Tutorial: Disallow resource types in your cloud environment
One popular goal of cloud governance is restricting what resource types are allowed in the environment. Businesses have many motivations behind resource type restrictions. For example, resource types might be costly or might go against business standards and strategies. Rather than using many policies for individual resource types, Azure Policy offers two built-in policies to achieve this goal:
| Name (Azure portal) |
Description | Effect | Version (GitHub) |
|---|---|---|---|
| Allowed resource types | This policy enables you to specify the resource types that your organization can deploy. Only resource types that support 'tags' and 'location' are affected by this policy. To restrict all resources, duplicate this policy and change the 'mode' to 'All'. | deny | 1.0.0 |
| Not allowed resource types | Restrict which resource types can be deployed in your environment. Limiting resource types can reduce the complexity and attack surface of your environment while also helping to manage costs. Compliance results are only shown for non-compliant resources. | Audit, Deny, Disabled | 2.0.0 |
In this tutorial, you apply the Not allowed resource types policy and manage resource types at scale through Microsoft Azure portal.
Prerequisites
If you don't have an Azure subscription, create a free account before you begin.
Assign the policy definition
The first step in disabling resource types is to assign the Not allowed resource types policy definition.
Go to Not allowed resource types in Azure portal.
Select the Assign button on the top of the page.
On the Basics tab, set the Scope by selecting the ellipsis and choosing a management group, subscription, or resource group. Ensure that the selected scope has at least one subscope. Then click Select at the bottom of the Scope page.
This example uses the Contoso subscription.
Note
If you assign this policy definition to your root management group scope, the portal can detect disallowed resource types and disable them in the All Services view so that portal users are aware of the restriction before trying to deploy a disallowed resource.
Resources can be excluded based on the Scope. Exclusions start at one level lower than the level of the Scope. Exclusions are optional, so leave it blank for now.
The Assignment name is automatically populated with the policy definition name you selected, but you can change it. You can also add an optional Description to provide details about this policy assignment.
Leave Policy enforcement as Enabled. When Disabled, this setting allows testing the outcome of the policy without triggering the effect. For more information, see enforcement mode.
Assigned by is automatically filled based on who is logged in. This field is optional, so custom values can be entered.
Select the Parameters tab at the top of the wizard. This tutorial skips the Advanced tab.
For the Not allowed resource types parameter, use the drop-down to search and select resource types that shouldn't be allowed in your cloud environment.
This policy definition doesn't have the
modifyordeployIfNotExistseffects, so it doesn't support remediation tasks. For this tutorial, skip the Remediation tab.Select the Non-compliance messages tab at the top of the wizard.
Set the Non-compliance message to This resource type isn't allowed. This custom message is displayed when a resource is denied or for non-compliant resources during regular evaluation.
Select the Review + create tab at the top of the wizard.
Review your selections, then select Create at the bottom of the page.
View disabled resource types in Azure portal
This step only applies when the policy was assigned at the root management group scope.
Now that you assigned a built-in policy definition, go to All Services. Azure portal is aware of the disallowed resource types from this policy assignment and disables them in the All Services page. The Create option is unavailable for disabled resource types.
Note
If you assign this policy definition to your root management group, users will see the following notification when they sign in for the first time or if the policy changes after they have signed in:
Policy changed by admin Your administrator has made changes to the policies for your account. It is recommended that you refresh the portal to use the updated policies.
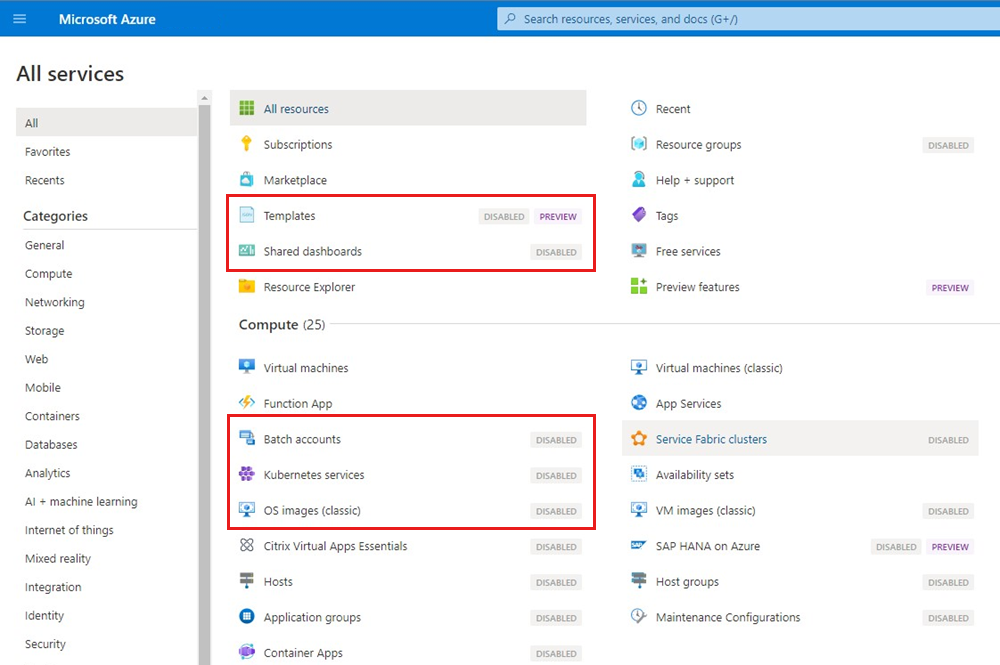
Create an exemption
Now suppose that one subscope should be allowed to have the resource types disabled by this policy. Let's create an exemption on this scope so that otherwise restricted resources can be deployed there.
Warning
If you assign this policy definition to your root management group scope, Azure portal is unable to detect exemptions at lower level scopes. Resources disallowed by the policy assignment will show as disabled from the All Services list and the Create option is unavailable. But you can create resources in the exempted scope with clients like Azure CLI, Azure PowerShell, or Azure Resource Manager templates.
Select Assignments under Authoring in the left side of the Azure Policy page.
Search for the policy assignment you created.
Select the Create exemption button on the top of the page.
In the Basics tab, select the Exemption scope, which is the subscope that should be allowed to have resources restricted by this policy assignment.
Fill out Exemption name with the desired text, and leave Exemption category as the default of Waiver. Don't switch the toggle for Exemption expiration setting, because this exemption won't be set to expire. Optionally add an Exemption description, and select Review + create.
This tutorial bypasses the Advanced tab. From the Review + create tab, select Create.
To view the exemption, select Exemptions under Authoring in the left side of the Azure Policy page.
Now your subscope can have the resource types disallowed by the policy.
Clean up resources
If you're done working with resources from this tutorial, use the following steps to delete any of the policy assignments or definitions created in this tutorial:
Select Definitions (or Assignments if you're trying to delete an assignment) under Authoring in the left side of the Azure Policy page.
Search for the new initiative or policy definition (or assignment) you want to remove.
Right-click the row or select the ellipses at the end of the definition (or assignment), and select Delete definition (or Delete assignment).
Review
In this tutorial, you successfully accomplished the following tasks:
- Assigned the Not allowed resource types built-in policy to deny creation of disallowed resource types
- Created an exemption for this policy assignment at a subscope
With this built-in policy you specified resource types that aren't allowed. The alternative, more restrictive approach is to specify resource types that are allowed using the Allowed resource types built-in policy.
Note
Azure portal's All Services will only disable resources not specified in the allowed resource type policy if the mode is set to All and the policy is assigned at the root management group. This is because it checks all resource types regardless of tags and locations. If you want the portal to have this behavior, duplicate the Allowed resource types built-in policy and change its mode from Indexed to All, then assign it to the root management group scope.
Next steps
To learn more about the structures of policy definitions, assignments, and exemptions, look at these articles:
Azure Policy definition structure Azure Policy assignment structure Azure Policy exemption structure
To see a full list of built-in policy samples, view this article: