Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
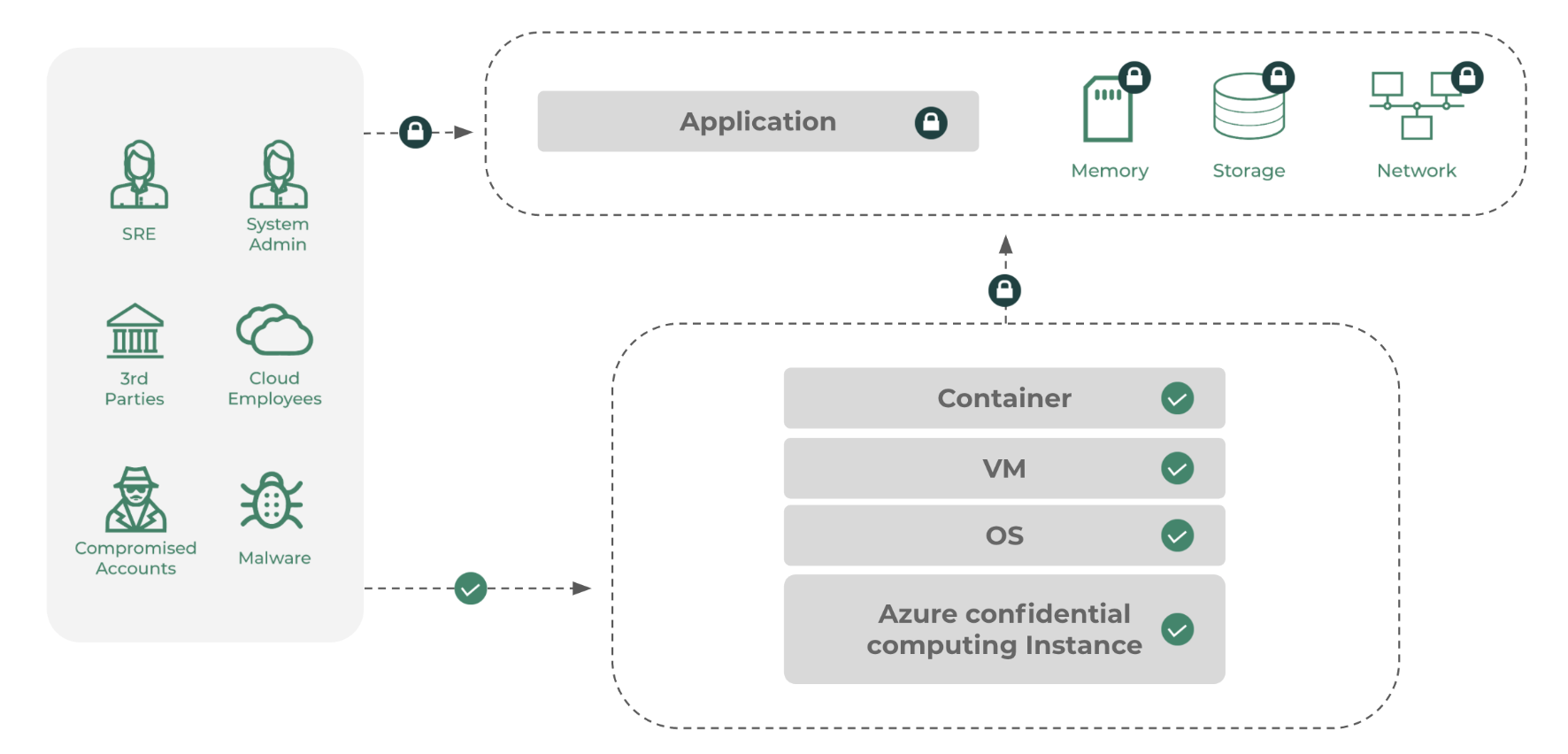
Confidential containers help you run existing unmodified container applications of most common programming languages runtimes (Python, Node, Java etc.) in the Intel SGX based Trusted Execution Environment(TEE). This packaging model typically does not need any source-code modifications or recompilation and is the fastest method to run in Intel SGX enclaves. Typical deployment process for running your standard docker containers requires an Open-Source SGX Wrapper or Azure Partner Solution. In this packaging and execution model each container application is loaded in the trusted boundary (enclave) and with a hardware-based isolation enforced by Intel SGX CPU. Each container running in an enclave receives its own memory encryption key delivered from the Intel SGX CPU. This model works well for off the shelf container applications available in the market or custom apps currently running on general purpose nodes. To run an existing Docker container, applications on confidential computing nodes require an Intel Software Guard Extensions (SGX) wrapper software to help the container execution within the bounds of special CPU instruction set. SGX creates a direct execution to the CPU to remove the guest operating system (OS), host OS, or hypervisor from the trust boundary. This step reduces the overall surface attack areas and vulnerabilities while achieving process level isolation within a single node.
The overall process for running unmodified containers involves changes to how your container is packaged today as detailed below.
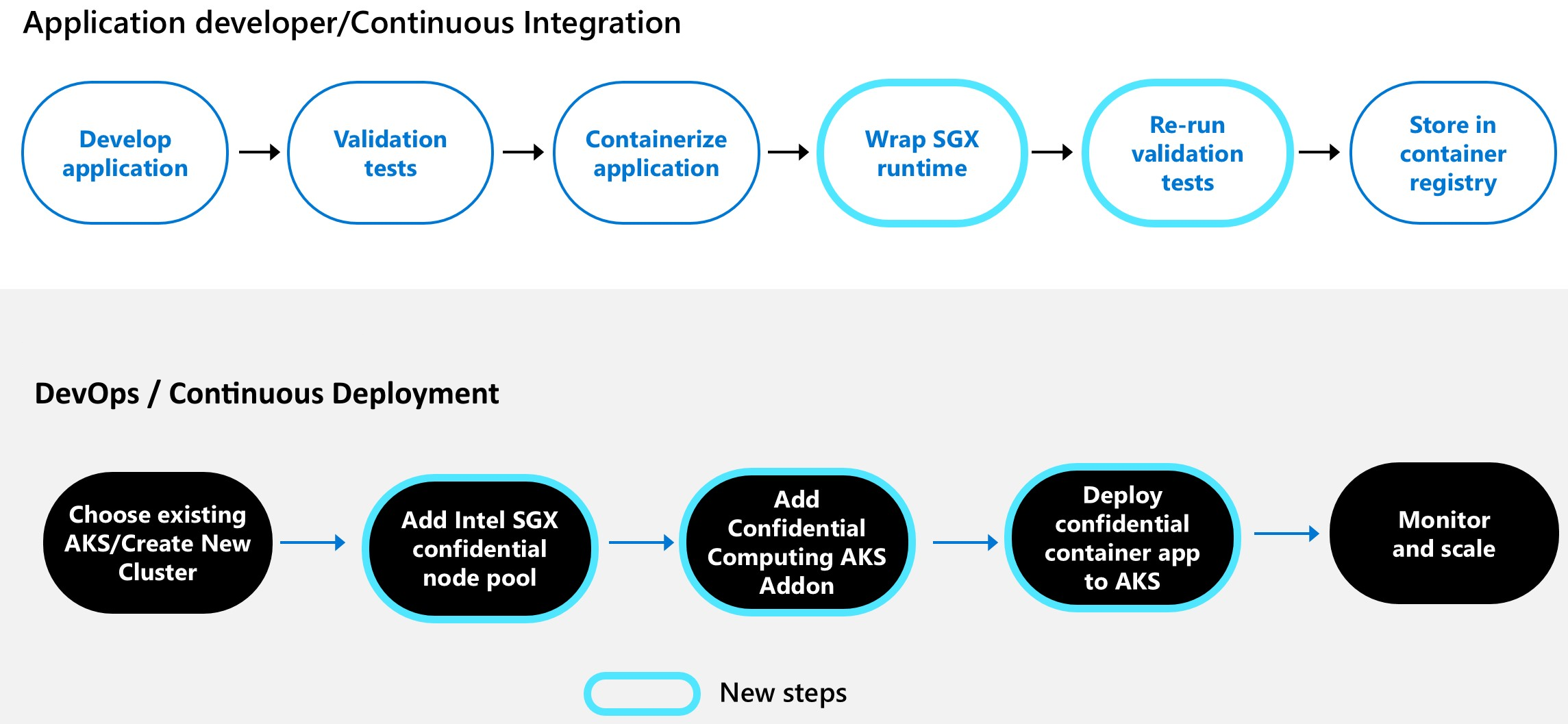
The SGX wrapper software needed to help run standard containers are offered by Azure software partners or Open Source Software (OSS)solutions.
Partner enablers
Developers can choose software providers based on their features, integration with Azure services and tooling support.
Important
Azure software partners often involve licensing fees on top of your Azure infrastructure. Please verify all partner software terms independently.
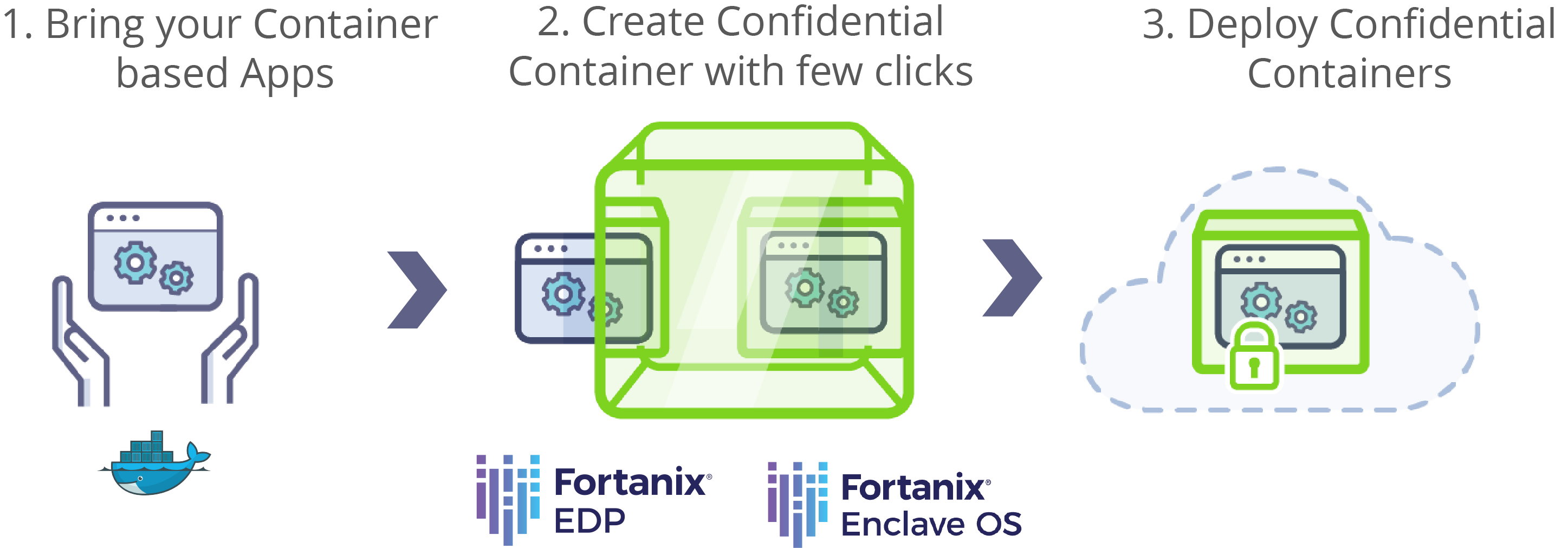
Fortanix
Fortanix has portal and Command Line Interface (CLI) experiences to convert their containerized applications to SGX-capable confidential containers. You don't need to modify or recompile the application. Fortanix provides the flexibility to run and manage a broad set of applications. You can use existing applications, new enclave-native applications, and pre-packaged applications. Start with Fortanix's Enclave Manager UI or REST APIs. Create confidential containers using the Fortanix's quickstart guide for AKS.
SCONE (Scontain)
SCONE (Scontain) security policies generate certificates, keys, and secrets. Only services with attestation for an application see these credentials. Application services automatically do attestation for each other through TLS. You don't need to modify the applications or TLS. For more explanation, see SCONE's Flask application demo.
SCONE can convert most existing binaries into applications that run inside enclaves. SCONE also protects interpreted languages like Python by encrypting both data files and Python code files. You can use SCONE security policies to protect encrypted files against unauthorized access, modifications, and rollbacks. For more information, see SCONE's documentation on how to use SCONE with an existing Python application.
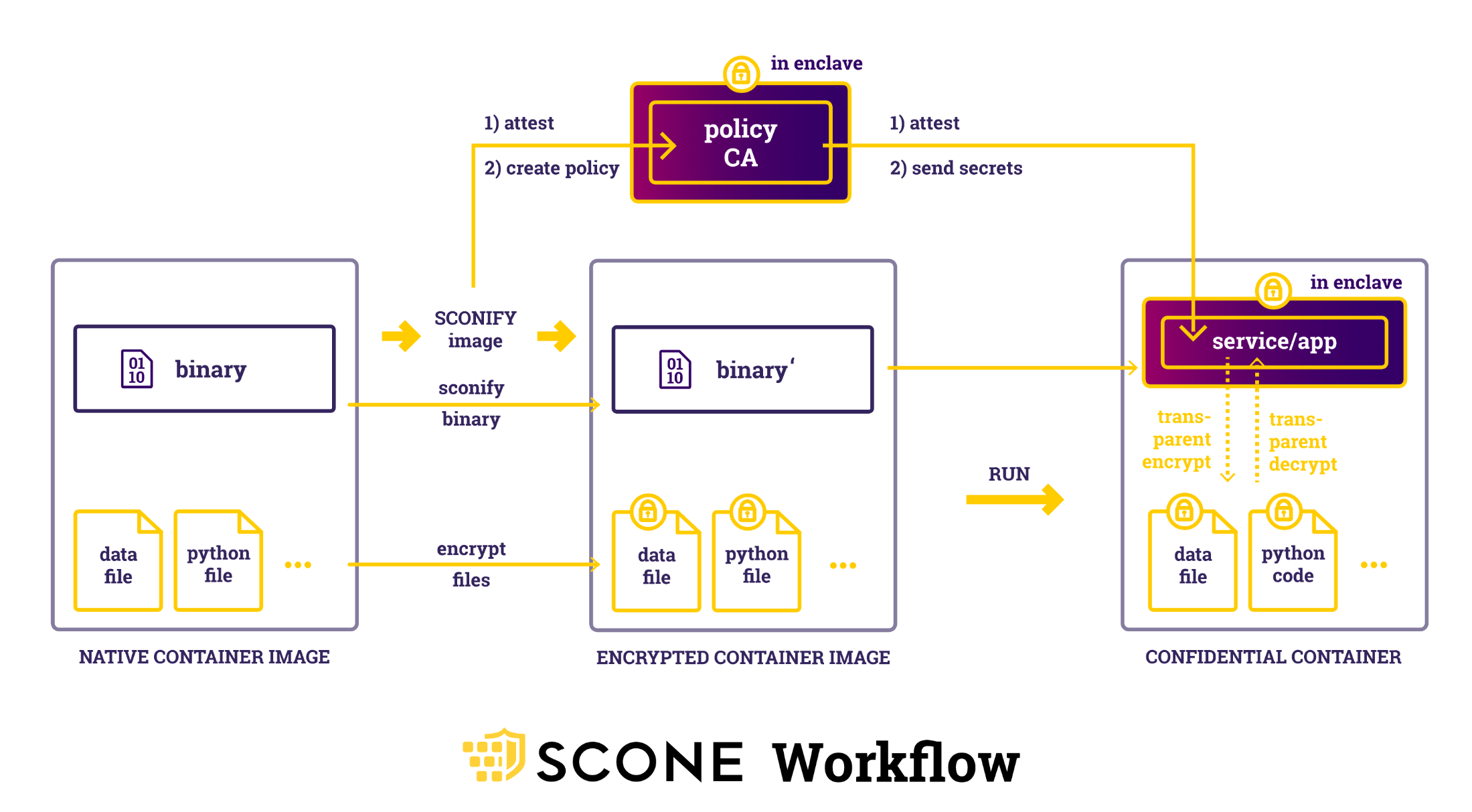
You can deploy SCONE on Azure confidential computing nodes with AKS following this SCONE sample AKS application deployment.
Anjuna
Anjuna provides SGX platform software to run unmodified containers on AKS. For more information, see Anjuna's documentation about functionality and sample applications.
Get started with a sample Redis Cache and Python Custom Application here
OSS enablers
Note
Azure confidential computing and Microsoft aren't directly affiliated with these projects and solutions.
Gramine
Gramine is a lightweight guest OS, designed to run a single Linux application with minimal host requirements. Gramine can run applications in an isolated environment. There's tooling support for converting existing Docker container to SGX ready containers.
For more information, see the Gramine's sample application and deployment on AKS
Occlum
Occlum is a memory-safe, multi-process library OS (LibOS) for Intel SGX. The OS enables legacy applications to run on SGX with little to no modifications to source code. Occlum transparently protects the confidentiality of user workloads while allowing an easy "lift and shift" to existing Docker applications.
For more information, see Occlum's deployment instructions and sample apps on AKS.
Marblerun
Marblerun is an orchestration framework for confidential containers. You can run and scale confidential services on SGX-enabled Kubernetes. Marblerun takes care of boilerplate tasks like verifying the services in your cluster, managing secrets for them, and establishing enclave-to-enclave mTLS connections between them. Marblerun also ensures that your cluster of confidential containers adheres to a manifest defined in simple JSON. You can verify the manifest with external clients through remote attestation.
This framework extends the confidentiality, integrity, and verifiability properties of a single enclave to a Kubernetes cluster.
Marblerun supports confidential containers created with Graphene, Occlum, and EGo, with examples for each SDK. The framework runs on Kubernetes alongside your existing cloud-native tooling. There's a CLI and helm charts. Marblerun also supports confidential computing nodes on AKS. Follow Marblerun's guide to deploy Marblerun on AKS.
Confidential Containers reference architectures
- Confidential data messaging for healthcare reference architecture and sample with Intel SGX confidential containers.
- Confidential big-data processing with Apache Spark on AKS with Intel SGX confidential containers.
Get in touch
Do you have questions about your implementation? Do you want to become an enabler for confidential containers? Send an email to acconaks@microsoft.com.