Note
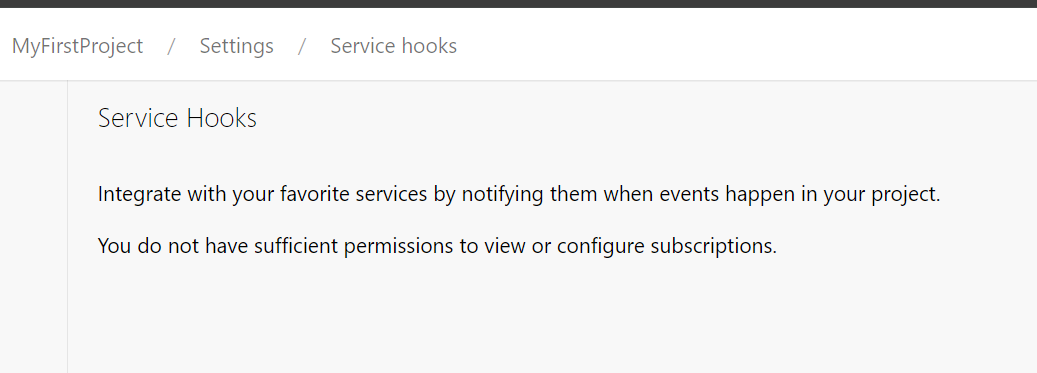
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
This article explains how to grant View or Edit permissions for Service Hooks in Azure DevOps. By default, only Project Administrators have these permissions. To assign them to other users or groups, use the command line tool or the Security REST API.
The ServiceHooks security namespace ID is defined under List Security Namespaces.
Prerequisites
| Category | Requirements |
|---|---|
| Project access | Project member. |
| Permissions | - Member of the Project Collection Administrators group. Organization owners are automatically members of this group. - Microsoft Entra token or Personal access token (PAT) for your Azure DevOps profile. > [!IMPORTANT] > We recommend the more secure Microsoft Entra tokens over higher-risk personal access tokens. Learn more about our efforts to reduce PAT usage. > Review our authentication guidance to choose the right authentication mechanism for your needs. |
| Tools | Azure CLI. 1. Sign in with az devops login.2. You can define your organization as default organization. Otherwise, define --org "https://dev.azure.com/{organization}" for each command. az devops configure --defaults organization="https://dev.azure.com/{organization}"3. Check if you can see list of permissions for your organization: az devops security permission namespace list --org "https://dev.azure.com/{organization}". |
Read group identity and permission token
Find your group identity descriptor.
> az devops security group list --project 00000000-0000-0000-0000-000000000000 --output table Name Descriptor ----------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------------------------- [TEAM FOUNDATION]\EntraServiceHooksRead Aa1Bb~2Cc3.-Dd4Ee5Ff6Gg7Hh8Ii9_Jj0Kk1Ll2If you want to filter by group name, you can use
findstrorgrepcommand depends on your command prompt.Get permission token.
> az devops security permission list --id 00000000-0000-0000-0000-000000000000 --subject <Group or user descriptor> --output table Token Effective Allow Effective Deny ------------------------------------------------------ ----------------- ---------------- PublisherSecurity 0 0 PublisherSecurity/00000000-0000-0000-0000-000000000000 0 0
Update read permission for service hooks
List of possible permissions that you can define for
--allow-bit.- View Subscriptions
- Edit Subscription
- Delete Subscriptions
- Publish Events
> az devops security permission namespace show --id 00000000-0000-0000-0000-000000000000 { "actions": [ { "bit": 1, "displayName": "View Subscriptions", "name": "ViewSubscriptions", "namespaceId": "00000000-0000-0000-0000-000000000000" }, { "bit": 2, "displayName": "Edit Subscription", "name": "EditSubscriptions", "namespaceId": "00000000-0000-0000-0000-000000000000" }, { "bit": 4, "displayName": "Delete Subscriptions", "name": "DeleteSubscriptions", "namespaceId": "00000000-0000-0000-0000-000000000000" }, { "bit": 8, "displayName": "Publish Events", "name": "PublishEvents", "namespaceId": "00000000-0000-0000-0000-000000000000" } ], "dataspaceCategory": "Default", "displayName": "ServiceHooks", "elementLength": -1, "extensionType": null, "isRemotable": true, "name": "ServiceHooks", "namespaceId": "00000000-0000-0000-0000-000000000000", "readPermission": 1, "separatorValue": "/", "structureValue": 1, "systemBitMask": 0, "useTokenTranslator": true, "writePermission": 7 }Set View access for the group. View ServiceHooks Subscriptions equals 1 for
--allow-bit.> az devops security permission update --namespace-id 00000000-0000-0000-0000-000000000000 --subject <Group or user descriptor> --token PublisherSecurity/00000000-0000-0000-0000-000000000000 --allow-bit 1 [ { "acesDictionary": { "Microsoft.TeamFoundation.Identity;00000000-0000-0000-0000-000000000000": { "allow": 1, "deny": 0, "descriptor": "Microsoft.TeamFoundation.Identity;00000000-0000-0000-0000-000000000000", "extendedInfo": { "effectiveAllow": 1 }, "resolvedPermissions": [ { "bit": 1, "displayName": "View Subscriptions", "effectivePermission": "Allow", "name": "ViewSubscriptions" } ] } }, "includeExtendedInfo": true, "inheritPermissions": true, "token": "PublisherSecurity/00000000-0000-0000-0000-000000000000" } ]Get permission token to see your changes.
> az devops security permission list --id 00000000-0000-0000-0000-000000000000 --subject <Group or user descriptor> --output table Token Effective Allow Effective Deny ------------------------------------------------------ ----------------- ---------------- PublisherSecurity 0 0 PublisherSecurity/00000000-0000-0000-0000-000000000000 1 0
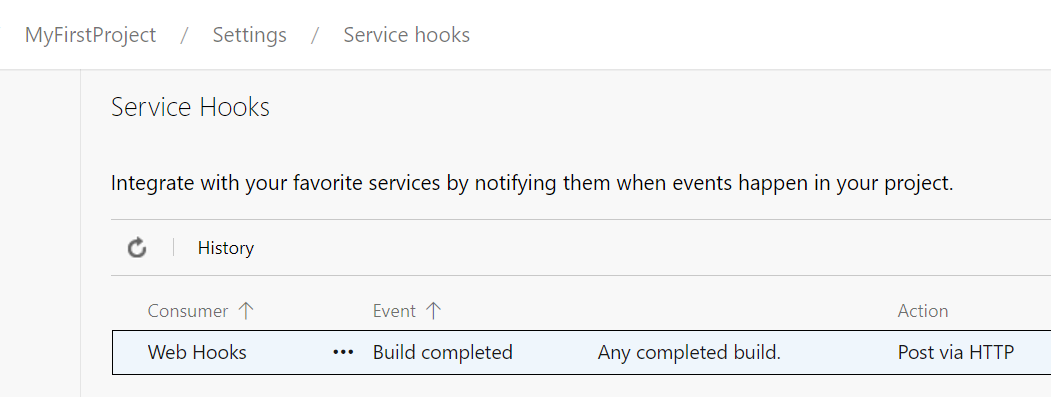
The following example shows that the user can see the service hooks subscriptions.
Reset all Service Hooks permissions of a group
If you need to reset all Service Hooks permissions of a group or user, you can call
reset-all.> az devops security permission reset-all --id 00000000-0000-0000-0000-000000000000 --subject <Group or user descriptor> --token PublisherSecurity/00000000-0000-0000-0000-000000000000 Are you sure you want to reset all explicit permissions for this user/group and token? (y/n): Y true > az devops security permission list --id 00000000-0000-0000-0000-000000000000 --subject <Group or user descriptor> --output table Token Effective Allow Effective Deny ------------------------------------------------------ ----------------- ---------------- PublisherSecurity 0 0 PublisherSecurity/00000000-0000-0000-0000-000000000000 0 0The following example shows that the user can't view to service hooks subscriptions after the permission gets reset.