Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Container Insights defaults to managed identity authentication, which has a monitoring agent that uses the cluster's managed identity to send data to Azure Monitor. It replaced the legacy certificate-based local authentication and removed the requirement of adding a Monitoring Metrics Publisher role to the cluster.
This article describes how to migrate to managed identity authentication if you enabled Container insights using legacy authentication method and also how to enable legacy authentication if you have that requirement.
Important
If you have a cluster with legacy authentication and Log Analytics workspace keys are rotated, then monitoring data will stop flowing to the Log Analytics workspace. You must disable and then reenable the Container insights addon to get monitoring data to start flowing again with the new rotated workspace keys. You should migrate to Container insights managed identity authentication which doesn't use Log Analytics workspace keys.
Migrate to managed identity authentication
If you enabled Container insights before managed identity authentication was available, you can use the following methods to migrate your clusters.
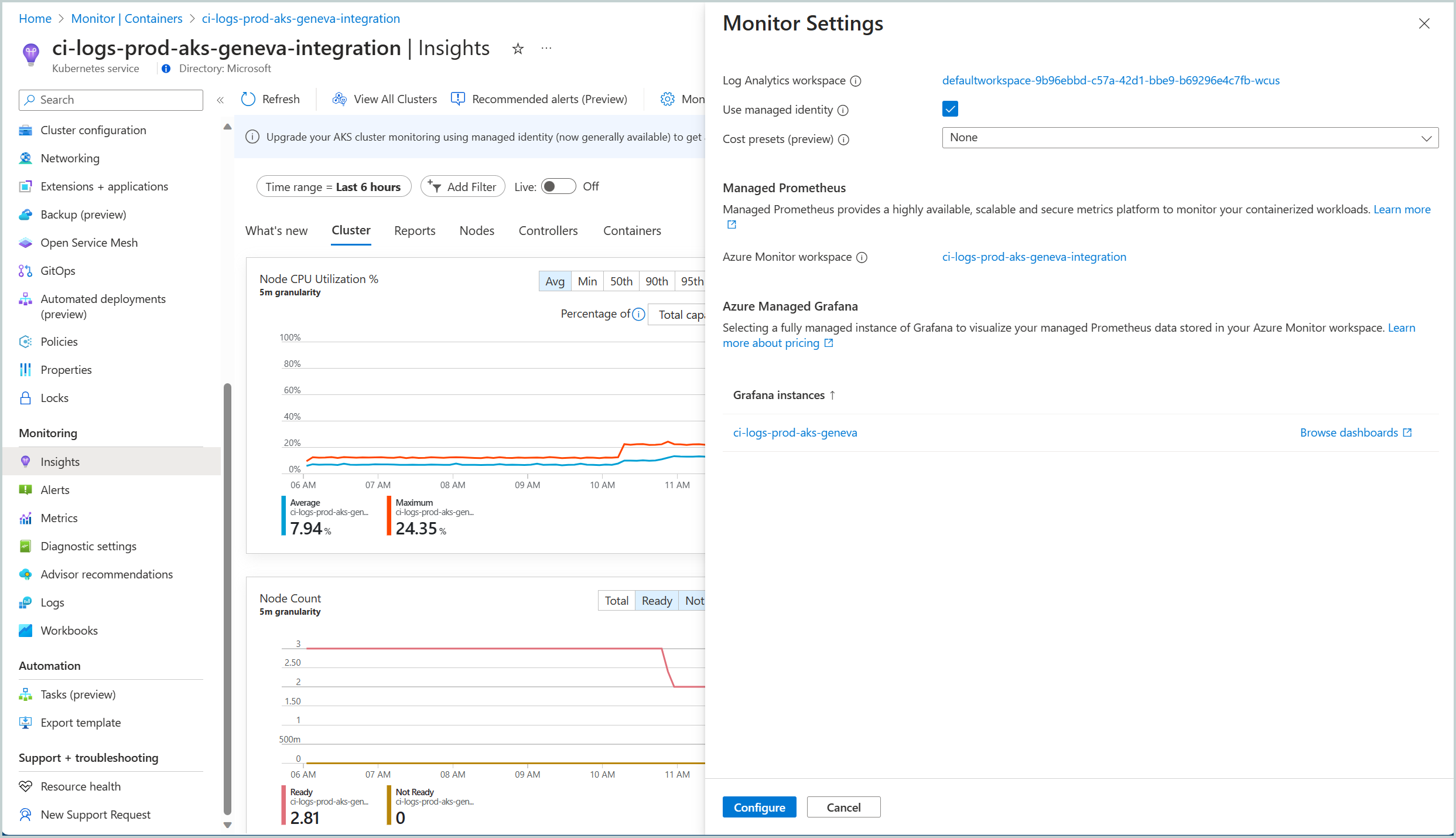
You can migrate to Managed Identity authentication from the Monitor settings panel for your AKS cluster. From the Monitoring section, click on the Insights tab. In the Insights tab, click on the Monitor Settings option and check the box for Use managed identity
If you don't see the Use managed identity option, you are using an SPN cluster. In that case, you must use command line tools to migrate. See other tabs for migration instructions and templates.
Enable legacy authentication
If you require legacy authentication, see Enable Container insights which has examples of different options for enabling Container insights.
Next steps
If you experience issues when you upgrade the agent, review the troubleshooting guide for support.