Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Use CA certificate chain in Azure Event Grid to authenticate clients while connecting to the service.
In this guide, you perform the following tasks:
- Upload a CA certificate, the immediate parent certificate of the client certificate, to the namespace.
- Configure client authentication settings.
- Connect a client using the client certificate signed by the previously uploaded CA certificate.
Prerequisites
- You need an Event Grid Namespace already created.
- You need a CA certificate chain: Client certificates and the parent certificate (typically an intermediate certificate) that was used to sign the client certificates.
Generate sample client certificate and thumbprint
If you don't already have a certificate, you can create a sample certificate using the step CLI. Consider installing manually for Windows.
- Once you installed Step, in Windows PowerShell, run the command to create root and intermediate certificates.
.\step ca init --deployment-type standalone --name MqttAppSamplesCA --dns localhost --address 127.0.0.1:443 --provisioner MqttAppSamplesCAProvisioner
- Using the CA files generated to create certificate for the client.
.\step certificate create client1-authnID client1-authnID.pem client1-authnID.key --ca .step/certs/intermediate_ca.crt --ca-key .step/secrets/intermediate_ca_key --no-password --insecure --not-after 2400h
- To view the thumbprint, run the Step command.
step certificate fingerprint client1-authn-ID.pem
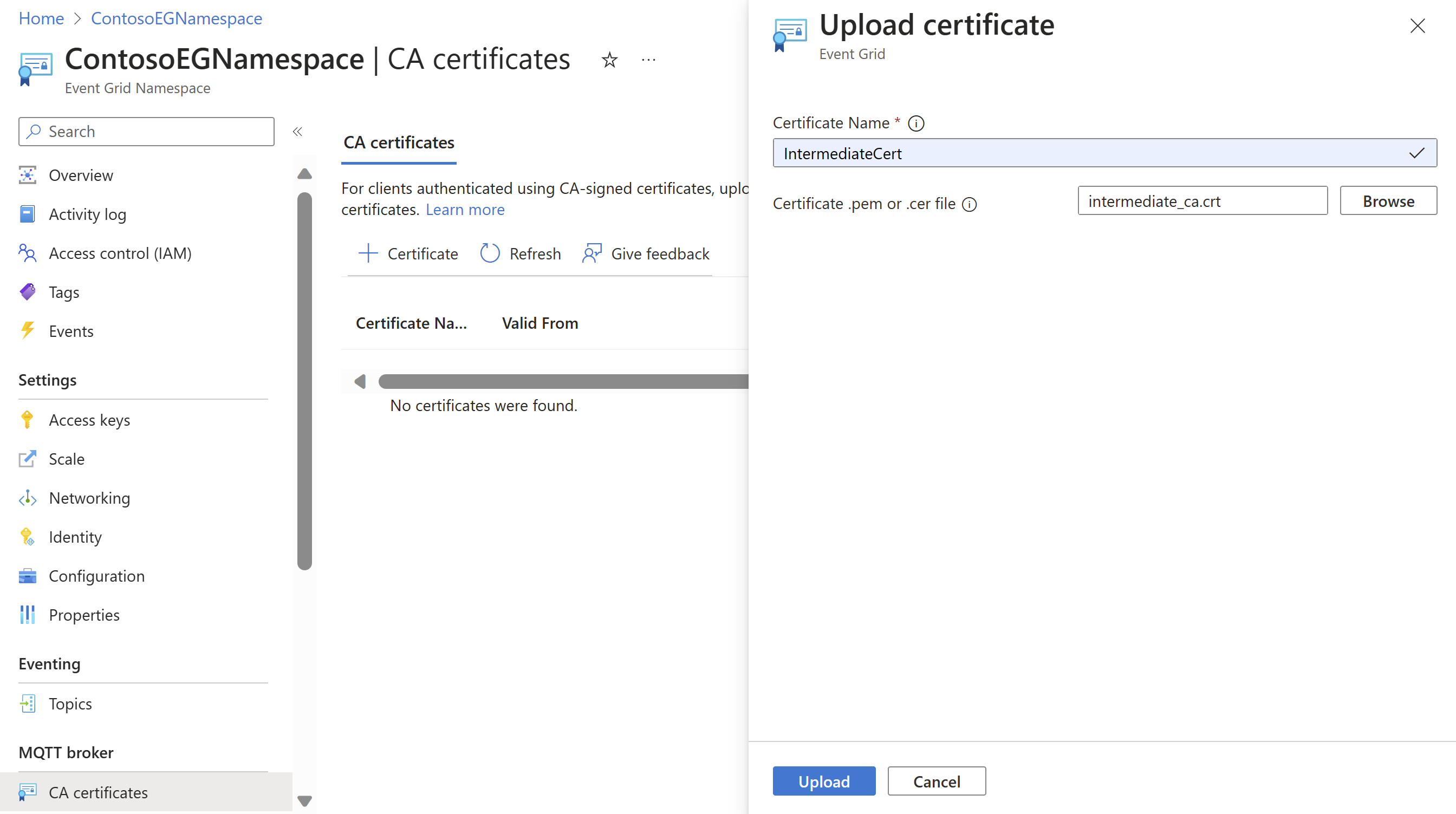
Upload the CA certificate to the namespace
- In Azure portal, navigate to your Event Grid namespace.
- Under the MQTT broker section in left rail, navigate to CA certificates menu.
- Select + Certificate to launch the Upload certificate page.
- Add certificate name and browse to find the intermediate certificate (.step/certs/intermediate_ca.crt) and select Upload. You can upload a file of .pem, .cer, or .crt type.
Note
- CA certificate name can be 3-50 characters long.
- CA certificate name can include alphanumeric, hyphen(-) and, no spaces.
- The name needs to be unique per namespace.
Configure client authentication settings
- Navigate to the Clients page.
- Select + Client to add a new client. If you want to update an existing client, you can select the client name and open the Update client page.
- In the Create client page, add the client name, client authentication name, and the client certificate authentication validation scheme. Typically the client authentication name would be in the subject name field for the client certificate.
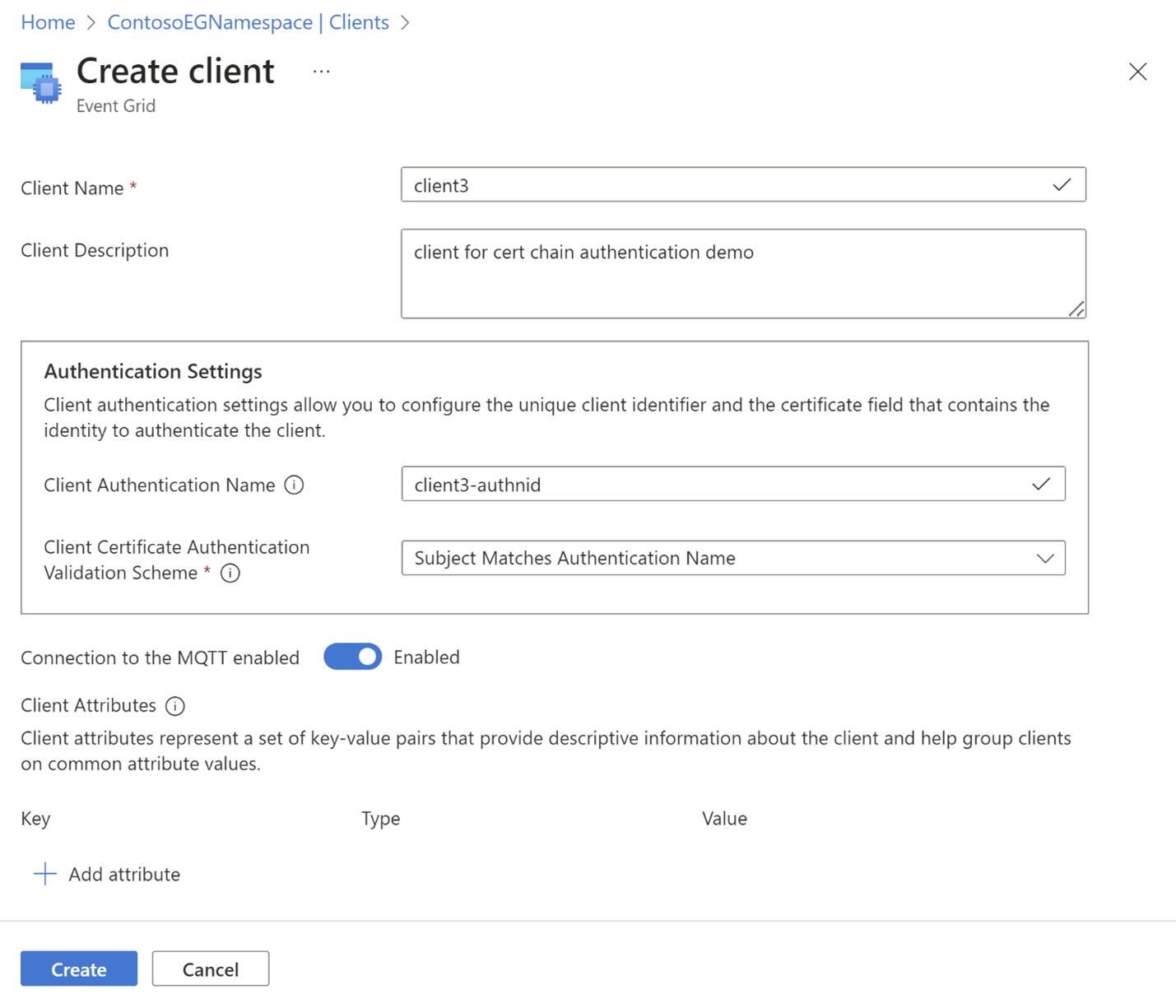
- Select Create button to create the client.
Sample certificate object schema
{
"properties": {
"description": "CA certificate description",
"encodedCertificate": "-----BEGIN CERTIFICATE-----`Base64 encoded Certificate`-----END CERTIFICATE-----"
}
}
Azure CLI configuration
Use the following commands to upload/show/delete a certificate authority (CA) certificate to the service
Upload certificate authority root or intermediate certificate
az eventgrid namespace ca-certificate create -g myRG --namespace-name myNS -n myCertName --certificate @./resources/ca-cert.json
Show certificate information
az eventgrid namespace ca-certificate show -g myRG --namespace-name myNS -n myCertName
Delete certificate
az eventgrid namespace ca-certificate delete -g myRG --namespace-name myNS -n myCertName