Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Note
Effective April 1, 2025, Microsoft Entra Permissions Management will no longer be available for purchase.
On October 1, 2025, Microsoft will retire and discontinue support for this product. Learn more about the retirement of Microsoft Entra Permissions Management.
The deprecation of Microsoft Entra Permissions Management doesn't affect any existing CIEM capabilities in Microsoft Defender for Cloud. Learn more about the future of CIEM in Microsoft Defender for Cloud.
Microsoft Defender for Cloud provides a cloud infrastructure entitlement management (CIEM) security model that helps organizations manage and control user access and entitlements in their cloud infrastructure. CIEM is a critical component of the Cloud Native Application Protection Platform (CNAPP) solution that provides visibility into who or what has access to specific resources. It ensures that access rights adhere to the principle of least privilege (PoLP), where users or workload identities, such as apps and services, receive only the minimum levels of access necessary to perform their tasks. CIEM also helps organizations to monitor and manage permissions across multiple cloud environments, including Azure, AWS, and GCP.
Before you start
You must enable Defender CSPM on your Azure subscription, AWS account, or GCP project.
You must have the following Azure roles and permissions, depending on the cloud environment, to enable the Permissions Management (CIEM) extension of Defender CSPM:
- AWS and GCP: Security Admin role and Application.ReadWrite.All permission for your tenant.
- Azure: Security Admin role and Microsoft.Authorization/roleAssignments/write permission for the subscription.
Enable CIEM for Azure
When you enabled the Defender CSPM plan on your Azure account, the Azure CSPM standard is automatically assigned to your subscription. The Azure CSPM standard provides Cloud Infrastructure Entitlement Management (CIEM) recommendations.
When Permissions Management (CIEM) is disabled, the CIEM recommendations within the Azure CSPM standard aren't calculated.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud.
Navigate to Environment settings.
Select relevant subscription.
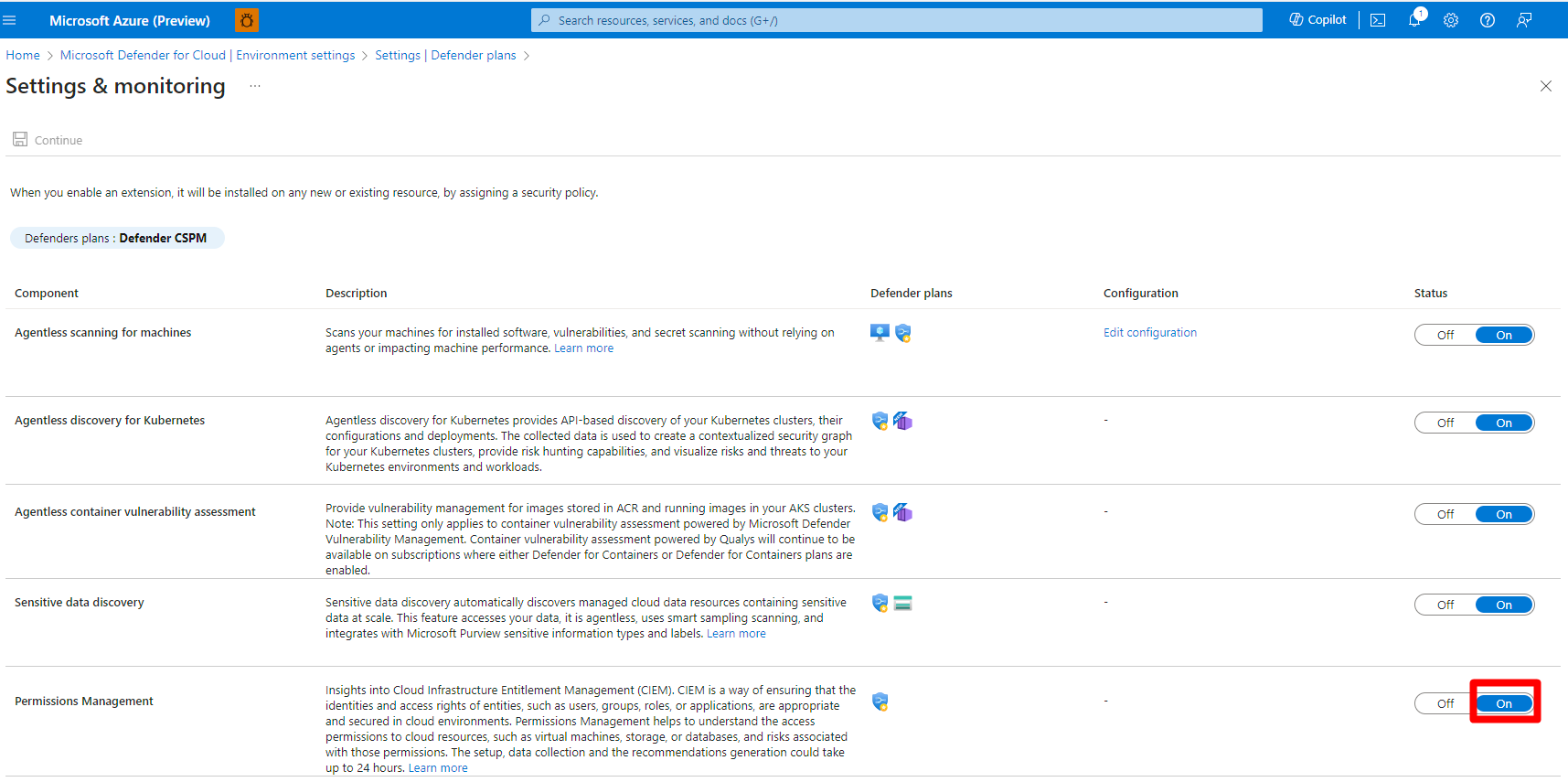
Locate the Defender CSPM plan and select Settings.
Enable Permissions Management (CIEM).
Select Continue.
Select Save.
The applicable CIEM recommendations appear on your subscription within a few hours.
List of Azure recommendations:
Azure overprovisioned identities should have only the necessary permissions
Permissions of inactive identities in your Azure subscription should be revoked
Enable CIEM for AWS
When you enabled the Defender CSPM plan on your AWS account, the AWS CSPM standard is automatically assigned to your subscription. The AWS CSPM standard provides Cloud Infrastructure Entitlement Management (CIEM) recommendations. When Permission Management is disabled, the CIEM recommendations within the AWS CSPM standard aren't calculated.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud.
Navigate to Environment settings.
Select relevant AWS account.
Locate the Defender CSPM plan and select Settings.
Enable Permissions Management (CIEM).
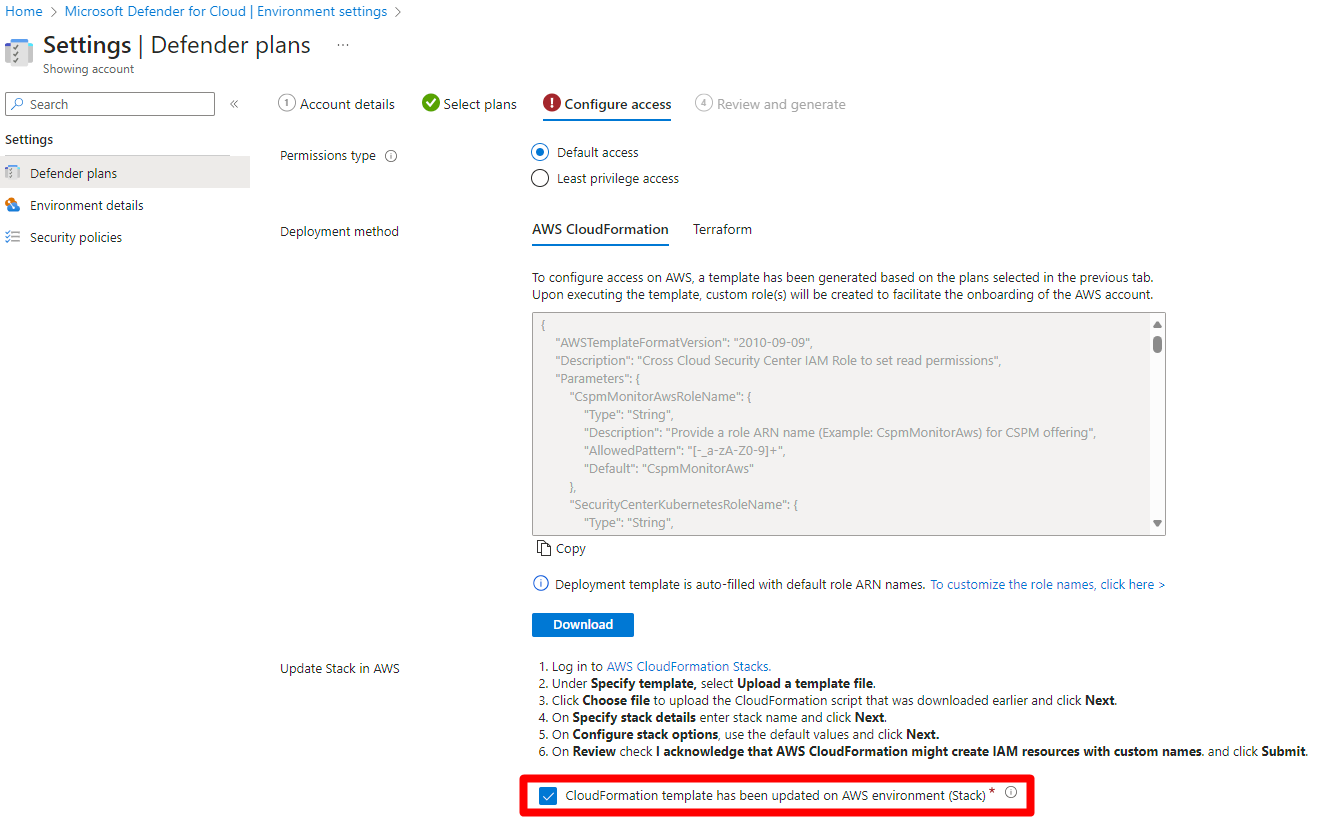
Select Configure access.
Select a deployment method.
Run the updated script on your AWS environment using the onscreen instructions.
Check the CloudFormation template has been updated on AWS environment (Stack) checkbox.
Select Review and generate.
Select Update.
The applicable CIEM recommendations appear on your subscription within a few hours.
List of AWS recommendations:
AWS overprovisioned identities should have only the necessary permissions
Permissions of inactive identities in your AWS account should be revoked
Enable CIEM for GCP
When you enabled the Defender CSPM plan on your GCP project, the GCP CSPM standard is automatically assigned to your subscription. The GCP CSPM standard provides Cloud Infrastructure Entitlement Management (CIEM) recommendations.
When Permissions Management (CIEM) is disabled, the CIEM recommendations within the GCP CSPM standard aren't calculated.
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud.
Navigate to Environment settings.
Select relevant GCP project.
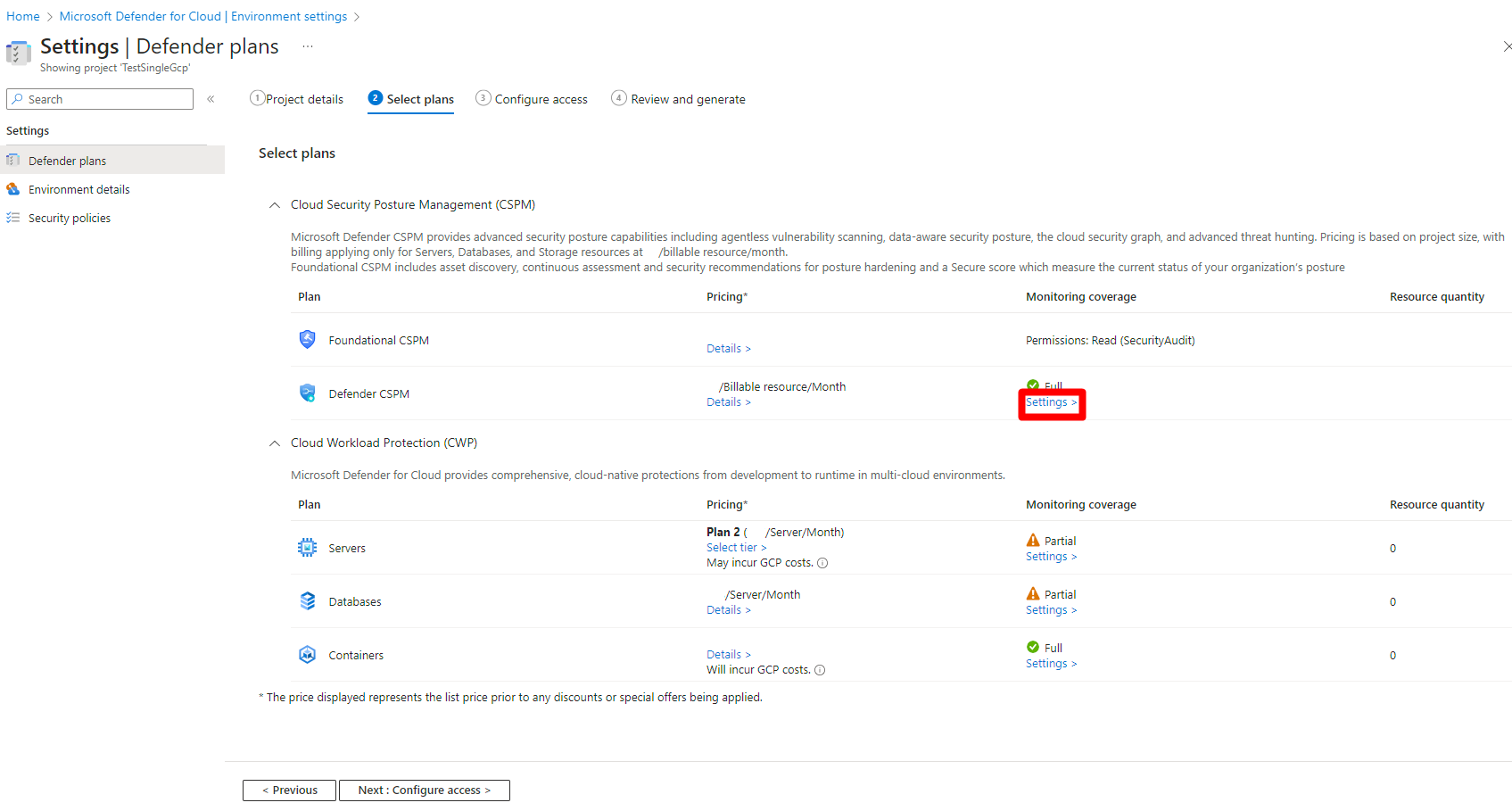
Locate the Defender CSPM plan and select Settings.
Toggle Permissions Management (CIEM) to On.
Select Save.
Select Next: Configure access.
Select the relevant permissions type.
Select a deployment method.
Run the updated Cloud shell or Terraform script on your GCP environment using the on screen instructions.
Add a check to the I ran the deployment template for the changes to take effect checkbox.
Select Review and generate.
Select Update.
The applicable CIEM recommendations appear on your subscription within a few hours.
List of GCP recommendations:
GCP overprovisioned identities should have only necessary permissions
Permissions of inactive identities in your GCP project should be revoked
Known limitations
AWS and GCP accounts that were onboarded to Permissions Management before being onboarded to Defender for Cloud can't be integrated through Microsoft Defender for Cloud.