Register an App to request authorization tokens and work with APIs
To access Azure REST APIs such as the Log analytics API, or to send custom metrics, you can generate an authorization token based on a client ID and secret. The token is then passed in your REST API request. This article shows you how to register a client app and create a client secret so that you can generate a token.
Register an App
Create a service principal and register an app using the Azure portal, Azure CLI, or PowerShell.
To register an app, open the Active Directory Overview page in the Azure portal.
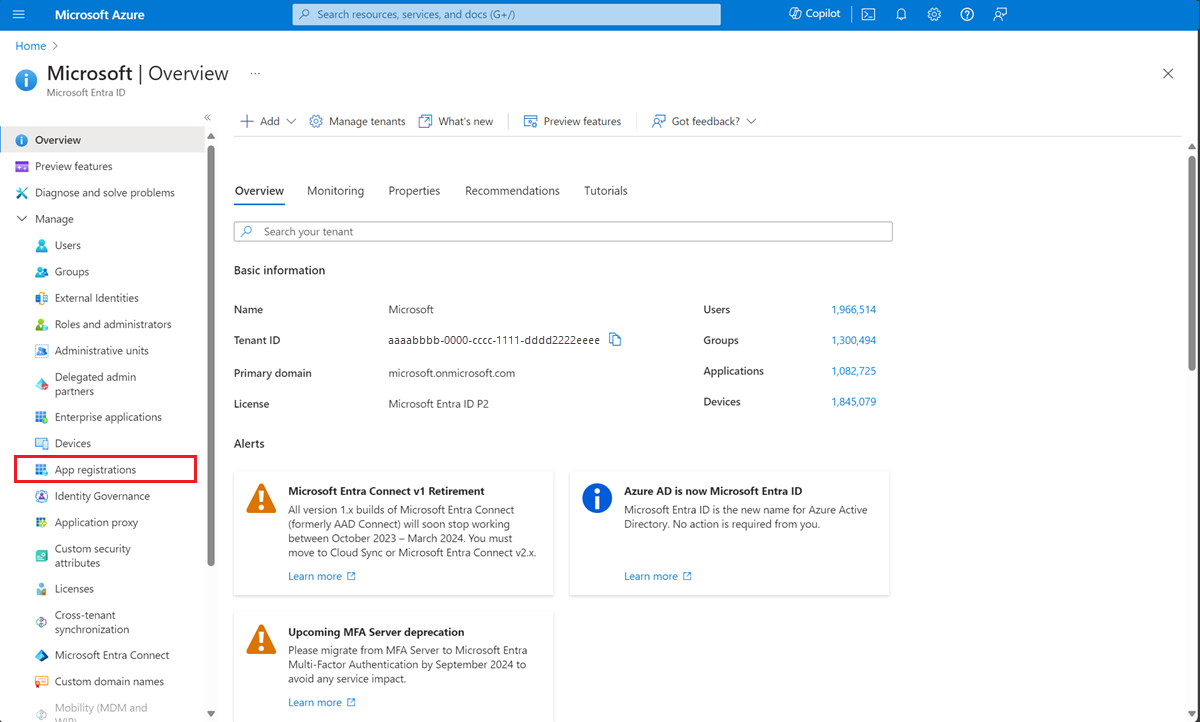
Select App registrations from the side bar.
Select New registration
On the Register an application page, enter a Name for the application.
Select Register
On the app's overview page, select Certificates and Secrets
Note the Application (client) ID. It's used in the HTTP request for a token.
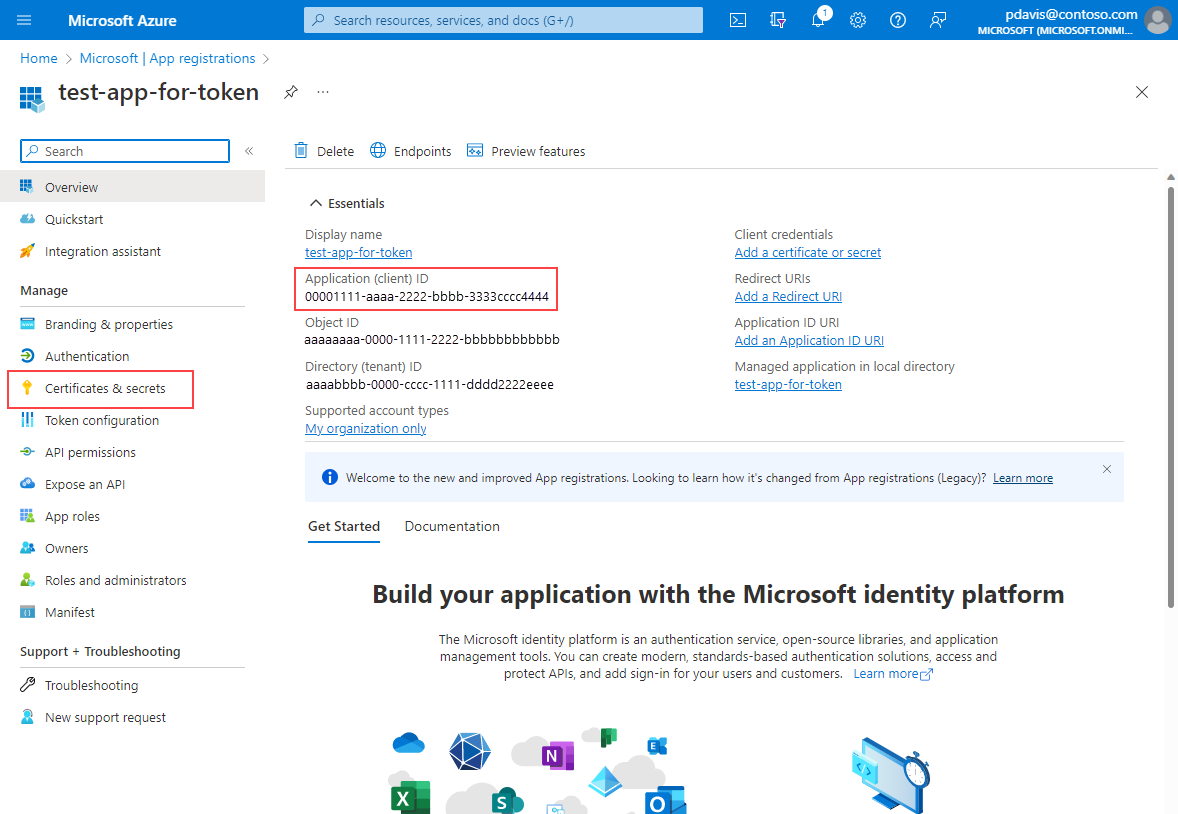
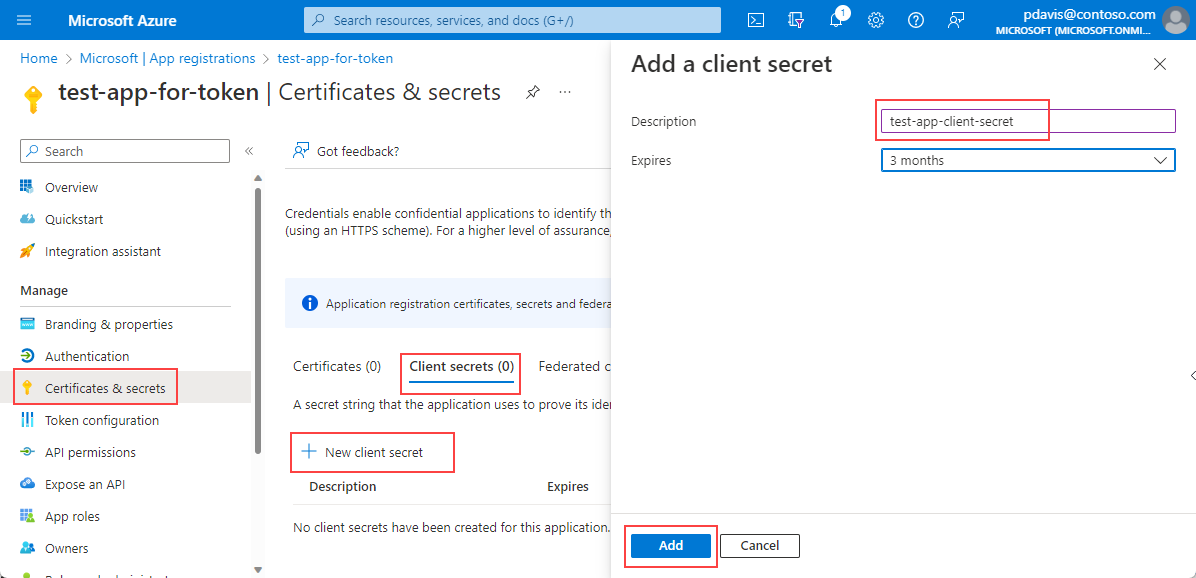
In the Client secrets tab Select New client secret
Enter a Description and select Add
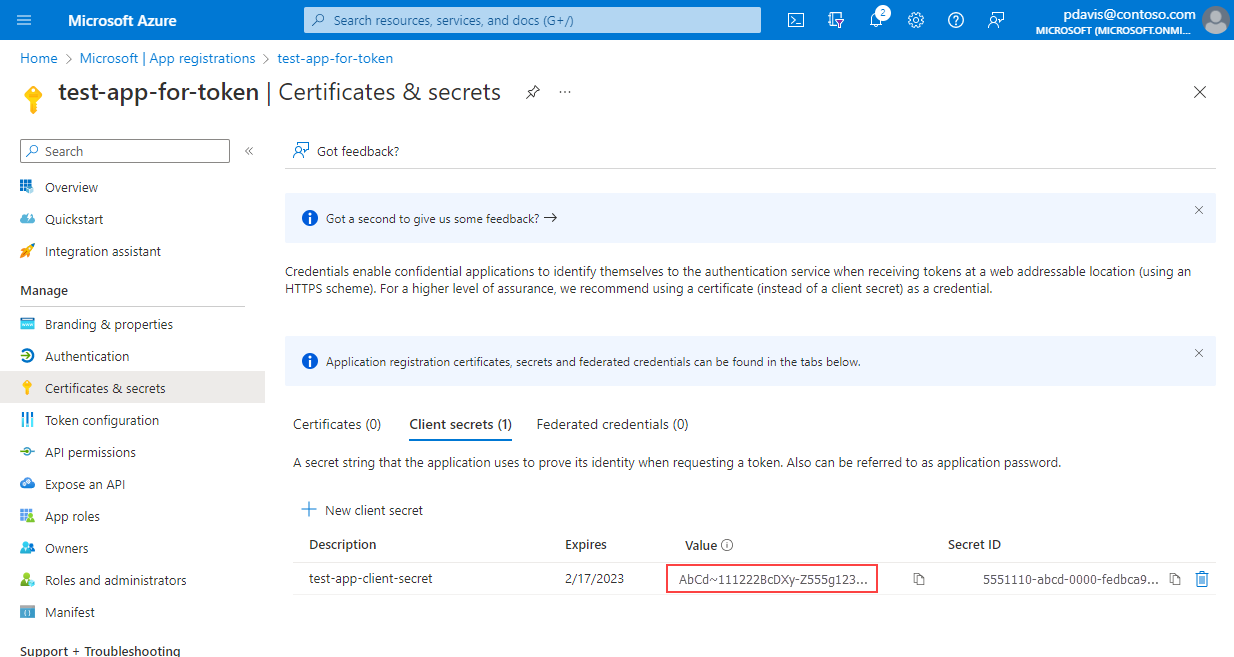
Copy and save the client secret Value.
Note
Client secret values can only be viewed immediately after creation. Be sure to save the secret before leaving the page.
Next steps
Before you can generate a token using your app, client ID, and secret, assign the app to a role using Access control (IAM) for resource that you want to access. The role will depend on the resource type and the API that you want to use.
For example,
To grant your app read from a Log Analytics Workspace, add your app as a member to the Reader role using Access control (IAM) for your Log Analytics Workspace. For more information, see Access the API
To grant access to send custom metrics for a resource, add your app as a member to the Monitoring Metrics Publisher role using Access control (IAM) for your resource. For more information, see Send metrics to the Azure Monitor metric database using REST API
For more information, see Assign Azure roles using the Azure portal
Once you've assigned a role, you can use your app, client ID, and client secret to generate a bearer token to access the REST API.
Note
When using Microsoft Entra authentication, it may take up to 60 minutes for the Azure Application Insights REST API to recognize new role-based access control (RBAC) permissions. While permissions are propagating, REST API calls may fail with error code 403.