Overview of the Azure Security Benchmark Foundation blueprint sample
Important
On July 11, 2026, Blueprints (Preview) will be deprecated. Migrate your existing blueprint definitions and assignments to Template Specs and Deployment Stacks. Blueprint artifacts are to be converted to ARM JSON templates or Bicep files used to define deployment stacks. To learn how to author an artifact as an ARM resource, see:
The Azure Security Benchmark Foundation blueprint sample provides a set of baseline infrastructure patterns to help you build a secure and compliant Azure environment. The blueprint helps you deploy a cloud-based architecture that offers solutions to scenarios that have accreditation or compliance requirements. It deploys and configures network boundaries, monitoring, and other resources in alignment with the policies and other guardrails defined in the Azure Security Benchmark.
Architecture
The foundational environment created by this blueprint sample is based on the architecture principals of a hub and spoke model. The blueprint deploys a hub virtual network that contains common and shared resources, services, and artifacts such as Azure Bastion, gateway and firewall for connectivity, management and jump box subnets to host additional/optional management, maintenance, administration, and connectivity infrastructure. One or more spoke virtual networks are deployed to host application workloads such as web and database services. Spoke virtual networks are connected to the hub virtual network using Azure virtual network peering for seamless and secure connectivity. Additional spokes can be added by reassigning the sample blueprint or manually creating an Azure virtual network and peering it with the hub virtual network. All external connectivity to the spoke virtual network(s) and subnet(s) is configured to route through the hub virtual network and, via firewall, gateway, and management jump boxes.
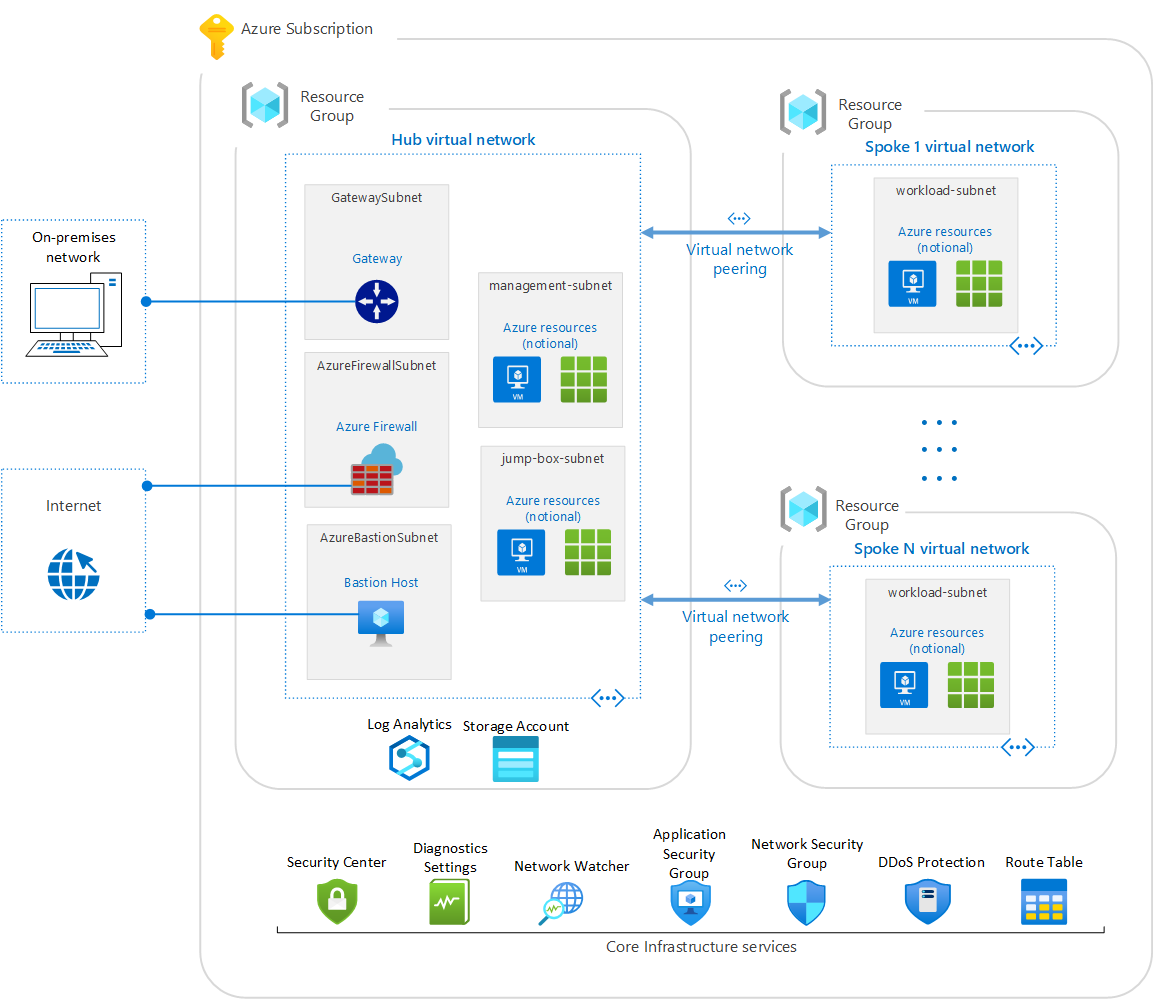
This blueprint deploys several Azure services to provide a secure, monitored, enterprise-ready foundation. This environment is composed of:
- Azure Monitor Logs and an Azure storage account to ensure resource logs, activity logs, metrics, and networks traffic flows are stored in a central location for easy querying, analytics, archival, and alerting.
- Azure Security Center (standard version) to provide threat protection for Azure resources.
- Azure Virtual Network in the hub supporting subnets for connectivity back to an on-premises network, an ingress and egress stack to/for Internet connectivity, and optional subnets for deployment of additional administrative or management services. Virtual Network in the spoke contains subnets for hosting application workloads. Additional subnets can be created after deployment as needed to support applicable scenarios.
- Azure Firewall to route all outbound internet traffic and to enable inbound internet traffic via jump box. (Default firewall rules block all internet inbound and outbound traffic and rules must be configured after deployment, as applicable.)
- Network security groups (NSGs) assigned to all subnets (except service-owned subnets such as Azure Bastion, Gateway and Azure Firewall) configured to block all internet inbound and outbound traffic.
- Application security groups to enable grouping of Azure virtual machines to apply common network security policies.
- Route tables to route all outbound internet traffic from subnets through the firewall. (Azure Firewall and NSG rules will need to be configured after deployment to open connectivity.)
- Azure Network Watcher to monitor, diagnose, and view metrics of resources in the Azure virtual network.
- Azure DDoS Protection to protect Azure resources against DDoS attacks.
- Azure Bastion to provide seamless and secure connectivity to a virtual machine that does not require a public IP address, agent, or special client software.
- Azure VPN Gateway to enable encrypted traffic between an Azure virtual network and an on-premises location over the public Internet.
Note
The Azure Security Benchmark Foundation lays out a foundational architecture for workloads. The architecture diagram above includes several notional resources to demonstrate potential use of subnets. You still need to deploy workloads on this foundational architecture.
Next steps
You've reviewed the overview and architecture of the Azure Security Benchmark Foundation blueprint sample.
Additional articles about blueprints and how to use them:
- Learn about the blueprint lifecycle.
- Understand how to use static and dynamic parameters.
- Learn to customize the blueprint sequencing order.
- Find out how to make use of blueprint resource locking.
- Learn how to update existing assignments.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for