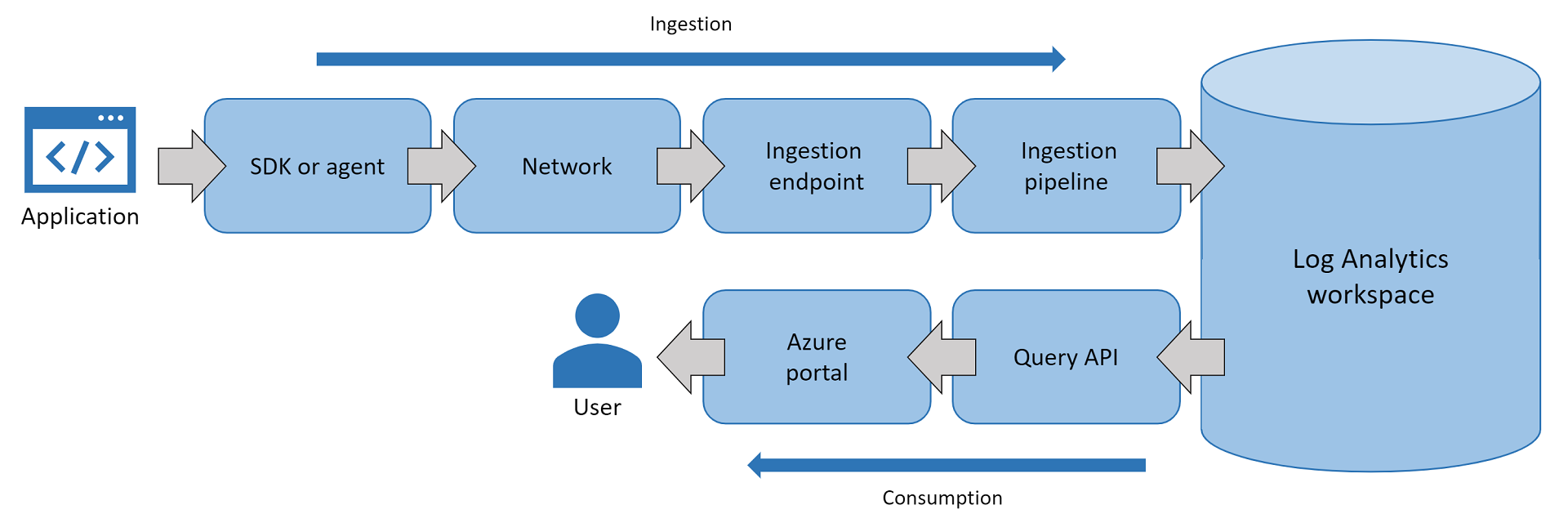
IP addresses used by Azure Monitor
Azure Monitor uses several IP addresses. Azure Monitor is made up of core platform metrics and logs in addition to Log Analytics and Application Insights. You might need to know IP addresses if the app or infrastructure that you're monitoring is hosted behind a firewall.
Note
Although these addresses are static, it's possible that we'll need to change them from time to time. All Application Insights traffic represents outbound traffic with the exception of availability monitoring and webhook action groups, which also require inbound firewall rules.
You can use Azure network service tags to manage access if you're using Azure network security groups. If you're managing access for hybrid/on-premises resources, you can download the equivalent IP address lists as JSON files, which are updated each week. To cover all the exceptions in this article, use the service tags ActionGroup, ApplicationInsightsAvailability, and AzureMonitor.
Outgoing ports
You need to open some outgoing ports in your server's firewall to allow the Application Insights SDK or Application Insights Agent to send data to the portal.
Note
These addresses are listed by using Classless Interdomain Routing notation. As an example, an entry like 51.144.56.112/28 is equivalent to 16 IPs that start at 51.144.56.112 and end at 51.144.56.127.
| Purpose | URL | Type | IP | Ports |
|---|---|---|---|---|
| Telemetry | dc.applicationinsights.azure.com dc.applicationinsights.microsoft.com dc.services.visualstudio.com *.in.applicationinsights.azure.com |
Global Global Global Regional |
443 | |
| Live Metrics | live.applicationinsights.azure.com rt.applicationinsights.microsoft.com rt.services.visualstudio.com {region}.livediagnostics.monitor.azure.com *Example for {region}: westus2 |
Global Global Global Regional |
20.49.111.32/29 13.73.253.112/29 |
443 |
Note
Application Insights ingestion endpoints are IPv4 only.
Application Insights Agent
Application Insights Agent configuration is needed only when you're making changes.
| Purpose | URL | Ports |
|---|---|---|
| Configuration | management.core.windows.net |
443 |
| Configuration | management.azure.com |
443 |
| Configuration | login.windows.net |
443 |
| Configuration | login.microsoftonline.com |
443 |
| Configuration | secure.aadcdn.microsoftonline-p.com |
443 |
| Configuration | auth.gfx.ms |
443 |
| Configuration | login.live.com |
443 |
| Installation | globalcdn.nuget.org, packages.nuget.org ,api.nuget.org/v3/index.json nuget.org, api.nuget.org, dc.services.vsallin.net |
443 |
Availability tests
For more information on availability tests, see Private availability testing.
Application Insights and Log Analytics APIs
| Purpose | URI | IP | Ports |
|---|---|---|---|
| API | api.applicationinsights.ioapi1.applicationinsights.ioapi2.applicationinsights.ioapi3.applicationinsights.ioapi4.applicationinsights.ioapi5.applicationinsights.iodev.applicationinsights.iodev.applicationinsights.microsoft.comdev.aisvc.visualstudio.comwww.applicationinsights.iowww.applicationinsights.microsoft.comwww.aisvc.visualstudio.comapi.loganalytics.io*.api.loganalytics.iodev.loganalytics.iodocs.loganalytics.iowww.loganalytics.io |
20.37.52.188 20.37.53.231 20.36.47.130 20.40.124.0 20.43.99.158 20.43.98.234 13.70.127.61 40.81.58.225 20.40.160.120 23.101.225.155 52.139.8.32 13.88.230.43 52.230.224.237 52.242.230.209 52.173.249.138 52.229.218.221 52.229.225.6 23.100.94.221 52.188.179.229 52.226.151.250 52.150.36.187 40.121.135.131 20.44.73.196 20.41.49.208 40.70.23.205 20.40.137.91 20.40.140.212 40.89.189.61 52.155.118.97 52.156.40.142 23.102.66.132 52.231.111.52 52.231.108.46 52.231.64.72 52.162.87.50 23.100.228.32 40.127.144.141 52.155.162.238 137.116.226.81 52.185.215.171 40.119.4.128 52.171.56.178 20.43.152.45 20.44.192.217 13.67.77.233 51.104.255.249 51.104.252.13 51.143.165.22 13.78.151.158 51.105.248.23 40.74.36.208 40.74.59.40 13.93.233.49 52.247.202.90 |
80,443 |
| Azure Pipeline annotations extension | aigs1.aisvc.visualstudio.com | dynamic | 443 |
Application Insights analytics
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Analytics portal | analytics.applicationinsights.io | dynamic | 80,443 |
| CDN | applicationanalytics.azureedge.net | dynamic | 80,443 |
| Media CDN | applicationanalyticsmedia.azureedge.net | dynamic | 80,443 |
The *.applicationinsights.io domain is owned by the Application Insights team.
Log Analytics portal
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Portal | portal.loganalytics.io | dynamic | 80,443 |
| CDN | applicationanalytics.azureedge.net | dynamic | 80,443 |
The *.loganalytics.io domain is owned by the Log Analytics team.
Application Insights Azure portal extension
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Application Insights extension | stamp2.app.insightsportal.visualstudio.com | dynamic | 80,443 |
| Application Insights extension CDN | insightsportal-prod2-cdn.aisvc.visualstudio.com insightsportal-prod2-asiae-cdn.aisvc.visualstudio.com insightsportal-cdn-aimon.applicationinsights.io |
dynamic | 80,443 |
Application Insights SDKs
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Application Insights JS SDK CDN | az416426.vo.msecnd.net js.monitor.azure.com |
dynamic | 80,443 |
Action group webhooks
You can query the list of IP addresses used by action groups by using the Get-AzNetworkServiceTag PowerShell command.
Action group service tag
Managing changes to source IP addresses can be time consuming. Using service tags eliminates the need to update your configuration. A service tag represents a group of IP address prefixes from a specific Azure service. Microsoft manages the IP addresses and automatically updates the service tag as addresses change, which eliminates the need to update network security rules for an action group.
In the Azure portal under Azure Services, search for Network Security Group.
Select Add and create a network security group:
- Add the resource group name, and then enter Instance details information.
- Select Review + Create, and then select Create.

Go to Resource Group, and then select the network security group you created:
- Select Inbound security rules.
- Select Add.

A new window opens in the right pane:
- Under Source, enter Service Tag.
- Under Source service tag, enter ActionGroup.
- Select Add.

Profiler
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Agent | agent.azureserviceprofiler.net *.agent.azureserviceprofiler.net |
20.190.60.38 20.190.60.32 52.173.196.230 52.173.196.209 23.102.44.211 23.102.45.216 13.69.51.218 13.69.51.175 138.91.32.98 138.91.37.93 40.121.61.208 40.121.57.2 51.140.60.235 51.140.180.52 52.138.31.112 52.138.31.127 104.211.90.234 104.211.91.254 13.70.124.27 13.75.195.15 52.185.132.101 52.185.132.170 20.188.36.28 40.89.153.171 52.141.22.239 52.141.22.149 102.133.162.233 102.133.161.73 191.232.214.6 191.232.213.239 |
443 |
| Portal | gateway.azureserviceprofiler.net | dynamic | 443 |
| Storage | *.core.windows.net | dynamic | 443 |
Snapshot Debugger
Note
Profiler and Snapshot Debugger share the same set of IP addresses.
| Purpose | URI | IP | Ports |
|---|---|---|---|
| Agent | agent.azureserviceprofiler.net *.agent.azureserviceprofiler.net |
20.190.60.38 20.190.60.32 52.173.196.230 52.173.196.209 23.102.44.211 23.102.45.216 13.69.51.218 13.69.51.175 138.91.32.98 138.91.37.93 40.121.61.208 40.121.57.2 51.140.60.235 51.140.180.52 52.138.31.112 52.138.31.127 104.211.90.234 104.211.91.254 13.70.124.27 13.75.195.15 52.185.132.101 52.185.132.170 20.188.36.28 40.89.153.171 52.141.22.239 52.141.22.149 102.133.162.233 102.133.161.73 191.232.214.6 191.232.213.239 |
443 |
| Portal | gateway.azureserviceprofiler.net | dynamic | 443 |
| Storage | *.core.windows.net | dynamic | 443 |
Frequently asked questions
This section provides answers to common questions.
Can I monitor an intranet web server?
Yes, but you need to allow traffic to our services by either firewall exceptions or proxy redirects:
- QuickPulse
https://rt.services.visualstudio.com:443 - ApplicationIdProvider
https://dc.services.visualstudio.com:443 - TelemetryChannel
https://dc.services.visualstudio.com:443
See IP addresses used by Azure Monitor to review our full list of services and IP addresses.
How do I reroute traffic from my server to a gateway on my intranet?
Route traffic from your server to a gateway on your intranet by overwriting endpoints in your configuration. If the Endpoint properties aren't present in your config, these classes use the default values shown in the following ApplicationInsights.config example.
Your gateway should route traffic to our endpoint's base address. In your configuration, replace the default values with http://<your.gateway.address>/<relative path>.
Example ApplicationInsights.config with default endpoints:
<ApplicationInsights>
...
<TelemetryModules>
<Add Type="Microsoft.ApplicationInsights.Extensibility.PerfCounterCollector.QuickPulse.QuickPulseTelemetryModule, Microsoft.AI.PerfCounterCollector">
<QuickPulseServiceEndpoint>https://rt.services.visualstudio.com/QuickPulseService.svc</QuickPulseServiceEndpoint>
</Add>
</TelemetryModules>
...
<TelemetryChannel>
<EndpointAddress>https://dc.services.visualstudio.com/v2/track</EndpointAddress>
</TelemetryChannel>
...
<ApplicationIdProvider Type="Microsoft.ApplicationInsights.Extensibility.Implementation.ApplicationId.ApplicationInsightsApplicationIdProvider, Microsoft.ApplicationInsights">
<ProfileQueryEndpoint>https://dc.services.visualstudio.com/api/profiles/{0}/appId</ProfileQueryEndpoint>
</ApplicationIdProvider>
...
</ApplicationInsights>
Note
ApplicationIdProvider is available starting in v2.6.0.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for