Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this tutorial, learn to integrate Microsoft Entra ID with Cloudflare Zero Trust. Build rules based on user identity and group membership. Users authenticate with Microsoft Entra credentials and connect to Zero Trust protected applications.
Prerequisites
- A Microsoft Entra subscription
- If you don't have one, get an Azure free account
- A Microsoft Entra tenant linked to the Microsoft Entra subscription
- A Cloudflare Zero Trust account
- If you don't have one, go to Get started with Cloudflare's Zero Trust platform
- One of the following roles: Cloud Application Administrator, or Application Administrator.
Integrate organization identity providers with Cloudflare Access
Cloudflare Zero Trust Access helps enforce default-deny, Zero Trust rules that limit access to corporate applications, private IP spaces, and hostnames. This feature connects users faster and safer than a virtual private network (VPN). Organizations can use multiple identity providers (IdPs), reducing friction when working with partners or contractors.
To add an IdP as a sign-in method, sign in to Cloudflare on the Cloudflare sign in page and Microsoft Entra ID.
The following architecture diagram shows the integration.
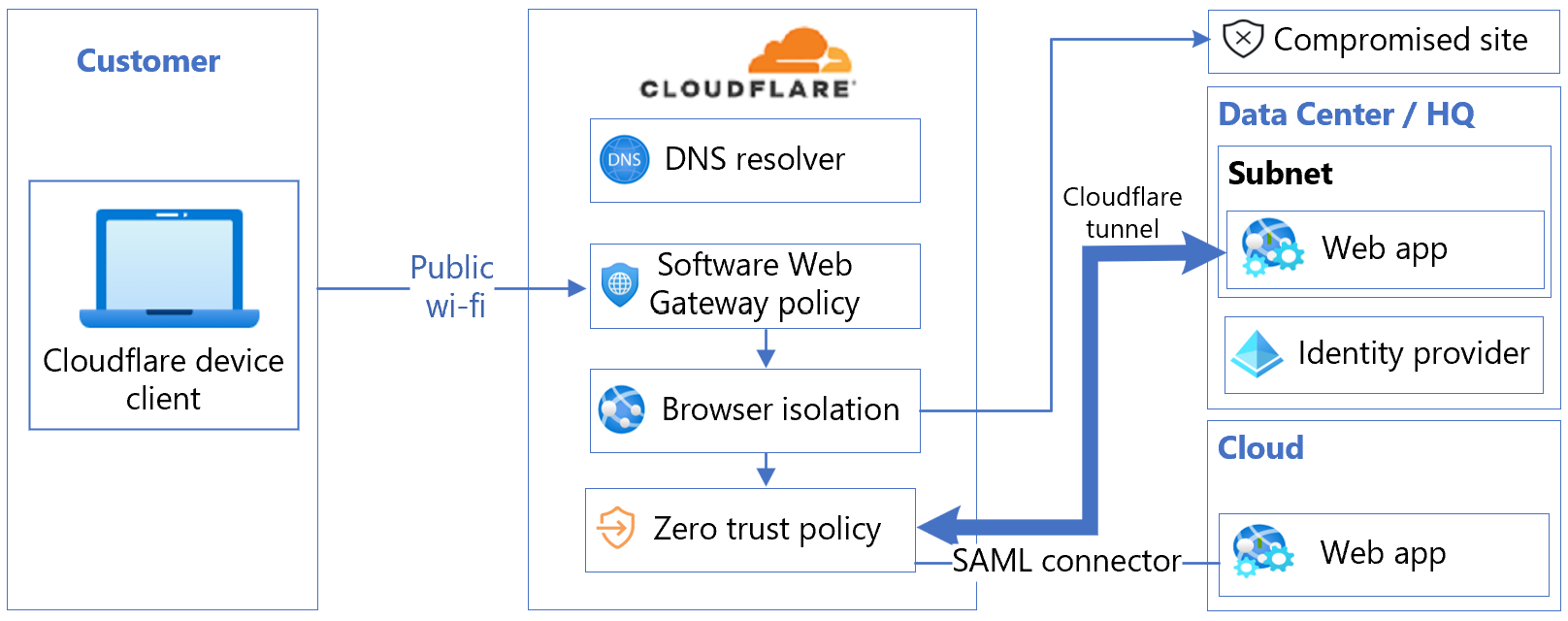
Integrate a Cloudflare Zero Trust account with Microsoft Entra ID
Integrate Cloudflare Zero Trust account with an instance of Microsoft Entra ID.
Sign in to the Cloudflare Zero Trust dashboard on the Cloudflare sign in page.
Navigate to Settings.
Select Authentication.
For Login methods, select Add new.
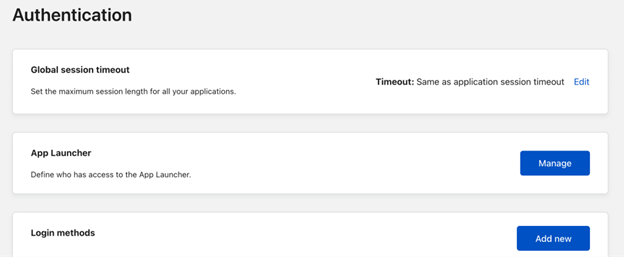
Under Select an identity provider, select Microsoft Entra ID.
The Add Azure ID dialog appears.
Enter Microsoft Entra instance credentials and make needed selections.
Select Save.
Register Cloudflare with Microsoft Entra ID
Use the instructions in the following three sections to register Cloudflare with Microsoft Entra ID.
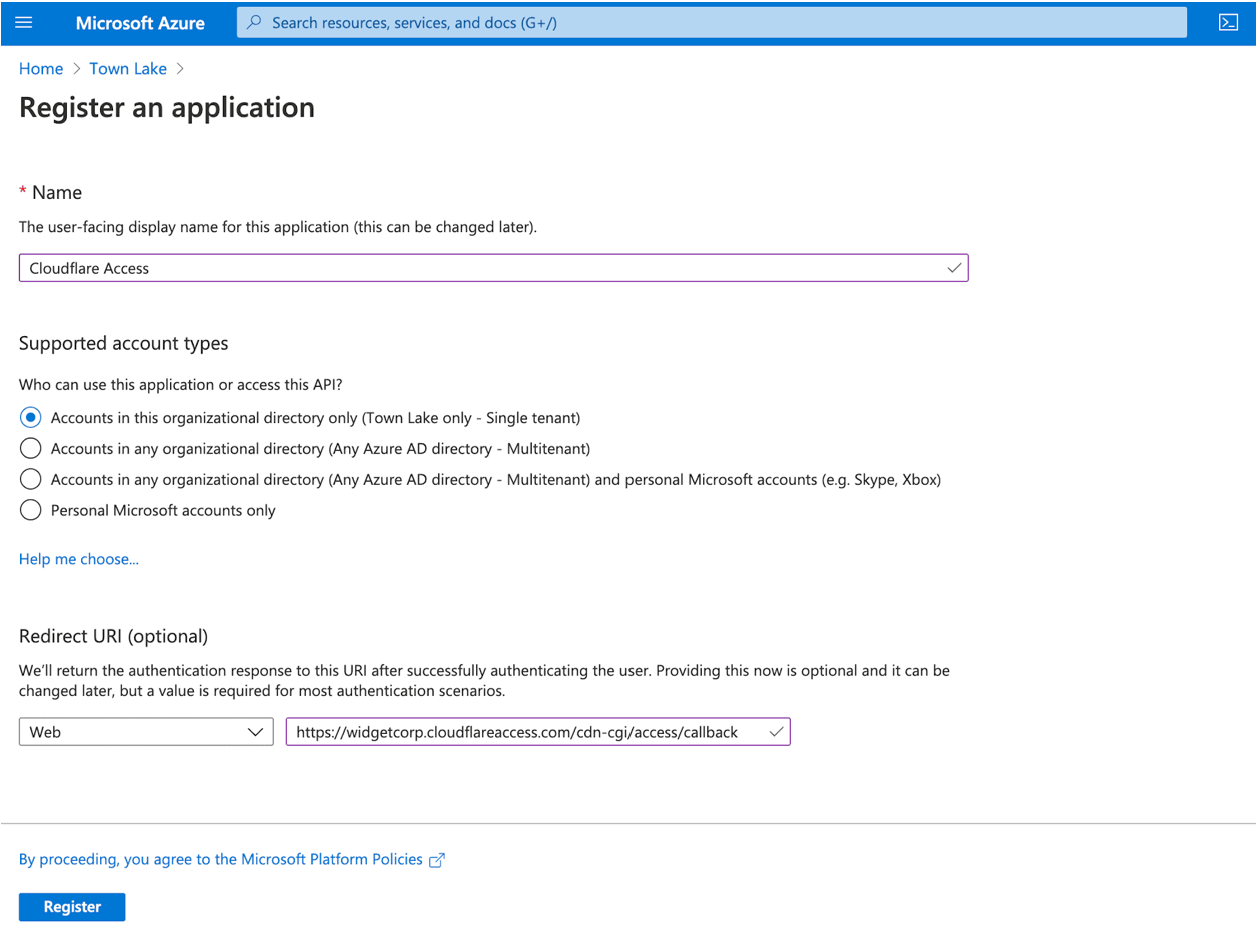
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Navigate to Entra ID > App registrations.
- Select New registration.
- Enter an application Name.
- Enter a team name with callback at the end of the path. For example,
https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callback - Select Register.
See the team domain definition in the Cloudflare Glossary.
Certificates & secrets
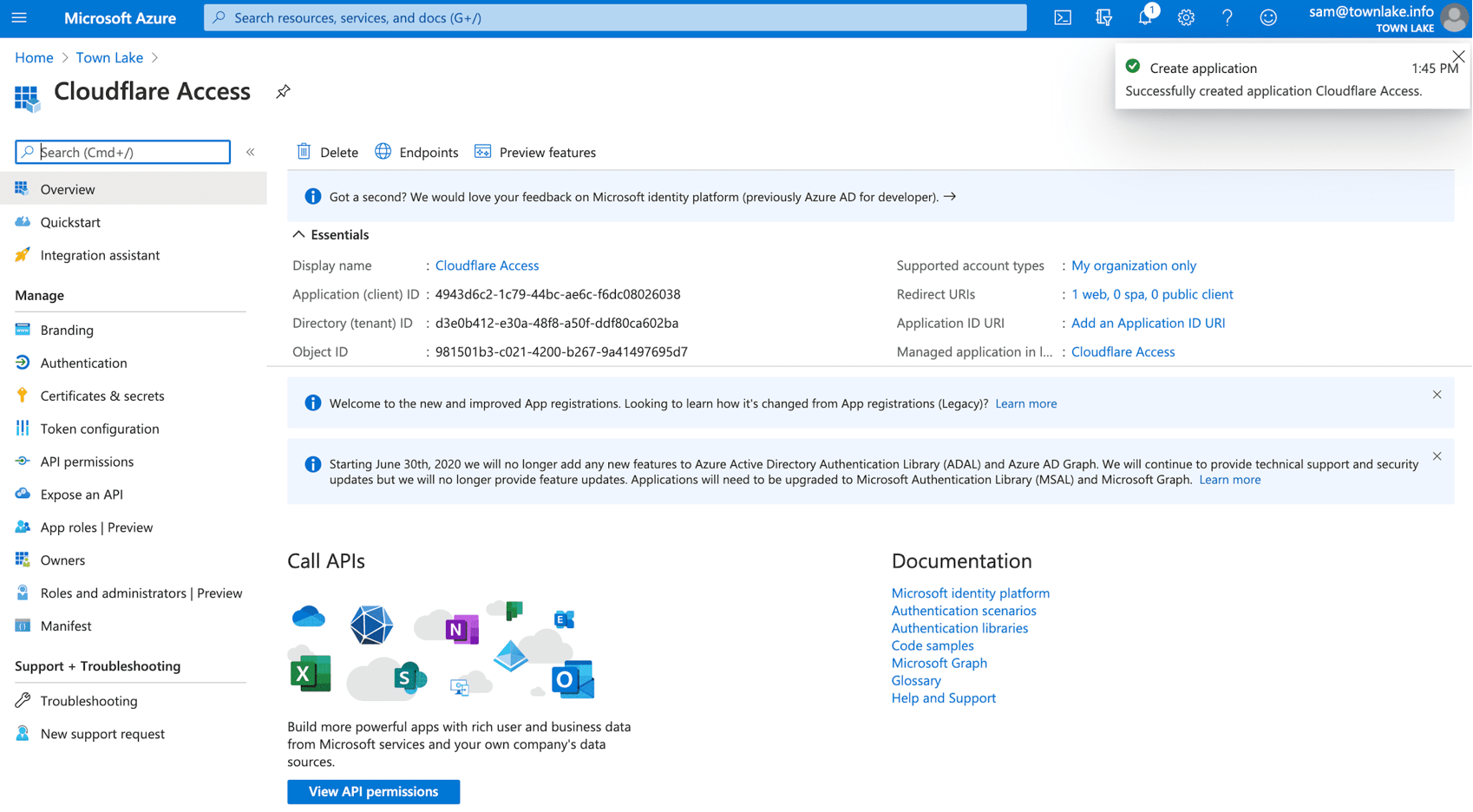
On the Cloudflare Access screen, under Essentials, copy and save the Application (Client) ID and the Directory (Tenant) ID.
In the left menu, under Manage, select Certificates & secrets.
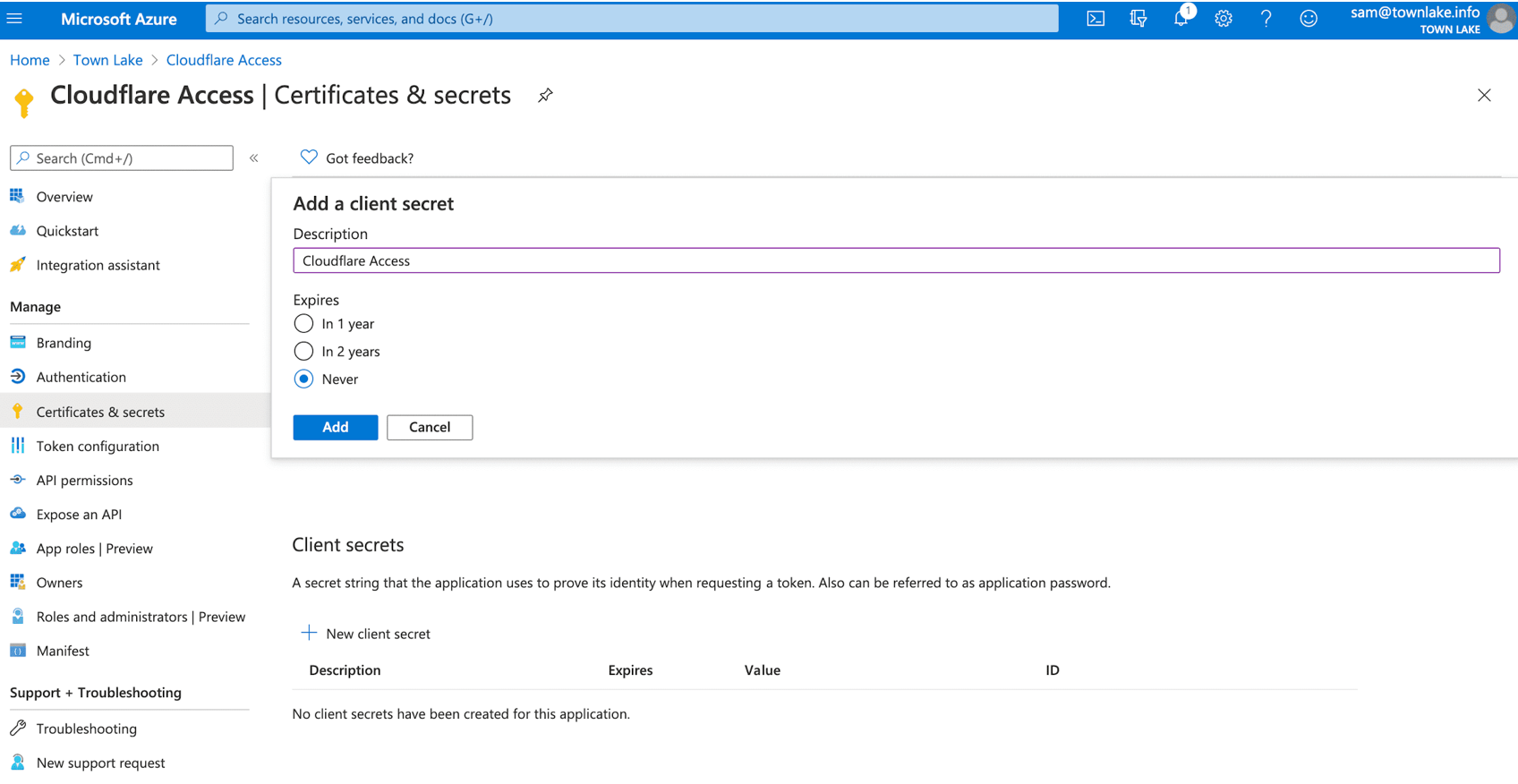
Under Client secrets, select + New client secret.
In Description, enter the Client Secret.
Under Expires, select an expiration.
Select Add.
Under Client secrets, from the Value field, copy the value. Consider the value an application password. The example value appears, Azure values appear in the Cloudflare Access configuration.
Permissions
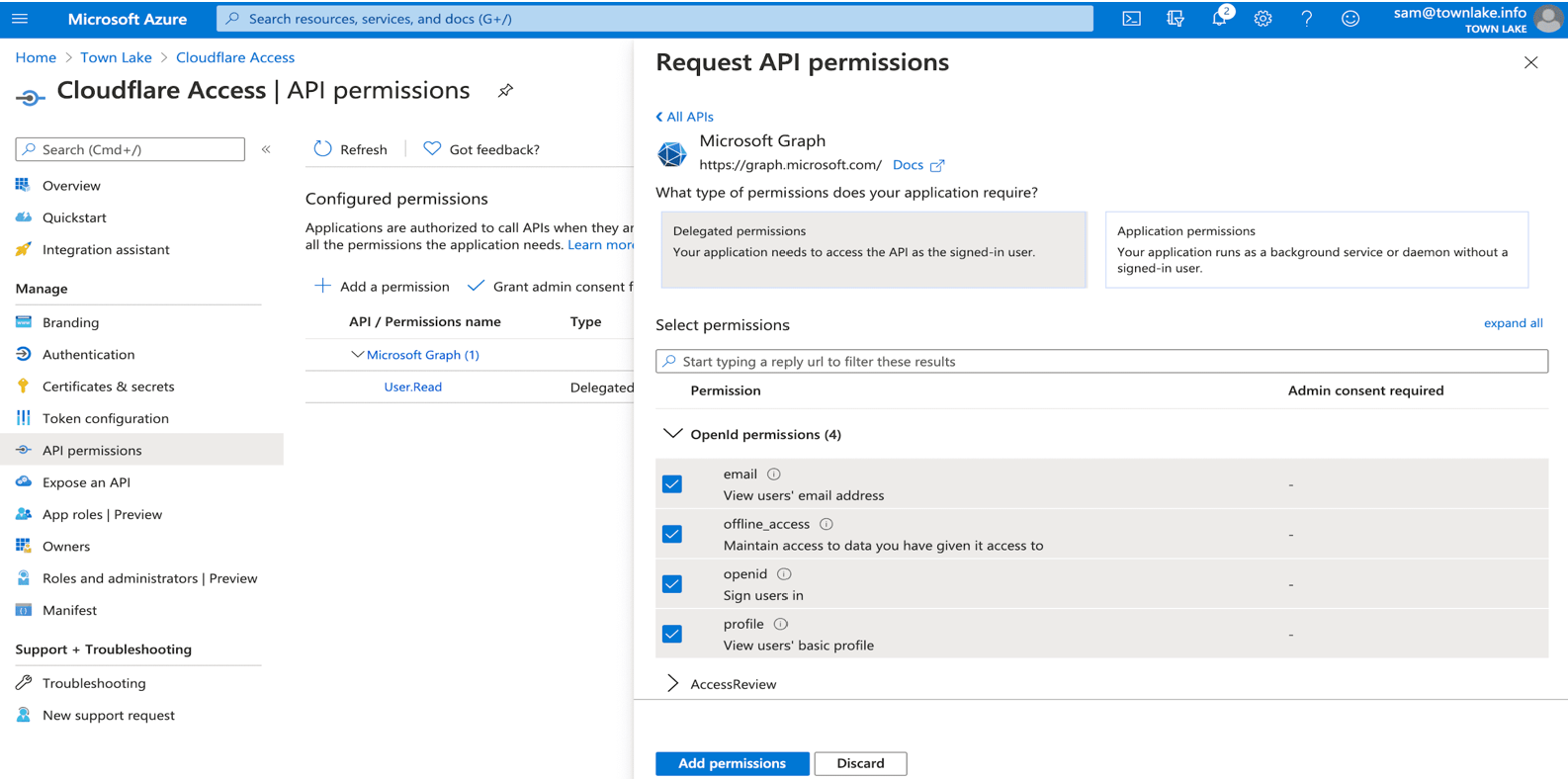
In the left menu, select API permissions.
Select + Add a permission.
Under Select an API, select Microsoft Graph.
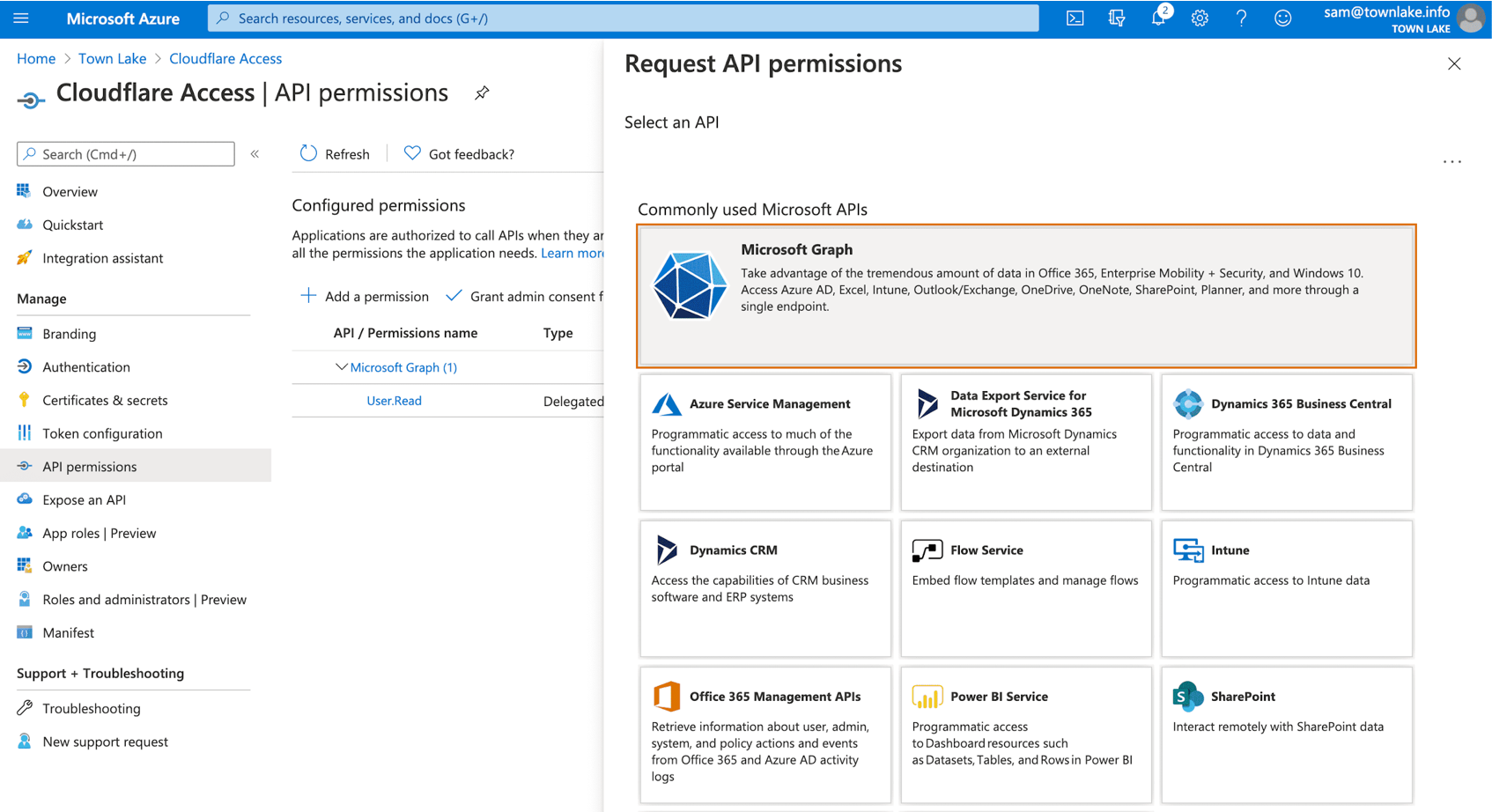
Select Delegated permissions for the following permissions:
- openid
- profile
- offline_access
- user.read
- directory.read.all
- group.read.all
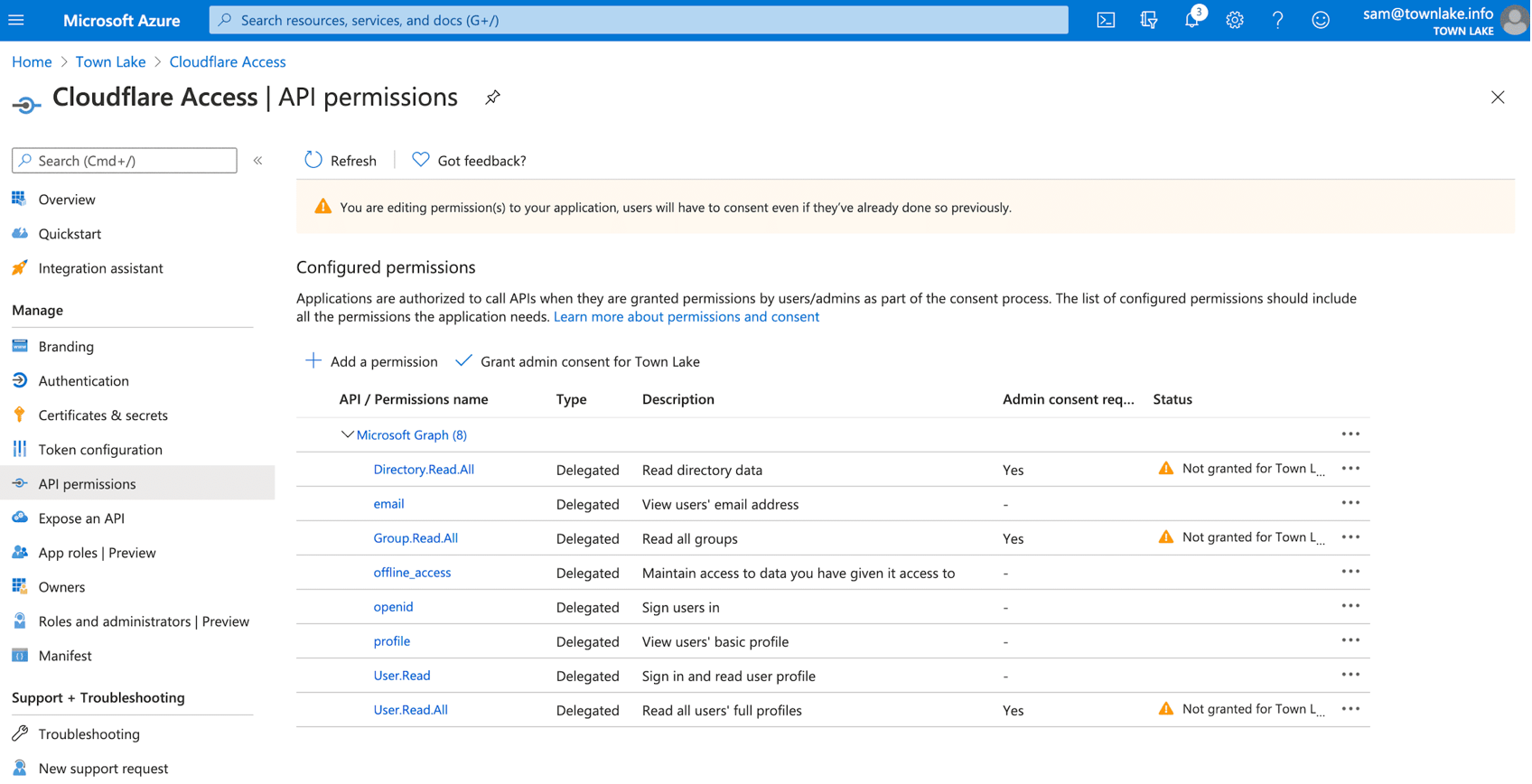
Under Manage, select + Add permissions.
Select Grant Admin Consent for ....
On the Cloudflare Zero Trust dashboard, navigate to Settings > Authentication.
Under Login methods, select Add new.
Select Microsoft Entra ID.
Enter values for Application ID, Application Secret, and Directory ID.
Select Save.
Note
For Microsoft Entra groups, in Edit your Microsoft Entra identity provider, for Support Groups select On.
Test the integration
On the Cloudflare Zero Trust dashboard, navigate to Settings > Authentication.
Under Login methods, for Microsoft Entra ID select Test.
Enter Microsoft Entra credentials.
The Your connection works message appears.
Related content
- Go to developer.cloudflare.com for Integrate Single sign-on
- Tutorial: Configure Conditional Access policies for Cloudflare Access