Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to integrate TurboRater with Microsoft Entra ID.
Integrating TurboRater with Microsoft Entra ID provides you with the following benefits:
- You can control in Microsoft Entra ID who has access to TurboRater.
- You can enable your users to be automatically signed in to TurboRater (single sign-on) with their Microsoft Entra accounts.
- You can manage your accounts in one central location: the Azure portal.
For details about software as a service (SaaS) app integration with Microsoft Entra ID, see What is application access and single sign-on with Microsoft Entra ID?.
Prerequisites
To configure Microsoft Entra integration with TurboRater, you need the following items:
- A Microsoft Entra subscription. If you don't have an Azure subscription, create a free account before you begin.
- A TurboRater subscription with single sign-on enabled.
Scenario description
In this article, you configure and test Microsoft Entra single sign-on in a test environment.
TurboRater supports IDP-initiated single sign-on (SSO).
Add TurboRater from the Azure Marketplace
To configure the integration of TurboRater into Microsoft Entra ID, you need to add TurboRater from the Azure Marketplace to your list of managed SaaS apps:
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Entra ID > Enterprise apps > New application.
- In the Add from the gallery section, type TurboRater in the search box.
- Select TurboRater from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Configure and test Microsoft Entra single sign-on
In this section, you configure and test Microsoft Entra single sign-on with TurboRater based on a test user named B Simon. For single sign-on to work, you must establish a link between a Microsoft Entra user and the related user in TurboRater.
To configure and test Microsoft Entra single sign-on with TurboRater, you need to complete the following building blocks:
- Configure Microsoft Entra single sign-on to enable your users to use this feature.
- Configure TurboRater single sign-on to configure the single sign-on settings on the application side.
- Create a Microsoft Entra test user to test Microsoft Entra single sign-on with B. Simon.
- Assign the Microsoft Entra test user to enable B. Simon to use Microsoft Entra single sign-on.
- Create a TurboRater test user so that there's a user named B. Simon in TurboRater who's linked to the Microsoft Entra user named B. Simon.
- Test single sign-on to verify whether the configuration works.
Configure Microsoft Entra single sign-on
In this section, you enable Microsoft Entra single sign-on.
To configure Microsoft Entra single sign-on with TurboRater, take the following steps:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Entra ID > Enterprise apps > TurboRater application integration page, select Single sign-on.
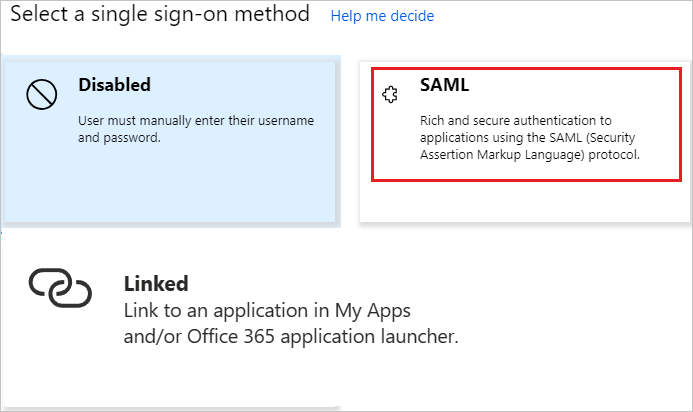
On the Select a single sign-on method pane, select SAML/WS-Fed mode to enable single sign-on.
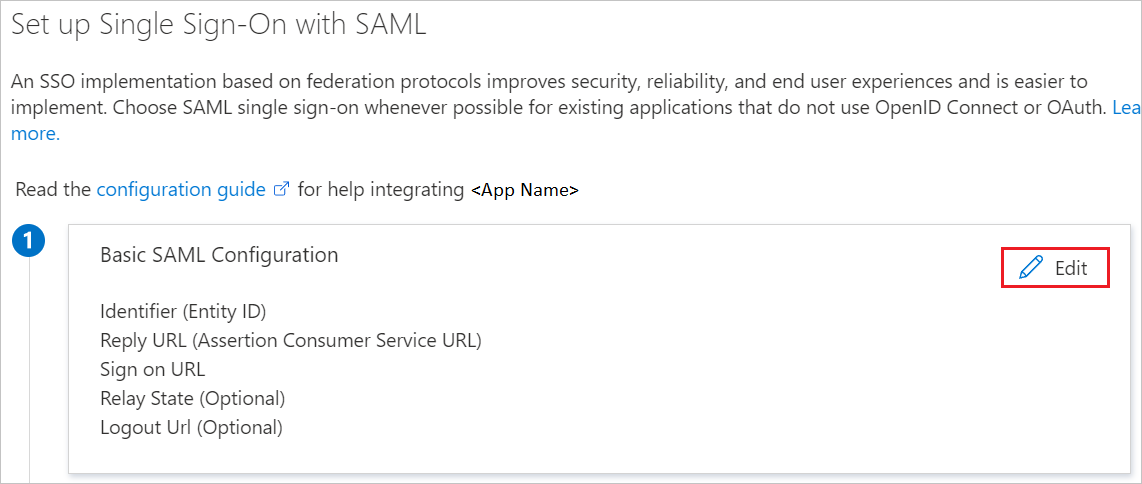
On the Set up Single Sign-On with SAML page, select Edit (the pencil icon) to open the Basic SAML Configuration pane.
In the Basic SAML Configuration pane, do the following steps:
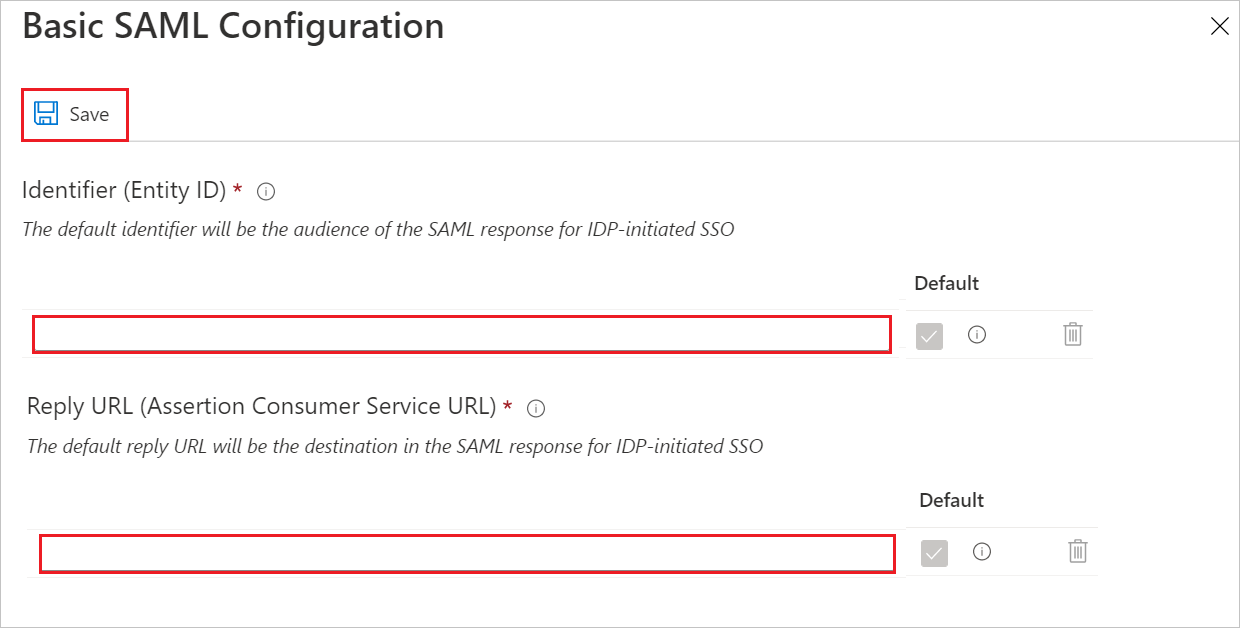
In the Identifier (Entity ID) box, enter a URL:
https://www.itcdataservices.comIn the Reply URL (Assertion Consumer Service URL) box, enter a URL by using the following pattern:
Environment URL Test https://ratingqa.itcdataservices.com/webservices/imp/saml/loginLive https://www.itcratingservices.com/webservices/imp/saml/login
Note
These values aren't real. Update these values with the actual identifier and reply URL. To get these values, contact the TurboRater support team. You can also refer to the patterns shown in the Basic SAML Configuration pane.
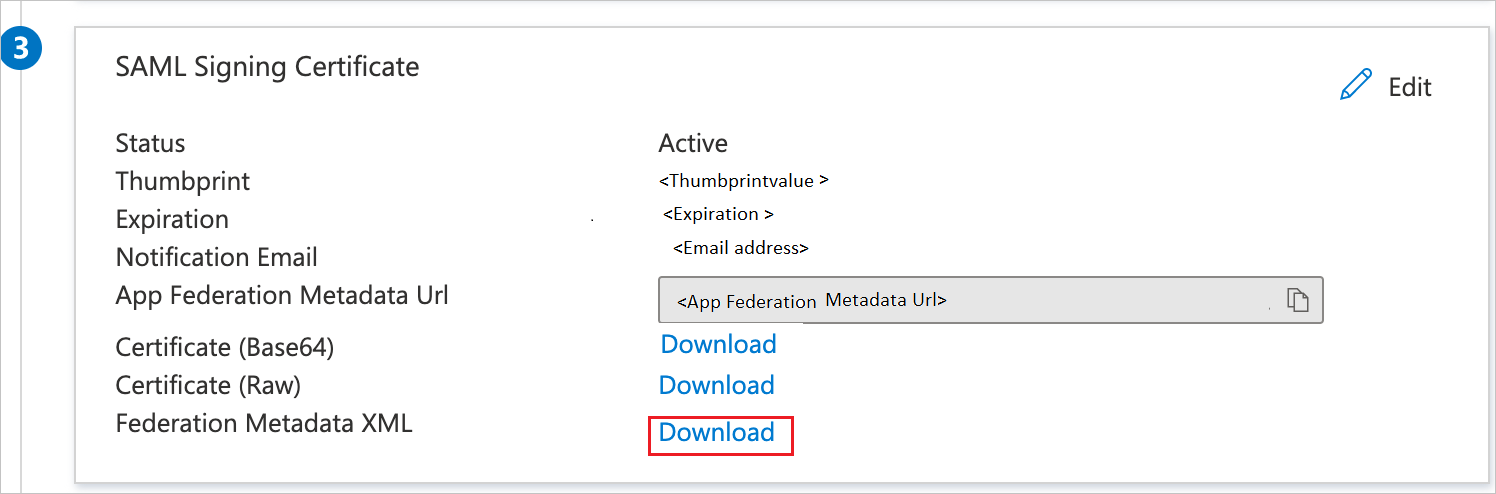
On the Set up Single Sign-On with SAML pane, in the SAML Signing Certificate section, select Download to download the Federation Metadata XML from the given options and save it on your computer.
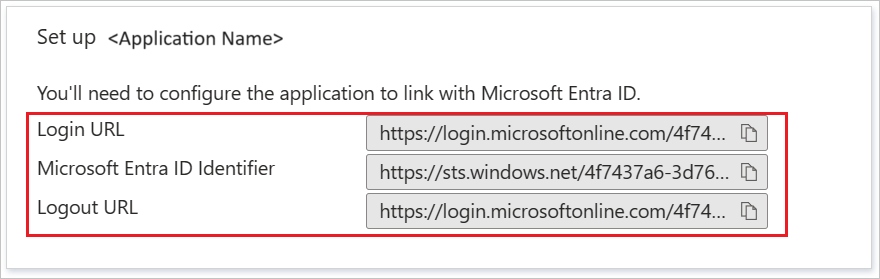
In the Set up TurboRater section, copy the URL or URLs that you need:
- Login URL
- Microsoft Entra Identifier
- Logout URL
Configure TurboRater single sign-on
To configure single sign-on on the TurboRater side, you need to send the downloaded Federation Metadata XML and the appropriate copied URLs to the TurboRater support team. The TurboRater team will make sure the SAML SSO connection is set properly on both sides.
Create a Microsoft Entra test user
In this section, you create a test user named Britta Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Entra ID > Users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
Assign the Microsoft Entra test user
In this section, you enable B. Simon to use Azure single sign-on by granting their access to TurboRater.
Browse to Entra ID > Enterprise apps > TurboRater.
In the applications list, select TurboRater.
In the left pane, under MANAGE, select Users and groups.
Select + Add user, and then select Users and groups in the Add Assignment pane.
In the Users and groups pane, select B. Simon in the Users list, and then choose Select at the bottom of the pane.
If you're expecting a role value in the SAML assertion, then in the Select Role pane, select the appropriate role for the user from the list. At the bottom of the pane, choose Select.
In the Add Assignment pane, select Assign.
Create a TurboRater test user
In this section, you create a user called B. Simon in TurboRater. Work with the TurboRater support team to add B. Simon as a user in TurboRater. Users must be created and activated before you use single sign-on.
Test single sign-on
In this section, you test your Microsoft Entra single sign-on configuration by using the My Apps portal.
When you select TurboRater in the My Apps portal, you should be automatically signed in to the TurboRater subscription for which you set up single sign-on. For more information about the My Apps portal, see Access and use apps on the My Apps portal.