Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra Privileged Identity Management (PIM) simplifies how enterprises manage privileged access to resources in Microsoft Entra ID and other Microsoft online services like Microsoft 365 or Microsoft Intune.
If you have been made eligible for an administrative role, then you must activate the role assignment when you need to perform privileged actions. For example, if you occasionally manage Microsoft 365 features, your organization's Privileged Role Administrators might not make you a permanent Global Administrator, since that role impacts other services, too. Instead, they would make you eligible for Microsoft Entra roles such as Exchange Online Administrator. You can request to activate that role when you need its privileges, and then have administrator control for a predetermined time period.
This article is for administrators who need to activate their Microsoft Entra role in Privileged Identity Management. Although any user can submit a request for the role they need through PIM without having the Privileged Role Administrator (PRA) role, this role is required for managing and assigning roles to others within the organization.
Important
When a role is activated, Microsoft Entra PIM temporarily adds active assignment for the role. Microsoft Entra PIM creates active assignment (assigns user to a role) within seconds. When deactivation (manual or through activation time expiration) happens, Microsoft Entra PIM removes the active assignment within seconds as well.
Application may provide access based on the role the user has. In some situations, application access may not immediately reflect the fact that user got role assigned or removed. If application previously cached the fact that user does not have a role – when user tries to access application again, access may not be provided. Similarly, if application previously cached the fact that user has a role – when role is deactivated, user may still get access. Specific situation depends on the application’s architecture. For some applications, signing out and signing back in may help get access added or removed.
Important
If a user activating an administrative role is signed in to Microsoft Teams on a mobile device, they will receive a notification from the Teams app saying "Open Teams to continue receiving notifications for <email address>", or "<email address> needs to sign in to see notifications". The user will need to open the Teams app to continue receiving notifications. This behavior is by design.
Prerequisites
Activate a role
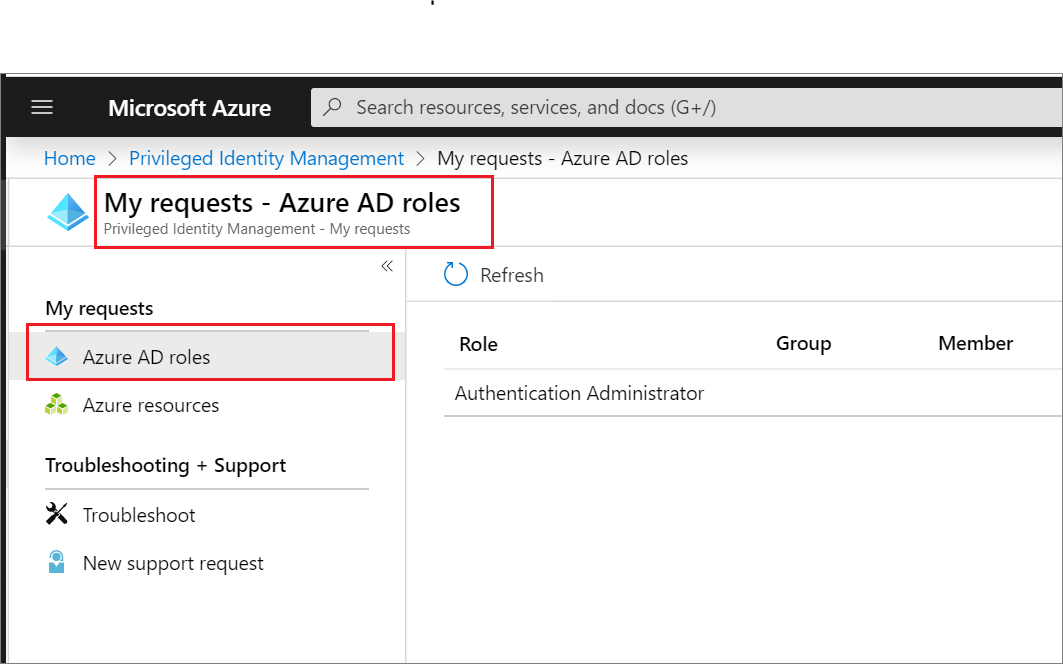
When you need to assume a Microsoft Entra role, you can request activation by opening My roles in Privileged Identity Management.
Note
PIM is now available in the Azure mobile app (iOS | Android) for Microsoft Entra ID and Azure resource roles. Easily activate eligible assignments, request renewals for ones that are expiring, or check the status of pending requests. Read more
Sign in to the Microsoft Entra admin center as a user who has an eligible role assignment.
Browse to ID Governance > Privileged Identity Management > My roles. For information about how to add the Privileged Identity Management tile to your dashboard, see Start using Privileged Identity Management.
Select Microsoft Entra roles to see a list of your eligible Microsoft Entra roles.
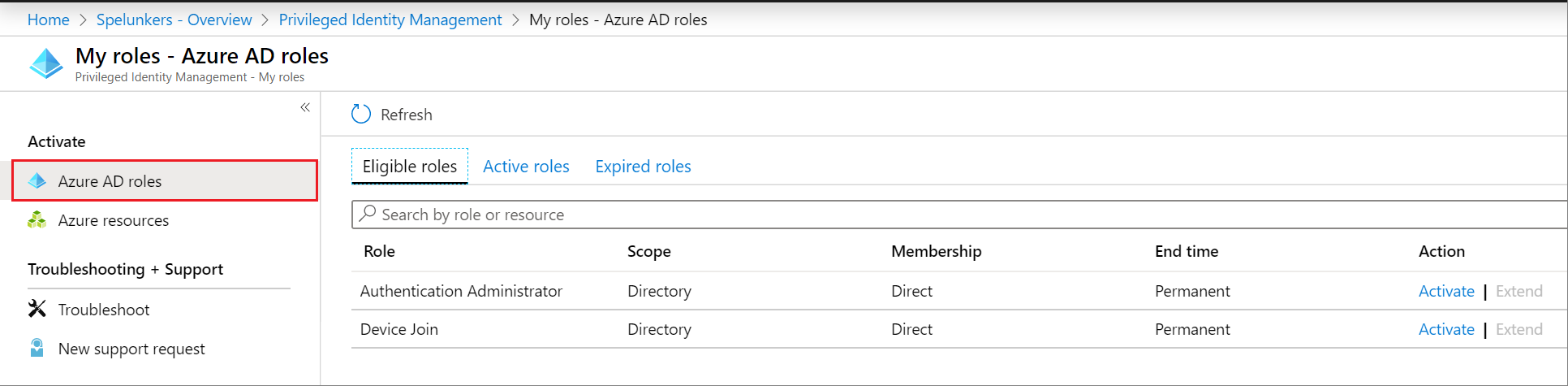
In the Microsoft Entra roles list, find the role you want to activate.
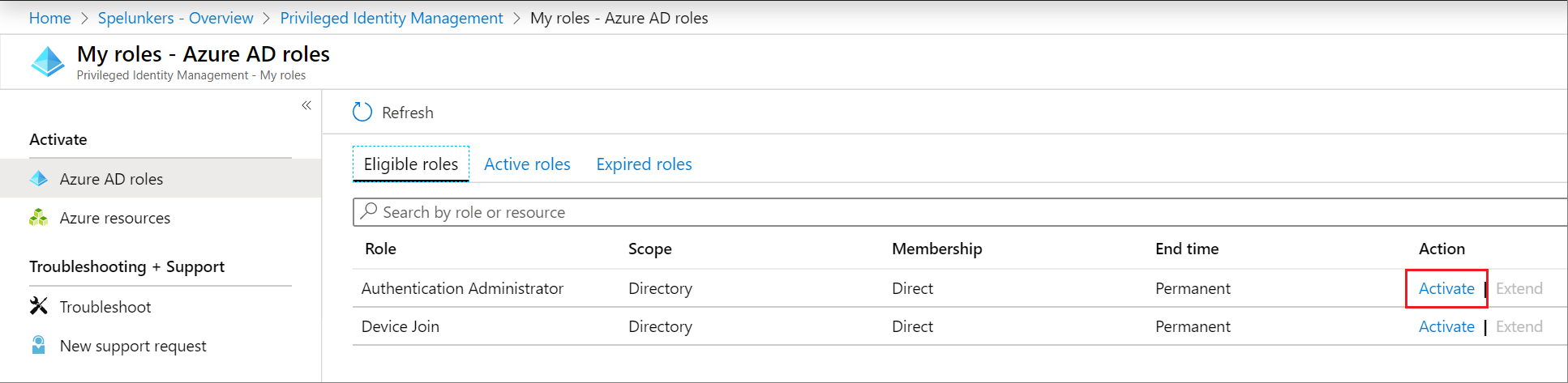
Select Activate to open the Activate pane.
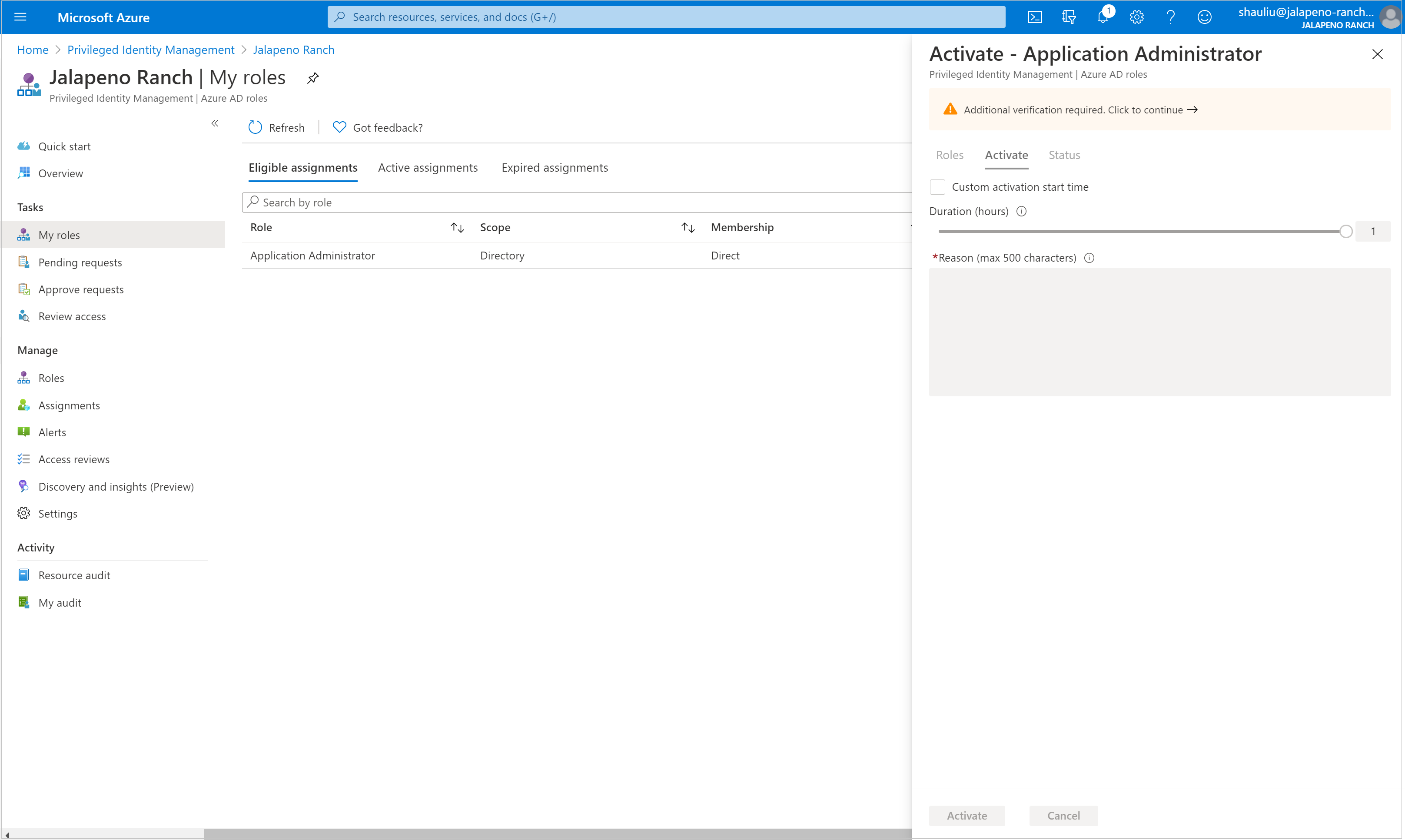
Select Additional verification required and follow the instructions to provide security verification. You are required to authenticate only once per session.
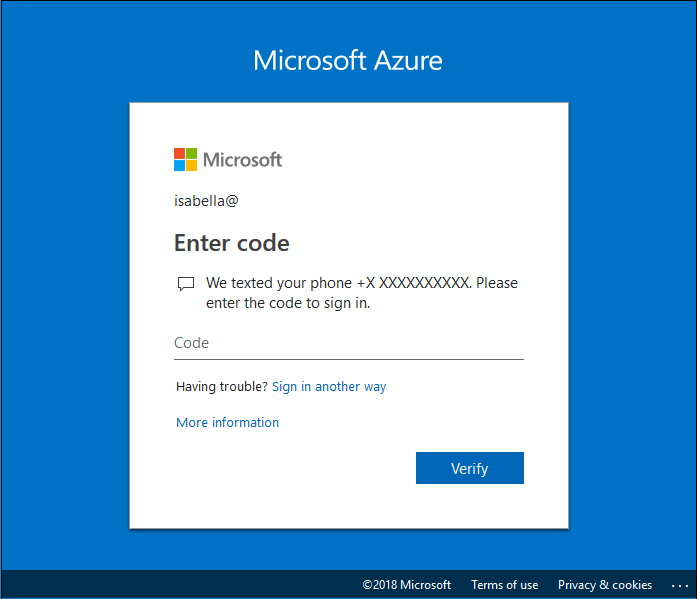
After multifactor authentication, select Activate before proceeding.
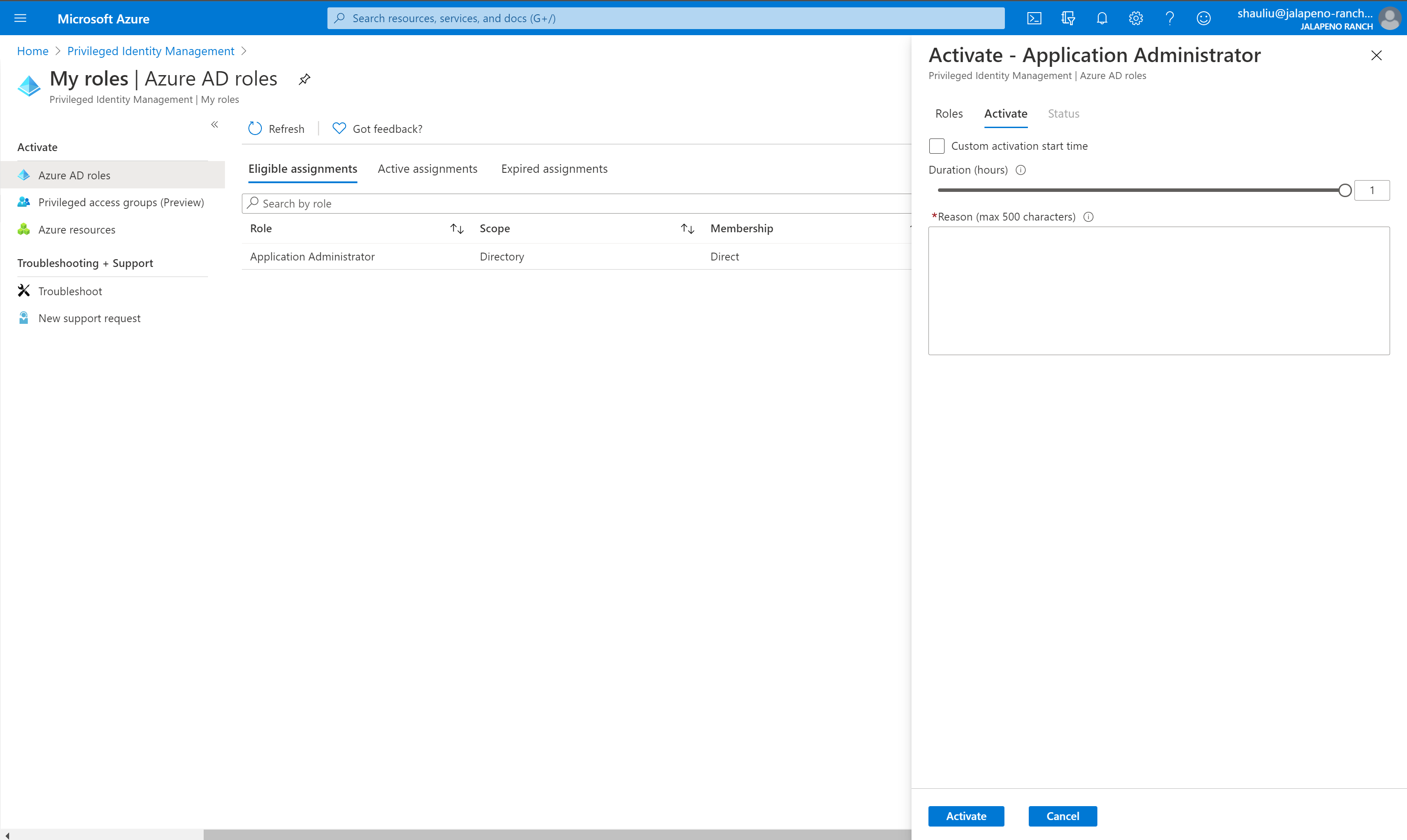
If you want to specify a reduced scope, select Scope to open the filter pane. On the filter pane, you can specify the Microsoft Entra resources that you need access to. It's a best practice to request access to the fewest resources that you need.
If necessary, specify a custom activation start time. The Microsoft Entra role would be activated after the selected time.
In the Reason box, enter the reason for the activation request.
Select Activate.
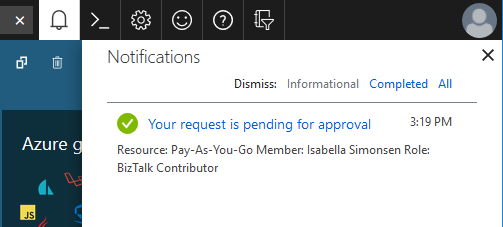
If the role requires approval to activate, a notification appears in the upper right corner of your browser informing you the request is pending approval.
Activate a role using Microsoft Graph API
For more information about Microsoft Graph APIs for PIM, see Overview of role management through the privileged identity management (PIM) API.
Get all eligible roles that you can activate
When a user gets their role eligibility via group membership, this Microsoft Graph request doesn't return their eligibility.
HTTP request
GET https://graph.microsoft.com/v1.0/roleManagement/directory/roleEligibilityScheduleRequests/filterByCurrentUser(on='principal')HTTP response
To save space we're showing only the response for one role, but all eligible role assignments that you can activate will be listed.
{ "@odata.context": "https://graph.microsoft.com/v1.0/$metadata#Collection(unifiedRoleEligibilityScheduleRequest)", "value": [ { "@odata.type": "#microsoft.graph.unifiedRoleEligibilityScheduleRequest", "id": "50d34326-f243-4540-8bb5-2af6692aafd0", "status": "Provisioned", "createdDateTime": "2022-04-12T18:26:08.843Z", "completedDateTime": "2022-04-12T18:26:08.89Z", "approvalId": null, "customData": null, "action": "adminAssign", "principalId": "aaaaaaaa-bbbb-cccc-1111-222222222222", "roleDefinitionId": "8424c6f0-a189-499e-bbd0-26c1753c96d4", "directoryScopeId": "/", "appScopeId": null, "isValidationOnly": false, "targetScheduleId": "50d34326-f243-4540-8bb5-2af6692aafd0", "justification": "Assign Attribute Assignment Admin eligibility to myself", "createdBy": { "application": null, "device": null, "user": { "displayName": null, "id": "00aa00aa-bb11-cc22-dd33-44ee44ee44ee" } }, "scheduleInfo": { "startDateTime": "2022-04-12T18:26:08.8911834Z", "recurrence": null, "expiration": { "type": "afterDateTime", "endDateTime": "2024-04-10T00:00:00Z", "duration": null } }, "ticketInfo": { "ticketNumber": null, "ticketSystem": null } } ] }Self-activate a role eligibility with justification
HTTP request
POST https://graph.microsoft.com/v1.0/roleManagement/directory/roleAssignmentScheduleRequests { "action": "selfActivate", "principalId": "aaaaaaaa-bbbb-cccc-1111-222222222222", "roleDefinitionId": "8424c6f0-a189-499e-bbd0-26c1753c96d4", "directoryScopeId": "/", "justification": "I need access to the Attribute Administrator role to manage attributes to be assigned to restricted AUs", "scheduleInfo": { "startDateTime": "2022-04-14T00:00:00.000Z", "expiration": { "type": "AfterDuration", "duration": "PT5H" } }, "ticketInfo": { "ticketNumber": "CONTOSO:Normal-67890", "ticketSystem": "MS Project" } }HTTP response
HTTP/1.1 201 Created Content-Type: application/json { "@odata.context": "https://graph.microsoft.com/v1.0/$metadata#roleManagement/directory/roleAssignmentScheduleRequests/$entity", "id": "911bab8a-6912-4de2-9dc0-2648ede7dd6d", "status": "Granted", "createdDateTime": "2022-04-13T08:52:32.6485851Z", "completedDateTime": "2022-04-14T00:00:00Z", "approvalId": null, "customData": null, "action": "selfActivate", "principalId": "aaaaaaaa-bbbb-cccc-1111-222222222222", "roleDefinitionId": "8424c6f0-a189-499e-bbd0-26c1753c96d4", "directoryScopeId": "/", "appScopeId": null, "isValidationOnly": false, "targetScheduleId": "911bab8a-6912-4de2-9dc0-2648ede7dd6d", "justification": "I need access to the Attribute Administrator role to manage attributes to be assigned to restricted AUs", "createdBy": { "application": null, "device": null, "user": { "displayName": null, "id": "071cc716-8147-4397-a5ba-b2105951cc0b" } }, "scheduleInfo": { "startDateTime": "2022-04-14T00:00:00Z", "recurrence": null, "expiration": { "type": "afterDuration", "endDateTime": null, "duration": "PT5H" } }, "ticketInfo": { "ticketNumber": "CONTOSO:Normal-67890", "ticketSystem": "MS Project" } }
View the status of activation requests
You can view the status of your pending requests to activate.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to ID Governance > Privileged Identity Management > My requests.
When you select My requests you see a list of your Microsoft Entra role and Azure resource role requests.
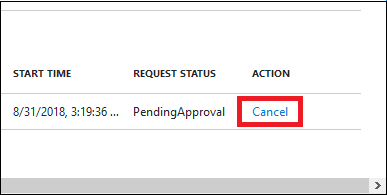
Scroll to the right to view the Request Status column.
Cancel a pending request for new version
If you don't require activation of a role that requires approval, you can cancel a pending request at any time.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to ID Governance > Privileged Identity Management > My requests.
For the role that you want to cancel, select the Cancel link.
When you select Cancel, the request is canceled. To activate the role again, you have to submit a new request for activation.
Deactivate a role assignment
When a role assignment is activated, you see a Deactivate option in the PIM portal for the role assignment. Also, you can't deactivate a role assignment within five minutes after activation.
Activate PIM roles using the Azure mobile app
PIM is now available in the Microsoft Entra ID and Azure resource roles mobile apps in both iOS and Android.
Note
An active Premium P2 or EMS E5 license is required for the signed-in user to use this inside the app.
To activate an eligible Microsoft Entra role assignment, start by downloading the Azure mobile app (iOS | Android). You can also download the app by selecting ‘Open in mobile’ from Privileged Identity Management > My roles > Microsoft Entra roles.
Open the Azure mobile app and sign in. Select the Privileged Identity Management card and select My Microsoft Entra roles to view your eligible and active role assignments.
Select the role assignment and click on Action > Activate under the role assignment details. Complete the steps to active and fill in any required details before clicking ‘Activate’ at the bottom.
View the status of your activation requests and your role assignments under My Microsoft Entra roles.