Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article provides an overview of the design areas in the Azure landing zone architecture for Azure Virtual Desktop. It targets architects and technical decision-makers. Use this guidance to quickly gain an understanding of the Virtual Desktop landing zone reference implementation.
Landing zone concepts
An Azure landing zone is an environment that follows key design principles across eight design areas. These design principles accommodate all application portfolios and enable application migration, modernization, and innovation at scale. An Azure landing zone uses subscriptions to isolate and scale application resources and platform resources.
An Azure landing zone provides the necessary foundation for cloud workloads such as Virtual Desktop. It defines essential components like governance, security, networking, identity, and operations. To host and manage services at scale, you need all these components.
Types of landing zones
Azure landing zones have two categories:
Platform landing zones provide shared foundational services like networking, identity management, and resource governance. Platform landing zones form the core infrastructure that supports application workloads.
Application landing zones host specific applications, workloads, or services. They provide the necessary environment to run applications. Policies and management groups enforce governance in application landing zones.
Reference architecture
The Virtual Desktop reference architecture is a proven architecture for running Virtual Desktop in an application landing zone. Start with this architecture for Virtual Desktop deployments.
The landing zone architecture for Virtual Desktop is part of the Virtual Desktop scenario article series in the Cloud Adoption Framework for Azure. This series describes compatibility requirements, design principles, and deployment guidance for the landing zone.
When you design Virtual Desktop to run from an application landing zone, follow this structured architecture to ensure scalability, security, and operational excellence. This architecture provides a robust foundation to deploy Virtual Desktop at scale while maintaining centralized governance, security, and performance.
Benefits of this reference architecture
Scalability: Supports large-scale deployments so that you can quickly scale resources based on demand
Security: Uses security measures like Azure role-based access control (Azure RBAC) and network security to protect your environment from threats
Operational efficiency: Includes automation and monitoring tools to reduce operational burden and improve system performance
Download a Visio file of this architecture.
Design areas
The letters "A" through "I" in the diagram indicate design areas for the Virtual Desktop landing zone. This diagram shows the hierarchy of resource organization.
| Legend | Design area | Objective |
|---|---|---|
| A | Azure billing and Active Directory tenant | Set up the tenant, enrollment, and billing configuration early on. |
| B | Identity and access management | Establish secure access to Virtual Desktop through Microsoft Entra ID, conditional access, and Azure RBAC. Identity and access management is a primary security boundary in the public cloud. It serves as the foundation of secure and fully compliant architectures. |
| C | Resource organization | Design subscriptions and management group hierarchies to support governance, operations management, and adoption patterns at scale. |
| D, G, H | Management and monitoring | Create a baseline that ensures operational visibility, compliance, and the ability to protect and recover workloads. |
| E | Network topology and connectivity | Design reliable and scalable network architecture as a foundational element of the cloud environment. |
| F | Security | Apply security controls directly within the Virtual Desktop workload. |
| G, F | Business continuity and disaster recovery | Create business continuity and disaster recovery strategies for Virtual Desktop and its supporting services to ensure resilience and recovery. This area isn't explicitly labeled in the diagram but is represented within sections G and F. |
| I | Platform automation and DevOps | Enable infrastructure as code and continuous integration and continuous delivery (CI/CD) pipelines to manage platform-level resources, management group policies, role definitions, and subscription provisioning. |
Tip
Review the Virtual Desktop design areas to ensure alignment with Virtual Desktop best practices.
Virtual Desktop Azure landing zone design areas: These areas define the foundational elements required to set up the Virtual Desktop deployment in an enterprise-scale environment. They focus on preparing resources like network configurations, identity management, security, and governance. This landing zone helps create a scalable and secure environment for Virtual Desktop workloads.
Virtual Desktop design areas: These areas represent the architectural principles and best practices for designing and operating Virtual Desktop workloads. They cover aspects such as application delivery, infrastructure design, security, and cost optimization. Each area aligns with Azure best practices to ensure an optimal and cost-effective Virtual Desktop implementation.
Design principles
Like other landing zones, the Virtual Desktop landing zone follows the core Azure landing zone design principles and aligns with common design areas.
This architecture uses the following key principles:
Subscription democratization: Teams manage their own resources within a controlled framework.
Policy-driven governance: Centralized policies and controls enforce compliance and governance.
Application-focused service model: The architecture supports organizations structured around applications.
Single control and management plane: Centralized resource management maintains oversight and control.
Reference implementation
The Virtual Desktop application landing zone reference implementation follows the reference architecture and design principles outlined in the Cloud Adoption Framework and the Azure Well-Architected Framework. This solution provides steps to prepare landing zone subscriptions for a scalable Virtual Desktop deployment and to deploy Virtual Desktop within those landing zone subscriptions.
The Virtual Desktop landing zone implementation provides your organization with an enterprise-ready Virtual Desktop deployment that aligns with best practices in scalability, security, and governance.
Architecture
Important
The accelerator deploys resources into the Virtual Desktop application landing zone and shared services landing zone subscriptions.
You must deploy a Cloud Adoption Framework platform landing zone first. This deployment provides the shared foundation services that resources in this implementation require.
Review the Virtual Desktop prerequisites before you start the deployment.
This architecture is based on multiple subscriptions that are each dedicated to specific purposes:
Virtual Desktop subscription: This subscription, or multiple subscriptions depending on environment scale, deploys the Virtual Desktop resources that are specific to individual workloads, not shared across workloads. These resources include virtual machines, storage accounts, key vaults, and private endpoints. This subscription is considered part of the application landing zone.
Virtual Desktop shared services subscription: This subscription hosts all services shared across multiple Virtual Desktop workloads. It includes resources like Azure Automation accounts, data collection rules, Log Analytics workspaces, and Azure compute galleries. This subscription is considered part of the application landing zone.
Platform subscriptions: These foundational subscriptions provide shared services across the entire environment. They support and connect to application landing zone subscriptions.
Management subscription: This subscription is part of the Azure landing zone platform structure and typically hosts shared management resources. These resources include monitoring solutions, update management tools, and governance tools. In this architecture, the management subscription isn't an active dependency for the Virtual Desktop workload. The workload team must implement their own automation, monitoring, and management capabilities within their designated workload subscription.
Connectivity subscription: This subscription contains network-related components like virtual networks, network security groups (NSGs), Azure Firewall, and Azure ExpressRoute or VPN gateways. In this architecture, this subscription provides the Virtual Desktop application landing zone with secure and scalable network infrastructure. This capability enables isolated traffic flows, segmentation between organization workloads, and secure access to cross-premises resources.
Identity subscription: This subscription handles identity and access management services required to support domain-joined Virtual Desktop session hosts. In this architecture, this subscription provides the Virtual Desktop application landing zone with domain services. These services include Microsoft Entra Domain Services or self-managed Active Directory domain controllers hosted in Azure. These services enable session hosts to join a domain and authenticate users securely, enforce group policies, and support legacy authentication scenarios that some applications require.
Download a Visio file of this architecture.
Benefits of this reference implementation
Scalability: It scales efficiently to meet your organization's needs.
Security: It uses enterprise-grade security, compliance, and governance controls to protect your environment.
Faster deployment: It accelerates deployment by using predefined templates, configurations, and best practices.
Best practices compliance: It follows the best practices in the architecture.
Accelerator overview
 The Virtual Desktop landing zone reference implementation supports multiple deployment scenarios depending on your requirements. Each deployment scenario supports both greenfield and brownfield deployments and provides multiple infrastructure as code (IaC) template options:
The Virtual Desktop landing zone reference implementation supports multiple deployment scenarios depending on your requirements. Each deployment scenario supports both greenfield and brownfield deployments and provides multiple infrastructure as code (IaC) template options:
- The Azure portal UI
- The Azure CLI or Azure PowerShell Bicep template
- A Terraform template
The accelerator uses resource naming automation based on the following recommendations:
Before you proceed with the deployment scenarios, familiarize yourself with the accelerator's Azure resource naming, tagging, and organization.
Download a Visio file of the image.
Accelerator deployment
To perform the deployment, do the following steps:
Review the deployment prerequisites. This step helps you ready your environment for the deployment.
Deploy the platform landing zone if you don't already have one. This step sets up the foundational components.
Deploy the Virtual Desktop reference implementation. After the platform landing zone is in place, deploy the Virtual Desktop landing zone reference implementation of the reference architecture.
To start, choose the following deployment scenario that best matches your requirements.
The baseline deployment deploys the Virtual Desktop resources and dependent services required to establish a Virtual Desktop baseline.
This deployment scenario includes the following items:
Virtual Desktop resources, including a workspace, scaling plan, host pool, application groups, session host virtual machines, and optionally, private endpoints
An Azure Files share integrated with your identity service
Azure Key Vault for secret, key, and certificate management
Optionally, a new Azure Virtual Network that includes baseline NSGs, application security groups (ASGs), and route tables
Optionally, Azure Storage account and Key Vault private endpoints and private Domain Name System (DNS) zones
When you're ready for deployment, do the following steps:
Follow the Baseline Deployment Guide for details about prerequisites, planning information, and deployment components.
Optionally, review the Custom image build deployment tab to build an updated image for your Virtual Desktop host sessions.
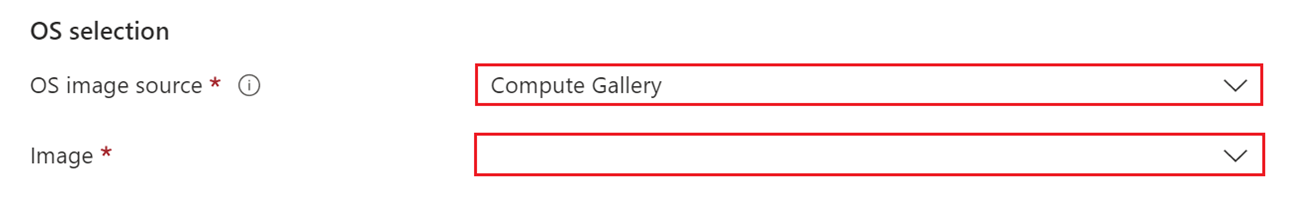
Do the baseline deployment steps. If you created a custom Azure Compute Gallery image in the previous step, on the Session hosts page, choose Compute Gallery as the OS selection source. Then select the correct Image.
Next steps
To build on the concepts from this design guide, explore the following Microsoft Learn resources:
Enterprise-scale support for Virtual Desktop landing zone accelerator: Learn how to deploy a Virtual Desktop landing zone by using IaC accelerators that align with the Cloud Adoption Framework.
Network topology and connectivity for Virtual Desktop: Explore recommended network designs, including hub-and-spoke topology, hybrid connectivity, RDP Shortpath, and security best practices for Virtual Desktop.
Security, governance, and compliance for Virtual Desktop: Understand how to implement security controls, Azure RBAC, monitoring, and governance to ensure the security and compliance of your Virtual Desktop environment.