Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Defender for Cloud is unifying all vulnerability assessment solutions to use the Microsoft Defender Vulnerability Management vulnerability scanner.
Microsoft Defender Vulnerability Management integrates across many cloud native use cases, such as containers ship and runtime scenarios.
The Defender for Cloud Containers Vulnerability Assessment powered by Qualys is now retired. If you haven't transitioned yet toVulnerability assessments for Azure with Microsoft Defender Vulnerability Management, follow the steps on the page to make the transition.
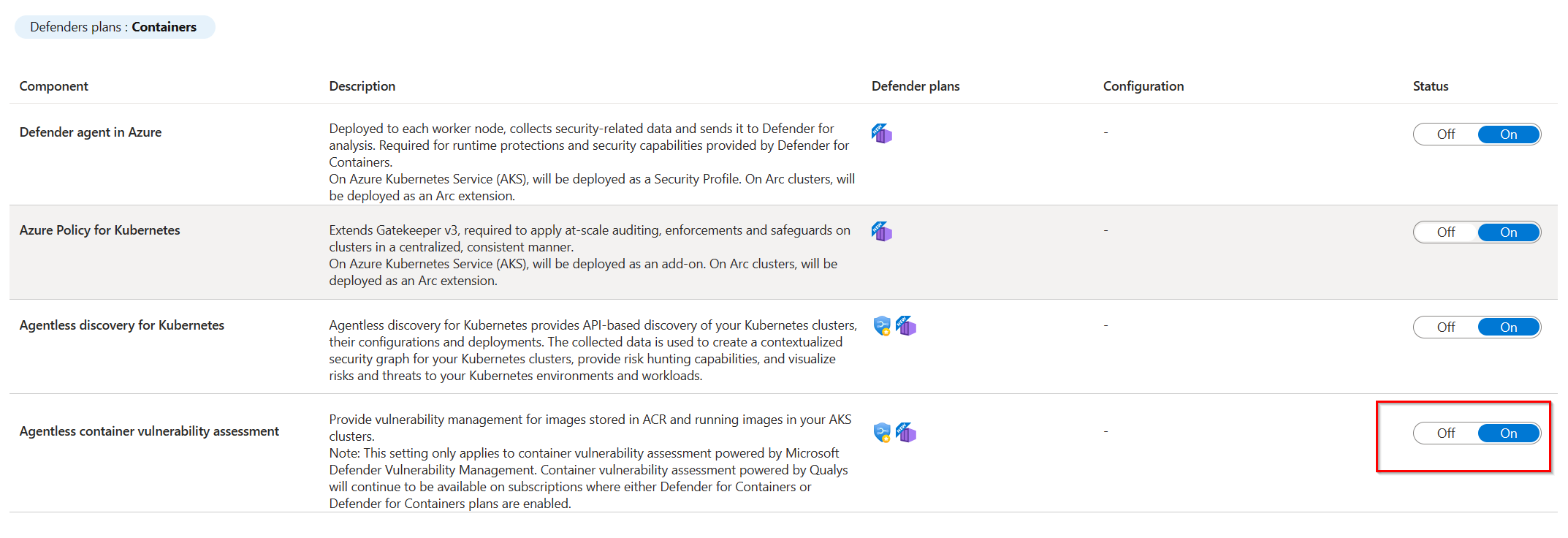
Step 1: Verify that scanning is enabled
Container vulnerability assessment scanning powered by Microsoft Defender Vulnerability Management is enabled by default for Defender for Containers, Defender for Container Registries (deprecated) and Defender Cloud Security Posture Management. Organizations that disabled it need to re-enable the Agentless container vulnerability assessment toggle in one of the plans. It reflects automatically to any of the mentioned plans enabled.
For more information on enabling Microsoft Defender Vulnerability Management scanning, see Enable vulnerability assessment powered by Microsoft Defender Vulnerability Management.
Step 2: (Optional) Update REST API and Azure Resource Graph queries
If you were accessing container vulnerability assessment results by Qualys programmatically, either via the Azure Resource Graph (ARG) Rest API or Subassessment REST API or ARG queries, you need to update your existing queries to match the new schema and/or REST API provided by the new container vulnerability assessment powered by Microsoft Defender Vulnerability Management.
The next section includes a few examples that can help in understanding how existing queries for the Qualys powered offering should be translated to equivalent queries with the Microsoft Defender Vulnerability Management powered offering.
ARG query examples
Any Azure Resource Graph queries used for reporting should be updated to reflect the Microsoft Defender Vulnerability Management assessmentKeys listed previously. The following are examples to help you transition to Microsoft Defender Vulnerability Management queries.
Show unhealthy container images
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.status.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.displayName,
patchable = properties.additionalData.patchable,
cve = properties.additionalData.cve,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Unhealthy'
Microsoft Defender Vulnerability Management
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
severity = properties.additionalData.vulnerabilityDetails.severity,
status = properties.status.code,
VulnId = properties.id,
description = properties.description,
fixStatus = properties.additionalData.softwareDetails.fixStatus,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Unhealthy'
Show healthy container images
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.repositoryName,
imageDigest = properties.additionalData.imageDigest
| where status == 'Healthy'
Microsoft Defender Vulnerability Management
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| project
Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id)),
ResourceType = tolower(split(id,"/").[6]),
subscriptionId,
status = properties.status.code,
Repo = properties.additionalData.artifactDetails.repositoryName,
imageUri = properties.resourceDetails.id
| where status == 'Healthy'
Count vulnerable images by severity
Qualys
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend status = tostring(parse_json(properties).status.code)
| extend severity = tostring(parse_json(properties).status.severity)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "dbd0cb49-b563-45e7-9724-889e799fa648"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
Microsoft Defender Vulnerability Management
securityresources
| where type == "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(".*assessments/(.+?)/.*",1, id)
| extend severity = tostring(properties.additionalData.vulnerabilityDetails.severity)
| extend status = tostring(parse_json(properties).status.code)
| extend vulId=tostring((properties).id)
| extend Resource = tolower(extract(@'(?i)(.*?)/providers/Microsoft.Security/([^/]+)', 1, id))
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| where status == 'Unhealthy'
| distinct
vulId,
severity
| summarize count=count() by tostring(severity)
View pod, container, and namespace for a running vulnerable image on the AKS cluster
Qualys
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey = extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id),
subAssessmentId = tostring(properties.id),
parentResourceId = extract("(.+)/providers/Microsoft.Security", 1, id)
| extend resourceId = extract(@'(?i)(.*?)@([^/]+)', 1,tostring(properties.resourceDetails.id))
| extend severity = tostring(parse_json(properties).status.severity)
| extend VulnId = tostring(parse_json(properties).id)
| extend status = tostring(parse_json(properties).status.code)
| where assessmentKey == "41503391-efa5-47ee-9282-4eff6131462c"
| extend resourceId = tostring(properties.resourceDetails.id),
parsedJson = parse_json(tostring(properties.additionalData))
| extend containerData = parse_json(tostring(parsedJson.data.Containers))
| mv-expand containerDetails = containerData to typeof(dynamic)
| extend ContainerName = tostring(containerDetails.Name),
ContainerPod = tostring(containerDetails.Pod.Name),
Namespace = tostring(containerDetails.Pod.Namespace),
ControllerType = tostring(containerDetails.Pod.ControllerType),
ControllerName = tostring(containerDetails.Pod.ControllerName)
| where status == 'Unhealthy'
|project Image=resourceId, VulnId,severity, Namespace, ContainerName, ContainerPod,ControllerName,ControllerType
Microsoft Defender Vulnerability Management
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| extend azureClusterId = tostring(properties.additionalData.clusterDetails.clusterResourceId)
| extend cve =tostring(properties.id)
| extend status = properties.status.code
| extend severity=tostring(parse_json(properties).additionalData.vulnerabilityDetails.severity)
| where status == "Unhealthy"
| extend azureImageId = tostring(properties.resourceDetails.id)
| extend severity = tolower(properties.additionalData.vulnerabilityDetails.severity)
| extend kubernetesContext = properties.additionalData.kubernetesContext
| mv-expand workload = kubernetesContext.workloads
| mv-expand OwnedResource = workload.ownedResources
| mv-expand OwnedContainer = OwnedResource.containers
| mv-expand Container = workload.containers
| extend isController = isnotempty(workload.ownedResources)
| extend namespace = tostring(workload.namespace)
| extend podName = iff(isController, tostring(OwnedResource.name), workload.name)
| extend containerName = iff(isController, tostring(OwnedContainer.name), Container.name)
| extend controllerName = iff(isController, tostring(workload.name),"")
| extend controllerType = iff(isController, tostring(workload.kind),"")
| extend imageName = extract("(.+)@sha256:", 1, azureImageId)
| project imageName, cve, severity, clusterId = azureClusterId, containerName, podName, controllerName, controllerType, namespace
Step 3: (Optional) Container Security reporting
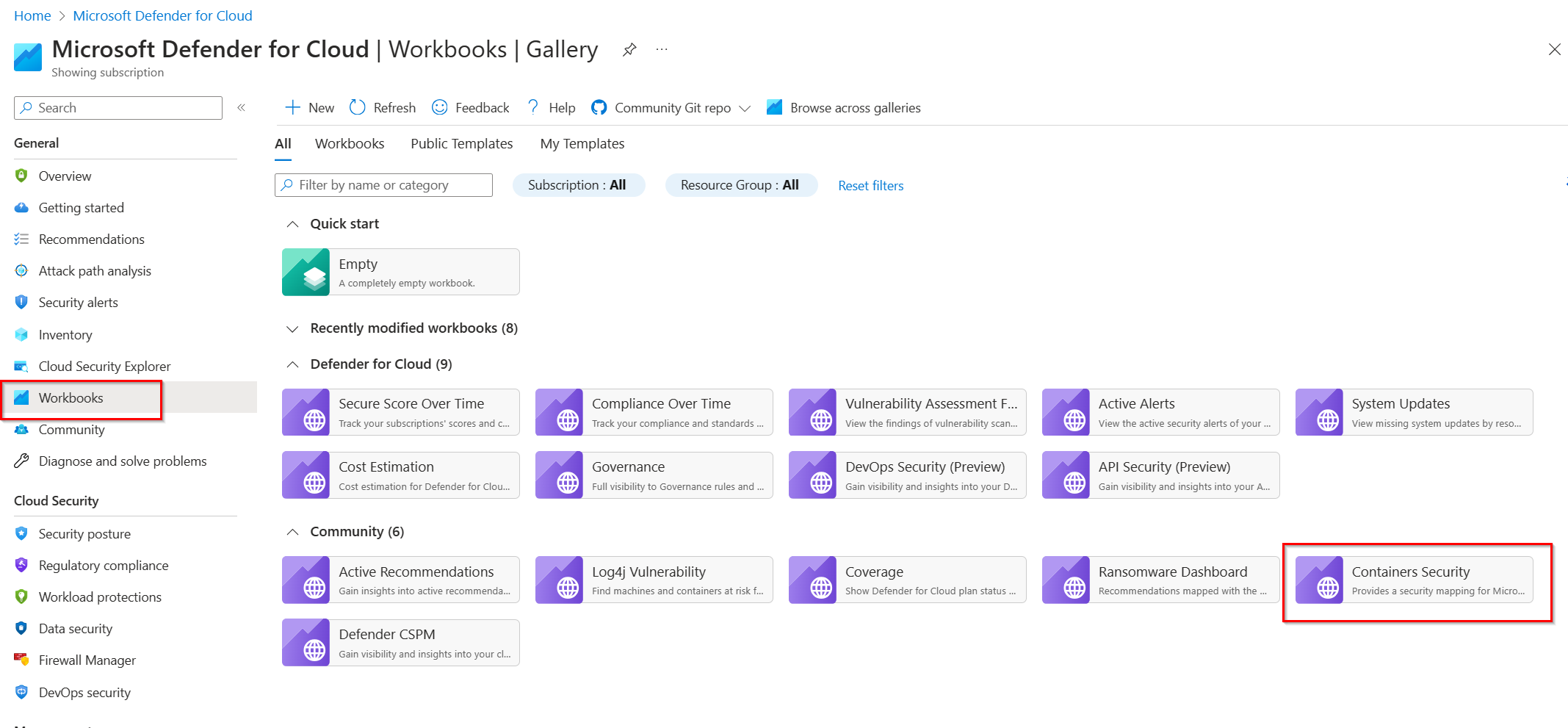
Microsoft Defender for Cloud provides out of the box reporting via Azure Workbooks, including a Container Security workbook.
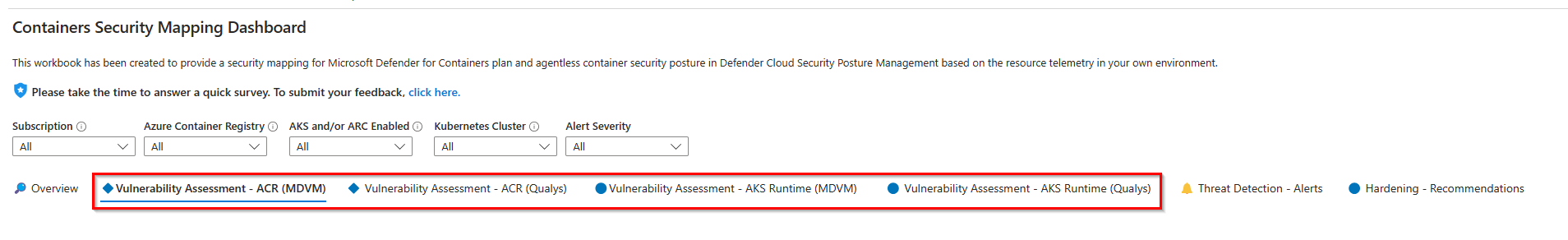
This workbook includes container vulnerability scanning results from both registry and runtime.
The workbook provides results from Microsoft Defender Vulnerability Management scanning, offering a comprehensive overview of vulnerabilities detected within your Azure Registry container images. The Containers Security workbook provides the following benefits for container vulnerability assessment:
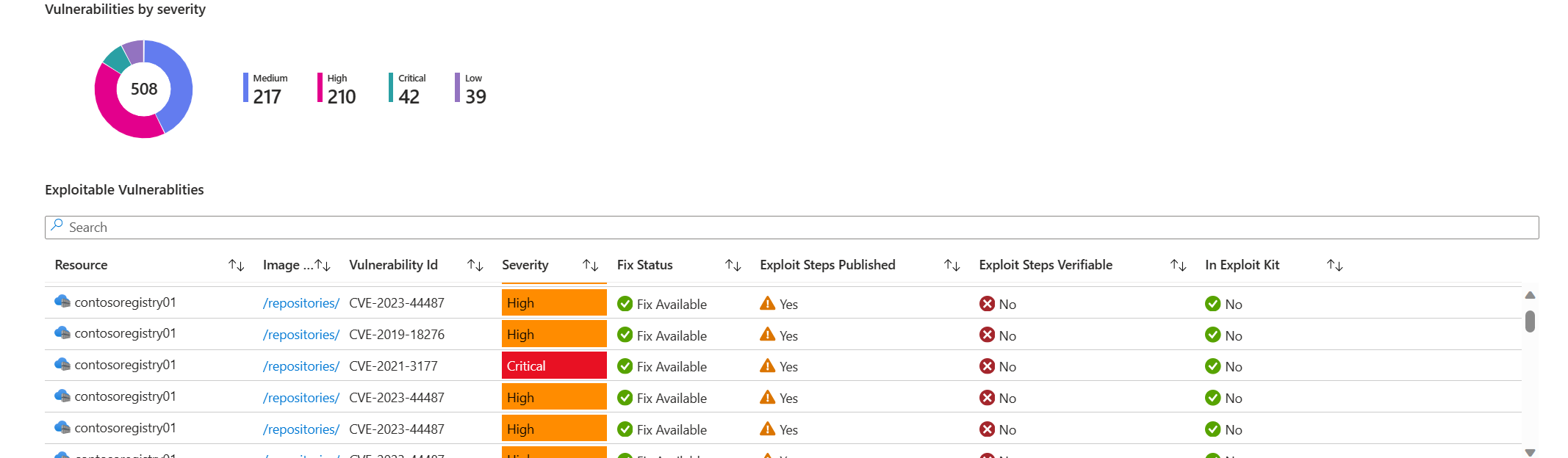
Overview of all vulnerabilities: View all vulnerabilities detected across your Azure Container Registries and running on the AKS cluster.
Exploitable vulnerabilities dashboard: A dedicated section highlighting vulnerabilities with known exploits, enabling security teams to focus on vulnerabilities that pose a high risk of exploitation. This is only available with container vulnerability assessment scanning powered by Microsoft Defender Vulnerability Management.
Additional ARG queries: You can use this workbook to view more examples of how to query ARG data between Qualys and Microsoft Defender Vulnerability Management. For more information on how to edit workbooks, see Workbooks gallery in Microsoft Defender for Cloud.