Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article walks you through the steps to configure settings on the FHIR® service for import operations. To configure settings, you need to:
- Enable a managed identity on the FHIR service.
- Create an Azure storage account or use an existing storage account, and grant permissions for the FHIR service to access it.
- Set the import configuration of the FHIR service.
- Use one of the options to securely import FHIR data into the FHIR service from an Azure Data Lake Storage Gen2 account.
Step 1: Enable a managed identity on the FHIR service
The first step is to enable a system-wide managed identity on the service. This identity is used to grant FHIR service access to the storage account. For more information about managed identities in Azure, see About managed identities for Azure resources.
To enable a managed identity on the FHIR service:
- In the Azure portal, browse to your FHIR service.
- On the left menu, select Identity.
- Set the Status option to On, and then select Save.
- Select Yes.
After you enable the managed identity, a system-assigned GUID value appears.

Step 2: Assign permissions to the FHIR service
Use the following steps to assign permissions to access the storage account.
In the storage account, browse to Access Control (IAM).
Select Add role assignment. If the option for adding a role assignment is unavailable, ask your Azure administrator to assign you permission to perform this step.
For more information about assigning roles in the Azure portal, see Azure built-in roles.
Add the Storage Blob Data Contributor role to the FHIR service.
Select Save.

Now you're ready to select the storage account for import.
Step 3: Set the import configuration of the FHIR service
Note
If you haven't assigned storage access permissions to the FHIR service, the import operation will fail.
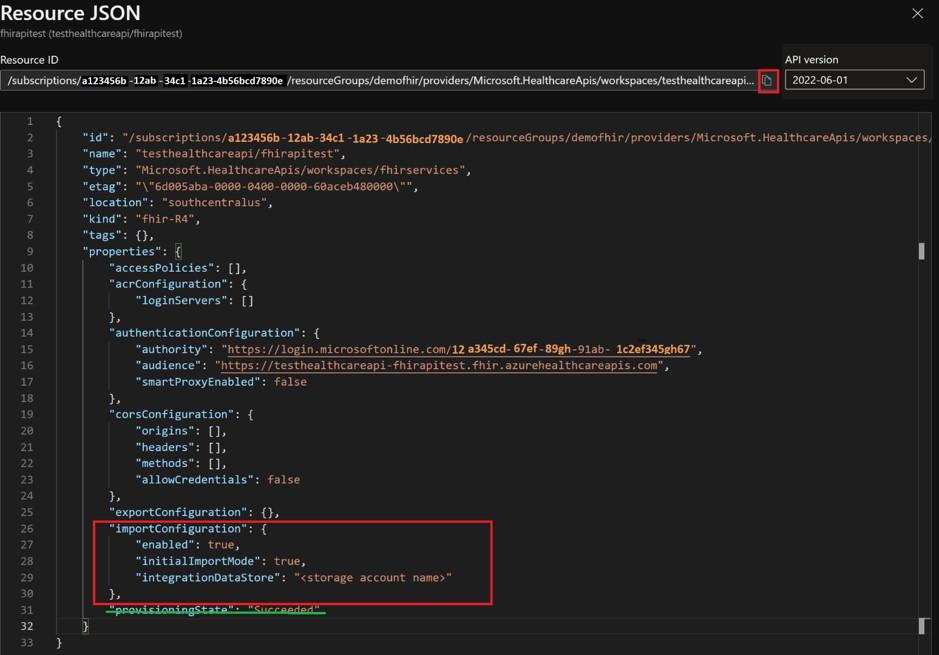
For this step, you need to get the request URL and JSON body.
- In the Azure portal, browse to your FHIR service.
- Select Overview.
- Select JSON View.
- Select the API version as 2022-06-01 or later.
To specify the Azure storage account in JSON view which is in READ mode, you need to use the REST API to update the FHIR service.
The following steps walk you through setting configurations for initial and incremental import modes. Choose the right import mode for your use case.
Set the import configuration for initial import mode
Make the following changes to JSON.
- In
importConfiguration, setenabledtotrue. - Update
integrationDataStorewith the target storage account name. - In
importConfiguration, setinitialImportModetotrue. - Delete the
provisioningStateline.
You're now ready to perform initial-mode import by using import.
Set the import configuration for incremental import mode
Make the following changes to JSON.
- In
importConfiguration, setenabledtotrue. - Update
integrationDataStorewith the target storage account name. - In
importConfiguration, setinitialImportModetofalse. - Delete the
provisioningStateline.
You're now ready to perform incremental-mode import by using import.
You can also use the Deploy to Azure button to open a custom Azure Resource Manager template that updates the configuration for import.
Step 4: Secure the FHIR service's import operation
To securely import FHIR data into the FHIR service from an Azure Data Lake Storage Gen2 account, you have three options:
- Enable the FHIR service as a trusted Microsoft service.
- Allow specific IP addresses associated with the FHIR service to access the storage account from other Azure regions.
- Allow specific IP addresses associated with the FHIR service to access the storage account in the same region as the FHIR service.
Enable the FHIR service as a trusted Microsoft service
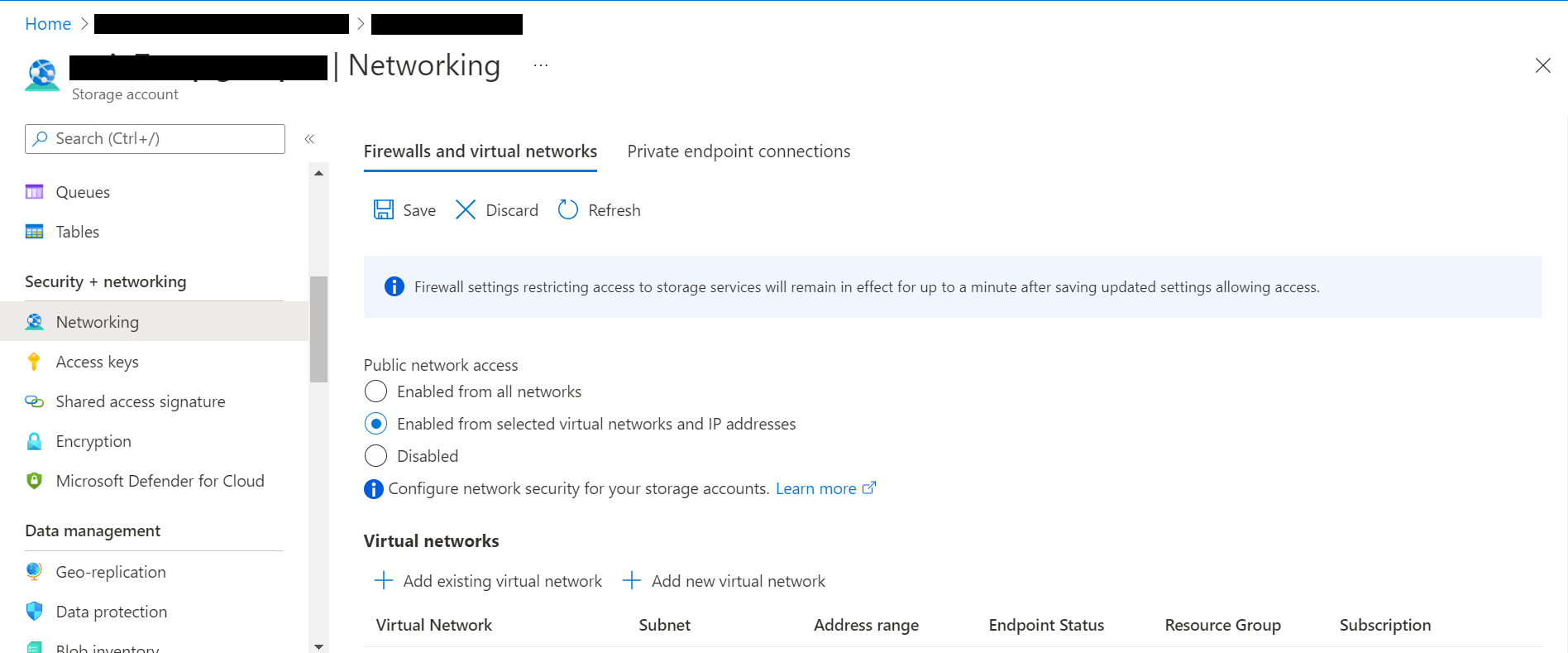
In the Azure portal, go to your Data Lake Storage Gen2 account.
On the left menu, select Networking.
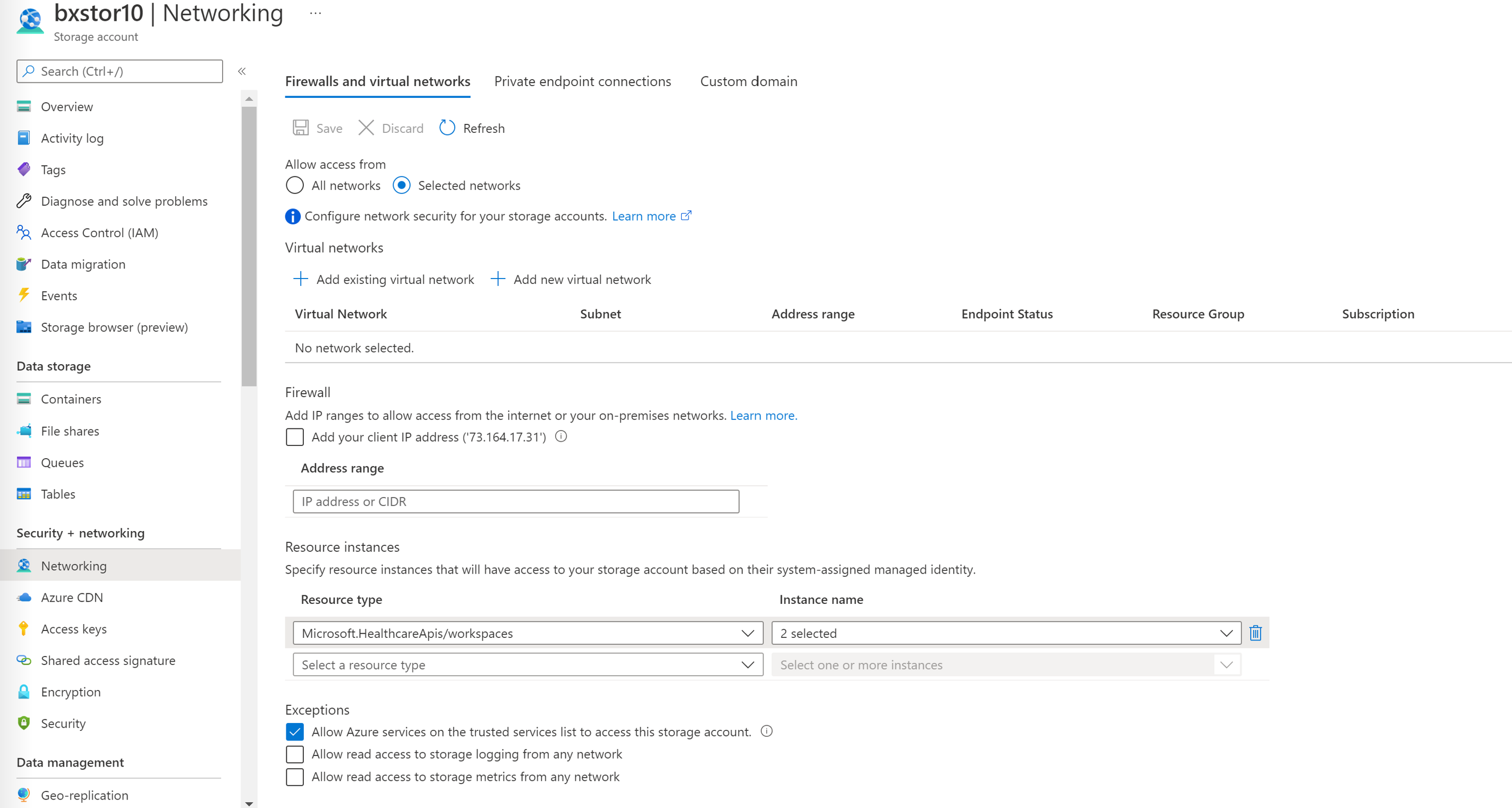
On the Firewalls and virtual networks tab, select Enabled from selected virtual networks and IP addresses.
In the Resource type dropdown list, select Microsoft.HealthcareApis/workspaces. In the Instance name dropdown list, select your workspace.
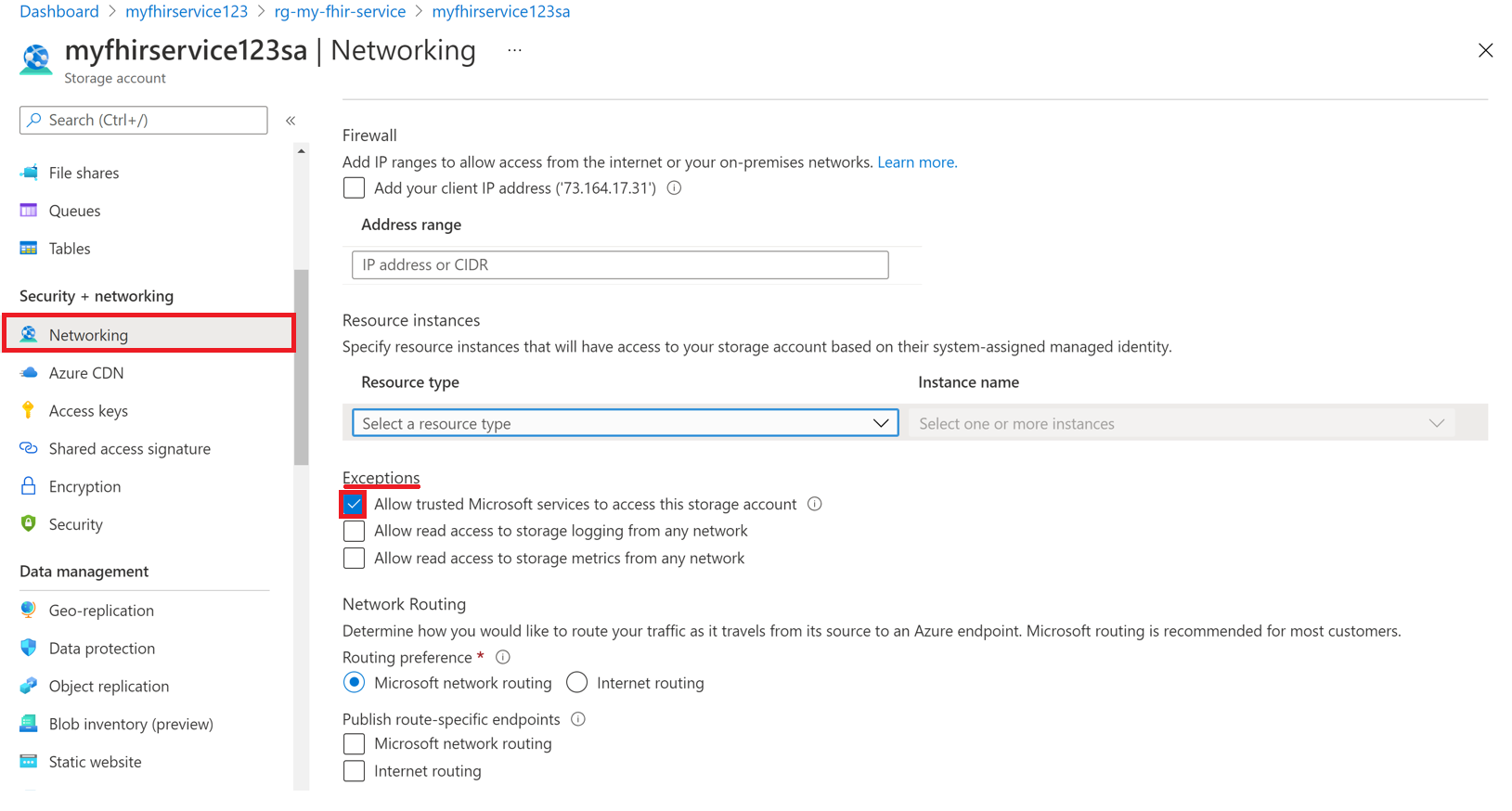
In the Exceptions section, select the Allow trusted Microsoft services to access this storage account checkbox.
Select Save to retain the settings.
Run the following PowerShell command to install the
Az.StoragePowerShell module in your local environment. You can use this module to configure your Azure storage accounts by using PowerShell.Install-Module Az.Storage -Repository PsGallery -AllowClobber -ForceUse the following PowerShell command to set the selected FHIR service instance as a trusted resource for the storage account. Make sure that all listed parameters are defined in your PowerShell environment.
You need to run the
Add-AzStorageAccountNetworkRulecommand as an administrator in your local environment. For more information, see Configure Azure Storage firewalls and virtual networks.$subscription="xxx" $tenantId = "xxx" $resourceGroupName = "xxx" $storageaccountName = "xxx" $workspacename="xxx" $fhirname="xxx" $resourceId = "/subscriptions/$subscription/resourceGroups/$resourceGroupName/providers/Microsoft.HealthcareApis/workspaces/$workspacename/fhirservices/$fhirname" Add-AzStorageAccountNetworkRule -ResourceGroupName $resourceGroupName -Name $storageaccountName -TenantId $tenantId -ResourceId $resourceIdConfirm that under Resource instances, 2 selected appears in the Instance name dropdown list. The two selected instances are the name of the workspace instance and the name of the FHIR service instance that you registered as trusted Microsoft resources.
You're now ready to securely import FHIR data from the storage account. The storage account is on selected networks and isn't publicly accessible. To securely access the files, you can use private endpoints for the storage account.
Allow specific IP addresses to access the Azure storage account from other Azure regions
In the Azure portal, go to the Azure Data Lake Storage Gen2 account.
On the left menu, select Networking.
Select Enabled from selected virtual networks and IP addresses.
In the Firewall section, in the Address range box, specify the IP address. Add IP ranges to allow access from the internet or your on-premises networks. You can find the IP address in the following table for the Azure region where the FHIR service is provisioned.
Azure region Public IP address Australia East 20.53.44.80 Canada Central 20.48.192.84 Central US 52.182.208.31 East US 20.62.128.148 East US 2 20.49.102.228 East US 2 EUAP 20.39.26.254 Germany North 51.116.51.33 Germany West Central 51.116.146.216 Japan East 20.191.160.26 Korea Central 20.41.69.51 North Central US 20.49.114.188 North Europe 52.146.131.52 South Africa North 102.133.220.197 South Central US 13.73.254.220 Southeast Asia 23.98.108.42 Switzerland North 51.107.60.95 UK South 51.104.30.170 UK West 51.137.164.94 West Central US 52.150.156.44 West Europe 20.61.98.66 West US 2 40.64.135.77
Allow specific IP addresses to access the Azure storage account in the same region
The configuration process for IP addresses in the same region is just like the previous procedure, except that you use a specific IP address range in Classless Inter-Domain Routing (CIDR) format instead (that is, 100.64.0.0/10). You must specify the IP address range (100.64.0.0 to 100.127.255.255) because an IP address for the FHIR service is allocated each time you make an operation request.
Note
It's possible to use a private IP address within the range of 10.0.2.0/24, but there's no guarantee that the operation will succeed in such a case. You can retry if the operation request fails, but until you use an IP address within the range of 100.64.0.0/10, the request won't succeed.
This network behavior for IP address ranges is by design. The alternative is to configure the storage account in a different region.
Next steps
In this article, you learned how the FHIR service supports the import operation, and how you can import data into the FHIR service from a storage account. You also learned about the steps for configuring import settings in the FHIR service. For more information about converting data to FHIR, exporting settings to set up a storage account, and moving data to Azure Synapse Analytics, see:
Note
FHIR® is a registered trademark of HL7 and is used with the permission of HL7.