Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
VMware Cloud Director service (CDs) with Azure VMware Solution enables enterprise customers to use APIs or the Cloud Director services portal to self-service, provision, and manage virtual datacenters through multi-tenancy with reduced time and complexity.
In this article, learn how to enable VMware Cloud Director service with Azure VMware Solution for enterprise customers to use Azure VMware Solution resources and Azure VMware Solution private clouds with underlying resources for virtual datacenters.
Important
VMware Cloud Director service is now available to use with Azure VMware Solution under the Enterprise Agreement (EA) model only. It's not suitable for MSP / Hosters to resell Azure VMware Solution capacity to customers at this point. For more information, see Azure Service terms.
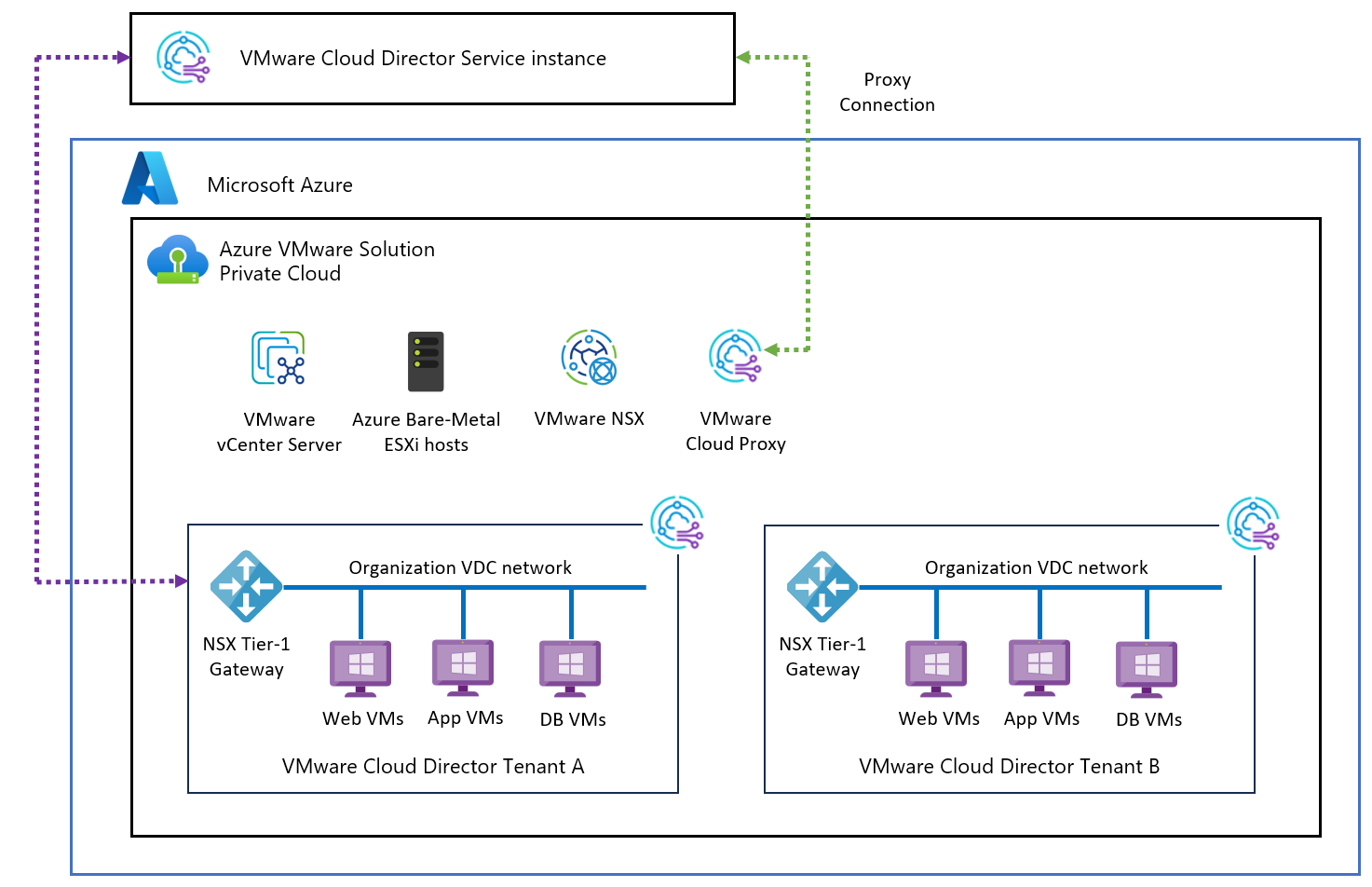
Reference architecture
The following diagram shows typical architecture for Cloud Director services with Azure VMware Solution and how they're connected. An SSL reverse proxy supports communication to Azure VMware Solution endpoints from Cloud Director service.
VMware Cloud Director supports multi-tenancy by using organizations. A single organization can have multiple organization virtual data centers (VDC). Each Organization's VDC can have their own dedicated Tier-1 router (Edge Gateway) which is further connected with the provider managed shared Tier-0 router.
Learn more about CDs on Azure VMware Solutions reference architecture
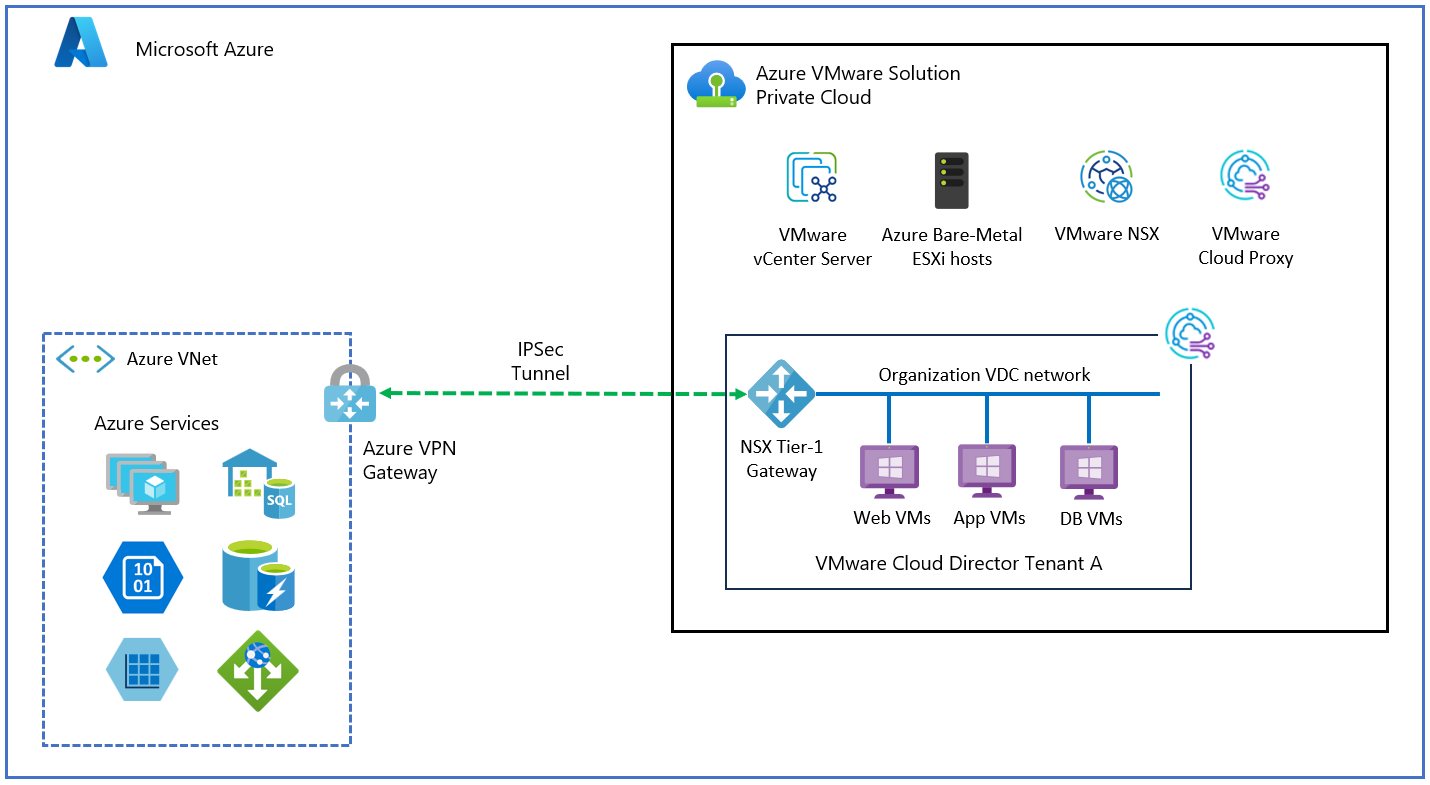
Connect tenants and their organization virtual datacenters to Azure VNet based resources
To provide access to VNet based Azure resources, each tenant can have their own dedicated Azure VNet with Azure VPN gateway. A site-to-site VPN between customer organization VDC and Azure VNet is established. To achieve this connectivity, the tenant provides public IP to the organization VDC. The organization VDC administrator can configure IPSEC VPN connectivity from the Cloud Director service portal.
As shown in the previous diagram, organization 01 has two organization virtual datacenters: VDC1 and VDC2. The virtual datacenter of each organization has its own Azure VNets connected with their respective organization VDC Edge gateway through IPSEC VPN. Providers provide public IP addresses to the organization VDC Edge gateway for IPSEC VPN configuration. An ORG VDC Edge gateway firewall blocks all traffic by default, specific allow rules needs to be added on organization Edge gateway firewall.
Organization VDCs can be part of a single organization and still provide isolation between them. For example, VM1 hosted in organization VDC1 can't ping Azure VM JSVM2 for tenant2.
Prerequisites
- Organization VDC is configured with an Edge gateway and has Public IPs assigned to it to establish IPSEC VPN by provider.
- Tenants created a routed Organization VDC network in tenant's virtual datacenter.
- Test VM1 and VM2 are created in the Organization VDC1 and VDC2 respectively. Both VMs are connected to the routed orgVDC network in their respective VDCs.
- Have a dedicated Azure VNet configured for each tenant. For this example, we created Tenant1-VNet and Tenant2-VNet for tenant1 and tenant2 respectively.
- Create an Azure Virtual network gateway for VNETs created earlier.
- Deploy Azure VMs JSVM1 and JSVM2 for tenant1 and tenant2 for test purposes.
Note
VMware Cloud Director service supports a policy-based VPN. Azure VPN gateway configures route-based VPN by default and to configure policy-based VPN policy-based selector needs to be enabled.
Configure Azure VNet
Create the following components in tenant's dedicated Azure VNet to establish IPSEC tunnel connection with the tenant's ORG VDC Edge gateway.
- Azure Virtual network gateway
- Local network gateway.
- Add IPSEC connection on VPN gateway.
- Edit connection configuration to enable policy-based VPN.
Create Azure virtual network gateway
To create an Azure virtual network gateway, see the create-a-virtual-network-gateway tutorial.
Create local network gateway
- Sign in to the Azure portal and select Local network gateway from marketplace and then select Create.
- Local Network Gateway represents remote end site details. Therefore provide tenant1 OrgVDC public IP address and orgVDC Network details to create local end point for tenant1.
- Under Instance details, select Endpoint as IP address
- Add IP address (add Public IP address from tenant's OrgVDC Edge gateway).
- Under Address space add Tenants Org VDC Network.
- Repeat steps 1-5 to create a local network gateway for tenant 2.
Create IPSEC connection on VPN gateway
Select tenant1 VPN Gateway (created earlier) and then select Connection (in left pane) to add new IPSEC connection with tenant1 orgVDC Edge gateway.
Enter the following details.
Name Connection Connection Type Site to Site VPN Gateway Tenant's VPN Gateway Local Network Gateway Tenant's Local Gateway PSK Shared Key (provide a password) IKE Protocol IKEV2 (ORG-VDC is using IKEv2) Select Ok to deploy local network gateway.
Configure IPsec Connection
VMware Cloud Director service supports a policy-based VPN. Azure VPN gateway configures route-based VPN by default and to configure policy-based VPN policy-based selector needs to be enabled.
- Select the connection you created earlier and then select configuration to view the default settings.
- IPSEC/IKE Policy
- Enable policy base traffic selector
- Modify all other parameters to match what you have in OrgVDC.
Note
Both source and destination of the tunnel should have identical settings for IKE,SA, DPD etc.
- Select Save.
Configure VPN on organization VDC Edge router
Sign in to Organization VMware Cloud Director service tenant portal and select the tenants Edge gateway.
Select IPSEC VPN option under Services and then select New.
Under general setting, provide Name and select desired security profile. Ensure that security profile settings (IKE, Tunnel, and DPD configuration) are same on both sides of the IPsec tunnel.
Modify Azure VPN gateway to match the Security profile, if necessary. You can also do security profile customization from CDS tenant portal.
Note
VPN tunnel won't establish if these settings were mismatched.
Under Peer Authentication Mode, provide the same preshared key that is used at the Azure VPN gateway.
Under Endpoint configuration, add the Organization's public IP and network details in local endpoint and Azure VNet details in remote endpoint configuration.
Under Ready to complete, review applied configuration.
Select Finish to apply configuration.
Apply firewall configuration
Organization VDC Edge router firewall denies traffic by default. You need to apply specific rules to enable connectivity. Use the following steps to apply firewall rules.
- Add IP set in VMware Cloud Director service portal
- Sign in to Edge router then select IP SETS under the Security tab in left plane.
- Select New to create IP sets.
- Enter Name and IP address of test VM deployed in orgVDC.
- Create another IP set for Azure VNet for this tenant.
- Apply firewall rules on ORG VDC Edge router.
- Under Edge gateway, select Edge gateway and then select firewall under services.
- Select Edit rules.
- Select NEW ON TOP and enter rule name.
- Add source and destination details. Use created IPSET in source and destination.
- Under Action, select Allow.
- Select Save to apply configuration.
- Verify tunnel status
- Under Edge gateway select Service, then select IPSEC VPN,
- Select View statistics.
Status of tunnel should show UP.
- Verify IPsec connection
- Sign in to Azure VM deployed in tenants VNet and ping tenant's test VM IP address in tenant's OrgVDC.
For example, ping VM1 from JSVM1. Similarly, you should be able to ping VM2 from JSVM2. You can verify isolation between tenants Azure VNets. Tenant 1 VM1 can't ping Tenant 2 Azure VM JSVM2 in tenant 2 Azure VNets.
- Sign in to Azure VM deployed in tenants VNet and ping tenant's test VM IP address in tenant's OrgVDC.
Connect Tenant workload to public Internet
- Tenants can use public IP to do SNAT configuration to enable Internet access for VM hosted in organization VDC. To achieve this connectivity, the provider can provide public IP to the organization VDC.
- Each organization VDC can be created with dedicated T1 router (created by provider) with reserved Public & Private IP for NAT configuration. Tenants can use public IP SNAT configuration to enable Internet access for VM hosted in organization VDC.
- OrgVDC administrator can create a routed OrgVDC network connected to their OrgVDC Edge gateway. To provide Internet access.
- OrgVDC administrator can configure SNAT to provide a specific VM or use network CIDR to provide public connectivity.
- OrgVDC Edge has default DENY ALL firewall rule. Organization administrators need to open appropriate ports to allow access through the firewall by adding a new firewall rule. Virtual machines configured on such OrgVDC network used in SNAT configuration should be able to access the Internet.
Prerequisites
- Public IP is assigned to the organization VDC Edge router. To verify, sign in to the organization's VDC. Under Networking> Edges, select Edge Gateway, then select IP allocations under IP management. You should see a range of assigned IP address there.
- Create a routed Organization VDC network. (Connect OrgvDC network to the Edge gateway with public IP address assigned)
Apply SNAT configuration
- Sign in to Organization VDC. Navigate to your Edge gateway and then select NAT under Services.
- Select New to add new SNAT rule.
- Provide Name and select Interface type as SNAT.
- Under External IP, enter public IP address from public IP pool assigned to your orgVDC Edge router.
- Under Internal IP, enter IP address for your test VM. This IP address is one of the orgVDC network IP assigned to the VM.
- State should be enabled.
- Under Priority, select a higher number. For example, 4096.
- Select Save to save the configuration.
Apply firewall rule
- Sign in to Organization VDC and navigate to Edge Gateway, then select IP set under security.
- Create an IPset. Provide IP address of your VM (you can use CIDR also). Select Save.
- Under services, select Firewall, then select Edit rules.
- Select New ON TOP and create a firewall rule to allow desired port and destination.
- Select the IPset your created earlier as source. Under Action, select Allow.
- Select Keep to save the configuration.
- Sign in to your test VM and ping your destination address to verify outbound connectivity.
Migrate workloads to VMware Cloud Director service on Azure VMware Solution
VMware Cloud Director Availability can be used to migrate VMware Cloud Director workload into the VMware Cloud Director service on Azure VMware Solution. Enterprise customers can drive self-serve one-way warm migration from the on-premises Cloud Director Availability vSphere plugin, or they can run the Cloud Director Availability plugin from the provider-managed Cloud Director instance and move workloads into Azure VMware Solution.
For more information about VMware Cloud Director Availability, see VMware Cloud Director Availability | Disaster Recovery & Migration
FAQs
What are the supported Azure regions for the VMware Cloud Director service?
This offering is supported in all Azure regions where Azure VMware Solution is available except for Brazil South and South Africa. Ensure that the region you wish to connect to VMware Cloud Director service is within a 150-milliseconds round trip time for latency with VMware Cloud Director service.
How do I configure VMware Cloud Director service on Microsoft Azure VMware Solutions?
Learn about how to configure CDs on Azure VMware Solutions
How is VMware Cloud Director service supported?
VMware Cloud Director service (CDs) is VMware owned and supported product connected to Azure VMware solution. For any support queries on CDs, contact VMware support for assistance. Both VMware and Microsoft support teams collaborate as necessary to address and resolve Cloud Director Service issues within Azure VMware Solution.
Next steps
VMware Cloud Director Service Documentation
Migration to Azure VMware Solutions with Cloud Director service