Manage cluster access
Important
This feature is currently in preview. The Supplemental Terms of Use for Microsoft Azure Previews include more legal terms that apply to Azure features that are in beta, in preview, or otherwise not yet released into general availability. For information about this specific preview, see Azure HDInsight on AKS preview information. For questions or feature suggestions, please submit a request on AskHDInsight with the details and follow us for more updates on Azure HDInsight Community.
This article provides an overview of the mechanisms available to manage access for HDInsight on AKS cluster pools and clusters. It also covers how to assign permission to users, groups, user-assigned managed identity, and service principals to enable access to cluster data plane.
When a user creates a cluster, then that user is authorized to perform the operations with data accessible to the cluster. However, to allow other users to execute queries and jobs on the cluster, access to cluster data plane is required.
Manage cluster pool or cluster access (Control plane)
The following HDInsight on AKS and Azure built-in roles are available for cluster management to manage the cluster pool or cluster resources.
| Role | Description |
|---|---|
| Owner | Grants full access to manage all resources, including the ability to assign roles in Azure RBAC. |
| Contributor | Grants full access to manage all resources but doesn't allow you to assign roles in Azure RBAC. |
| Reader | View all resources but doesn't allow you to make any changes. |
| HDInsight on AKS Cluster Pool Admin | Grants full access to manage a cluster pool including ability to delete the cluster pool. |
| HDInsight on AKS Cluster Admin | Grants full access to manage a cluster including ability to delete the cluster. |
You can use Access control (IAM) blade to manage the access for cluster pool’s and control plane.
Refer: Grant a user access to Azure resources using the Azure portal - Azure RBAC.
Manage cluster access (Data plane)
This access enables you to do the following actions:
- View clusters and manage jobs.
- All the monitoring and management operations.
- To enable auto scale and update the node count.
The access is restricted for:
- Cluster deletion.
To assign permission to users, groups, user-assigned managed identity, and service principals to enable access to cluster’s data plane, the following options are available:
Using Azure portal
How to grant access
The following steps describe how to provide access to other users, groups, user-assigned managed identity, and service principals.
Navigate to the Cluster access blade of your cluster in the Azure portal and click Add.
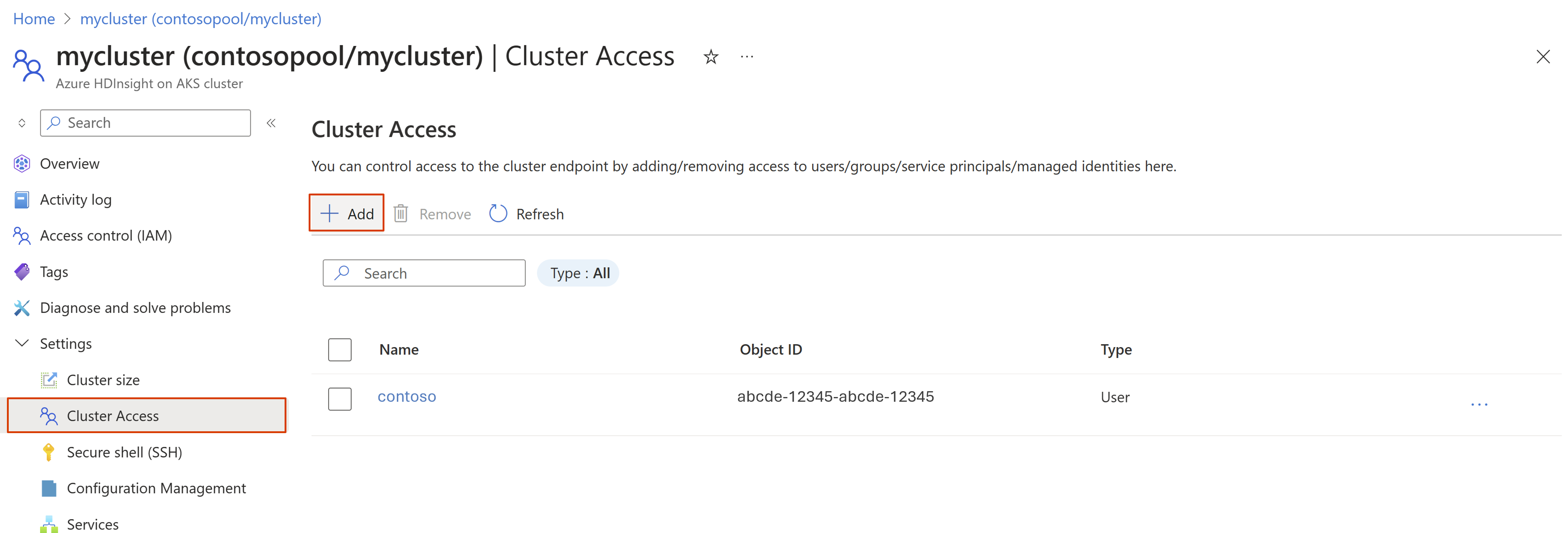
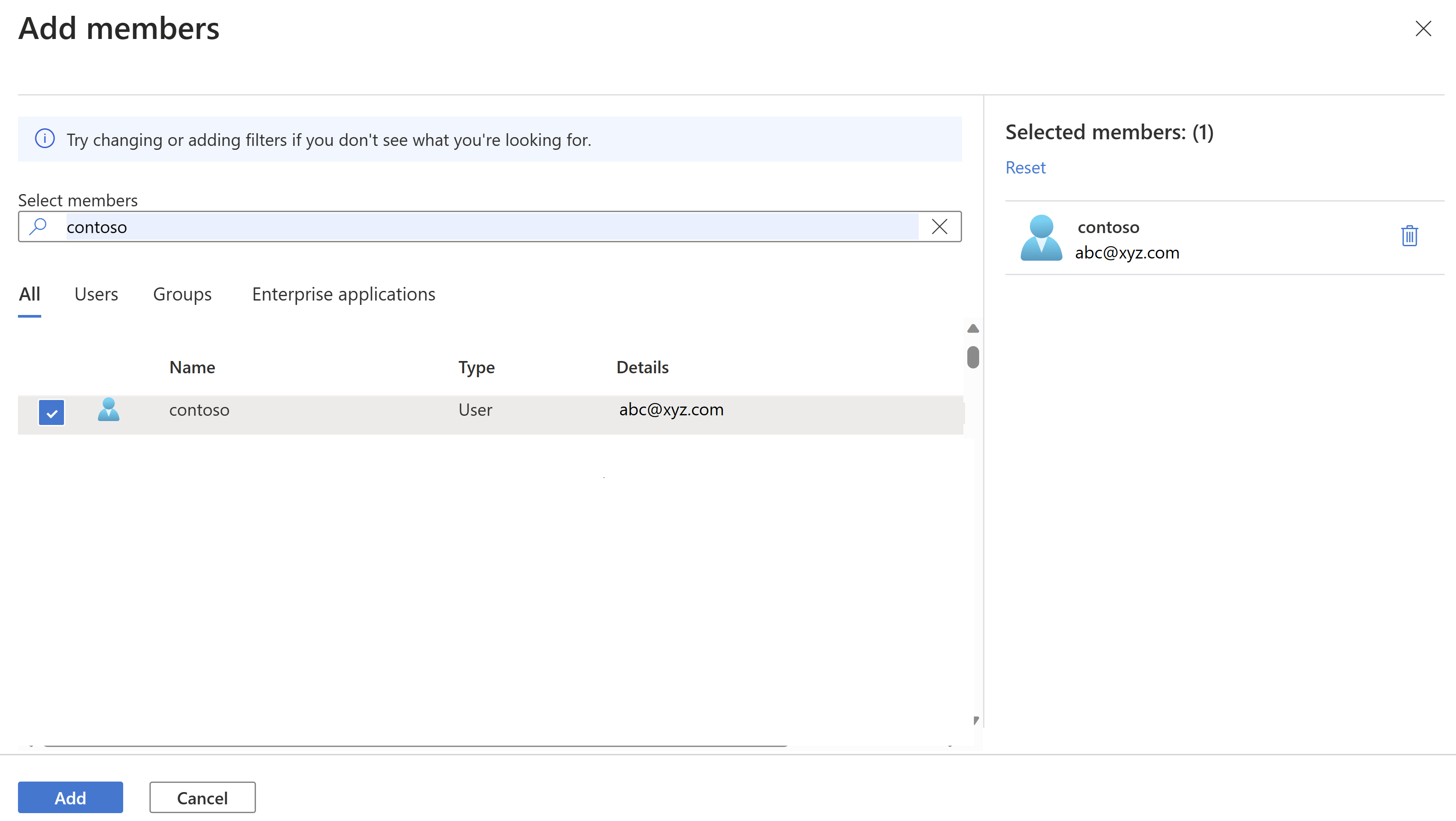
Search for the user/group/user-assigned managed identity/service principal to grant access and click Add.
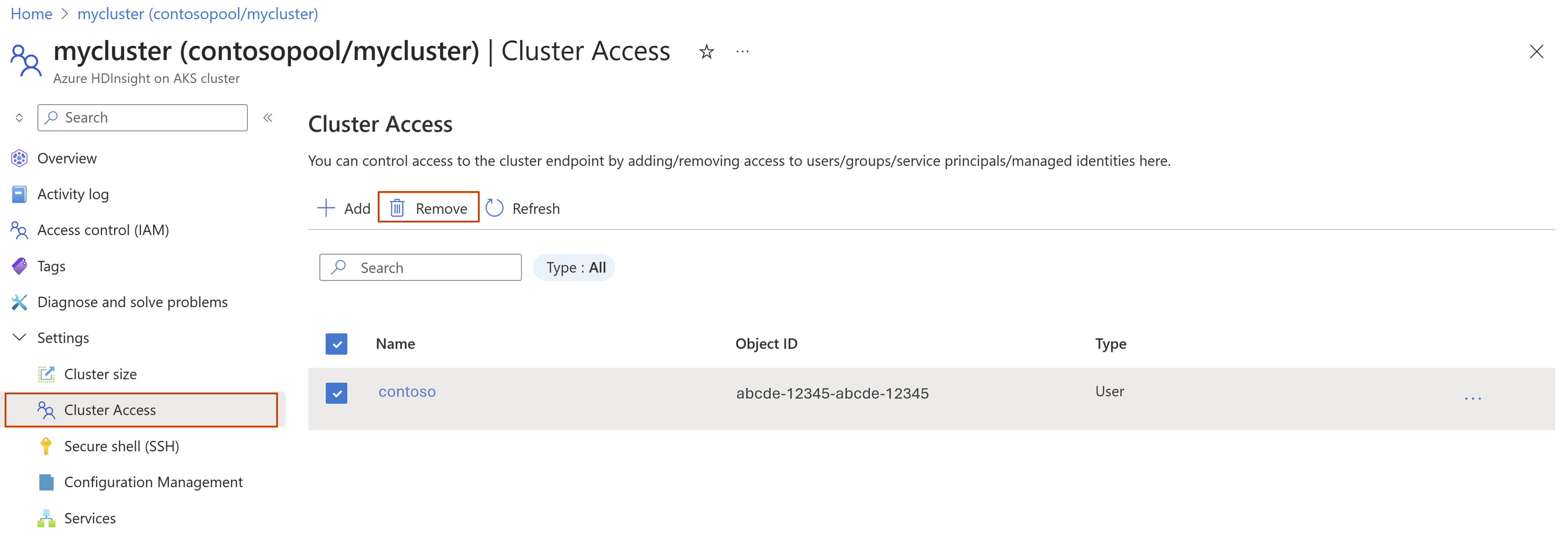
How to remove access
Select the members to be removed and click Remove.
Using ARM template
Prerequisites
- An operational HDInsight on AKS cluster.
- ARM template for your cluster.
- Familiarity with ARM template authoring and deployment.
Follow the steps to update authorizationProfile object under clusterProfile section in your cluster ARM template.
In the Azure portal search bar, search for user/group/user-assigned managed identity/service principal.
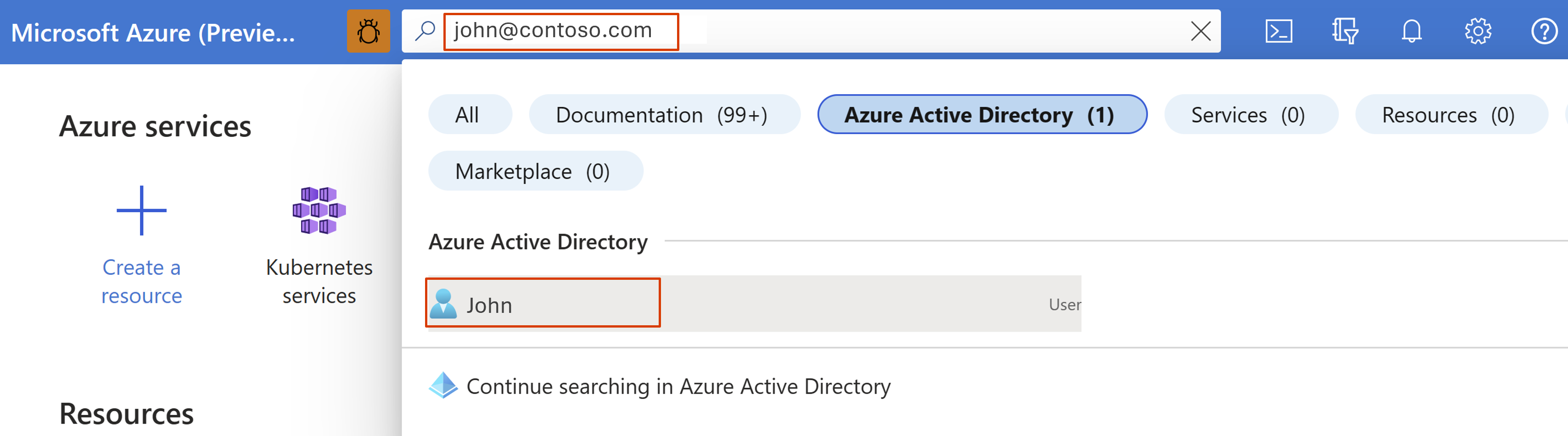
Copy the Object ID or Principal ID.
Modify the
authorizationProfilesection in your cluster ARM template.Add user/user-assigned managed identity/service principal Object ID or Principal ID under
userIdsproperty.Add groups Object ID under
groupIdsproperty."authorizationProfile": { "userIds": [ "abcde-12345-fghij-67890", "a1b1c1-12345-abcdefgh-12345" ], "groupIds": [] },
Deploy the updated ARM template to reflect the changes in your cluster. Learn how to deploy an ARM template.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for