Configure customer-managed key encryption at rest in Azure VMware Solution
This article illustrates how to encrypt VMware vSAN key encryption keys (KEKs) with customer-managed keys (CMKs) managed by a customer-owned Azure Key Vault instance.
When CMK encryptions are enabled on your Azure VMware Solution private cloud, Azure VMware Solution uses the CMK from your key vault to encrypt the vSAN KEKs. Each ESXi host that participates in the vSAN cluster uses randomly generated disk encryption keys (DEKs) that ESXi uses to encrypt disk data at rest. vSAN encrypts all DEKs with a KEK provided by the Azure VMware Solution key management system. The Azure VMware Solution private cloud and the key vault don't need to be in the same subscription.
When you manage your own encryption keys, you can:
- Control Azure access to vSAN keys.
- Centrally manage the lifecycle of CMKs.
- Revoke Azure access to the KEK.
The CMKs feature supports the following key types and their key sizes:
- RSA: 2048, 3072, 4096
- RSA-HSM: 2048, 3072, 4096
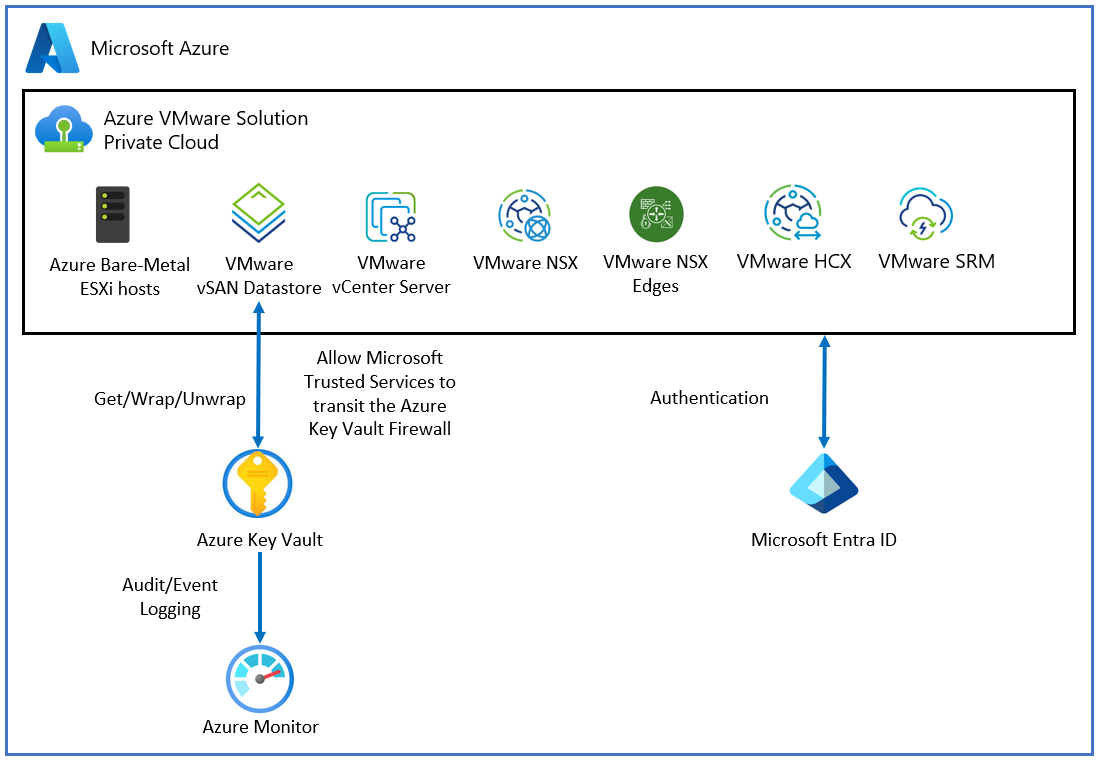
Topology
The following diagram shows how Azure VMware Solution uses Microsoft Entra ID and a key vault to deliver the CMK.
Prerequisites
Before you begin to enable CMK functionality, ensure that the following requirements are met:
You need a key vault to use CMK functionality. If you don't have a key vault, you can create one by using Quickstart: Create a key vault using the Azure portal.
If you enabled restricted access to Key Vault, you need to allow Microsoft Trusted Services to bypass the Key Vault firewall. Go to Configure Azure Key Vault networking settings to learn more.
Note
After firewall rules are in effect, users can only perform Key Vault data plane operations when their requests originate from allowed VMs or IPv4 address ranges. This restriction also applies to accessing Key Vault from the Azure portal. It also affects the Key Vault Picker by Azure VMware Solution. Users might be able to see a list of key vaults, but not list keys, if firewall rules prevent their client machine or the user doesn't have list permission in Key Vault.
Enable System Assigned identity on your Azure VMware Solution private cloud if you didn't enable it during software-defined datacenter (SDDC) provisioning.
To enable System Assigned identity:
Sign in to the Azure portal.
Go to Azure VMware Solution and locate your private cloud.
On the leftmost pane, open Manage and select Identity.
In System Assigned, select Enable > Save. System Assigned identity should now be enabled.
After System Assigned identity is enabled, you see the tab for Object ID. Make a note of the Object ID for use later.
Configure the key vault access policy to grant permissions to the managed identity. You use it to authorize access to the key vault.
- Sign in to the Azure portal.
- Go to Key vaults and locate the key vault you want to use.
- On the leftmost pane, under Settings, select Access policies.
- In Access policies, select Add Access Policy and then:
- In the Key Permissions dropdown, choose Select, Get, Wrap Key, and Unwrap Key.
- Under Select principal, select None selected. A new Principal window with a search box opens.
- In the search box, paste the Object ID from the previous step. Or search for the private cloud name you want to use. Choose Select when you're finished.
- Select ADD.
- Verify that the new policy appears under the current policy's Application section.
- Select Save to commit changes.
Customer-managed key version lifecycle
You can change the CMK by creating a new version of the key. The creation of a new version doesn't interrupt the virtual machine (VM) workflow.
In Azure VMware Solution, CMK key version rotation depends on the key selection setting that you chose during CMK setup.
Key selection setting 1
A customer enables CMK encryption without supplying a specific key version for CMK. Azure VMware Solution selects the latest key version for CMK from the customer's key vault to encrypt the vSAN KEKs. Azure VMware Solution tracks the CMK for version rotation. When a new version of the CMK key in Key Vault is created, it gets captured by Azure VMware Solution automatically to encrypt vSAN KEKs.
Note
Azure VMware Solution can take up to 10 minutes to detect a new autorotated key version.
Key selection setting 2
A customer can enable CMK encryption for a specified CMK key version to supply the full key version URI under the Enter Key from URI option. When the customer's current key expires, they need to extend the CMK key expiration or disable CMK.
Enable CMK with system-assigned identity
System-assigned identity is restricted to one per resource and is tied to the lifecycle of the resource. You can grant permissions to the managed identity on Azure resource. The managed identity is authenticated with Microsoft Entra ID, so you don't have to store any credentials in code.
Important
Ensure that Key Vault is in the same region as the Azure VMware Solution private cloud.
Go to your Key Vault instance and provide access to the SDDC on Key Vault by using the principal ID captured on the Enable MSI tab.
From your Azure VMware Solution private cloud, under Manage, select Encryption. Then select Customer-managed keys (CMKs).
CMK provides two options for Key Selection from Key Vault:
Option 1:
- Under Encryption key, choose select from Key Vault.
- Select the encryption type. Then select the Select Key Vault and key option.
- Select the Key Vault and key from the dropdown. Then choose Select.
Option 2:
- Under Encryption key, select Enter key from URI.
- Enter a specific Key URI in the Key URI box.
Important
If you want to select a specific key version instead of the automatically selected latest version, you need to specify the Key URI with the key version. This choice affects the CMK key version lifecycle.
The Key Vault Managed Hardware Security Module (HSM) option is only supported with the Key URI option.
Select Save to grant access to the resource.
Change from a customer-managed key to a Microsoft managed key
When a customer wants to change from a CMK to a Microsoft-managed key (MMK), the VM workload isn't interrupted. To make the change from a CMK to an MMK:
- Under Manage, select Encryption from your Azure VMware Solution private cloud.
- Select Microsoft-managed keys (MMK).
- Select Save.
Limitations
Key Vault must be configured as recoverable. You need to:
- Configure Key Vault with the Soft Delete option.
- Turn on Purge Protection to guard against force deletion of the secret vault, even after soft delete.
Updating CMK settings don't work if the key is expired or the Azure VMware Solution access key was revoked.
Troubleshooting and best practices
Here are troubleshooting tips for some common issues you might encounter and also best practices to follow.
Accidental deletion of a key
If you accidentally delete your key in the key vault, the private cloud can't perform some cluster modification operations. To avoid this scenario, we recommend that you keep soft deletes enabled in the key vault. This option ensures that if a key is deleted, it can be recovered within a 90-day period as part of the default soft-delete retention. If you're within the 90-day period, you can restore the key to resolve the issue.
Restore key vault permission
If you have a private cloud that has lost access to the CMK, check if Managed System Identity (MSI) requires permissions in the key vault. The error notification returned from Azure might not correctly indicate MSI requiring permissions in the key vault as the root cause. Remember, the required permissions are get, wrapKey, and unwrapKey. See step 4 in Prerequisites.
Fix an expired key
If you aren't using the autorotate function and the CMK expired in Key Vault, you can change the expiration date on the key.
Restore key vault access
Ensure that the MSI is used for providing private cloud access to the key vault.
Deletion of MSI
If you accidentally delete the MSI associated with a private cloud, you need to disable the CMK. Then follow the steps to enable the CMK from the start.
Next steps
- Learn about Azure Key Vault backup and restore.
- Learn about Azure Key Vault recovery.