Identity providers
APPLIES TO: SDK v4
An identity provider authenticates user or client identities and issues consumable security tokens. It provides user authentication as a service.
Client applications, such as web applications, delegate authentication to a trusted identity provider. Such client applications are said to be federated, that is, they use federated identity. For more information, see Federated Identity pattern.
Using a trusted identity provider:
- Enables single sign-on (SSO) features, allowing an application to access multiple secured resources.
- Facilitates connections between cloud computing resources and users, decreasing the need for users to reauthenticate.
Single sign-on
Single sign-on refers to an authentication process that lets a user log on to a system once with a single set of credentials to access multiple applications or services.
A user logs in with a single ID and password to gain access to any of several related software systems. For more information, see Single sign on.
Many identity providers support a sign-out operation that revokes the user token and terminates access to the associated applications and services.
Important
SSO enhances usability by reducing the number of times a user must enter credentials. It also provides better security by decreasing the potential attack surface.
Microsoft Entra ID identity provider
Microsoft Entra ID is the identity service in Microsoft Azure that provides identity management and access control capabilities. It allows you to securely sign in users using industry standard protocols like OAuth2.0.
You can choose from two Active Directory identity provider implementations, which have different settings as shown below.
Note
Use these settings when configuring OAuth Connection Settings in the Azure bot registration application. For more information, see Add authentication to a bot.
The Microsoft identity platform (v2.0)—also known as the Microsoft Entra ID endpoint—allows a bot to get tokens to call Microsoft APIs, such as Microsoft Graph or other APIs. The identity platformis an evolution of the Azure AD platform (v1.0). For more information, see the Microsoft identity platform (v2.0) overview.
Use the AD v2 settings below to enable a bot to access Office 365 data via the Microsoft Graph API.
| Property | Description or value |
|---|---|
| Name | A name for this identity provider connection. |
| Service Provider | The identity provider to use. Select Microsoft Entra ID. |
| Client id | The application (client) ID for your Azure identity provider app. |
| Client secret | The secret for your Azure identity provider app. |
| Tenant ID | Your directory (tenant) ID or common. For more information, see the note about tenant IDs. |
| Scopes | A space-separated list of the API permissions you granted the Microsoft Entra ID identity provider app, such as openid, profile, Mail.Read, Mail.Send, User.Read, and User.ReadBasic.All. |
| Token Exchange URL | For an SSO-enabled skill bot use the token exchange URL associated with the OAuth connection; otherwise, leave this empty. For information about the SSO token exchange URL, see Create an OAuth connection settings. |
Note
If you selected one of the following, enter the tenant ID you recorded for the Microsoft Entra ID identity provider app:
- Accounts in this organizational directory only (Microsoft only - Single tenant)
- Accounts in any organizational directory(Microsoft AAD directory - Multi tenant)
If you selected Accounts in any organizational directory (Any Microsoft Entra ID directory - Multi tenant and personal Microsoft accounts e.g., Skype, Xbox, Outlook.com), enter common.
Otherwise, the Microsoft Entra ID identity provider app will use the tenant to verify the selected ID and exclude personal Microsoft accounts.
For more information, see:
- Why update to Microsoft identity platform (v2.0)?
- Microsoft identity platform (Microsoft Entra ID for developers).
Other identity providers
Azure supports several identity providers. You can get a complete list, along with the related details, by running the following Azure console commands:
az login
az bot authsetting list-providers
You can also see the list of these providers in the Azure portal when you define the OAuth connection settings for a bot registration app.
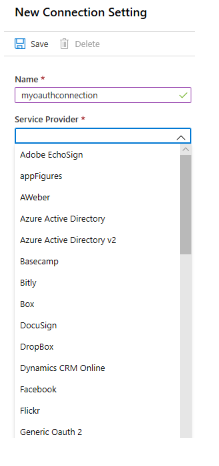
OAuth generic providers
Azure supports generic OAuth2, which allows you to use your own identity provider.
You can choose from two generic identity provider implementations, which have different settings as shown below.
Note
Use the settings described here when configuring the OAuth Connection Settings in the Azure bot registration application.
Use this provider to configure any generic OAuth2 identity provider that has similar expectations as Microsoft Entra ID provider, particularly AD v2. For this connection type, the query strings and request body payloads are fixed.
| Property | Description or value |
|---|---|
| Name | A name for this identity provider connection. |
| Service Provider | The identity provider to use. Select Generic Oauth 2. |
| Client id | Your client ID obtained from the identity provider. |
| Client secret | Your client secret obtained from the identity provider registration. |
| Authorization URL | https://login.microsoftonline.com/common/oauth2/v2.0/authorize |
| Token URL | https://login.microsoftonline.com/common/oauth2/v2.0/token |
| Refresh URL | https://login.microsoftonline.com/common/oauth2/v2.0/token |
| Token Exchange URL | Leave this empty. |
| Scopes | A comma-separated list of the API permissions you granted to the identity provider app. |