Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure DevOps Services | Azure DevOps Server 2022 | Azure DevOps Server 2020
When you integrate a service with Azure DevOps, you can grant the service access to your Azure DevOps resources, such as work items, source code, and build results.
Azure DevOps uses OpenID Connect (OIDC)-based authentication to grant the service access to your resources.
- Authorizations are bound to your credentials, so the service can use an authorization to access your resources in Azure DevOps.
- You use your Microsoft account or your work account to authorize the service.
- The service that you authorize doesn't have access to your Azure DevOps credentials.
Prerequisites
| Category | Requirement |
|---|---|
| Project access | Project member. |
| Access levels | At least Basic access. |
| Permissions | Member of the Project Collection Administrators group. Organization owners are automatically members of this group. |
Authentication frameworks
When you build an application on top of Azure DevOps REST APIs, you can use OIDC-based authentication by registering your application in Microsoft Entra ID. For more information, see What is the Microsoft identity platform?.
Some older apps use an implementation of OAuth 2.0 to get access tokens for Azure DevOps resources. Registrations of these Azure DevOps OAuth applications are no longer supported, because Azure DevOps OAuth is slated for deprecation in 2026. For more information, see No new Azure DevOps OAuth apps beginning April 2025.
Authorize a service
A typical authorization flow might include the following steps:
You use a service that uses Azure DevOps resources, so the service requests authorization.
To initiate the authentication process for the service, the registered app opens a Microsoft Entra ID website that prompts you to select an account.
After you select an account, the authorization approval page appears.

You review the request and approve the authorization.
The authorized service uses that authorization to access resources in your Azure DevOps organization.
To ensure an authorization request is legitimate, take the following precautions:
- Pay attention to any HTTPS-related security warnings in your browser.
- Don't give your credentials to other services directly. Enter your credentials only through the authorization approval page in Azure DevOps.
Manage authorizations
When you register an app in Microsoft Entra ID, the app can request tokens from the Microsoft identity platform. An authenticated service can then use a token to access specific protected resources. The lifetime of each token is at most 90 minutes. After a token expires, the service's access to the resources is revoked. For more information, see Token lifetime.
In contrast, apps that are registered with Azure DevOps OAuth can authorize services to access Azure DevOps resources for longer periods of time. For a list of services that are currently authorized to access your account, go to https://app.vssps.visualstudio.com/Profile/View and select Manage authorizations.
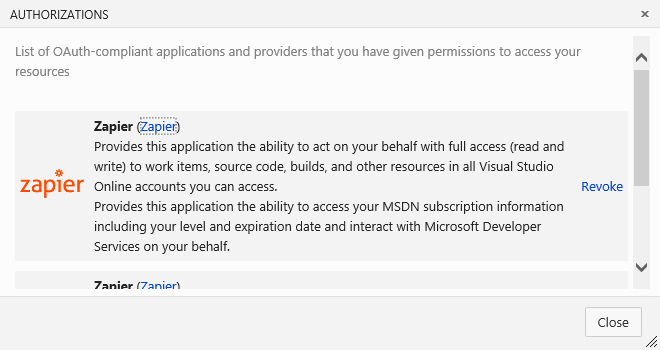
You can use this page to revoke authorizations so that services can't access your account on your behalf.