Configure common credential providers in credential manager
APPLIES TO: All API Management tiers
In this article, you learn about configuring identity providers for managed connections in your API Management instance. Settings for the following common providers are shown:
- Microsoft Entra provider
- Generic OAuth 2.0 provider
You configure a credential provider in your API Management instance's credential manager. For a step-by-step example of configuring a Microsoft Entra provider and connection, see:
Prerequisites
To configure any of the supported providers in API Management, first configure an OAuth 2.0 app in the identity provider that will be used to authorize API access. For configuration details, see the provider's developer documentation.
If you're creating a credential provider that uses the authorization code grant type, configure a Redirect URL (sometimes called Authorization Callback URL or a similar name) in the app. For the value, enter
https://authorization-manager.consent.azure-apim.net/redirect/apim/<YOUR-APIM-SERVICENAME>.Depending on your scenario, configure app settings such as scopes (API permissions).
Minimally, retrieve the following app credentials that will be configured in API Management: the app's client ID and client secret.
Depending on the provider and your scenario, you might need to retrieve other settings such as authorization endpoint URLs or scopes.
Microsoft Entra provider
API credential manager supports the Microsoft Entra identity provider, which is the identity service in Microsoft Azure that provides identity management and access control capabilities. It allows users to securely sign in using industry-standard protocols.
- Supported grant types: authorization code, client credentials
Note
Currently, the Microsoft Entra credential provider supports only the Azure AD v1.0 endpoints.
Microsoft Entra provider settings
| Property | Description | Required | Default |
|---|---|---|---|
| Provider name | Name of credential provider resource in API Management | Yes | N/A |
| Identity provider | Select Azure Active Directory v1 | Yes | N/A |
| Grant type | The OAuth 2.0 authorization grant type to use Depending on your scenario, select either Authorization code or Client credentials. |
Yes | Authorization code |
| Authorization URL | https://graph.microsoft.com |
Yes | N/A |
| Client ID | The application (client) ID used to identify the Microsoft Entra app | Yes | N/A |
| Client secret | The client secret used for the Microsoft Entra app | Yes | N/A |
| Login URL | The Microsoft Entra login URL | No | https://login.windows.net |
| Resource URL | The URL of the resource that requires authorization Example: https://graph.microsoft.com |
Yes | N/A |
| Tenant ID | The tenant ID of your Microsoft Entra app | No | common |
| Scopes | One or more API permissions for your Microsoft Entra app, separated by the " " character Example: ChannelMessage.Read.All User.Read |
No | API permissions set in Microsoft Entra app |
Generic OAuth 2.0 providers
You can use two generic providers for configuring connections:
- Generic OAuth 2.0
- Generic OAuth 2.0 with PKCE
A generic provider allows you to use your own OAuth 2.0 identity provider based on your specific needs.
Note
We recommend using the generic OAuth 2.0 with PKCE provider for improved security if your identity provider supports it. Learn more
- Supported grant types: authorization code, client credentials
Generic credential provider settings
| Property | Description | Required | Default |
|---|---|---|---|
| Provider name | Name of credential provider resource in API Management | Yes | N/A |
| Identity provider | Select Generic Oauth 2 or Generic Oauth 2 with PKCE. | Yes | N/A |
| Grant type | The OAuth 2.0 authorization grant type to use Depending on your scenario and your identity provider, select either Authorization code or Client credentials. |
Yes | Authorization code |
| Authorization URL | The authorization endpoint URL | No | UNUSED |
| Client ID | The ID used to identify an app to the identity provider's authorization server | Yes | N/A |
| Client secret | The secret used by the app to authenticate with the identity provider's authorization server | Yes | N/A |
| Refresh URL | The URL that your app makes a request to in order to exchange a refresh token for a renewed access token | No | UNUSED |
| Token URL | The URL on the identity provider's authorization server that is used to programmatically request tokens | Yes | N/A |
| Scopes | One or more specific actions the app is allowed to do or information that it can request on a user's behalf from an API, separated by the " " character Example: user web api openid |
No | N/A |
Other identity providers
API Management supports several providers for popular SaaS offerings, including GitHub, LinkedIn, and others. You can select from a list of these providers in the Azure portal when you create a credential provider.
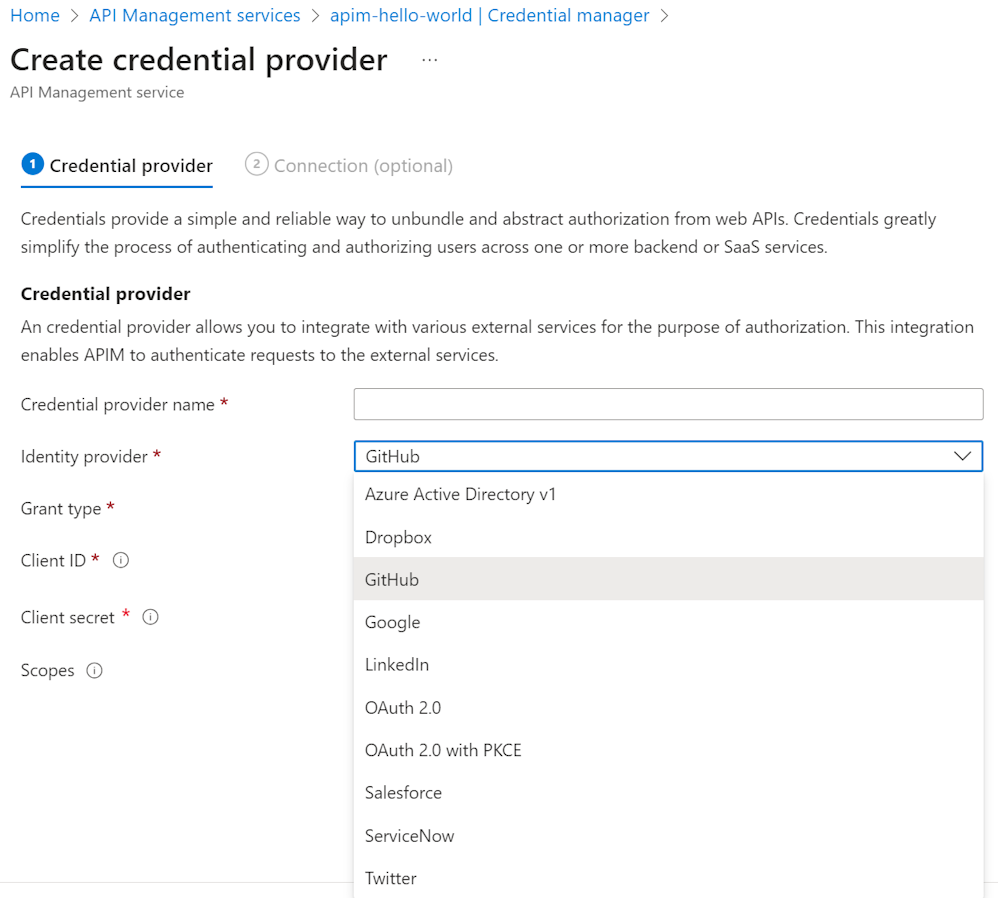
Supported grant types: authorization code, client credentials (depends on provider)
Required settings for these providers differ from provider to provider but are similar to those for the generic OAuth 2.0 providers. Consult the developer documentation for each provider.
Related content
- Learn more about managing connections in API Management.
- Create a connection for Microsoft Entra ID or GitHub.