Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Note
This page describes the new risk-based approach to vulnerability management in Defender for Cloud. Defender for CSPM customers should use this method. To use the classic secure score approach, see View and remediate vulnerabilities for registry images (Secure Score).
Defender for Cloud offers customers the capability to remediate vulnerabilities in container images while they're still stored in the registry. Additionally, it conducts contextual analysis of the vulnerabilities in your environment, aiding in prioritizing remediation efforts based on the risk level associated with each vulnerability.
In this article, we review the Container images in Azure registry should have vulnerability findings resolved recommendation. For the other supported environments, see the parallel recommendations in Vulnerability assessments for supported environments.
View vulnerabilities on a specific container image
In Defender for Cloud, open the Recommendations page. If you're not on the new risk-based page, select Recommendations by risk on the top menu. If issues were found, you'll see the recommendation Container images in Azure registry should have vulnerability findings resolved. Select the recommendation.
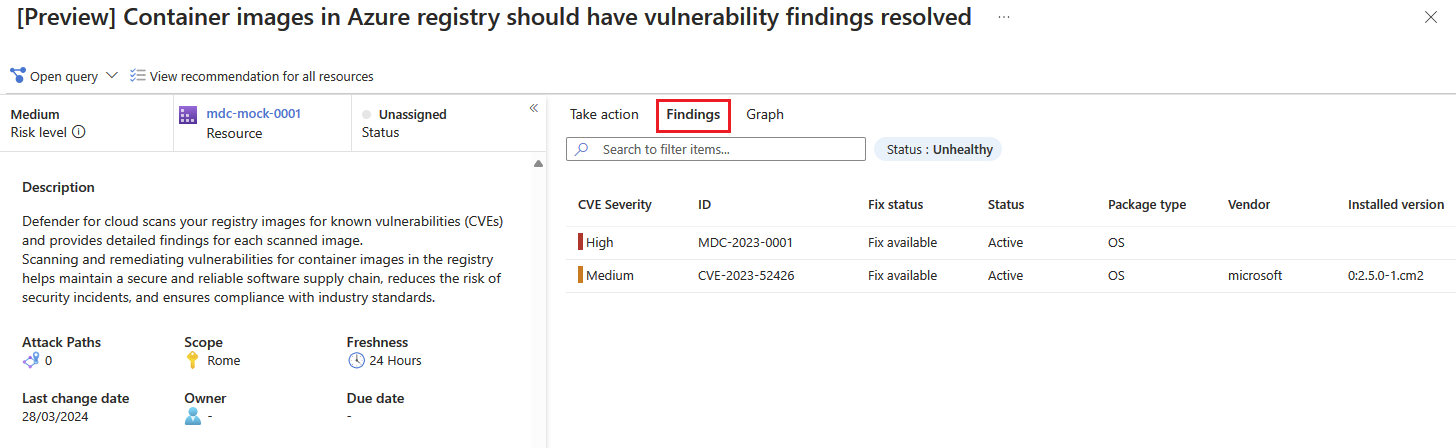
The recommendation details page opens with additional information. This information includes details about your registry image and the remediation steps.
Select the Findings tab to see the list of vulnerabilities impacting the registry image.
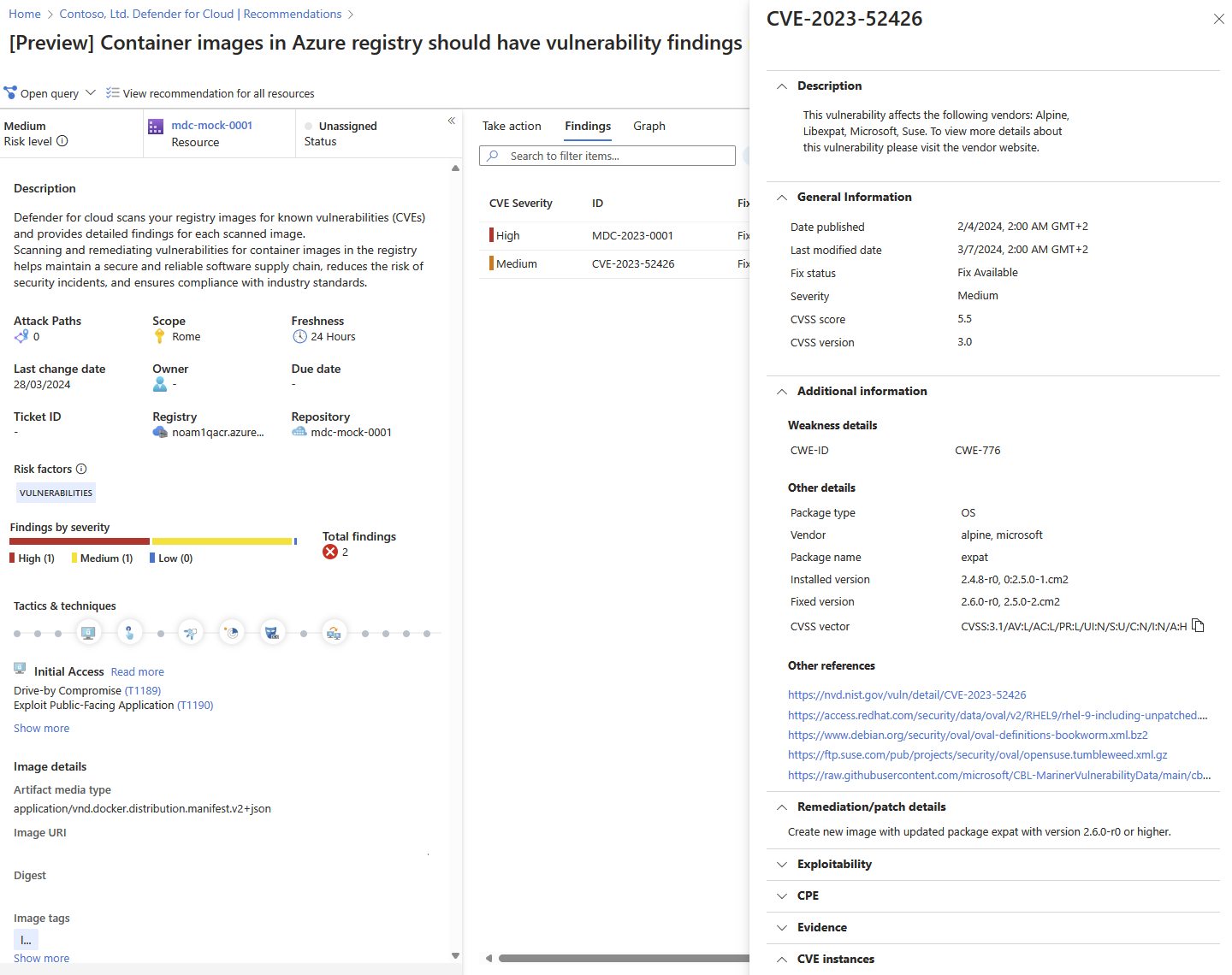
Select each vulnerability for a detailed description of the vulnerability, additional images affected by that vulnerability, information on the software version that contributes to resolving the vulnerability, and links to external resources to help with patching the vulnerability.
To find all images impacted by a specific vulnerability, group recommendations by title. For more information, see Group recommendations by title.
For information on how to remediate the vulnerabilities, see Remediate recommendations.