Restrict access to Azure DevOps Services IPs only
We highly recommend that you restrict access to your Azure Storage account to only IPs from Azure DevOps Services. You can restrict access by only allowing connections from Azure DevOps Services IPs that are involved in the collection database import process. The IPs that need to be granted access to your storage account depend on the region you're importing into.
Option 1: Using Service Tags
You can easily allow connections from all Azure DevOps Services regions by adding the azuredevops Service Tag to your network security groups or firewalls either through the portal or programmatically.
Option 2: Using IpList
Use the IpList command to get the list of IPs that need to be granted access to allow connections from a specific Azure DevOps Services region.
Included in the help documentation are instructions and examples for running Migrator from the Azure DevOps Server instance itself and a remote machine. If you're running the command from one of the Azure DevOps Server instance's application tiers, your command should have the following structure:
Migrator IpList /collection:{CollectionURI} /tenantDomainName:{name} /region:{region}
You can add the list of IPs to your network security groups or firewalls either through the portal or programatically.
Configure IP firewall exceptions for SQL Azure
Note
This section only applies to configuring firewall exceptions for SQL Azure. For DACPAC imports, see Configure Azure Storage firewalls and virtual networks
Note
The data migration tool requires the Azure DevOps Services IPs to be configured for inbound connections only on port 1433.
Granting exceptions for the necessary IPs is handled at the Azure networking layer for your SQL Azure VM. To get started, go to your SQL Azure VM in the Azure portal. In Settings, select Networking. You can grant exceptions for the IPs by selecting Add inbound port rule in the networking settings.
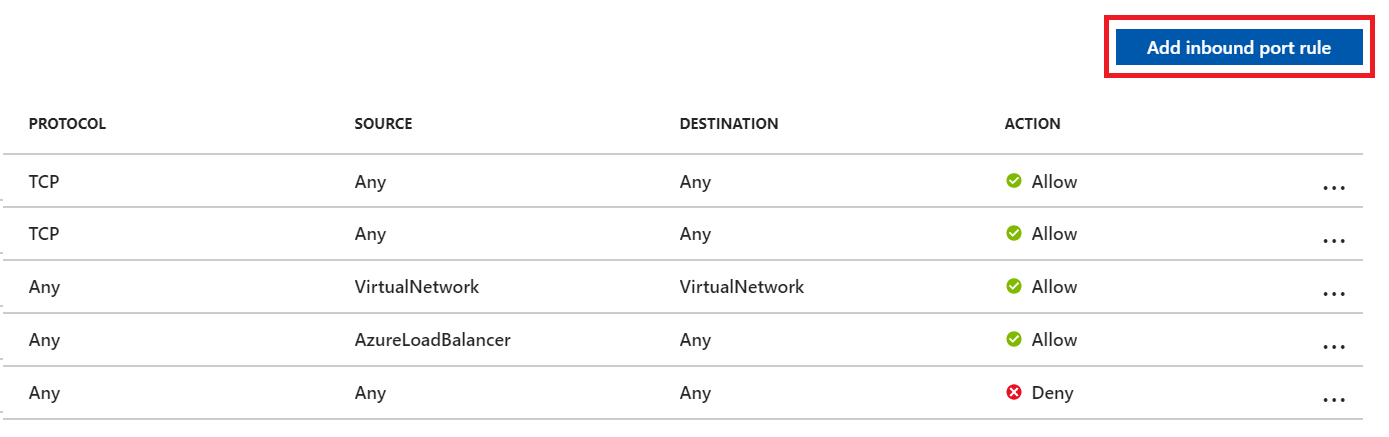
On the Add inbound security rule pane, select Advanced to configure an inbound port rule for a specific IP.
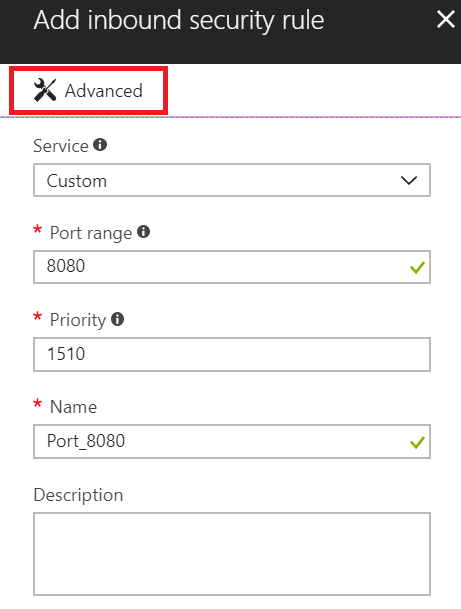
In the Source drop-down list, select IP Addresses, enter an IP address that needs to be granted an exception, set the Destination port range to 1433 and, in the Name box, enter a name that best describes the exception you're configuring.
Depending on other inbound port rules that have been configured, you might need to change the default priority for the Azure DevOps Services exceptions so they don't get ignored. For example, if you have a "deny on all inbound connections to 1433" rule with a higher priority than your Azure DevOps Services exceptions, the data migration tool might be unable to make a successful connection to your database.
Repeat adding inbound port rules until all necessary Azure DevOps Services IPs have been granted an exception. Missing one IP could result in your import failing to start.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for