Continuous deployment to Azure App Service
Azure App Service enables continuous deployment from GitHub, Bitbucket, and Azure Repos repositories by pulling in the latest updates.
Prepare your repository
To get automated builds from Azure App Service build server, make sure that your repository root has the correct files in your project.
| Runtime | Root directory files |
|---|---|
| ASP.NET (Windows only) | *.sln, *.csproj, or default.aspx |
| ASP.NET Core | *.sln or *.csproj |
| PHP | index.php |
| Ruby (Linux only) | Gemfile |
| Node.js | server.js, app.js, or package.json with a start script |
| Python | *.py, requirements.txt, or runtime.txt |
| HTML | default.htm, default.html, default.asp, index.htm, index.html, or iisstart.htm |
| WebJobs | <job_name>/run.<extension> under App_Data/jobs/continuous for continuous WebJobs, or App_Data/jobs/triggered for triggered WebJobs. For more information, see Kudu WebJobs documentation. |
| Functions | See Continuous deployment for Azure Functions. |
To customize your deployment, include a .deployment file in the repository root. For more information, see Customize deployments and Custom deployment script.
Note
If you use Visual Studio, let Visual Studio create a repository for you. Your project will immediately be ready for deployment via Git.
Configure the deployment source
In the Azure portal, go to the management page for your App Service app.
In the left pane, select Deployment Center. Then select Settings.
In the Source box, select one of the CI/CD options:
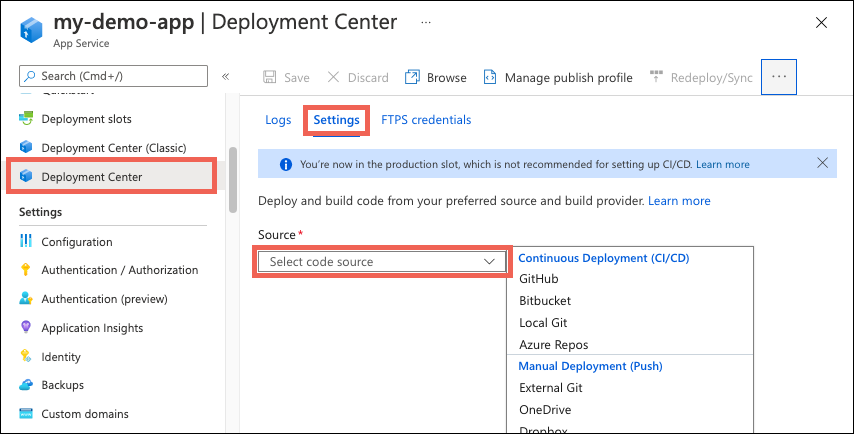
Select the tab that corresponds to your build provider to continue.
GitHub Actions is the default build provider. To change the provider, select Change provider > App Service Build Service > OK.
If you're deploying from GitHub for the first time, select Authorize and follow the authorization prompts. If you want to deploy from a different user's repository, select Change Account.
After you authorize your Azure account with GitHub, select the Organization, Repository, and Branch you want.
If you can’t find an organization or repository, you might need to enable more permissions on GitHub. For more information, see Managing access to your organization's repositories.
Under Authentication type, select User-assigned identity for better security. For more information, see frequently asked questions.
Note
If your Azure account has the required permissions for the User-assigned identity option, Azure creates a user-assigned managed identity for you. If you don't, work with your Azure administrator to create an identity with the required role on your app, then select it here in the dropdown.
(Optional) To see the file before saving your changes, select Preview file. App Service selects a workflow template based on the language stack setting of your app and commits it into your selected GitHub repository.
Select Save.
New commits in the selected repository and branch now deploy continuously into your App Service app. You can track the commits and deployments on the Logs tab.
Disable continuous deployment
In the Azure portal, go to the management page for your App Service app.
In the left pane, select Deployment Center. Then select Settings > Disconnect:
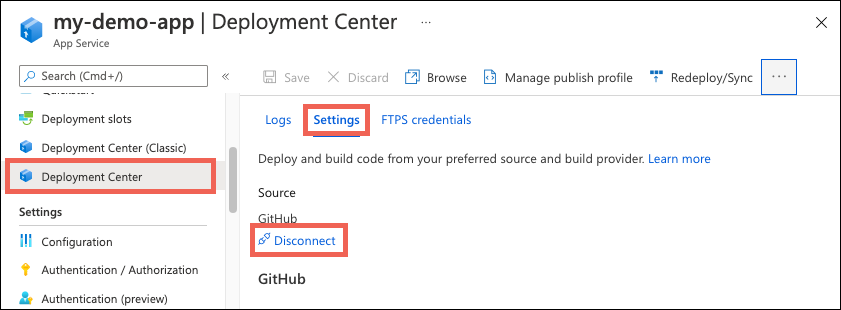
By default, the GitHub Actions workflow file is preserved in your repository, but it continues to trigger deployment to your app. To delete the file from your repository, select Delete workflow file.
Select OK.
What are the build providers?
Depending on your deployment source in the Deployment Center, you might see a few options to select for build providers. Build providers help you build a CI/CD solution with Azure App Service by automating build, test, and deployment.
You're not limited to the build provider options found in the Deployment Center, but App Service lets you set them up quickly and offers some integrated deployment logging experience.
The GitHub Actions build provider is available only for GitHub deployment. When configured from the app's Deployment Center, it completes these actions to set up CI/CD:
- Deposits a GitHub Actions workflow file into your GitHub repository to handle build and deploy tasks to App Service.
- For basic authentication, adds the publish profile for your app as a GitHub secret. The workflow file uses this secret to authenticate with App Service.
- For user-assigned identity, see What does the user-assigned identity option do for GitHub Actions?
- Captures information from the workflow run logs and displays it on the Logs tab in the Deployment Center.
You can customize the GitHub Actions build provider in these ways:
- Customize the workflow file after it's generated in your GitHub repository. For more information, see Workflow syntax for GitHub Actions. Just make sure that the workflow deploys to App Service with the azure/webapps-deploy action.
- If the selected branch is protected, you can still preview the workflow file without saving the configuration and then manually add it into your repository. This method doesn't give you log integration with the Azure portal.
- Instead of using basic authentication or a user-assigned identity, you can also deploy by using a service principal in Microsoft Entra ID. This can't be configured in the portal.
What happens to my app during deployment?
All the officially supported deployment methods make changes to the files in the /home/site/wwwroot folder of your app. These files are used to run your app. So the deployment can fail because of locked files. The app might also behave unpredictably during deployment because the files aren't all updated at the same time. This behavior is undesirable for a customer-facing app. There are a few ways to avoid these issues:
- Run your app directly from the ZIP package, without unpacking it.
- Stop your app or enable offline mode for it during deployment. For more information, see Deal with locked files during deployment.
- Deploy to a staging slot with auto swap turned on.
Frequently asked questions
- Does the GitHub Actions build provider work with basic authentication if basic authentication is disabled?
- What does the user-assigned identity option do for GitHub Actions?
- Why do I see the error, "This identity does not have write permissions on this app. Please select a different identity, or work with your admin to grant the Website Contributor role to your identity on this app"?
- Why do I see the error, "This identity does not have write permissions on this app. Please select a different identity, or work with your admin to grant the Website Contributor role to your identity on this app"?
Does the GitHub Actions build provider work with basic authentication if basic authentication is disabled?
No. Try using GitHub Actions with the user-assigned identity option.
For more information, see Deployment without basic authentication.
What does the user-assigned identity option do for GitHub Actions?
When you select user-assigned identity under the GitHub Actions source, App Service configures all the necessary resources in Azure and in GitHub to enable the recommended OpenID Connect authentication with GitHub Actions.
Specifically, App Service does the following operations:
- Creates a federated credential between a user-assigned managed identity in Azure and your selected repository and branch in GitHub.
- Creates the secrets
AZURE_CLIENT_ID,AZURE_TENANT_ID, andAZURE_SUBSCRIPTION_IDfrom the federated credential in your selected GitHub repository. - Assigns the identity to your app.
In a GitHub Actions workflow in your GitHub repository, you can then use the Azure/login action to authenticate with your app by using OpenID Connect. For examples, see Add the workflow file to your GitHub repository.
If your Azure account has the required permissions, App Service creates a user-assigned managed identity and configures it for you. This identity isn't shown in the Identities page of your app. If your Azure account doesn't have the required permissions, you must select an existing identity with the required role.
Why do I see the error, "You do not have sufficient permissions on this app to assign role-based access to a managed identity and configure federated credentials"?
The message indicates that your Azure account doesn't have the required permissions to create a user-assigned managed identity for the GitHub Actions. The required permissions (scoped to your app) are:
Microsoft.Authorization/roleAssignments/writeMicrosoft.ManagedIdentity/userAssignedIdentities/write
By default, the User Access Administrator role and Owner role have these permissions already, but the Contributor role doesn't. If you don't have the required permissions, work with your Azure administrator to create a user-assigned managed identity with the Website Contributor role. In the Deployment Center, you can then select the identity in the GitHub > Identity dropdown.
For more information on the alternative steps, see Deploy to App Service using GitHub Actions.
Why do I see the error, "This identity does not have write permissions on this app. Please select a different identity, or work with your admin to grant the Website Contributor role to your identity on this app"?
The message indicates that the selected user-assigned managed identity doesn't have the required role to enable OpenID Connect between the GitHub repository and the App Service app. The identity must have one of the following roles on the app: Owner, Contributor, Websites Contributor. The least privileged role that the identity needs is Websites Contributor.
More resources
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for