Access Syslog data in Container Insights
Container Insights offers the ability to collect Syslog events from Linux nodes in your Azure Kubernetes Service (AKS) clusters. This includes the ability to collect logs from control plane components like kubelet. Customers can also use Syslog for monitoring security and health events, typically by ingesting syslog into a SIEM system like Microsoft Sentinel.
Prerequisites
- Syslog collection needs to be enabled for your cluster using the guidance in Configure and filter log collection in Container insights.
- Port 28330 should be available on the host node.
Built-in workbooks
To get a quick snapshot of your syslog data, use the built-in Syslog workbook using one of the following methods:
Note
The Reports tab won't be available if you enable the Container insights Prometheus experience for your cluster.
Reports tab in Container Insights. Navigate to your cluster in the Azure portal and open the Insights. Open the Reports tab and locate the Syslog workbook.
Workbooks tab in AKS Navigate to your cluster in the Azure portal. Open the Workbooks tab and locate the Syslog workbook.
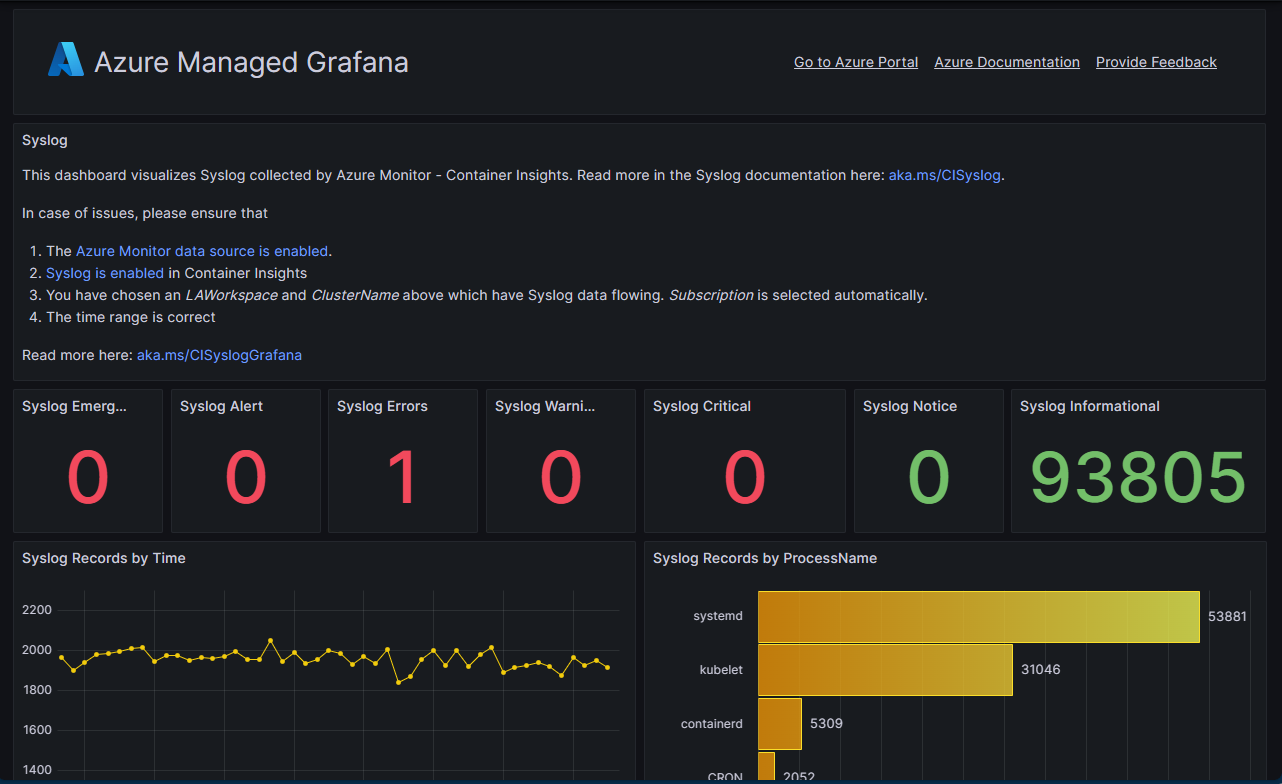
Grafana dashboard
If you use Grafana, you can use the Syslog dashboard for Grafana to get an overview of your Syslog data. This dashboard is available by default if you create a new Azure-managed Grafana instance. Otherwise, you can import the Syslog dashboard from the Grafana marketplace.
Note
You need the Monitoring Reader role on the Subscription containing the Azure Managed Grafana instance to access syslog from Container Insights.
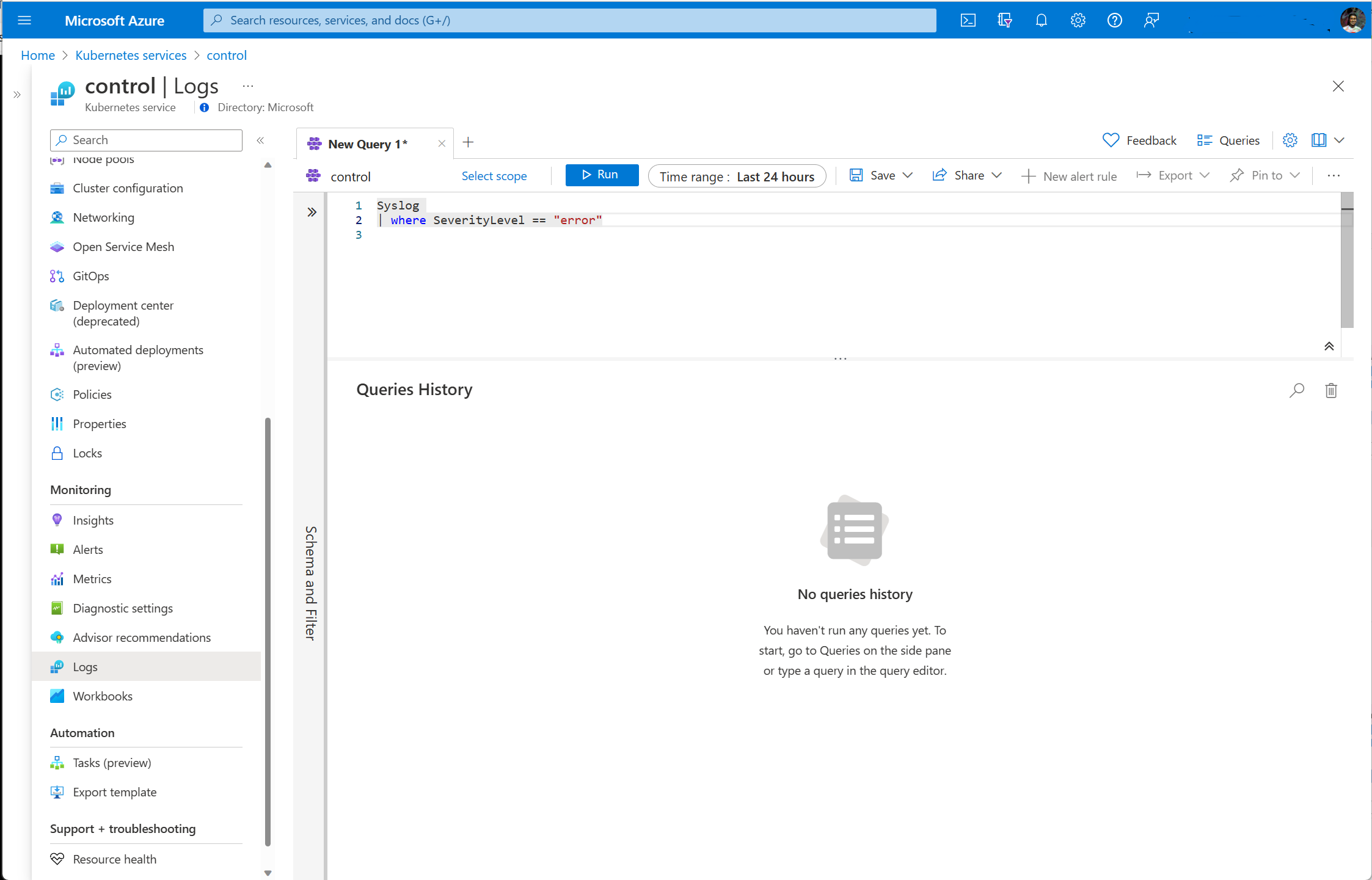
Log queries
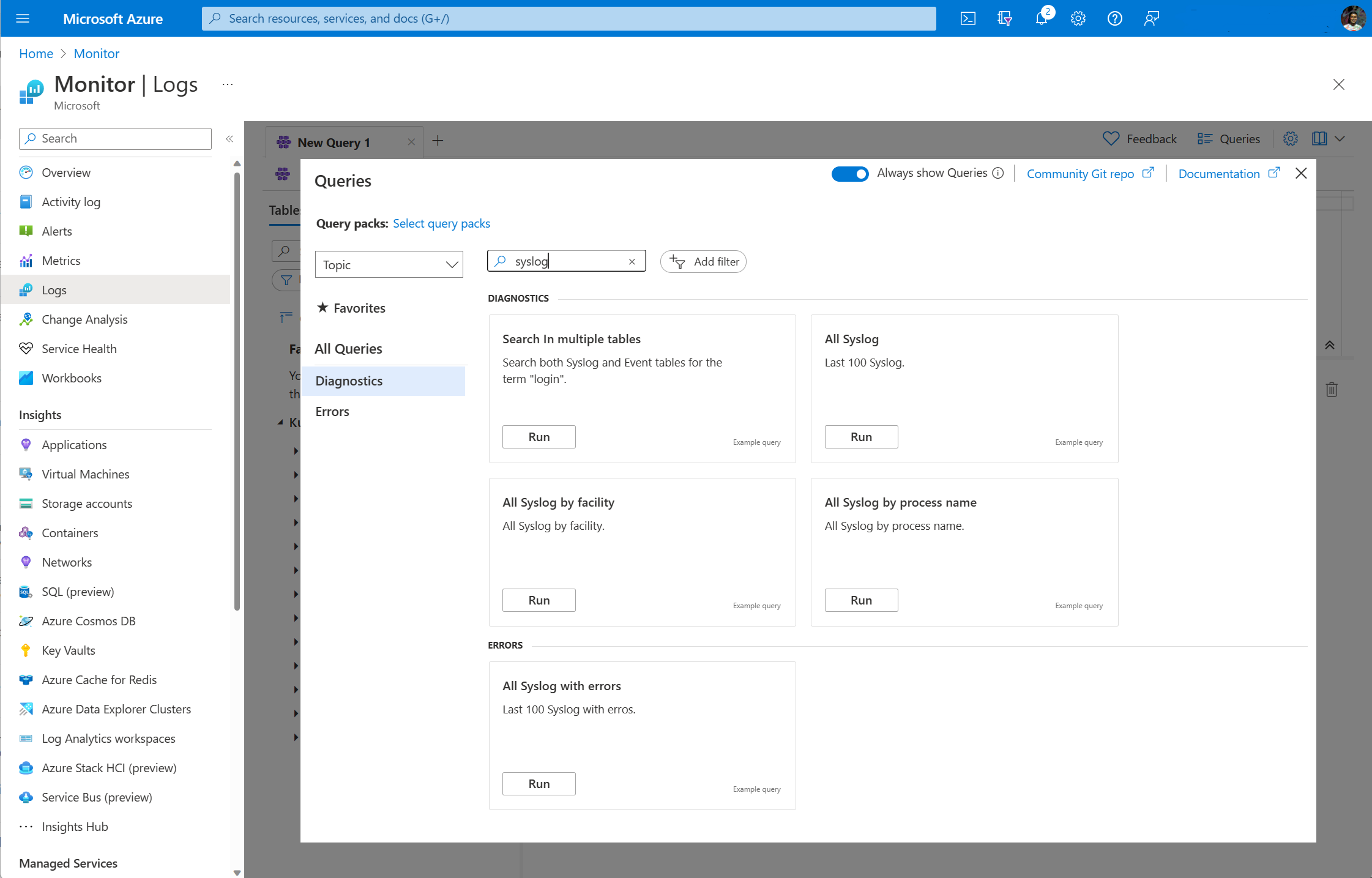
Syslog data is stored in the Syslog table in your Log Analytics workspace. You can create your own log queries in Log Analytics to analyze this data or use any of the prebuilt queries.
You can open Log Analytics from the Logs menu in the Monitor menu to access Syslog data for all clusters or from the AKS cluster's menu to access Syslog data for a single cluster.
Sample queries
The following table provides different examples of log queries that retrieve Syslog records.
| Query | Description |
|---|---|
Syslog |
All Syslogs |
Syslog | where SeverityLevel == "error" |
All Syslog records with severity of error |
Syslog | summarize AggregatedValue = count() by Computer |
Count of Syslog records by computer |
Syslog | summarize AggregatedValue = count() by Facility |
Count of Syslog records by facility |
Syslog | where ProcessName == "kubelet" |
All Syslog records from the kubelet process |
Syslog | where ProcessName == "kubelet" and SeverityLevel == "error" |
Syslog records from kubelet process with errors |
Next steps
Once setup customers can start sending Syslog data to the tools of their choice
Share your feedback for this feature here: https://forms.office.com/r/BBvCjjDLTS