Manage access with Microsoft Entra groups
Azure DevOps Services
To control access to your team's critical resources and key business assets in Azure DevOps Services, use Microsoft services like Microsoft 365 or Microsoft Entra ID. Microsoft Entra ID works with your organization to control access and authenticate users.
Organize your directory members with Microsoft Entra groups and manage permissions in bulk for your organization. Add these groups to built-in groups like Project Collection Administrators or Contributors, or to custom groups like your project management team. Microsoft Entra group members inherit permissions from the Azure DevOps group, so you don't have to manage group members individually.
For more information on Microsoft Entra ID benefits and how to control organization access with Microsoft accounts or Microsoft Entra ID, see the provided links.
Note
Due to a functional limitation on Microsoft Graph, service principals don't appear in any list of Microsoft Entra group members on Azure DevOps. Permissions set on any Microsoft Entra groups still apply to any service principals in the group that have been added to the organizations, even if they aren't displaying on the web UI.
Prerequisites
| Category | Requirements |
|---|---|
| Permissions | - Member of the Project Collection Administrators group. Organization owners are automatically members of this group. - Microsoft Entra Administrator in the Azure portal. |
| Access levels | At least Basic access. |
Add a Microsoft Entra group to an Azure DevOps group
Note
To enable the preview feature, Organization Permissions Settings Page v2, see Enable preview features.
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Why am I asked to choose between my work or school account and my personal account?
Go to Organization settings.
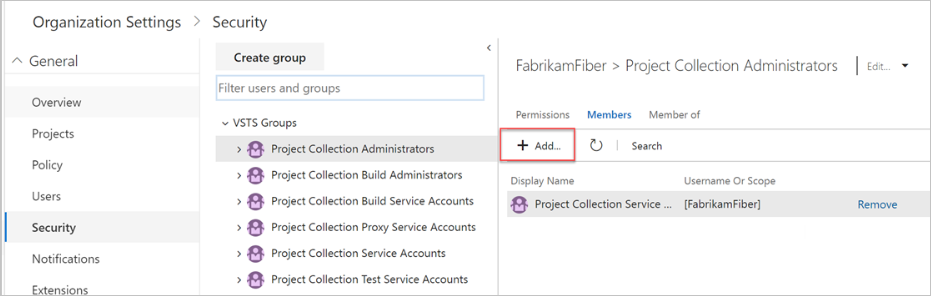
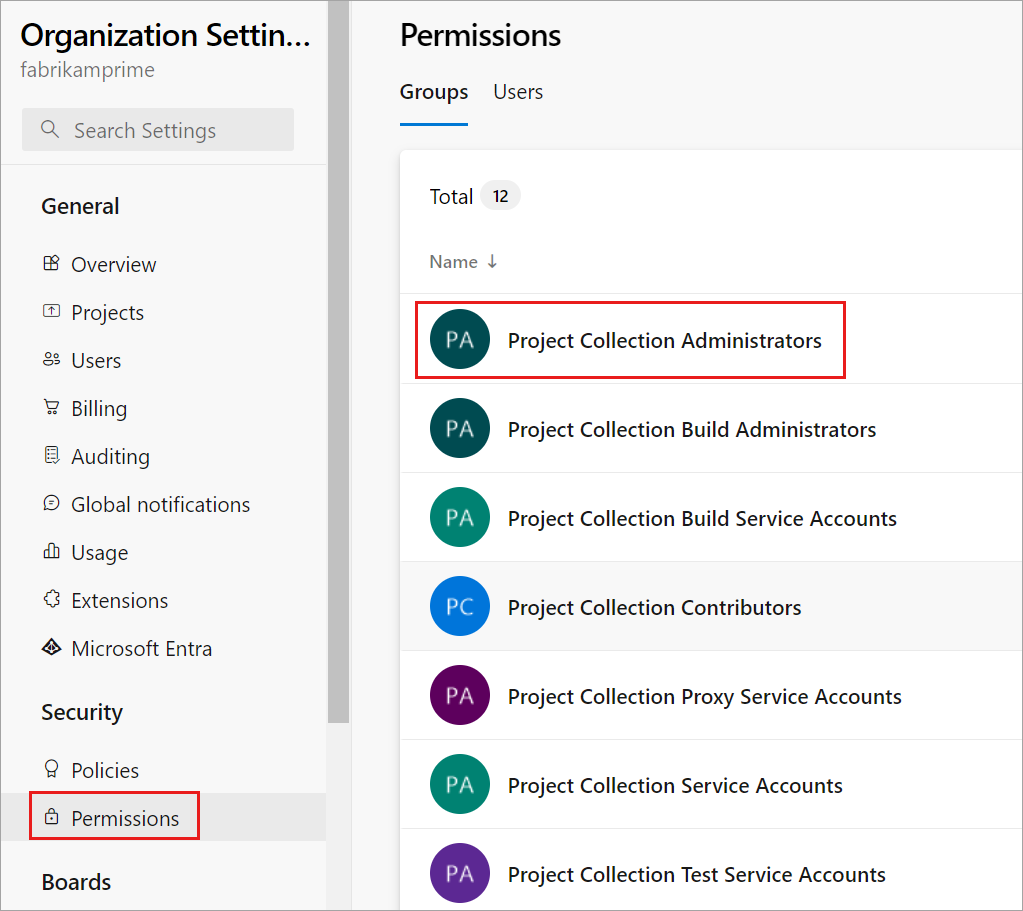
Choose Permissions, and then select the group you want to add a member to.
Select Members, and then select Add.
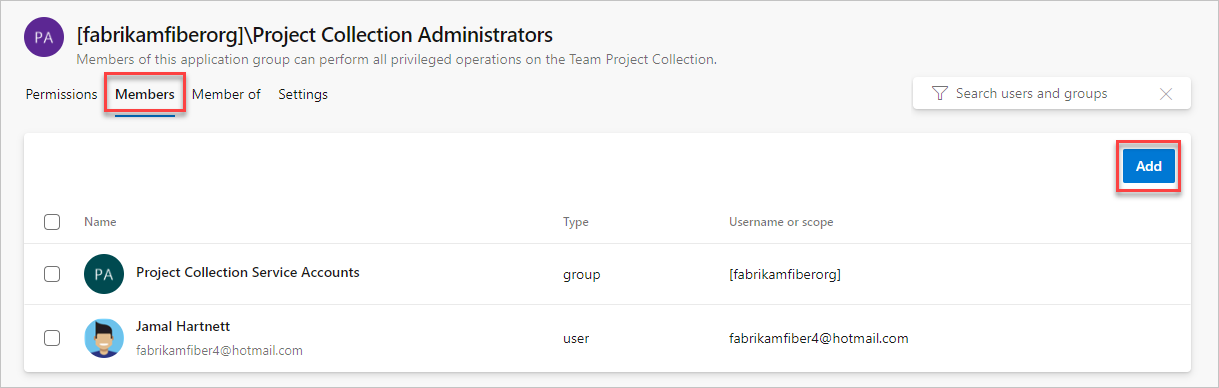
You invite guests into Microsoft Entra ID and into your Microsoft Entra ID-backed organizations, without waiting for them to accept. This invitation allows you to add those guests to your organization, grant access to projects, assign extensions, and more.
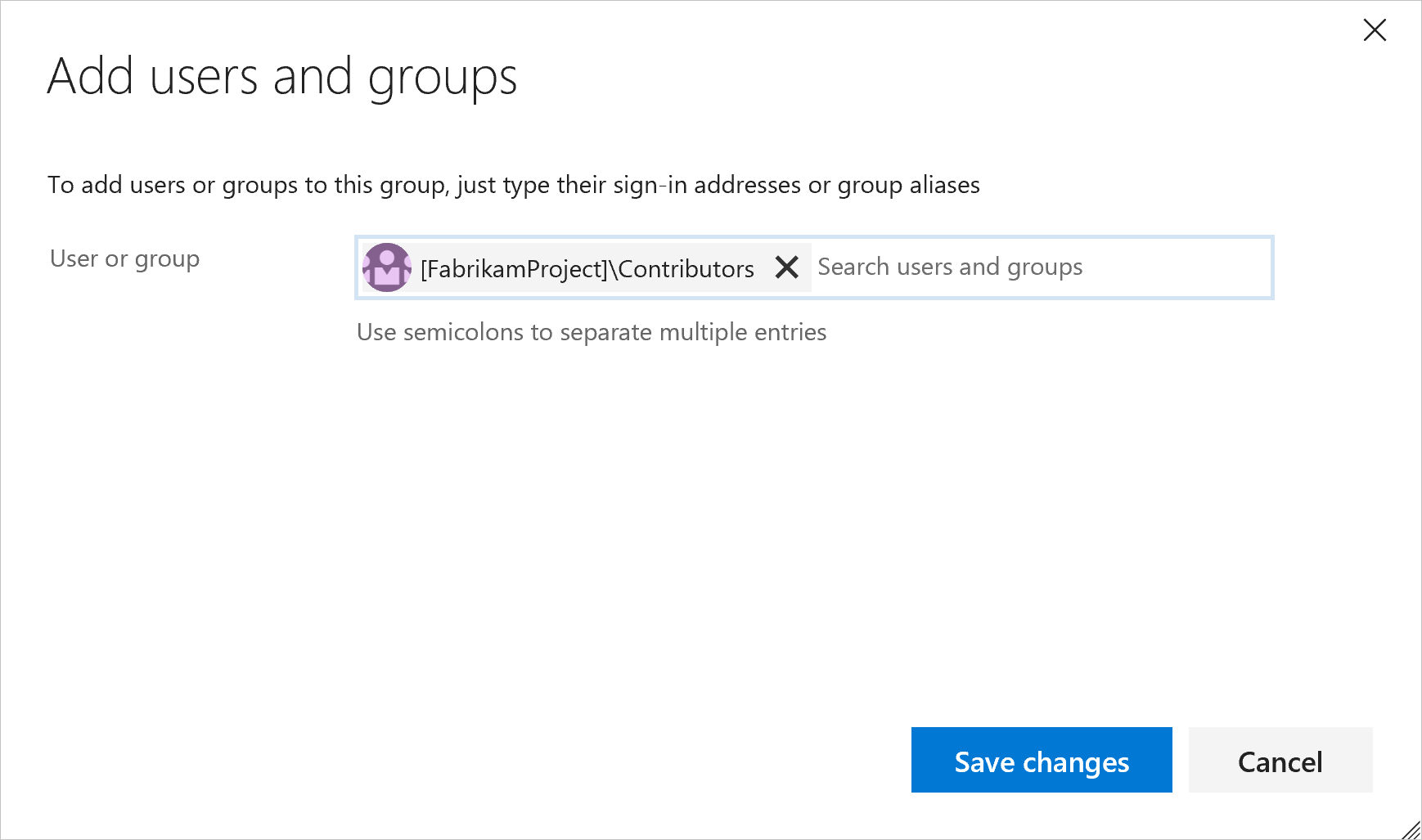
Add users or groups, and then Save your changes.
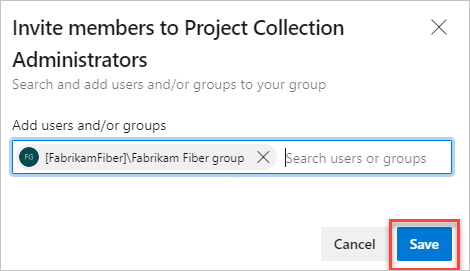
Microsoft Entra ID changes might take up to 1 hour to be visible in Azure DevOps, but you can immediately reevaluate your permissions.