Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
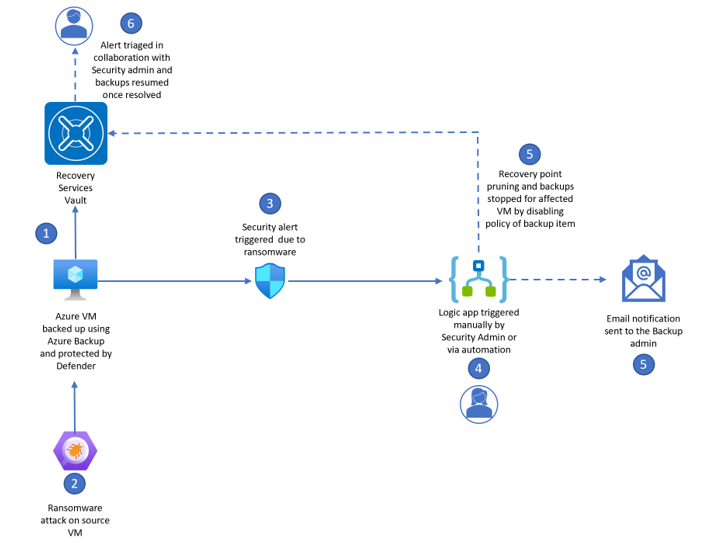
This article describes how to integrate Microsoft Defender's ransomware alerts to preserve Azure Backup recovery points. Assume there has been a breach on the Virtual Machine that is protected by both Defender and Azure Backup. Defender detects the ransomware, raises an alert which includes details of the activity and suggested recommendations to remediate. As soon as a ransomware signal is detected from Defender, ensuring backups are preserved (i.e., paused from expiring) to minimize the data loss is top of our customers’ mind.
Azure Backup provides several security capabilities to help you protect your backup data. Soft delete, Immutable vaults, Multi-User Authorization (MUA) are part of a comprehensive data protection strategy for backup data. Soft delete is enabled by default, with option to make it always-on (irreversible). Soft deleted backup data is retained at no additional cost for 14 days, with option to extend the duration. Enabling immutability on vaults can protect backup data by blocking any operations that could lead to loss of recovery points. You can configure Multi-user authorization (MUA) for Azure Backup as an additional layer of protection to critical operations on your Recovery Services vaults. By default, critical alert for destructive operation (such as stop protection with delete backup data) is raised and an email is sent to subscription owners, admins, and co-admins.
Microsoft Defender for Cloud (MDC) is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) for all of your Azure, on-premises, and multicloud (Amazon AWS and Google GCP) resources. Defender for Cloud generates security alerts when threats are identified in your cloud, hybrid, or on-premises environment. It's available when you enable enhanced security features. Each alert provides details of affected resources along with the information you need to quickly investigate the issue and steps to take to remediate an attack. If a malware or a ransomware attacks on an Azure Virtual Machine, Microsoft Defender for Cloud detects suspicious activity and indicators associated with ransomware on an Azure VM and generates a Security Alert. Examples of the Defender for Cloud Alerts that trigger on a Ransomware detection: Ransomware indicators detected, Behavior similar to ransomware detected, and so on.
Note
This solution is scoped to Azure Virtual Machines. You can deployed the logic app only at a subscription level, which means all Azure VMs under the subscription can use the logic app to pause expiry of recovery points in the event of a security alert.
Solution workflow
This solution demonstrates integration of Azure Backup with Microsoft Defender for Cloud (MDC) for detection and response to alerts to accelerate response. The disgram illustrates the following three use cases:
- Ability to send email alerts to the Backup Admin.
- Security Admin to triage and manually trigger logic app to secure backups.
- Workflow to automatically respond to the alert by performing the Disable Backup Policy (Stop backup and retain data) operation.
Prerequisites
- Enable Azure Backup for Azure virtual machines.
- Enable Microsoft Defender for Servers Plan 2 for the Subscription.
Deploy Azure Logic Apps
To deploy Azure Logic Apps, follow these steps:
Go to GitHub and select Deploy to Azure.

On the deployment pane, enter the following details:
Subscription: Select the subscription whose Azure VMs the logic app should govern.
Name: Enter a suitable name for the logic app.
Region: Choose the region with which the subscription is associated.
Email: Enter the email address of the Backup admin for them to receive alerts when policy is suspended.
Resource group: Select the resource group with which logic apps need to be associated for deployment.
Managed Identity: Create and assign a Managed Identity with the below minimum permissions for the service to perform the Stop backup and retain data operation on the backup item automatically during a malware alert.
- Virtual Machine Contributor on the subscription
- The Backup Operator on the subscription
- Security Reader
Note
To further tighten the security, we recommend you create a custom role and assign that to the Managed Identity instead of the above built-in roles. This ensures that all the calls run with least privileges. For more information on custom role, see the GitHub article.
Managed Identity Subscription: Enter the name of a Subscription that the Managed Identity should reside in.
Managed Identity Resource Group: Enter the name of a resource group that the Managed Identity should reside in.

Note
You need Owner access on the Subscription to deploy the logic app.
Select Review + Create.
Authorize Office 365 for email alerts
To authorize the API connection to Office 365, follow these steps:
Go to the resource group you used to deploy the template resources.
Select the Office365 API connection (which is one of the resources you deployed) and select the error that appears at the API connection.
Select Edit API connection.
Select Authorize.
Note
Ensure that you authenticate against Microsoft Entra ID.
Select Save.
Trigger the logic app
You can trigger the deployed logic app manually or automatically using workflow automation.
Trigger manually
To trigger the logic app manually, follow these steps:
- Go to Microsoft Defender for Cloud, and then select Security Alerts on the left pane.
- Select the required alert to expand details.
- Select Take action, choose Trigger automated response, and then select Trigger logic app.
- Search the deployed logic app by name, and then select Trigger.
Note
The minimum Azure RBAC permissions needed to trigger an action for the security alert are:
- Logic app Operator
- Security Admin role
Trigger using workflow automation via Azure portal
Workflow automation ensures that during a security alert, your backups corresponding to the VM facing this issue changes to Stop backup and retain data state, thus suspend policy and pause recovery point pruning. You can also use Azure Policy to deploy workflow automation.
Note
The minimum role required to deploy the workflow automation are:
- Logic app Operator
- Security Admin
To trigger the logic app using automatic workflow, follow these steps:
Go to Defender for Cloud, and then select Workflow automation on the left pane.
Select Add workflow automation to open the options pane for the new automation.
Enter the following details:
- Name and Description: Enter a suitable name for the automation.
- Subscription: Select the subscription same as the scope of the logic app.
- Resource group: Select the resource group in which the automation will reside.
- Defender for Cloud Data Type: Select Security Alert.
- Alert name contains: Select Malware or ransomware.
- Alert severity: Select High.
- Logic app: Select the logic app you deployed.
Select Create.
Email alerts
When the backup policy on the backup item gets disabled, the logic app also sends an email to the ID you've entered during deployment. The email ID should ideally be of the Backup Admin. You can then investigate the alert and resume the backups when the issue is resolved or if it's a false alarm.
Next steps
About backup and restore plan to protect against ransomware.