Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Security DevOps is a command line application that integrates static analysis tools into the development lifecycle. Security DevOps installs, configures, and runs the latest versions of static analysis tools such as, SDL, security and compliance tools. Security DevOps is data-driven with portable configurations that enable deterministic execution across multiple environments.
Microsoft Security DevOps uses the following Open Source tools:
| Name | Language | License |
|---|---|---|
| AntiMalware | AntiMalware protection in Windows from Microsoft Defender for Endpoint, that scans for malware and breaks the build if malware has been found. This tool scans by default on windows-latest agent. | Not Open Source |
| Bandit | Python | Apache License 2.0 |
| BinSkim | Binary--Windows, ELF | MIT License |
| Checkov | Terraform, Terraform plan, CloudFormation, AWS SAM, Kubernetes, Helm charts, Kustomize, Dockerfile, Serverless, Bicep, OpenAPI, ARM | Apache License 2.0 |
| ESlint | JavaScript | MIT License |
| Template Analyzer | ARM Template, Bicep | MIT License |
| Terrascan | Terraform (HCL2), Kubernetes (JSON/YAML), Helm v3, Kustomize, Dockerfiles, CloudFormation | Apache License 2.0 |
| Trivy | container images, Infrastructure as Code (IaC) | Apache License 2.0 |
Prerequisites
An Azure subscription If you don’t have an Azure subscription, create a free account before you begin.
Open the Microsoft Security DevOps GitHub action in a new window.
Ensure that Workflow permissions are set to Read and Write on the GitHub repository. This includes setting "id-token: write" permissions in the GitHub Workflow for federation with Defender for Cloud.
Configure the Microsoft Security DevOps GitHub action
To setup GitHub action:
Sign in to GitHub.
Select a repository you want to configure the GitHub action to.
Select Actions.
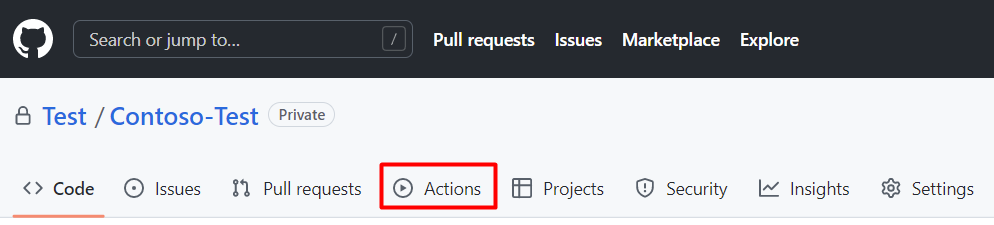
Select New workflow.
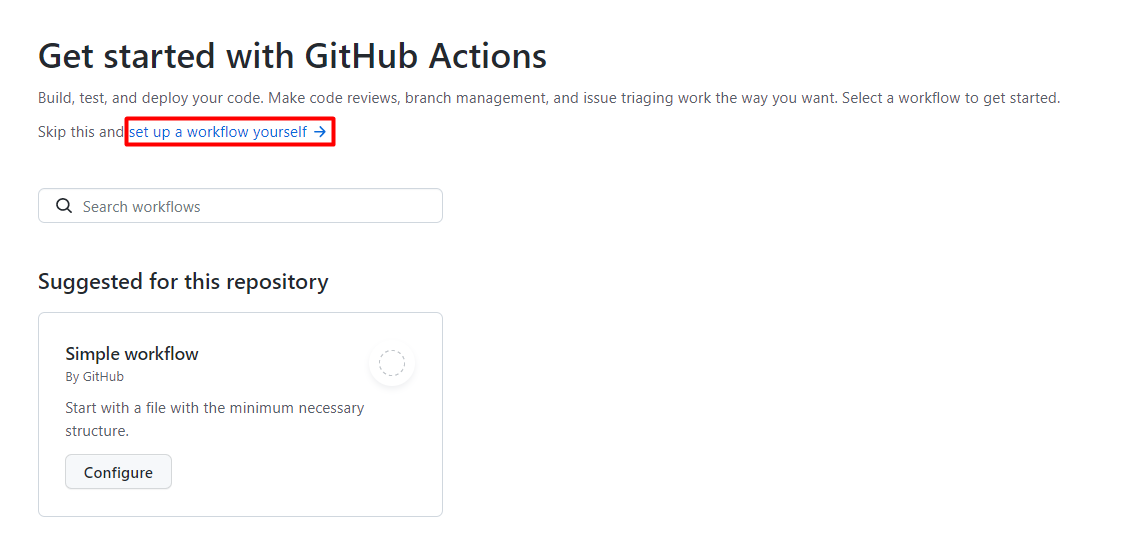
On the Get started with GitHub Actions page, select set up a workflow yourself
In the text box, enter a name for your workflow file. For example,
msdevopssec.yml.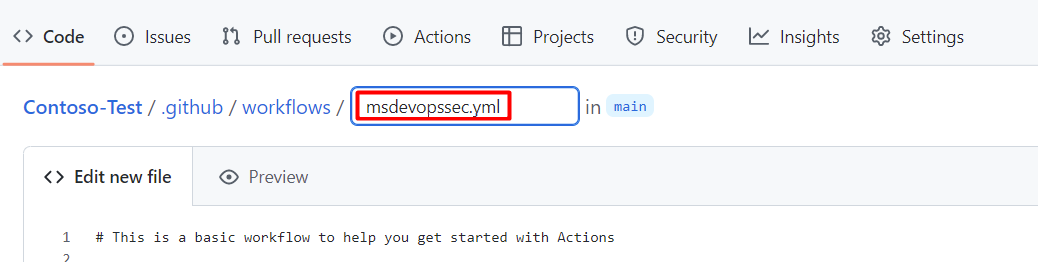
Copy and paste the following sample action workflow into the Edit new file tab.
name: MSDO on: push: branches: - main jobs: sample: name: Microsoft Security DevOps # Windows and Linux agents are supported runs-on: windows-latest permissions: contents: read id-token: write actions: read # Write access for security-events is only required for customers looking for MSDO results to appear in the codeQL security alerts tab on GitHub (Requires GHAS) security-events: write steps: # Checkout your code repository to scan - uses: actions/checkout@v3 # Run analyzers - name: Run Microsoft Security DevOps uses: microsoft/security-devops-action@latest id: msdo # with: # config: string. Optional. A file path to an MSDO configuration file ('*.gdnconfig'). # policy: 'GitHub' | 'microsoft' | 'none'. Optional. The name of a well-known Microsoft policy. If no configuration file or list of tools is provided, the policy may instruct MSDO which tools to run. Default: GitHub. # categories: string. Optional. A comma-separated list of analyzer categories to run. Values: 'code', 'artifacts', 'IaC', 'containers'. Example: 'IaC, containers'. Defaults to all. # languages: string. Optional. A comma-separated list of languages to analyze. Example: 'javascript,typescript'. Defaults to all. # tools: string. Optional. A comma-separated list of analyzer tools to run. Values: 'bandit', 'binskim', 'checkov', 'eslint', 'templateanalyzer', 'terrascan', 'trivy'. # Upload alerts to the Security tab - required for MSDO results to appear in the codeQL security alerts tab on GitHub (Requires GHAS) # - name: Upload alerts to Security tab # uses: github/codeql-action/upload-sarif@v3 # with: # sarif_file: ${{ steps.msdo.outputs.sarifFile }} # Upload alerts file as a workflow artifact - required for MSDO results to appear in the codeQL security alerts tab on GitHub (Requires GHAS) # - name: Upload alerts file as a workflow artifact # uses: actions/upload-artifact@v3 # with: # name: alerts # path: ${{ steps.msdo.outputs.sarifFile }}Note
For additional tool configuration options and instructions, see the Microsoft Security DevOps wiki
Select Start commit
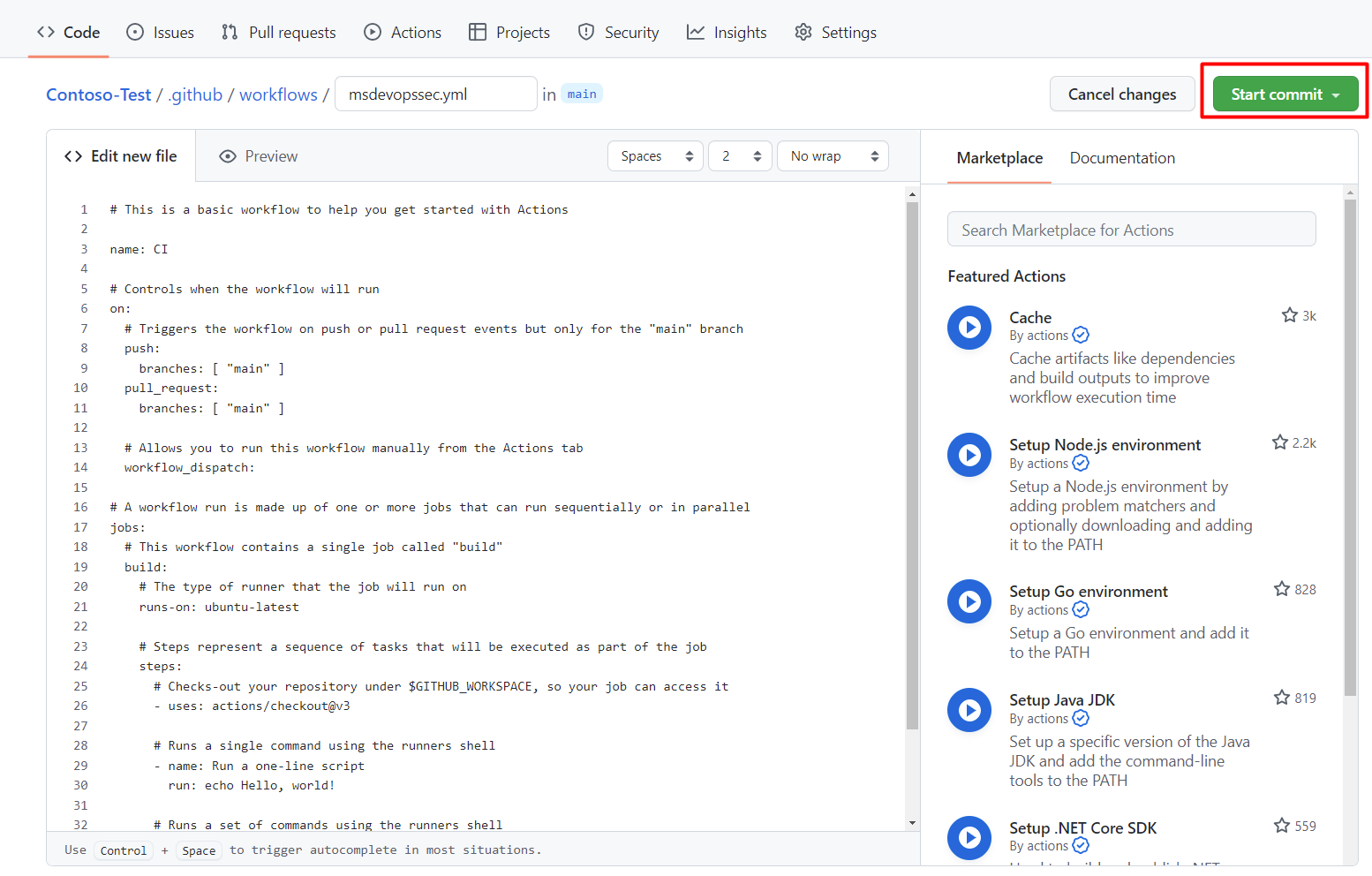
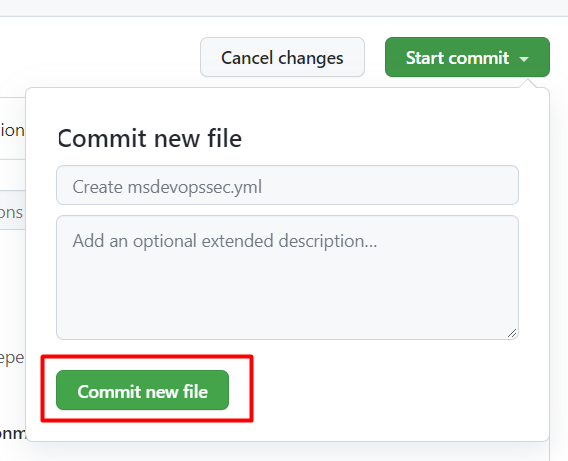
Select Commit new file. Note that the process can take up to one minute to complete.
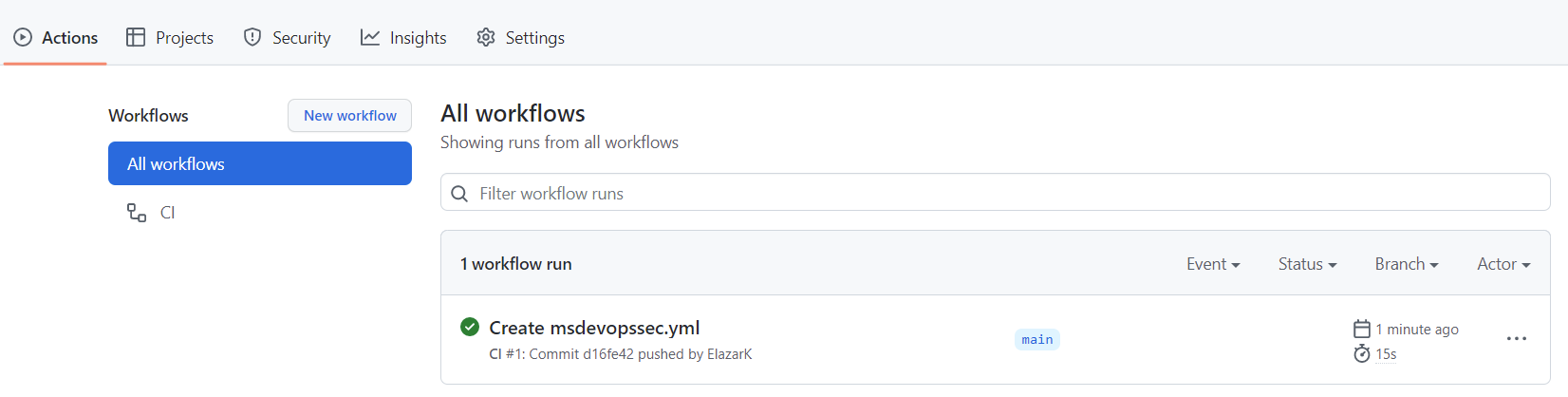
Select Actions and verify the new action is running.
View Scan Results
To view your scan results:
Sign in to Azure.
Navigate to Defender for Cloud > DevOps Security.
From the DevOps security blade, you should begin seeing the same MSDO security results developers see in their CI logs within minutes for the associated repository. Customers with GitHub Advanced Security will see the findings ingested from these tools as well.
Learn more
Learn about GitHub actions for Azure.
Learn how to deploy apps from GitHub to Azure.
Next steps
Learn more about DevOps security in Defender for Cloud.
Learn how to connect your GitHub Organizations to Defender for Cloud.