Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Application enclaves, such as Intel SGX, are isolated environments that protect specific code and data. When creating enclaves, you must determine what part of the application runs within the enclave. When you create or manage enclaves, be sure to use compatible SDKs and frameworks for the chosen deployment stack.
Note
If you haven't already read the introduction to Intel SGX VMs and enclaves, do so before continuing.
Microsoft Mechanics
Developing applications
There are two partitions in an application built with enclaves.
The host is the "untrusted" component. Your enclave application runs on top of the host. The host is an untrusted environment. When you deploy enclave code on the host, the host can't access that code.
The enclave is the "trusted" component. The application code and its cached data and memory run in the enclave. The enclave environment protects your secrets and sensitive data. Make sure your secure computations happen in an enclave.
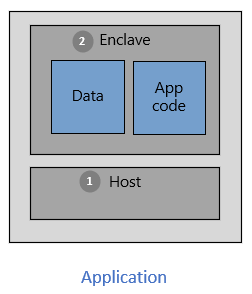
To use the power of enclaves and isolated environments, choose tools that support confidential computing. Various tools support enclave application development. For example, you can use these open-source frameworks:
- The Open Enclave Software Development Kit (OE SDK)
- The Intel SGX SDK
- The EGo Software Development Kit
- The Confidential Consortium Framework (CCF)
As you design an application, identify and determine what part of needs to run in enclaves. Code in the trusted component is isolated from the rest of your application. After the enclave initializes and the code loads to memory, untrusted components can't read or change that code.