Build the second layer of defense with Microsoft Defender XDR Security services
Solution ideas
This article describes a solution idea. Your cloud architect can use this guidance to help visualize the major components for a typical implementation of this architecture. Use this article as a starting point to design a well-architected solution that aligns with your workload's specific requirements.
Many organizations operate in a hybrid environment, with resources hosted both on Azure and on-premises. Most Azure resources, such as virtual machines (VMs), Azure applications, and Microsoft Entra ID, can be secured using Azure’s built-in security services.
In addition, organizations frequently subscribe to Microsoft 365 to provide users with applications like Word, Excel, PowerPoint, and Exchange Online. Microsoft 365 also offers security services that can be used to add an extra layer of protection to some of the most widely used Azure resources.
To effectively utilize Microsoft 365 security services, it's important to understand key terminology and the structure of Microsoft 365 services. This fourth article in a series of five explores these topics in greater detail, building on concepts covered in previous articles, particularly:
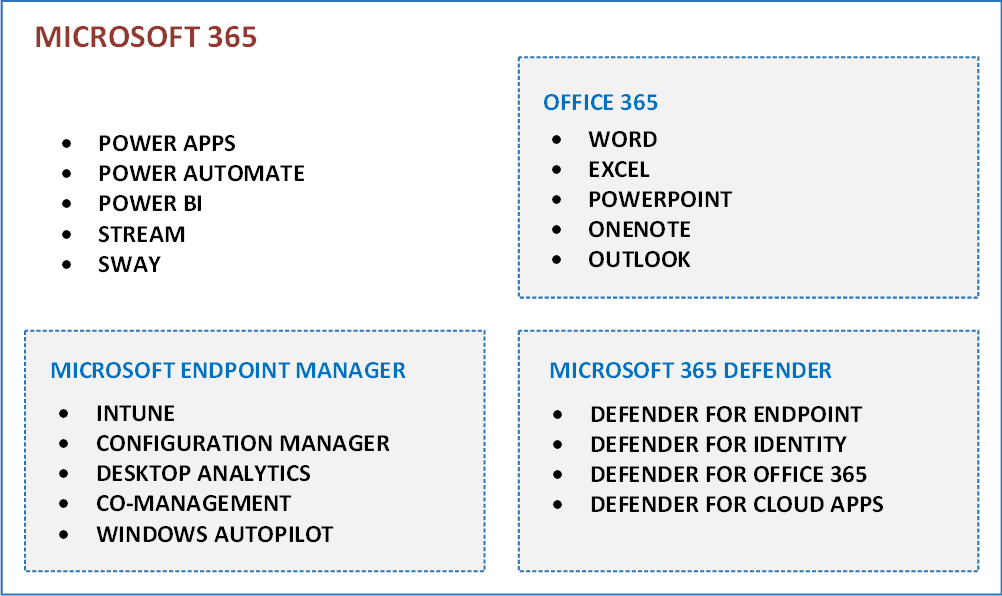
Microsoft 365 and Office 365 are cloud-based services designed to address your organization's needs for strong security, reliability, and enhanced user productivity. Microsoft 365 encompasses services such as Power Automate, Forms, Stream, Sway, and Office 365. Office 365 specifically includes the familiar suite of productivity applications. For more information about subscription options for these two services, see Microsoft 365 and Office 365 plan options.
Depending on the license that you acquire for Microsoft 365, you can also get the security services for Microsoft 365. These security services are called Microsoft Defender XDR, which provides multiple services:
- Microsoft Defender for Endpoint (MDE)
- Microsoft Defender for Identity (MDI)
- Microsoft Defender for Office (MDO)
- Microsoft Defender for Cloud Apps (MDA)
- "Microsoft Defender for Cloud Apps" accessed through "security.microsoft.com" is different from "Microsoft Defender for Cloud" that is another security solution accessed through "portal.azure.com".
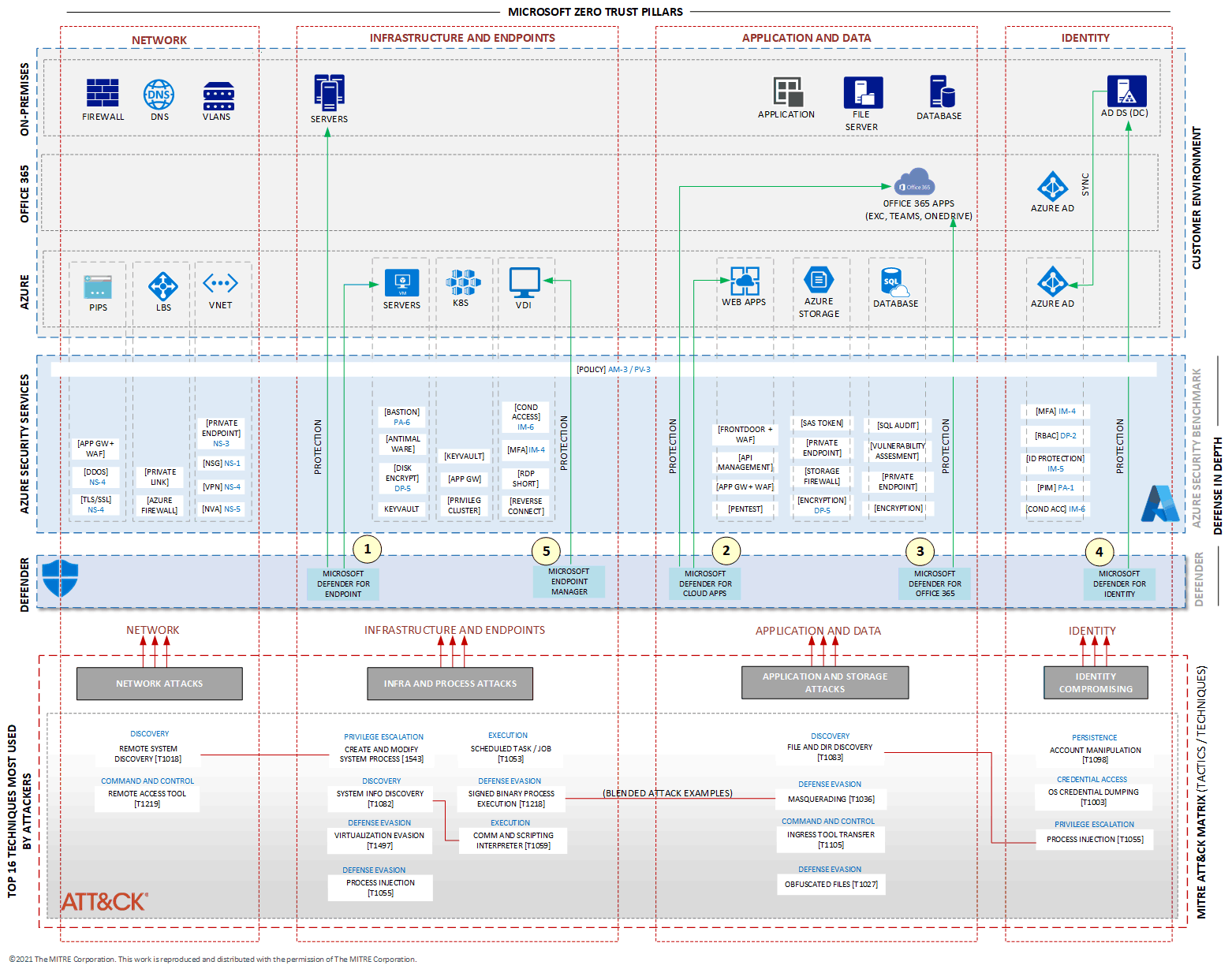
The following diagram illustrates the relationship of solutions and main services that Microsoft 365 offers, though not all services are listed.
Potential use case
People often get confused about Microsoft 365 security services and their role in IT cybersecurity. A major cause of this confusion stems from the similarity in names, including some Azure security services like Microsoft Defender for Cloud (formerly Azure Security Center) and Defender for Cloud Apps (formerly Microsoft Cloud App Security).
However, the confusion goes beyond terminology. Some services provide similar protections but for different resources. For example, Defender for Identity and Azure Identity Protection both safeguard identity services, but Defender for Identity secures on-premises identities (via Active Directory Domain Services and Kerberos authentication), while Azure Identity Protection secures cloud identities (via Microsoft Entra ID and OAuth authentication).
These examples highlight the importance of understanding how Microsoft 365 security services differ from Azure security services. By gaining this understanding, you can more effectively plan your security strategy in the Microsoft cloud while maintaining a strong security posture for your IT environment. This article aims to help you achieve that.
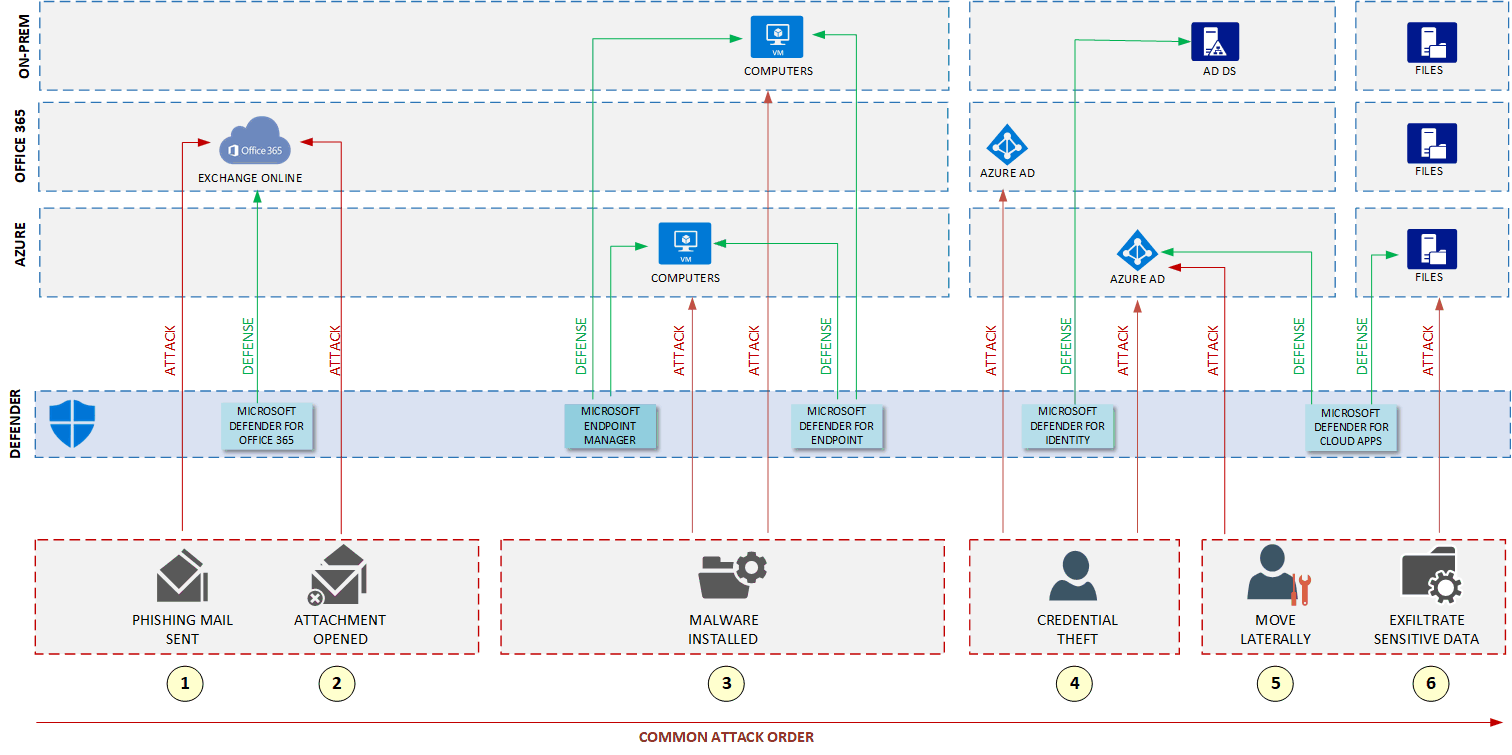
The following diagram presents a real-world use case for Microsoft Defender XDR security services. It shows the resources that need protection, the services running in the environment, and some potential threats. Microsoft Defender XDR services are positioned in the middle, defending the organization's resources from those threats.
Architecture
Microsoft's Extended Detection and Response (XDR) solution, known as Microsoft Defender XDR, integrates multiple security tools and services to provide unified protection, detection, and response across endpoints, identities, email, applications, and cloud environments. It combines advanced threat intelligence, automation, and AI-driven analytics to detect and respond to sophisticated cyber threats in real-time, enabling security teams to quickly mitigate risks and reduce the impact of attacks. By consolidating security data from various sources, Microsoft Defender XDR helps organizations achieve comprehensive, streamlined defense across their entire IT infrastructure.
The following diagram shows a layer, labeled as DEFENDER, that represents the Microsoft Defender XDR security services. Adding these services to your IT environment helps you to build better defense for your environment. The services in the Defender layer can work with Azure security services.
Download a Visio file of this architecture.
©2021 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.
Workflow
Microsoft Defender for Endpoint
Defender for Endpoint secures endpoints in your enterprise and is designed to help networks prevent, detect, investigate, and respond to advanced threats. It creates a layer of protection for VMs that run on Azure and on-premises. For more information about what it can protect, see Microsoft Defender for Endpoint.
Microsoft Defender for Cloud Apps
Formerly known as Microsoft Cloud Application Security, Defender for Cloud Apps is a cloud access security broker (CASB) that supports multiple deployment modes. Those modes include log collection, API connectors, and reverse proxy. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your Microsoft and third-party cloud services. It provides protection and risk mitigation for Cloud Apps and even for some apps that run on-premises. It also provides a protection layer for users who access those apps. For more information, see Microsoft Defender for Cloud Apps overview.
It's important to not confuse Defender for Cloud Apps with Microsoft Defender for Cloud, which provides recommendations and a score of the security posture of servers, apps, storage accounts, and other resources running in Azure, on-premises, and in other clouds. Defender for Cloud consolidates two previous services, Azure Security Center and Azure Defender.
Microsoft Defender for Office
Defender for Office 365 safeguards your organization against malicious threats that are posed by email messages, links (URLs), and collaboration tools. It provides protection for email and collaboration. Depending on the license, you're able to add post-breach investigation, hunting, and response, as well as automation and simulation (for training). For more information about licensing options, see Microsoft Defender for Office 365 security overview.
Microsoft Defender for Identity
Defender for Identity is a cloud-based security solution that uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions that are directed at your organization. It protects Active Directory Domain Services (AD DS) that run on-premises. Even though this service runs on the cloud, it works to protect identities on-premises. Defender for Identity was formerly named Azure Advanced Threat Protection. For more information, see What is Microsoft Defender for Identity?
If you need protection for identities that are provided by Microsoft Entra ID and that runs natively on the cloud, consider Microsoft Entra ID Protection.
Intune (formerly part of the Microsoft Endpoint Manager
Microsoft Intune is a cloud-based service that helps organizations manage and secure their devices, apps, and data. It allows IT administrators to control how company devices such as laptops, smartphones, and tablets are used, ensuring compliance with security policies. With Intune, you can enforce device configurations, deploy software, manage mobile applications, and protect corporate data by using features like Conditional Access and remote wipe. It is particularly useful for enabling secure remote work, managing both corporate-owned and personal (BYOD) devices, and ensuring data security across diverse platforms like Windows, iOS, Android, and macOS.
Another service that was part of Endpoint Manager is the Configuration Manager, an on-premises management solution that allows you to manage client and server computers that are on your network, connected directly or via the internet. You can enable cloud functionality to integrate Configuration Manager with Intune, Microsoft Entra ID, Defender for Endpoint, and other cloud services. Use it to deploy apps, software updates, and operating systems. You can also monitor compliance, query for objects, act on clients in real time, and much more. To learn about all the services that are available, see Microsoft Endpoint Manager overview.
Attack order of example threats
The threats named in the diagram follow a common attack order:
An attacker sends a phishing email with malware attached to it.
An end user opens the attached malware.
The malware installs in the back end without the user noticing.
The installed malware steals some users' credentials.
The attacker uses the credentials to gain access to sensitive accounts.
If the credentials provide access to an account that has elevated privilege, the attacker compromises additional systems.
The diagram also shows in the layer labeled as DEFENDER which Microsoft Defender XDR services can monitor and mitigate those attacks. This is an example of how Defender provides an additional layer of security that works with Azure security services to offer additional protection of the resources that are shown in the diagram. For more information about how potential attacks threaten your IT environment, see the second article in this series, Map threats to your IT environment. For more information about Microsoft Defender XDR, see Microsoft Defender XDR.
Access and manage Microsoft Defender XDR Security services
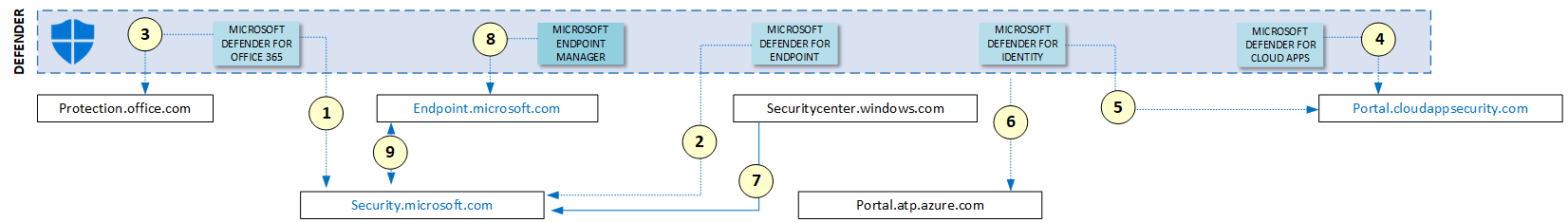
The following diagram shows which portals are currently available and their relationships with each other. In the time of the update for this articles, some of those portals may be already deprecated.
Security.microsoft.com is currently the most important portal available because it brings functionalities from Microsoft Defender for Office 365 (1), from Defender for Endpoint (2), from Defender for Office (3), Defender for Identity (5), Defender for Apps (4) and also for Microsoft Sentinel.
It is important to mention that Microsoft Sentinel has some features that still run only on the Azure Portal (portal.azure.com).
Lastly, endpoint.microsoft.com provides functionality mainly for Intune and Configuration Manager, but also for other services that are part of Endpoint Manager. Because security.microsoft.com and endpoint.microsoft.com deliver security protection for endpoints, they have many interactions between them (9) to offer a great security posture for your endpoints.
Components
The example architecture in this article uses the following Azure components:
Microsoft Entra ID is a cloud-based identity and access management service. Microsoft Entra ID helps your users to access external resources, such as Microsoft 365, the Azure portal, and thousands of other SaaS applications. It also helps them access internal resources, like apps on your corporate intranet network.
Azure Virtual Network is the fundamental building block for your private network in Azure. Virtual Network enables many types of Azure resources to securely communicate with each other, the internet, and on-premises networks. Virtual Network provides a virtual network that benefits from Azure's infrastructure, such as scale, availability, and isolation.
Azure Load Balancer is a high-performance, low-latency Layer 4 load-balancing service (inbound and outbound) for all UDP and TCP protocols. It's built to handle millions of requests per second while ensuring that your solution is highly available. Azure Load Balancer is zone-redundant, ensuring high availability across Availability Zones.
Virtual machines are one of several types of on-demand, scalable computing resources that Azure offers. An Azure virtual machine (VM) gives you the flexibility of virtualization without having to buy and maintain the physical hardware that runs it.
Azure Kubernetes service (AKS) is a fully managed Kubernetes service for deploying and managing containerized applications. AKS provides serverless Kubernetes, continuous integration/continuous delivery (CI/CD), and enterprise-grade security and governance.
Azure Virtual Desktop is a desktop and app virtualization service that runs on the cloud to provide desktops for remote users.
Web Apps is an HTTP-based service for hosting web applications, REST APIs, and mobile back ends. You can develop in your favorite language, and applications run and scale with ease on both Windows and Linux-based environments.
Azure Storage is highly available, massively scalable, durable, and secure storage for various data objects in the cloud, including object, blob, file, disk, queue, and table storage. All data written to an Azure storage account is encrypted by the service. Azure Storage provides you with fine-grained control over who has access to your data.
Azure SQL Database is a fully managed PaaS database engine that handles most of the database management functions such as upgrading, patching, backups, and monitoring. It provides these functions without user involvement. SQL Database provides a range of built-in security and compliance features to help your application meet security and compliance requirements.
Contributors
This article is maintained by Microsoft. It was originally written by the following contributors.
Principal author:
- Rudnei Oliveira | Senior Customer Engineer
Other contributors:
- Gary Moore | Programmer/Writer
- Andrew Nathan | Senior Customer Engineering Manager
Next steps
- Defend against threats with Microsoft 365
- Detect and respond to cyber attacks with Microsoft Defender XDR
- Get started with Microsoft Defender XDR
- Implement threat intelligence in Microsoft 365
- Manage security with Microsoft 365
- Protect against malicious threats with Microsoft Defender for Office 365
- Protect on-premises identities with Microsoft Defender for Cloud for Identity
Related resources
For more details about this reference architecture, see the other articles in this series: