Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article shows you how to enable Microsoft Defender for Containers on your Azure Kubernetes Service (AKS) clusters through the Azure portal. You can choose to enable all security features at once for comprehensive protection, or selectively deploy specific components based on your requirements.
When to use this guide
Use this guide if you want to:
- Set up Defender for Containers on Azure for the first time
- Enable all security features for comprehensive protection
- Selectively deploy specific components
- Fix or add missing components to an existing deployment
- Exclude certain clusters from protection
Prerequisites
Network requirements
The Defender sensor must connect to Microsoft Defender for Cloud to send security data and events. Make sure that the required endpoints are configured for outbound access.
Connection requirements
The Defender sensor needs connectivity to:
- Microsoft Defender for Cloud (for sending security data and events)
By default, AKS clusters have unrestricted outbound (egress) internet access.
For clusters with restricted egress, you must allow specific FQDNs for Microsoft Defender for Containers to function properly. See Microsoft Defender for Containers - Required FQDN/application rules in the AKS outbound network documentation for the required endpoints.
Private link configuration
If event egress from the cluster requires the use of an Azure Monitor Private Link Scope (AMPLS), you must:
Define the cluster with Container insights and a Log Analytics workspace
Define the cluster's Log Analytics workspace as a resource in the AMPLS
Create a virtual network private endpoint in the AMPLS between:
- The virtual network of the cluster
- The Log Analytics resource
The virtual network private endpoint integrates with a private DNS zone.
For instructions, see Create an Azure Monitor Private Link Scope.
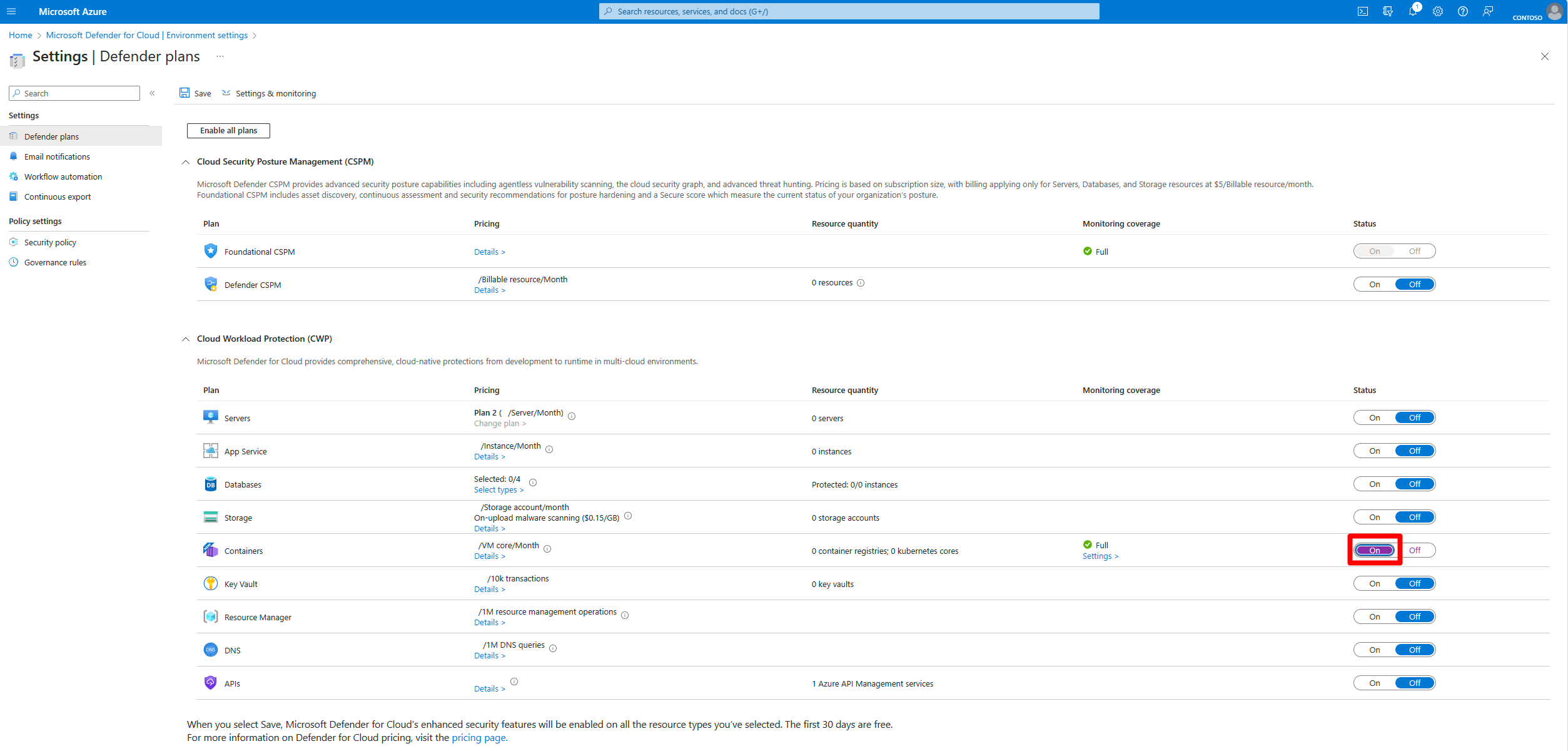
Enable Defender for Containers plan
First, enable the Defender for Containers plan on your subscription:
Sign in to the Azure portal.
Go to Microsoft Defender for Cloud.
In the left menu, select Environment settings.
Select the subscription where your AKS clusters are located.
On the Defender plans page, find the Containers row and toggle the status to On.
Configure plan components
After you enable the plan, review and configure the components. By default, all components are enabled when you turn on the Defender for Containers plan.
Select Settings in the Containers plan row.
In Settings, you see all available components.
Review the components that are enabled by default:
- Agentless scanning for machines - Scans your machines for installed software, vulnerabilities, and secret scanning without relying on agents or impacting machine performance
- Defender sensor - Deployed on each worker node, collects security related data, required for runtime threat protection
- Azure Policy - Deployed as an agent on your Kubernetes cluster. Provides Kubernetes data plane hardening
- Kubernetes API access - Required for agentless container posture, runtime vulnerability assessment and response actions
- Registry access - Enables agentless vulnerability assessment for registry images
You can:
- Keep all components enabled (recommended for comprehensive protection)
- Disable specific components you don't need
- Re-enable components if you previously disabled them
Select Continue.
Review the monitoring coverage page to see what resources are protected.
Select Continue.
Review the configuration summary and select Save.
Roles and permissions
Learn more about the roles for provisioning Defender for Containers extensions.
Monitor deployment progress
After you save your changes, Defender for Cloud automatically starts deploying the selected components to your AKS clusters:
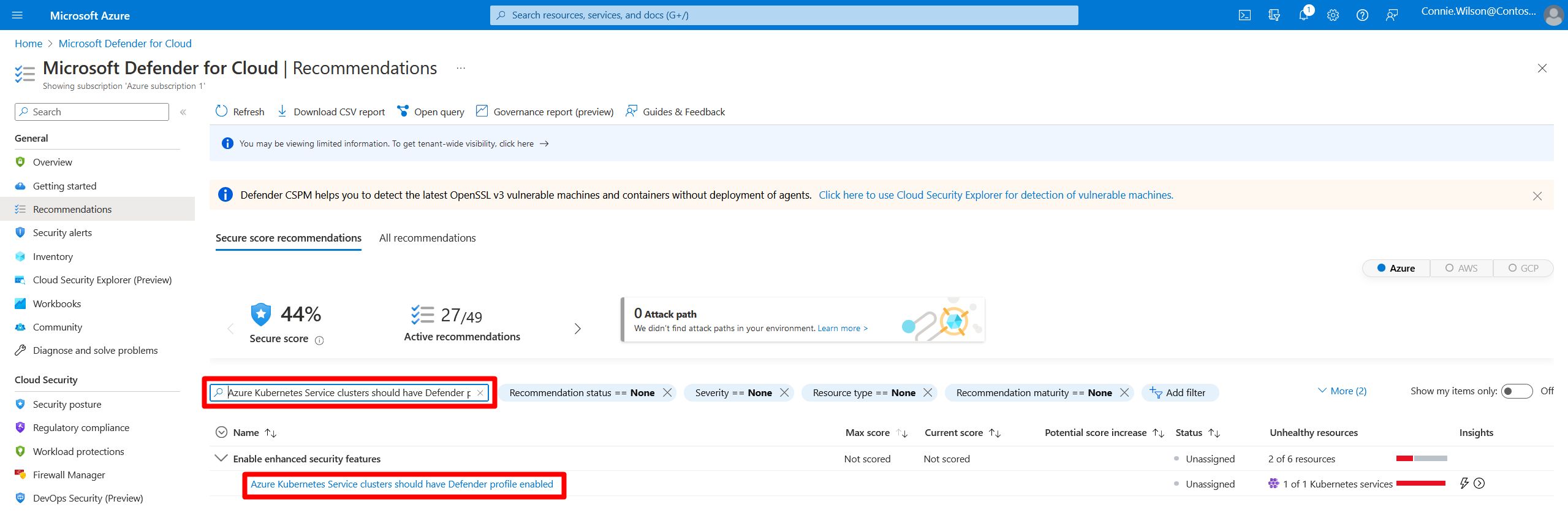
Go to Microsoft Defender for Cloud > Recommendations.
Filter recommendations by Resource type = Kubernetes services.
Look for these key recommendations:
- "Azure Kubernetes Service clusters should have Defender profile enabled"
- "Azure Policy for Kubernetes should be installed and enabled on your clusters"
Select each recommendation to see the affected resources and remediation progress.
Deploy the Defender sensor
Important
Deploying the Defender sensor using Helm: Unlike other options that are autoprovisioned and updated automatically, Helm lets you flexibly deploy the Defender sensor. This approach is especially useful in DevOps and infrastructure-as-code scenarios. With Helm, you can integrate deployment into CI/CD pipelines and control all sensor updates. You can also choose to receive preview and GA versions. For instructions on installing the Defender sensor using Helm, see Install Defender for Containers sensor using Helm.
When you enable the Defender sensor setting, it automatically deploys to all AKS clusters in your subscription. If you disable automatic deployment, you can manually deploy the sensor by using the following methods:
Deploy to a group of selected AKS clusters
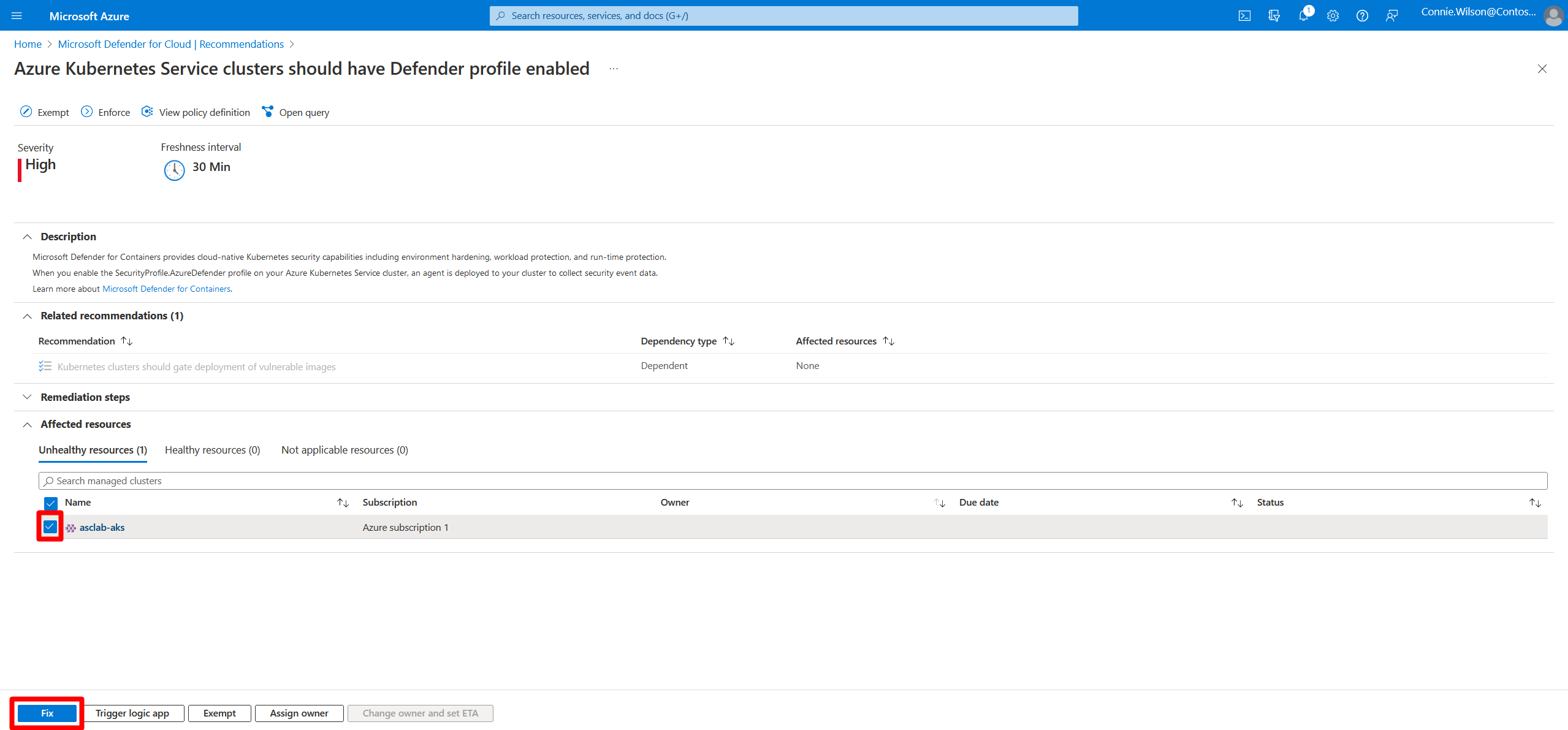
Go to Microsoft Defender for Cloud > Recommendations.
Search for and select "Azure Kubernetes Service clusters should have Defender profile enabled".
Select the AKS clusters that need the sensor.
Select Fix.
Review the deployment configuration.
Select Fix X resources to deploy.
Note
You can also deploy the Defender sensor by using Helm for more control over the deployment configuration. For Helm deployment instructions, see Deploy the Defender sensor using Helm.
Deploy to a specific AKS cluster
To deploy the Defender sensor to specific AKS clusters:
Go to your AKS cluster in the Azure portal.
In the left menu under the cluster name, select Microsoft Defender for Cloud.
On the Microsoft Defender for Cloud page for your cluster, select Settings in the top row, locate the Defender sensor row, and toggle it to On.
Select Save.
Exclude specific clusters (optional)
You can exclude specific AKS clusters from automatic provisioning by applying tags:
Go to your AKS cluster.
Under Overview, select Tags.
Add one of these tags:
- For Defender sensor:
ms_defender_container_exclude_sensors=true - For Azure Policy:
ms_defender_container_exclude_azurepolicy=true
- For Defender sensor:
Monitor ongoing security
After setup, regularly:
- Manage vulnerabilities - Review findings of container image vulnerability scans
- Review recommendations - Address security issues identified for your AKS clusters
- Investigate alerts - Respond to runtime threats detected by the Defender sensor
- Track compliance - Monitor adherence to security standards and benchmarks
Clean up resources
To disable Defender for Containers and remove all deployed components from your AKS clusters, see Remove Defender for Containers from Azure (AKS).