in. Enabling this policy is a great way to ensure new users in your organization register for MFA on their first day. Multifactor authentication is one of the self-remediation methods for risk events within ID Protection. Self-remediation allows your users to take action on their own to reduce helpdesk call volume.
More information about Microsoft Entra multifactor authentication can be found in the article, How it works: Microsoft Entra multifactor authentication.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for