Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
We’re excited to announce new enhancements in Azure DevOps that improve security and simplify workflows. The Generate Git Credentials button has been removed from the Clone Repository dialogs in Repos and Wiki, aligning with our move to Microsoft Entra tokens for authentication—helping teams adopt a more secure and efficient Git workflow.
Additionally, we are pleased to announce that in Azure Pipelines, managed DevOps pools is now generally available. This feature enhances scalability, reliability, and streamlined management for Azure DevOps Virtual Machine Scale Set agent pools.
Check out the release notes for details.
General
- Removal of Generate Git Credentials Button in Repos and Wiki
- Update to Azure DevOps Allowed IP addresses
GitHub Advanced Security for Azure DevOps
- GitHub Advanced Security updates for default branch changes
- CodeQL installation for self-hosted agents supports proxy configurations
- Alerts branch picker now displays all branches with a successful scan
- Enhanced pull request annotations in GitHub Advanced Security
- Improvements for Get alerts API
Azure Pipelines
- Azure Classic Service Connections are being retired
- Managed DevOps Pools is generally available
- New tasks to implement secret-less access to Azure storage accounts
Test Plans
- Direct link from Test Plan work item to Test Plans page
- Azure Test Plans bug fixes
- Export test cases with custom columns in XLSX
- Auto-pause manual test case run
General
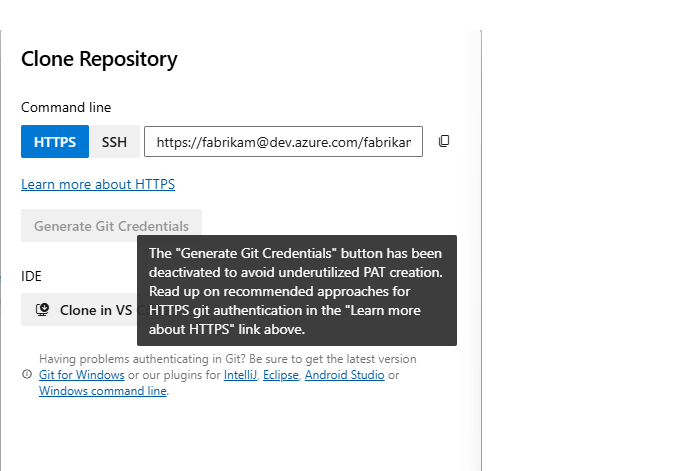
Removal of Generate Git Credentials button in Repos and Wiki
The Generate Git Credentials button has been removed from the Clone Repository dialogs in the Repos and Wiki UI to support the transition to Microsoft Entra tokens for authentication in Git operations. Previously, selecting this button generated a new Personal Access Token (PAT) with the vso.code scope, active for seven days. Each use created a new PAT, often resulting in unnecessary credentials.
To enhance security and streamline authentication, consider using Entra tokens for ad-hoc Git clone operations in Repos and Wiki. Documentation is available to help you configure authentication via the command line or within the Git Credential Manager (GCM).
While PATs remain available for Git operations, they must now be manually created with the appropriate vso.code scope from the Personal Access Token page. Ensure that PATs are only active as long as needed and revoked when no longer in use. As a best practice, store PATs securely in a secret management service such as Azure Key Vault (AKV) and rotate them regularly.
Update to Azure DevOps Allowed IP addresses
We’re thrilled to announce ongoing improvements to our networking infrastructure to enhance performance and reliability. As part of this effort, new IP addresses are being introduced. To ensure uninterrupted access, please add the new IP addresses to your firewall allow list as soon as possible.
IP V4 Ranges:
- 150.171.22.0/24
- 150.171.23.0/24
- 150.171.73.0/24
- 150.171.74.0/24
- 150.171.75.0/24
- 150.171.76.0/24
IP V6 Ranges:
- 2620:1ec:50::/48
- 2620:1ec:51::/48
- 2603:1061:10::/48
For more details, visit our blog: Update to Azure DevOps Allowed IP addresses.
GitHub Advanced Security for Azure DevOps
GitHub Advanced Security updates for default branch changes
Within GitHub Advanced Security, navigating to the advanced security tab shows the alert state for your default branch first, while the Security Overview view pulls alert information for your default branch only.
Now, Advanced Security detects changes to your default branch and updates both the Security Overview and repository-level alert view shortly after the default branch assignment is changed.
CodeQL installation for self-hosted agents supports proxy configurations
If you have a network proxy configured and used the enableAutomaticCodeQLInstall variable in the AdvancedSecurity-CodeQL-Init task, the task may have previously encountered the error message [warning] Maximum number of redirects exceeded when downloading the CodeQL tool cache to your self-hosted agent. With this update, we introduce handling for network proxies so that automatic installation runs successfully.
Alerts branch picker now displays all branches with a successful scan
The branch picker in GitHub Advanced Security has been updated to display all branches with a successful scan, even if no vulnerabilities are detected. Previously, only branches with alerts were shown, making it difficult to confirm whether a scan completed successfully.
Both the repository-level alerts UX and the Analysis - List API now return branches with a successful SARIF submission for dependency and code scanning, improving scan visibility.
Enhanced pull request annotations in GitHub Advanced Security
With this release, we've improved the pull request annotation experience in GitHub Advanced Security through:
Increased dependency scanning annotations: Advanced Security displays pull request annotations even when Advanced Security can't determine physical file location.
Auto-closure: pull request comments will be automatically resolved if the associated alert is dismissed. We've also introduced performance improvements and batch handling for pull request events for a smoother experience.
Improvements for Get Alerts API
With this update we introduce new improvements for the Advanced Security Get alerts API:
- Minimal API expand option: fetch a minimal version of the Alerts API using the parameter
expand=minimalin your payload. E.g.:https://advsec.dev.azure.com/{organization}/{project}/_apis/Alert/repositories/{repository}/Alerts?expand=minimal.
New metadata for alerts: the Alerts API now returns specific
AdditionalPropertiessuch as CVE ID or advisory ID for dependency alerts and tags for code scanning alerts.Batched Alert API calls: use
criteria.alertIds={alertId1},{alertId2}with the Alerts API to receive details for a comma separated list of alert IDs. E.g.:https://advsec.dev.azure.com/{organization}/{project}/_apis/Alert/repositories/{repository}/Alerts?criteria.alertIds=100,200,130.
Azure Pipelines
Azure Classic Service Connections are being retired
Cloud Services, also known as Azure Service Manager (ASM), was the original deployment model for Azure. Since its replacement by Azure Resource Manager (ARM) in 2014, it has now been retired. Consequently, we are discontinuing the ability to create new Azure Classic service connections. However, existing Azure Classic service connections will remain unaffected.
Managed DevOps Pools is generally available
Managed DevOps Pools is an evolution of Azure DevOps Virtual Machine Scale Set agent pools. It provides better pool scalability and reliability, simplifies pool management, and allows you to use the VM images from Microsoft-hosted agents on custom Azure VMs.
Managed DevOps Pools is now generally available. You can read about Managed DevOps Pools features and the features newly added for GA here and here.
New tasks to implement secret-less access to Azure storage accounts
The AzureVmssDeployment, JavaToolInstaller, JenkinsDownloadArtifacts tasks can be configured to use Azure Storage:
- task: AzureVmssDeployment@1
inputs:
(required properties)
azureSubscription: <service connection>
customScriptsStorageAccount: <storage account>
- task: JavaToolInstaller@2
inputs:
(required properties)
jdkSourceOption: 'AzureStorage'
azureResourceManagerEndpoint: <service connection>
azureStorageAccountName: <storage account>
- task: JenkinsDownloadArtifacts@2
inputs:
(required properties)
artifactProvider: 'azureStorage'
ConnectedServiceNameARM: <service connection>
storageAccountName: <storage account>
New task versions have been created that now use Azure RBAC instead of storage account key/sas. The new tasks require the Storage Blob Data Contributor role to be assigned to the identity of the service connection configured.
You will need to assign the appropriate Azure RBAC role for service connection used in the task to be able to access the Azure Storage Account. See Assign an Azure role for access to blob data.
The AzureVmssDeployment@1 task needs additional RBAC roles configured to access the storage account configured in customScriptsStorageAccount:
- The
azureSubscriptionService Connection: Contributor or Virtual Machine Contributor role on the Virtual Machine Scale Set - The
azureSubscriptionService Connection: Storage Blob Data Contributor role on the storage account that holds the custom script - The Virtual Machine Scale Set System-assigned Managed Identity: Storage Blob Data Reader role on the storage account that holds the custom script
Test Plans
Direct Link from Test plan work item to Test plans page
You can now easily access the Test plans page directly from the Test plans work item. We're adding a clear, direct entry point to help you quickly navigate to the corresponding test plan without extra steps. This improvement makes it faster and more intuitive to trace your test plans, ensuring a smoother experience when managing your test workflow.

Give it a try and let us know via email what you think!
Azure Test Plans bug fixes
With this sprint, we made updates to Azure Test Plans to resolve several bugs and improve usability. Here's what's been fixed:
Fixed an issue where Test Suites didn't update correctly when switching between Test Plans. For details on the initial bug, see this DevComm post.
Fixed an issue in the Test & Feedback Extension where session reports failed to download and redirected users to a blank page.
Fixed an issue in the new Boards hub where Shared Steps opened in the old work item form and users couldn't delete comments in the discussion section. this DevComm post.
Fixed an issue where filtering test results by the Owner clause didn't work, causing queries to return an error instead of results. this DevComm post.
Export test cases with custom columns in XLSX
You can now export custom columns in XLSX. We've heard your feedback requesting Test Plans supports exporting test cases with custom columns. This feature gives you greater flexibility and control over the data you share and analyze. In addition, it helps you tailor exports to your needs, ensuring the information you export is relevant and actionable.
Auto-pause manual test case run
Never lose progress on your test runs with auto-pause test case run. This new feature automatically pauses your test case run if your work is interrupted, ensuring that partial progress is saved without needing a manual pause. Whether you step away or close the session, you can easily resume your test case right where you left off, reducing the risk of data loss and improving your workflow. By simplifying the pause and resume process, auto-pause helps you stay focused on testing without worrying about losing your progress.
Give it a try, and let us know via email what you think!
Next steps
Note
These features will roll out over the next two to three weeks.
Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.
Thanks,
Silviu Andrica