Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Outbound white listing of Fully Qualified Domain Names (FQDN) is a network security practice that allows organizations to control and restrict outbound traffic from their networks to specific, approved domain names.
Overview
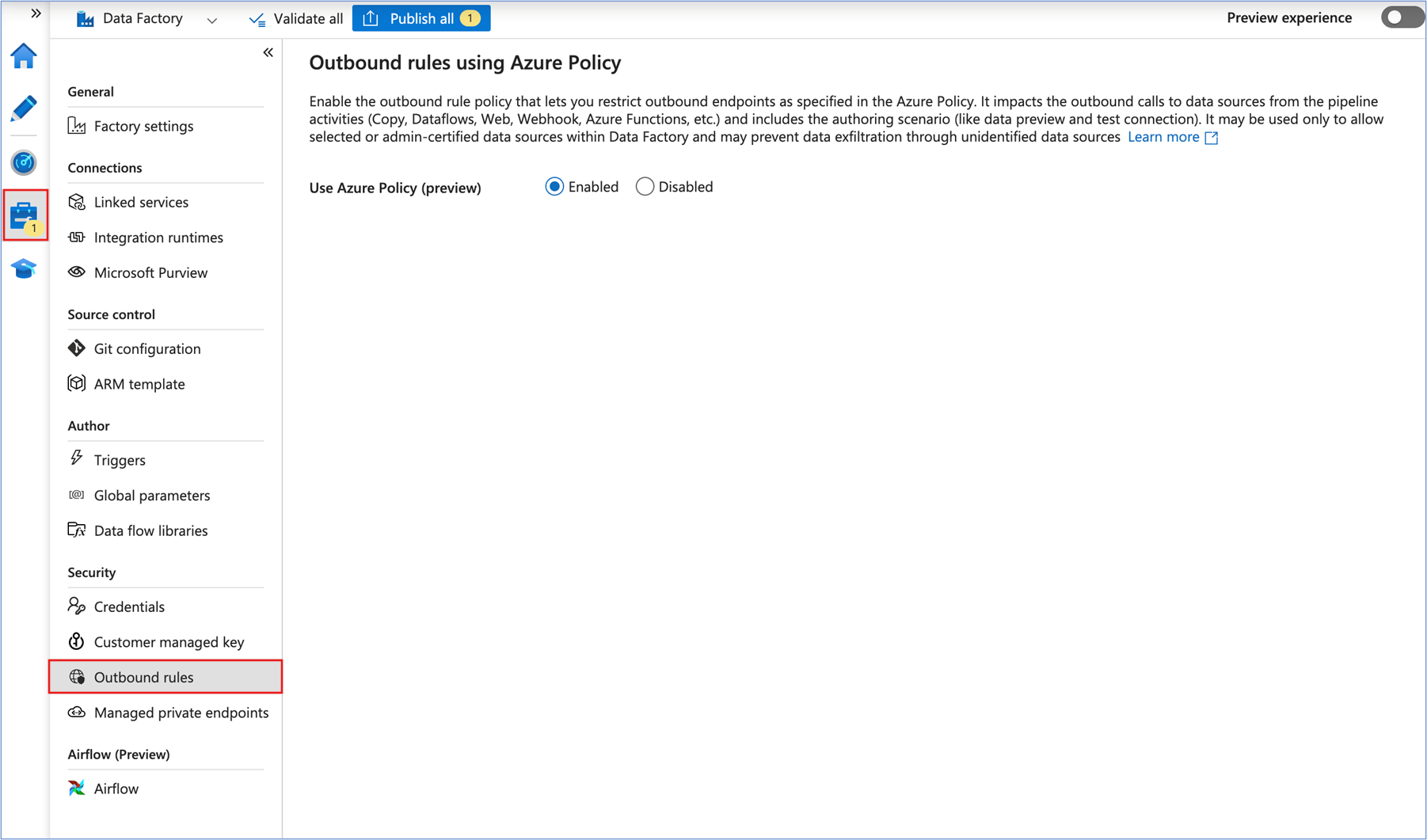
Outbound rules in Azure Data Factory are an effective way for users to limit outgoing traffic by specifying allowed Fully Qualified Domain Names (FQDN) or network endpoints. This critical feature offers network security administrators greater control, improving governance and preventing data exfiltration. Azure Policy is used to enforce these rules .
These outbound rules apply to various pipeline activities. This includes Copy, Dataflows, Web, Webhook, and Azure Function activities, as well as authoring scenarios like data preview and test connection. In addition to Managed VNet, these outbound rules help you build a secure and exfiltration-proof data integration solution.
Note
This feature is currently in preview.
Prerequisites
To apply an Azure Policy to Azure Data Factory, user needs to have the Resource Policy Contributor permission. This role can be assigned to the individual responsible for configuring policies for Data Factory.
Steps to enable Azure Policy for outbound rules
To apply policies to an Azure Data Factory instance, complete the following steps.
Navigate to a resource group that contains the Azure Data Factory instance.
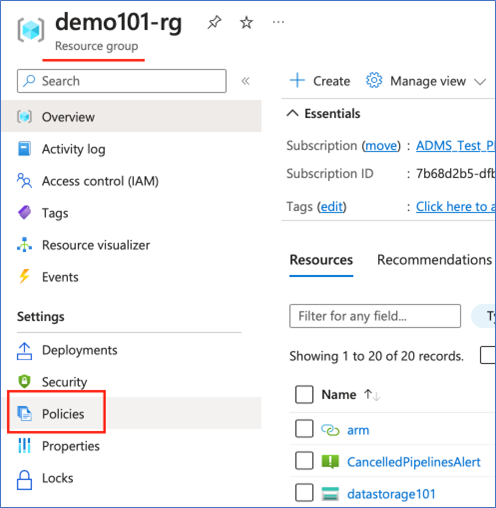
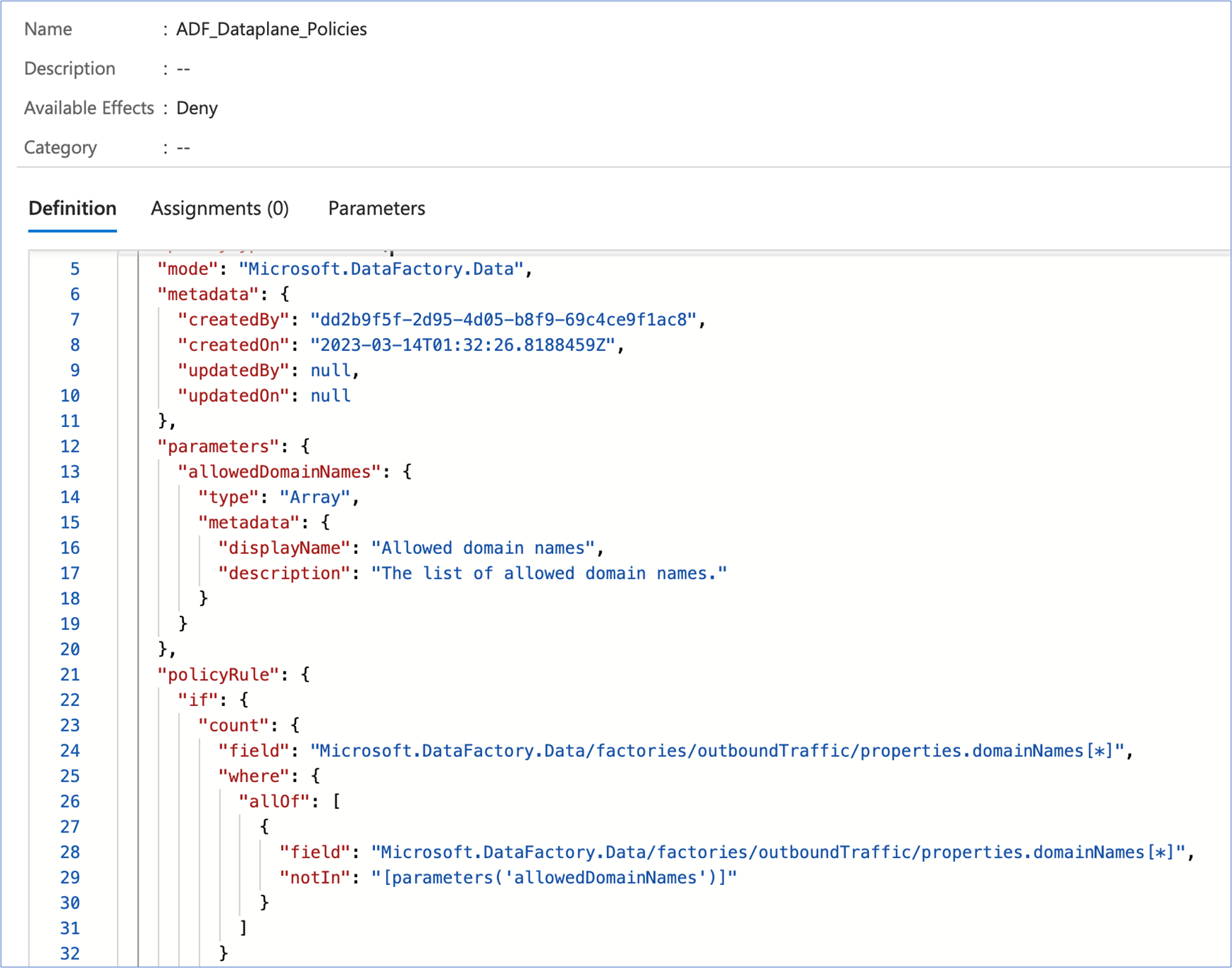
Select the policies tab on the left and then navigate to built-in policy definitions published by Microsoft. Select ADF_Dataplane_Policies - Microsoft Azure.
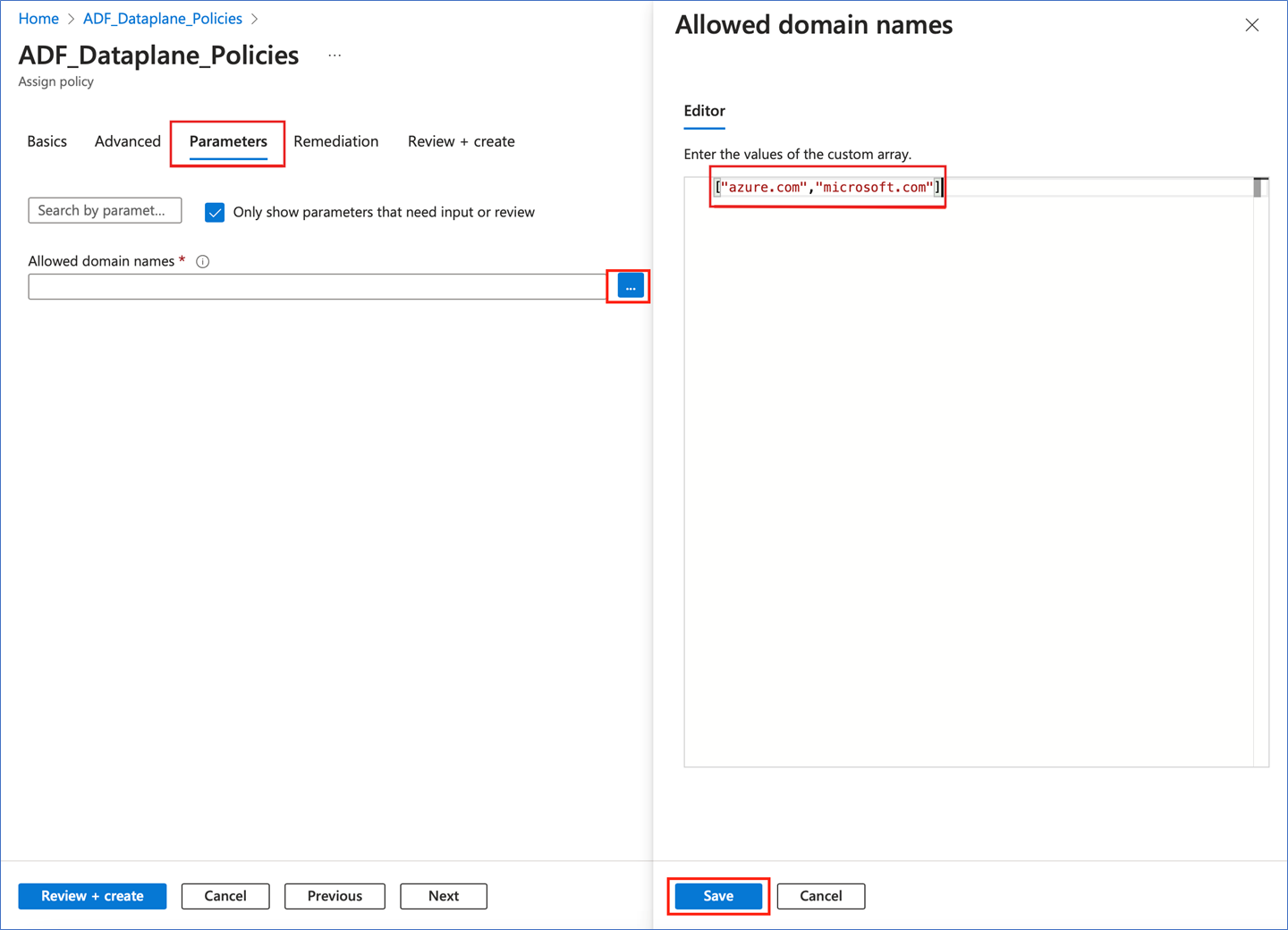
Assign the policy.
On the Parameters tab, provide the list of domain names that are trusted, then select Save.
Note
This is a JSON array and needs to be provided as shown in the image, with each domain in quotes, separated by commas, and the entire list surrounded by square brackets.
Review and create the policy.
Navigate to the Azure Data Factory Studio and enable outbound rules functionality by selecting the Manage tab on the left, and then Outbound rules.
Note
To update the allow-list to add new URLs, edit the policy parameters.
Known limitations
- Outbound policy rules aren't enforced for Airflow and SSIS scenarios.
- While configuring domain names, you must provide fully qualified domain names. Wildcard/regex patterns aren't supported in domain names. If you want to specify that both microsoft.com, & www.microsoft.com as trusted domains, then both need to be specified while configuring policy. For example: [“microsoft.com”, “www.microsoft.com”].
- Throttling limits applied in Azure Policy during the preview:
- For an individual Azure Data factory: 1,000 requests / 5 minutes. Only 1,000 activity runs can be executed in a 5-minute period. Subsequent run requests fail once this limit is reached.
- For a subscription: 50,000 requests / 5 minutes. Only 50,000 activity runs can be executed in a 5-minute period per subscription. Subsequent run requests fail once this limit is reached.
Related content
Check out the following article to learn more about the Azure security baseline: