Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
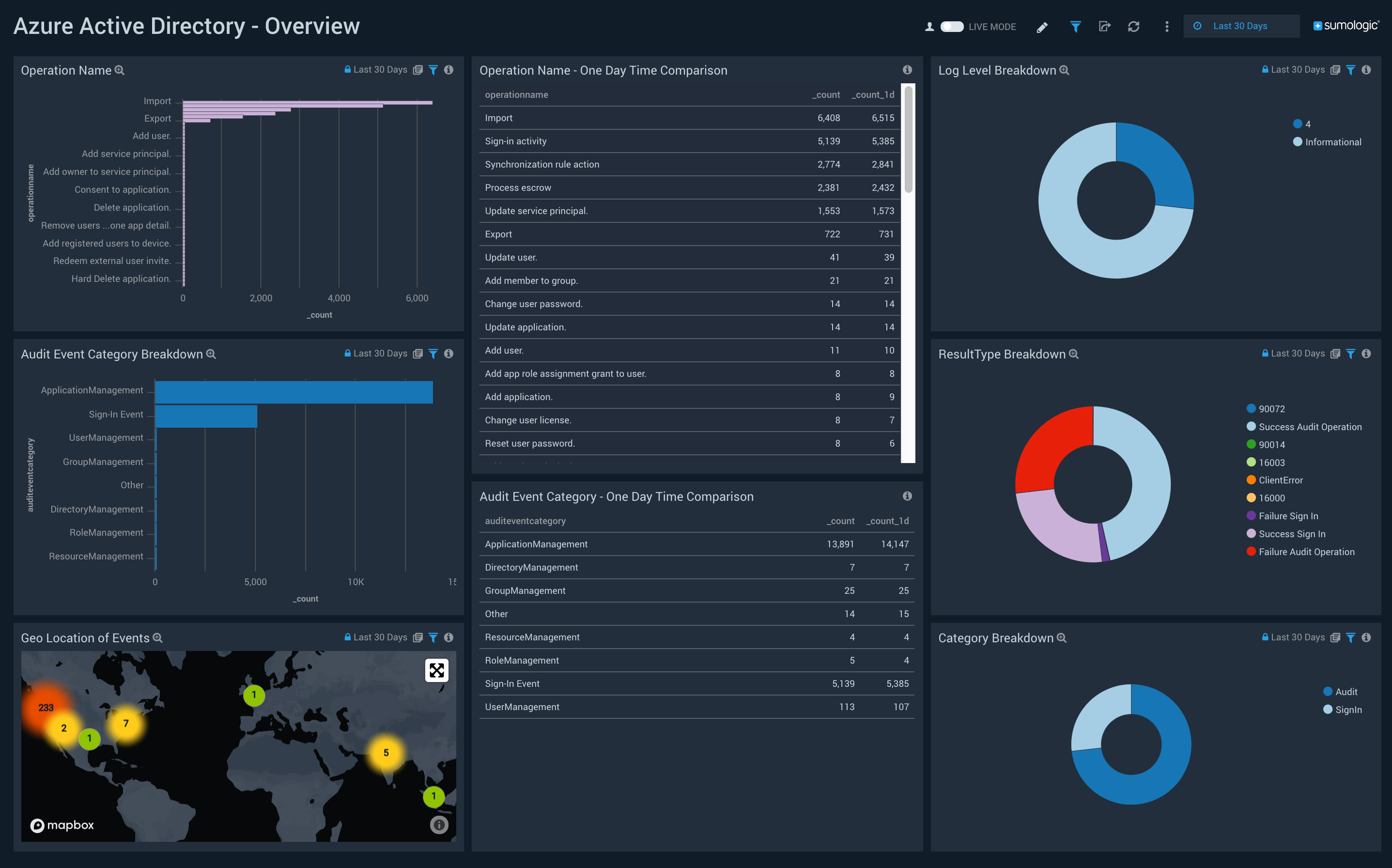
Your Microsoft Entra tenant produces large amounts of data every second. Sign-in activity and logs of changes made in your tenant add up to so much data that it can be hard to analyze. Integrating with Security Information and Event Management (SIEM) tools can help you gain insights into your environment.
This article shows how you can stream your logs to an event hub, to integrate with one of several SIEM tools.
Prerequisites
- An Azure subscription. If you don't have an Azure subscription, you can sign up for a free trial.
- An Azure event hub that is already set up. Learn how to create an event hub.
- Security Administrator access to create general diagnostic settings for the Microsoft Entra tenant.
- Attribute Log Administrator access to create diagnostic settings for custom security attribute logs.
Stream logs to an event hub
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Entra ID > Monitoring & health > Diagnostic settings. You can also select Export Settings from either the Audit Logs or Sign-ins page.
Select + Add diagnostic setting to create a new integration or select Edit setting for an existing integration.
Enter a Diagnostic setting name. If you're editing an existing integration, you can't change the name.
Select the log categories that you want to stream.
Select the Stream to an event hub check box.
Select the Azure subscription, Event Hubs namespace, and optional event hub where you want to route the logs.
The subscription and Event Hubs namespace must both be associated with the Microsoft Entra tenant from where you're streaming the logs.
Once you have the Azure event hub ready, navigate to the SIEM tool you want to integrate with the activity logs. The process is finished in the SIEM tool.
We currently support Splunk, SumoLogic, and ArcSight. Select a tab to get started. Refer to the tool's documentation.
To use this feature, you need the Splunk Add-on for Microsoft Cloud Services.
Integrate Microsoft Entra logs with Splunk
Open your Splunk instance and select Data Summary.
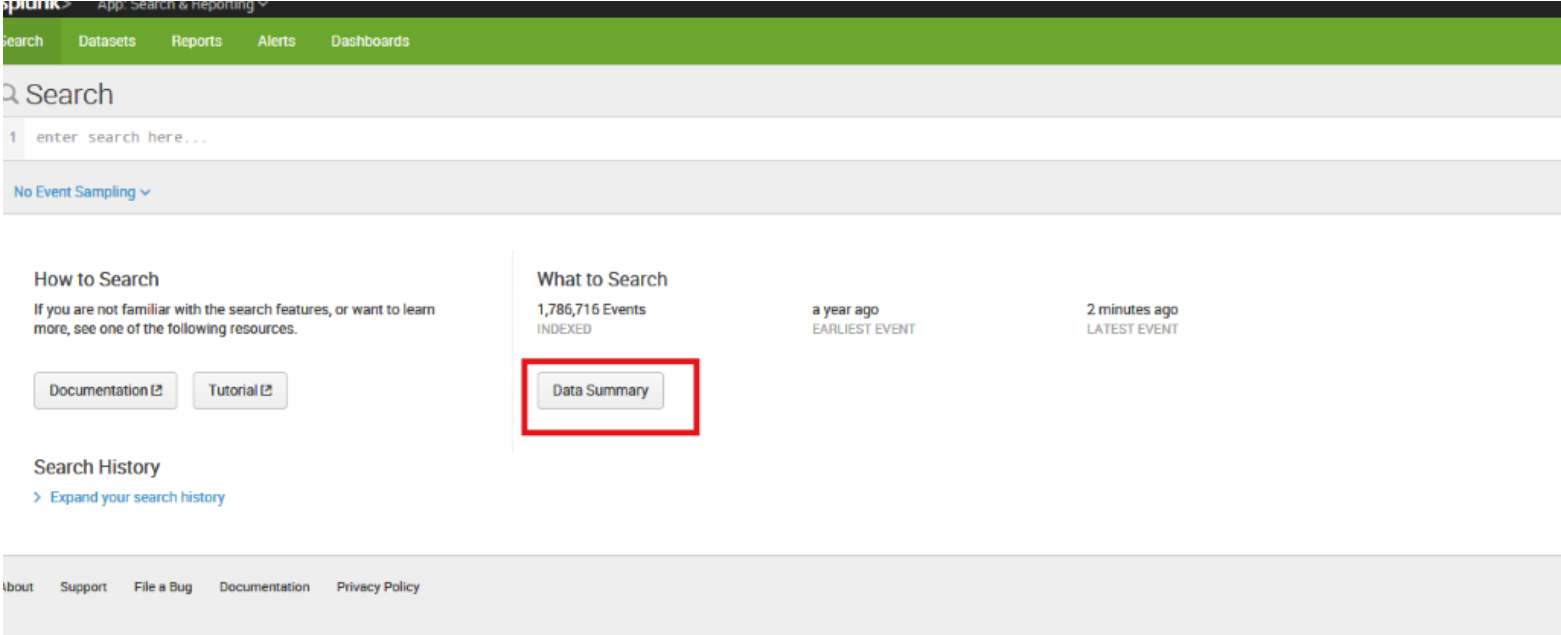
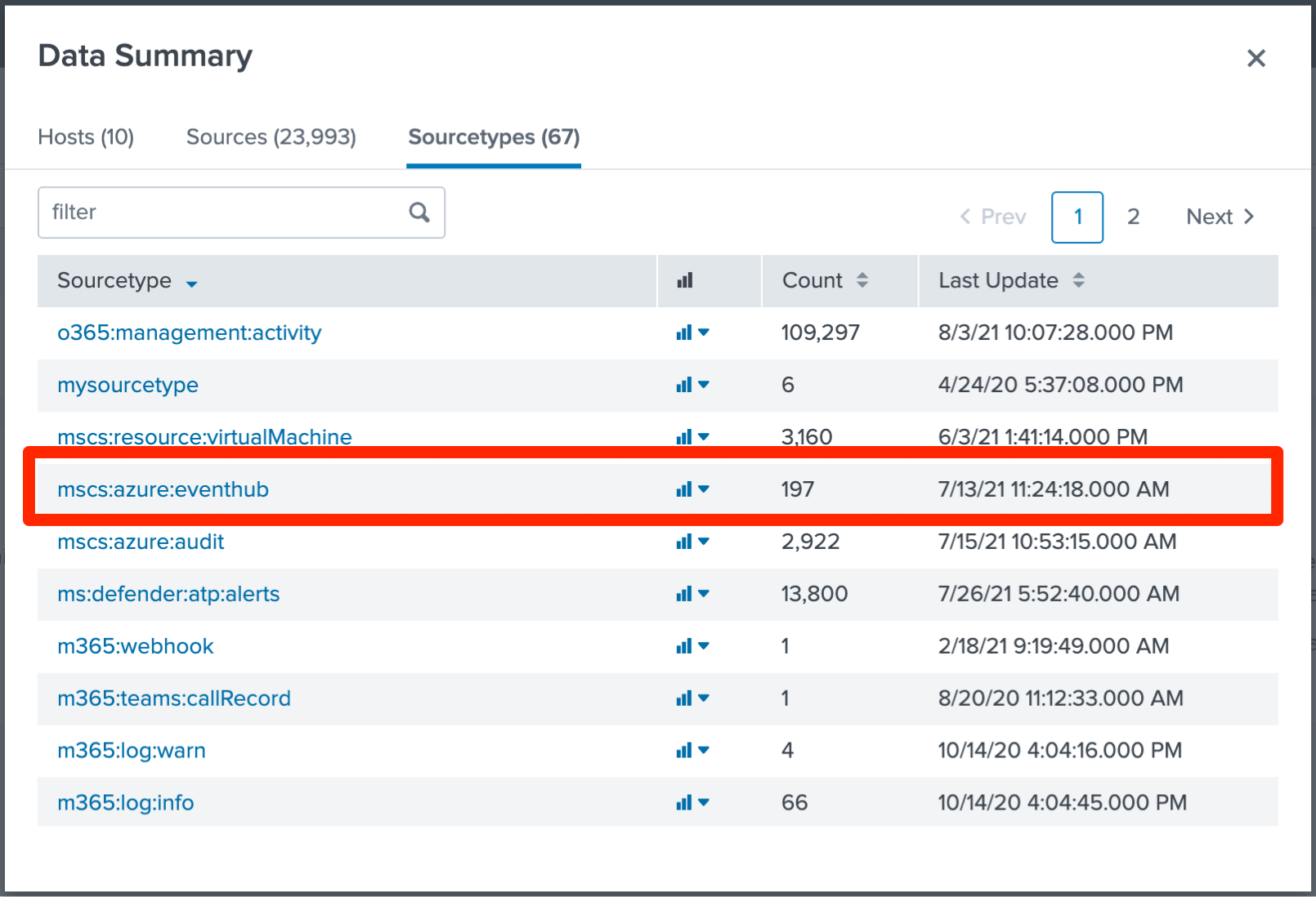
Select the Sourcetypes tab, and then select mscs:azure:eventhub
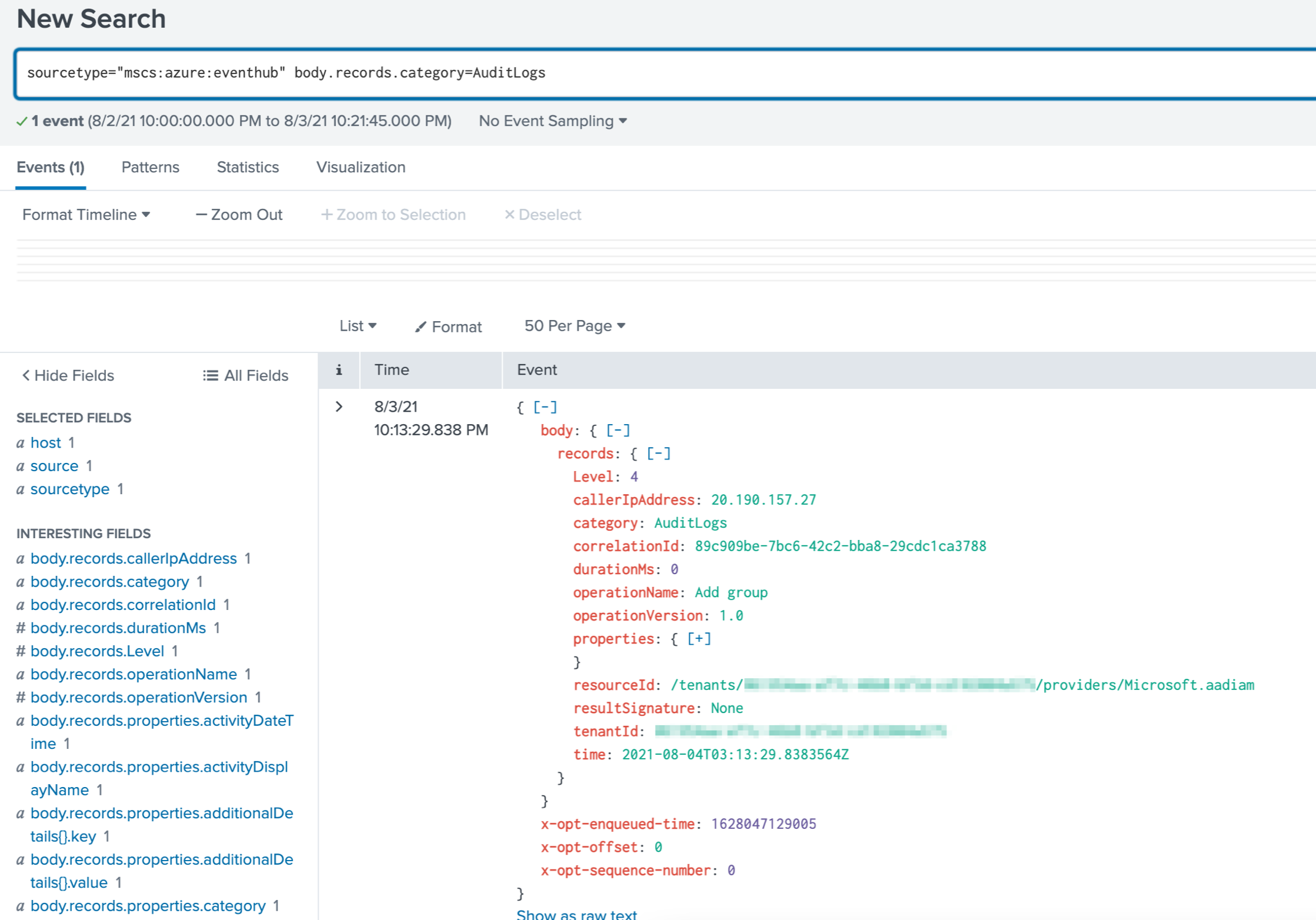
Append body.records.category=AuditLogs to the search. The Microsoft Entra activity logs are shown in the following figure:
If you can't install an add-on in your Splunk instance (for example, if you're using a proxy or running on Splunk Cloud), you can forward these events to the Splunk HTTP Event Collector. To do so, use this Azure function, which is triggered by new messages in the event hub.
Activity log integration options and considerations
If your current SIEM isn't supported in Azure Monitor diagnostics yet, you can set up custom tooling by using the Event Hubs API. To learn more, see the Getting started receiving messages from an event hub.
IBM QRadar is another option for integrating with Microsoft Entra activity logs. The DSM and Azure Event Hubs Protocol are available for download at IBM support. For more information about integration with Azure, go to the IBM QRadar Security Intelligence Platform 7.3.0 site.
Some sign-in categories contain large amounts of log data, depending on your tenant’s configuration. In general, the non-interactive user sign-ins and service principal sign-ins can be 5 to 10 times larger than the interactive user sign-ins.