Add a service principal to the server administrator role
To automate unattended PowerShell tasks, a service principal must have server administrator privileges on the Analysis Services server being managed. This article describes how to add a service principal to the server administrators role on an Analysis Services server. You can do this using SQL Server Management Studio or a Resource Manager template.
Note
Service principals must be added directly to the server administrator role. Adding a service principal to a security group, and then adding that security group to the server administrator role is not supported.
Before you begin
Before completing this task, you must have a service principal registered in Microsoft Entra ID.
Create service principal - Azure portal
Create service principal - PowerShell
Using SQL Server Management Studio
You can configure server administrators using SQL Server Management Studio (SSMS). To complete this task, you must have server administrator permissions on the Analysis Services server.
In SSMS, connect to your Analysis Services server.
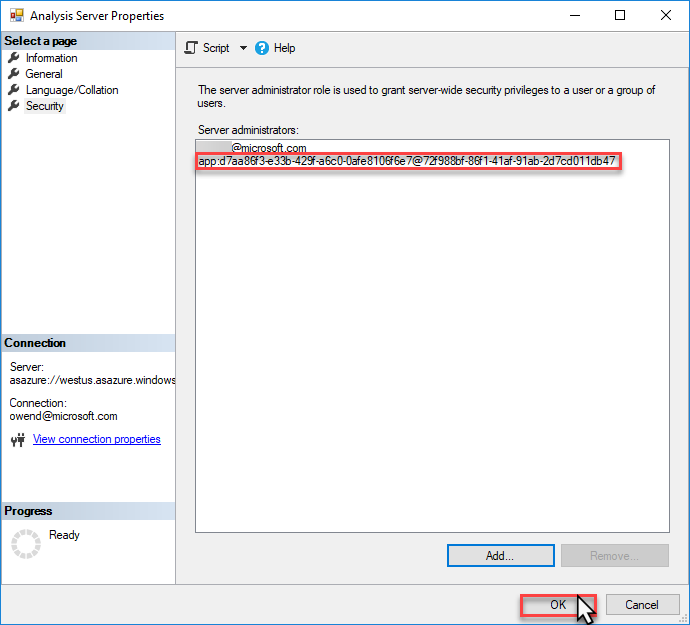
In Server Properties > Security, click Add.
In Select a User or Group, search for your registered app by name, select, and then click Add.
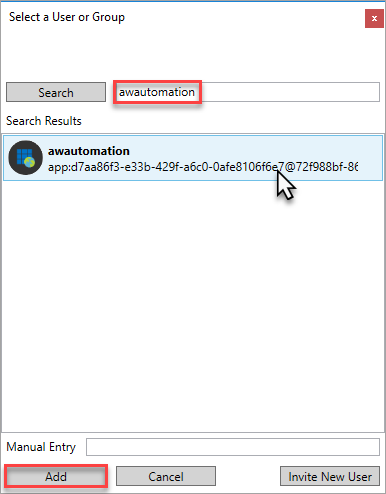
Verify the service principal account ID, and then click OK.
Using a Resource Manager template
You can also configure server administrators by deploying the Analysis Services server using an Azure Resource Manager template. The identity running the deployment must belong to the Contributor role for the resource in Azure role-based access control (Azure RBAC).
Important
The service principal must be added using the format app:{service-principal-client-id}@{azure-ad-tenant-id}.
The following Resource Manager template deploys an Analysis Services server with a specified service principal added to the Analysis Services Admin role:
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"analysisServicesServerName": {
"type": "string"
},
"location": {
"type": "string"
},
"analysisServicesSkuName": {
"type": "string"
},
"analysisServicesCapacity": {
"type": "int"
},
"servicePrincipalClientId": {
"type": "string"
},
"servicePrincipalTenantId": {
"type": "string"
}
},
"resources": [
{
"name": "[parameters('analysisServicesServerName')]",
"type": "Microsoft.AnalysisServices/servers",
"apiVersion": "2017-08-01",
"location": "[parameters('location')]",
"sku": {
"name": "[parameters('analysisServicesSkuName')]",
"capacity": "[parameters('analysisServicesCapacity')]"
},
"properties": {
"asAdministrators": {
"members": [
"[concat('app:', parameters('servicePrincipalClientId'), '@', parameters('servicePrincipalTenantId'))]"
]
}
}
}
]
}
Using managed identities
Managed identies that are added to database or server roles will be unable to login to the service or do any operations. Managed identities for service principals are not supported in Azure Analysis Services.
Related information
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for