Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Defender for Cloud's provides organizations the capability to perform external attack surface management (outside-in) scans to improve their security posture through its integration with Defender External Attack Surface Management. Defender for Cloud's external attack surface management scans uses the information provided by the Defender External Attack Surface Management integration to provide actionable recommendations and visualizations of attack paths to reduce the risk of bad actors exploiting internet exposed IP addresses.
Through the use Defender for Cloud's cloud security explorer, security teams can build queries and proactively hunt for security risks. Security teams can also use the attack path analysis to visualize the potential attack paths that an attacker could use to reach their critical assets.
Prerequisites
You need a Microsoft Azure subscription. If you don't have an Azure subscription, you can sign up for a free subscription.
You must enable the Defender Cloud Security Posture Management (CSPM) plan.
Detect internet exposed IP addresses with the cloud security explorer
The cloud security explorer allows you to build queries, such as an outside-in scan, that can proactively hunt for security risks in your environments, including IP addresses that are exposed to the internet.
Sign in to the Azure portal.
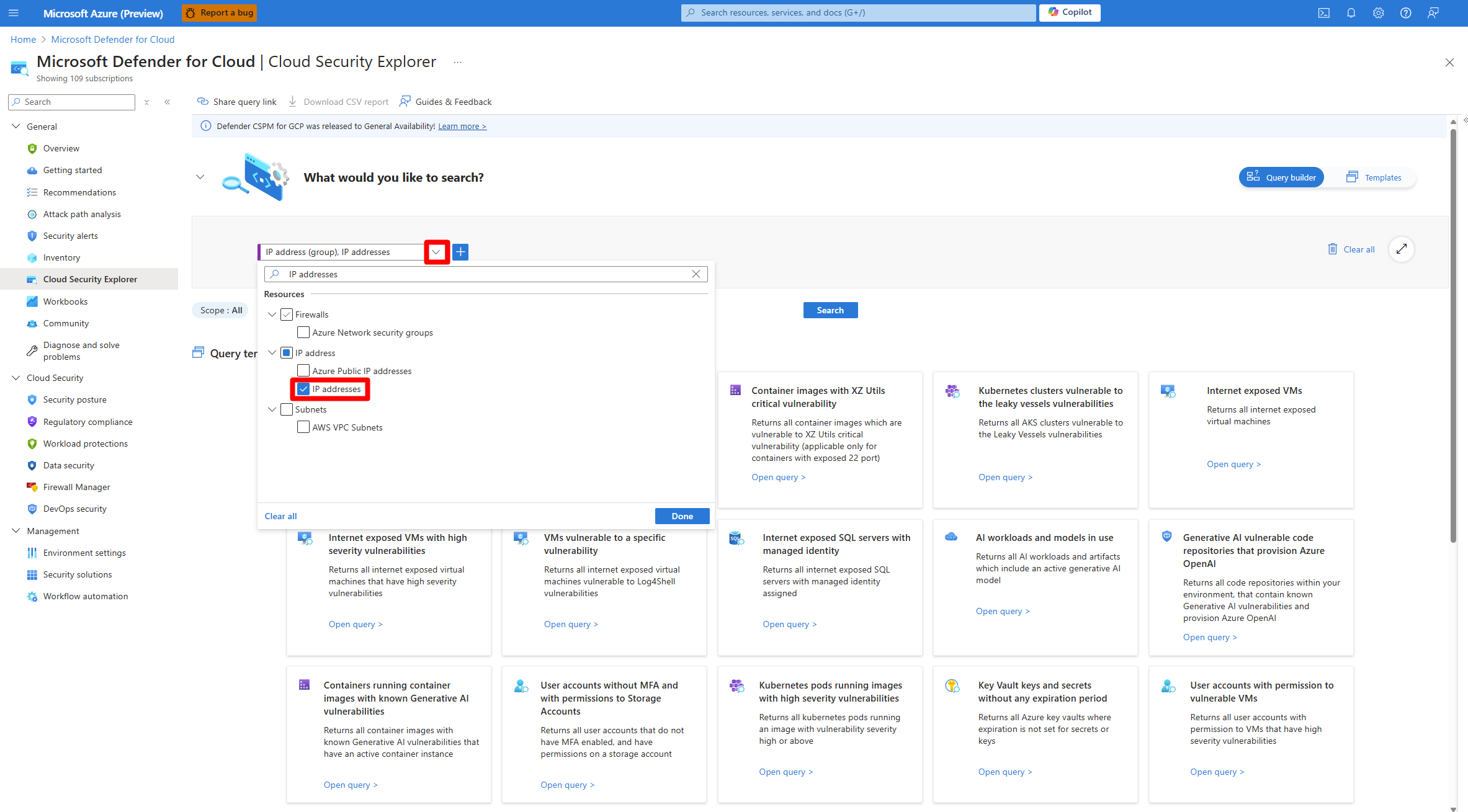
Search for and select Microsoft Defender for Cloud > Cloud security explorer.
In the dropdown menu, search for and select IP addresses.
Select Done.
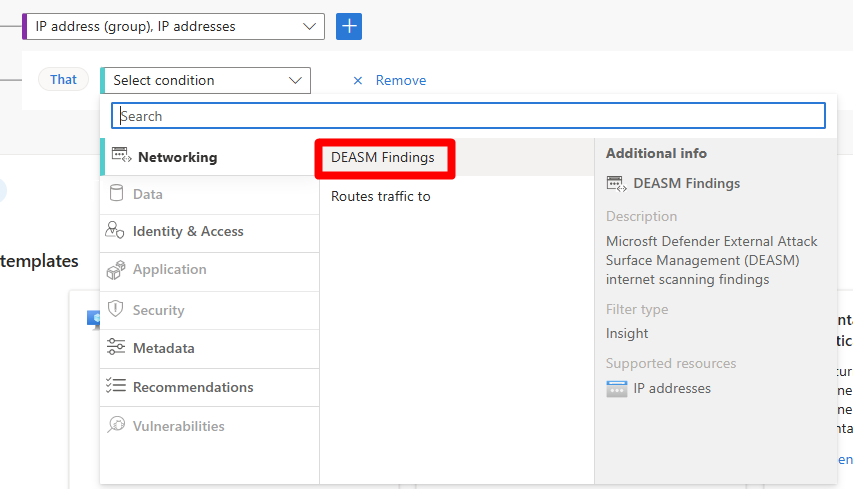
Select +.
In the select condition dropdown menu, select DEASM Findings.
Select the + button.
In the select condition dropdown menu, select Routes traffic to.
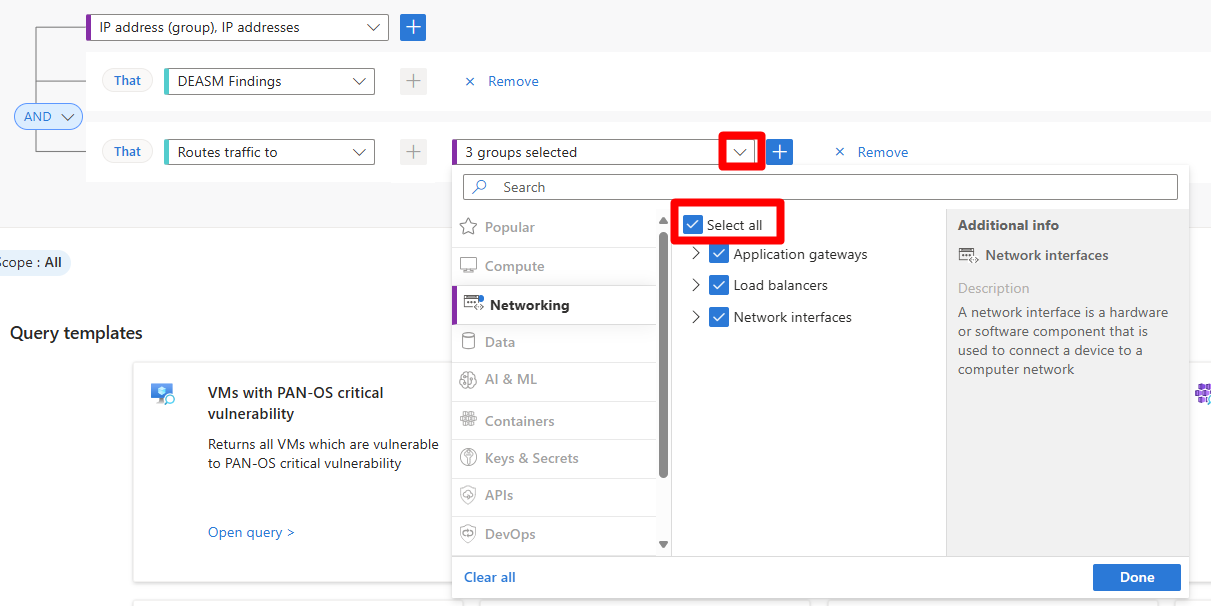
In the select resource type dropdown menu, select Select all.
Select Done.
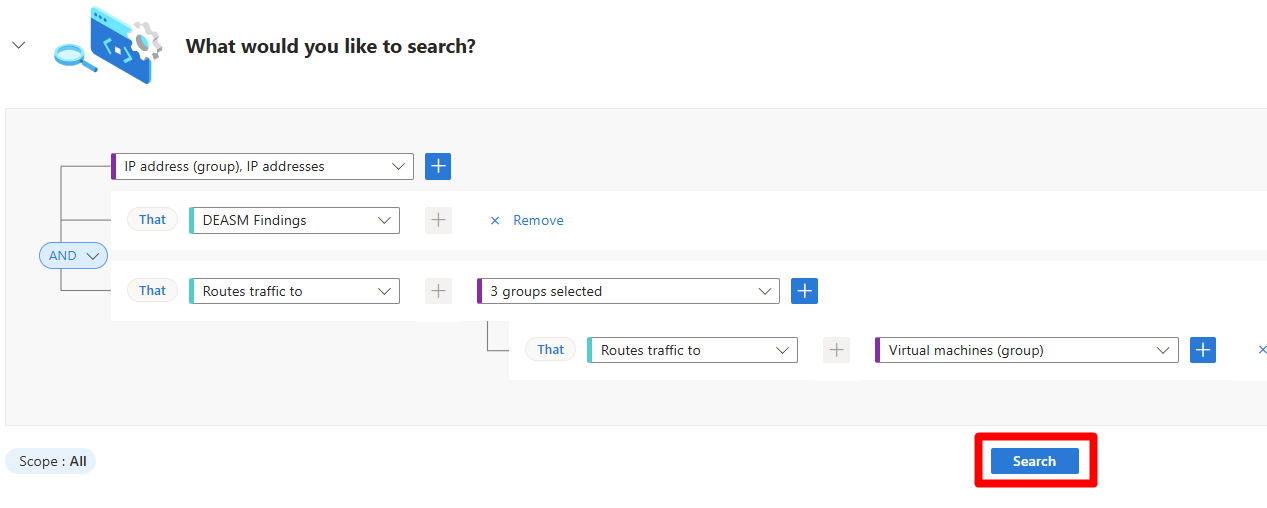
Select the + button.
In the select condition dropdown menu, select Routes traffic to.
In the select resource type dropdown menu, select Virtual machine.
Select Done.
Select Search.
Select a result to review the findings.
Detect exposed IP addresses with attack path analysis
Using the attack path analysis, you can view a visualization of the attack paths that an attacker could use to reach your critical assets.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud > Attack path analysis.
Search for Internet exposed.
Review and select a result.