Use policies to manage personal access tokens for users
Azure DevOps Services
This article provides guidance on how to use Microsoft Entra policies to manage personal access tokens (PATs) in Azure DevOps. It explains how to limit the creation, scope, and lifespan of new or renewed PATs, as well as how to handle the automatic revocation of leaked PATs. Each section details the default behavior of the respective policies, helping administrators effectively control and secure PAT usage within their organization.
Important
Existing PATs, created through both the UI and APIs, remain valid for the rest of their lifespan. Update your existing PATs to comply with the new restrictions to ensure successful renewal.
Prerequisites
- Organization Connection: Ensure your organization is linked to Microsoft Entra ID.
- Roles: Be an Azure DevOps Administrator in Microsoft Entra ID. To check your role, sign in to the Azure portal, and go to Microsoft Entra ID > Roles and administrators. If you're not an Azure DevOps administrator, you can't see the policies. Contact your administrator, if necessary.
Restrict creation of global PATs
The Azure DevOps Administrator in Microsoft Entra can restrict users from creating global Personal Access Tokens (PATs), which apply to all accessible organizations rather than a single organization. When this policy is enabled, new PATs must be associated with specific Azure DevOps organizations. By default, this policy is set to off.
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.
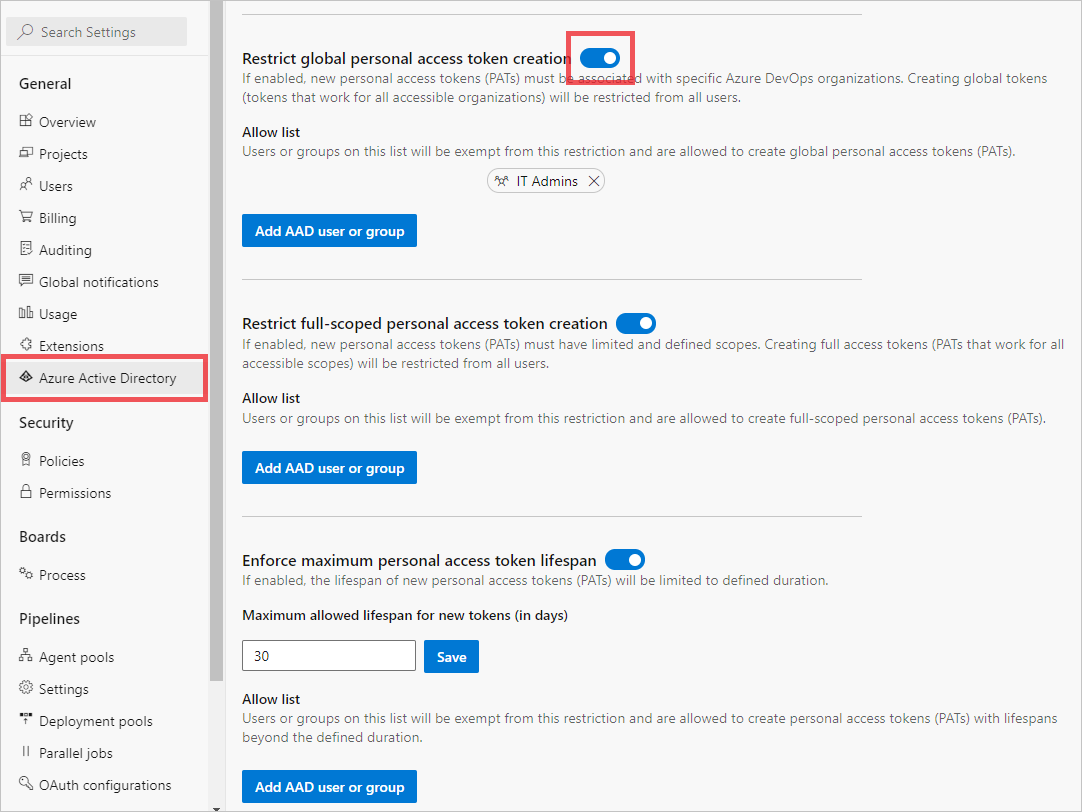
Select Microsoft Entra, find the Restrict global personal access token creation policy and move the toggle on.
Restrict creation of full-scoped PATs
The Azure DevOps Administrator in Microsoft Entra can restrict users from creating full-scoped PATs. Enabling this policy requires new PATs to be limited to a specific, custom-defined set of scopes. By default, this policy is set to off.
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
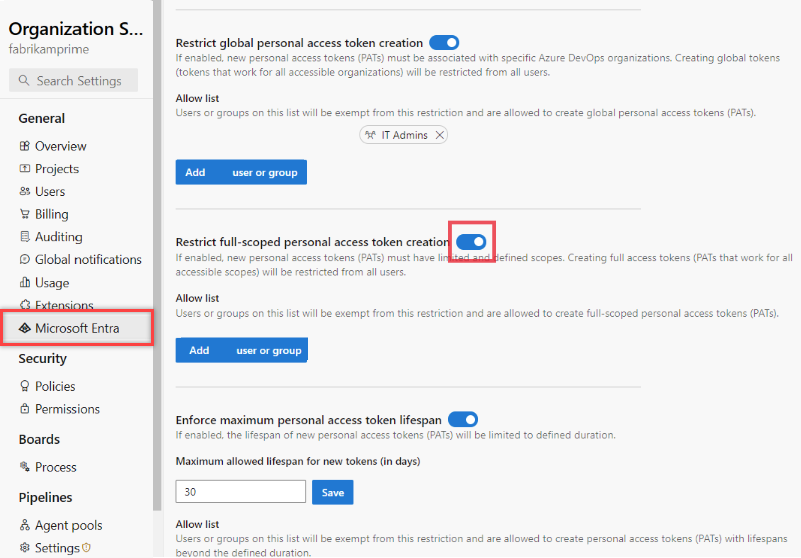
Organization settings.Select Microsoft Entra, find the Restrict full-scoped personal access token creation policy and move the toggle on.
Set maximum lifespan for new PATs
The Azure DevOps Administrator in Microsoft Entra ID can define the maximum lifespan of a PAT, specifying it in days. By default, this policy is set to off.
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.Select Microsoft Entra, find the Enforce maximum personal access token lifespan policy and move the toggle on.
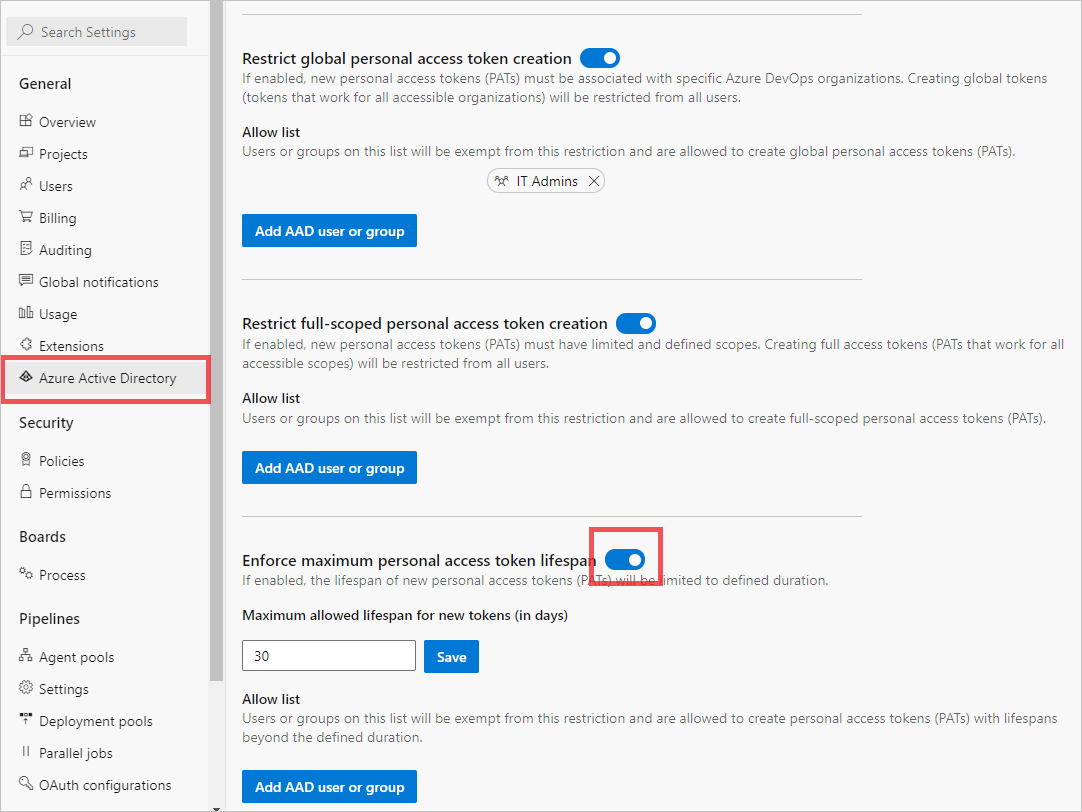
Enter the number of maximum days, and then select Save.
Add Microsoft Entra users or groups to the allowlist
Warning
We recommend using groups for your tenant policy allow lists. If you use a named user, a reference to their identity resides in the United States, Europe (EU), and Southeast Asia (Singapore).
Users or groups on the allowlist are exempt from the restrictions and enforcements of these policies when enabled. To add a user or group, select Add Microsoft Entra user or group, then select Add. Each policy has its own allowlist. If a user is on the allowlist for one policy, other activated policies still apply. Therefore, to exempt a user from all policies, add them to each allowlist.
Revoke leaked PATs automatically
The Azure DevOps Administrator in Microsoft Entra ID can manage the policy that automatically revokes leaked PATs. This policy applies to all PATs within organizations linked to your Microsoft Entra tenant. By default, this policy is set to on. If Azure DevOps PATs are checked into public GitHub repositories, they're automatically revoked.
Warning
Disabling this policy means any PATs checked into public GitHub repositories will remain active, potentially compromising your Azure DevOps organization and data, and putting your applications and services at significant risk. Even with the policy disabled, you will still receive an email notification if a PAT is leaked, but it will not be revoked automatically.
Turn off automatic revocation of leaked PATs
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.Select Microsoft Entra, find the Automatically revoke leaked personal access tokens policy and move the toggle to off.
The policy is disabled and any PATs checked into public GitHub repositories remain active.