How to manage the Private access traffic forwarding profile
The Private Access traffic forwarding profile routes traffic to your private network through the Global Secure Access Client. Enabling this traffic forwarding profile allows remote workers to connect to internal resources without a VPN. With the features of Microsoft Entra Private Access, you can control which private resources to tunnel through the service and apply Conditional Access policies to secure access to those services. Once your configurations are in place, you can view and manage all of those configurations from one place.
Prerequisites
To enable the Microsoft 365 traffic forwarding profile for your tenant, you must have:
- A Global Secure Access Administrator role in Microsoft Entra ID
- The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses.
Known limitations
- At this time, Private Access traffic can only be acquired with the Global Secure Access Client. Private Access traffic can't be acquired from remote networks.
- Tunneling traffic to Private Access destinations by IP address is supported only for IP ranges outside of the end-user device local subnet.
- You must disable DNS over HTTPS (Secure DNS) to tunnel network traffic based on the rules of the fully qualified domain names (FQDNs) in the traffic forwarding profile.
Enable the Private access traffic forwarding profile
- Sign in to the Microsoft Entra admin center.
- Browse to Global Secure Access (preview) > Connect > Traffic forwarding.
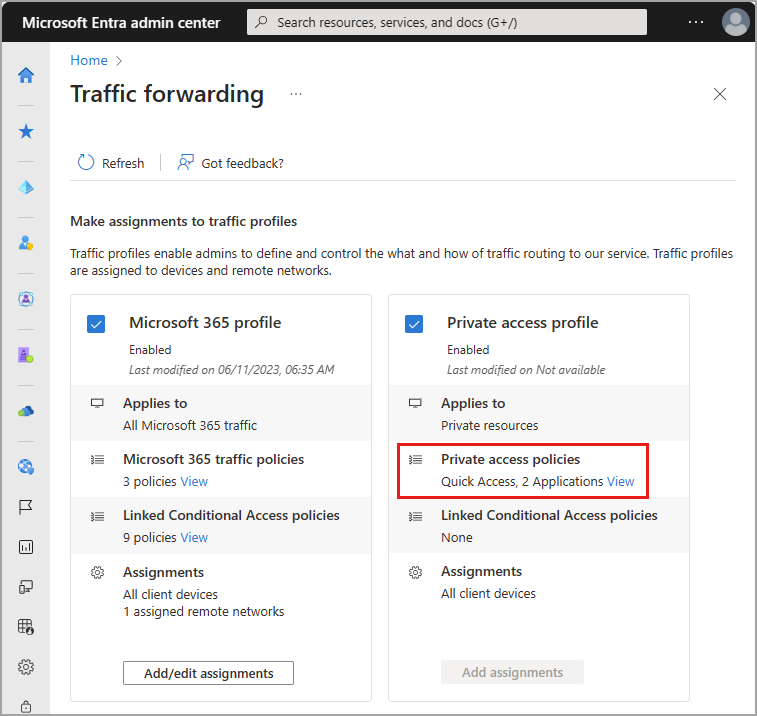
- Select the checkbox for Private Access profile.
Private Access policies
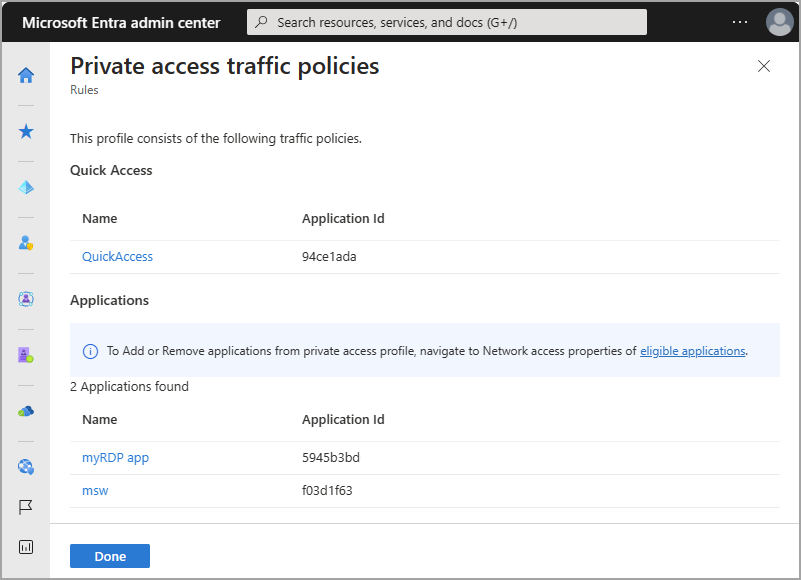
To enable the Private Access traffic forwarding profile, we recommend you first configure Quick Access. Quick Access includes the IP addresses, IP ranges, and fully qualified domain names (FQDNs) for the private resources you want to include in the policy. For more information, see Configure Quick Access.
You can also configure per-app access to your private resources by creating a Private Access app. Similar to Quick Access, you create a new Enterprise app, which can then be assigned to the Private Access traffic forwarding profile. Quick Access contains the main group of private resources you always want to route through the service. Private Access apps can be enabled and disabled as needed without impacting the FQDNs and IP addresses included in Quick Access.
To manage the details included in the Private access traffic forwarding policy, select the View link for Private access policies.
Details of your Quick Access and enterprise apps for Private Access are displayed. Select the link for the application to view the details from the Enterprise applications area of Microsoft Entra ID.
Linked Conditional Access policies
Conditional Access policies for Private Access are configured at the application level for each app. Conditional Access policies can be created and applied to the application from two places:
- Go to Global Secure Access (preview) > Applications > Enterprise applications. Select an application and then select Conditional Access from the side menu.
- Go to Protection > Conditional Access > Policies. Select + Create new policy.
For more information, see Apply Conditional Access policies to Private Access apps.
Edit an existing Conditional Access policy
- Select the View link for Linked Conditional Access policies.
- Select a policy from the list. The details of the policy open in Conditional Access.
Terms of Use
Your use of the Microsoft Entra Private Access and Microsoft Entra Internet Access preview experiences and features is governed by the preview online service terms and conditions of the agreement(s) under which you obtained the services. Previews may be subject to reduced or different security, compliance, and privacy commitments, as further explained in the Universal License Terms for Online Services and the Microsoft Products and Services Data Protection Addendum (“DPA”), and any other notices provided with the Preview.
Next steps
The next step for getting started with Microsoft Entra Internet Access is to install and configure the Global Secure Access Client on end-user devices.
For more information about Private Access, see the following articles:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for