Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
For users to access Azure Device Update for IoT Hub, you must grant them access to the Device Update account and instance. You must also grant the Device Update service principal access to the linked IoT hub so it can manage updates and gather information. This article describes how to grant the necessary access by using Azure role-based access control (RBAC) in the Azure portal or Azure CLI.
Prerequisites
- Owner or User Access Administrator role in your Azure subscription.
- A Device Update account and instance configured with an IoT hub.
- To run Azure CLI commands, the Bash environment in Azure Cloud Shell or Azure CLI installed locally.
Configure access control for Device Update account
The following roles are available for assigning access to Device Update:
- Device Update Administrator
- Device Update Reader
- Device Update Content Administrator
- Device Update Content Reader
- Device Update Deployments Administrator
- Device Update Deployments Reader
For more information, see Azure role-based access control (RBAC) and Device Update.
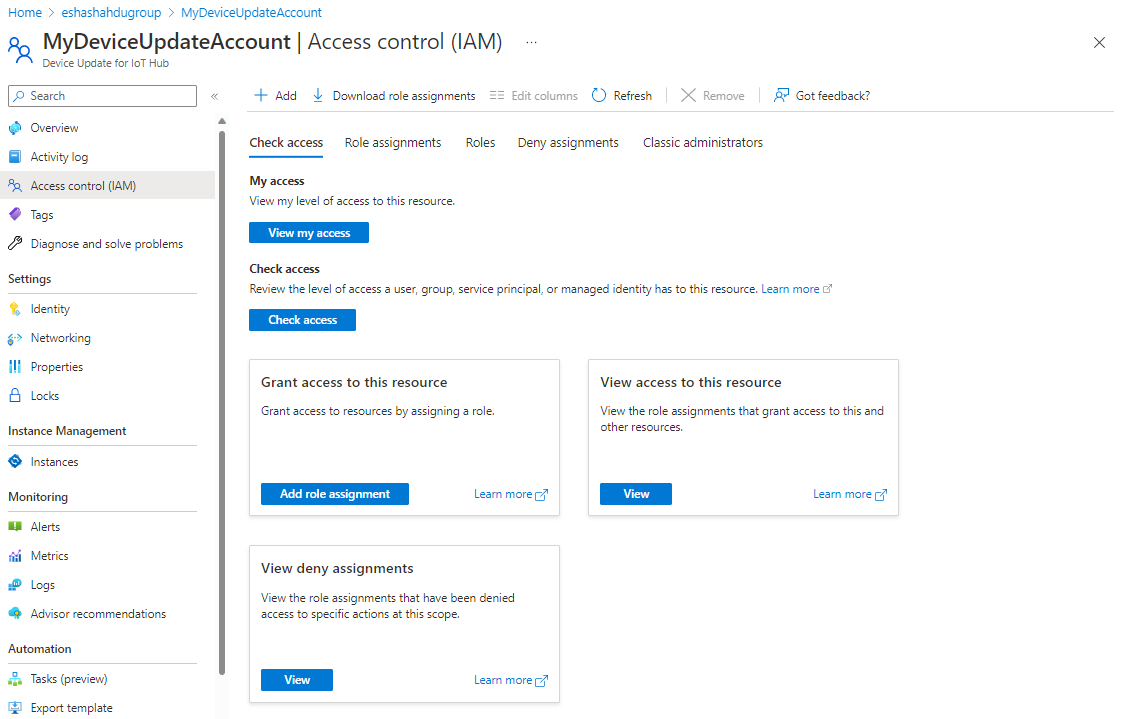
In your Device Update account in the Azure portal, select Access control (IAM) from the navigation menu, and then select Add role assignment.
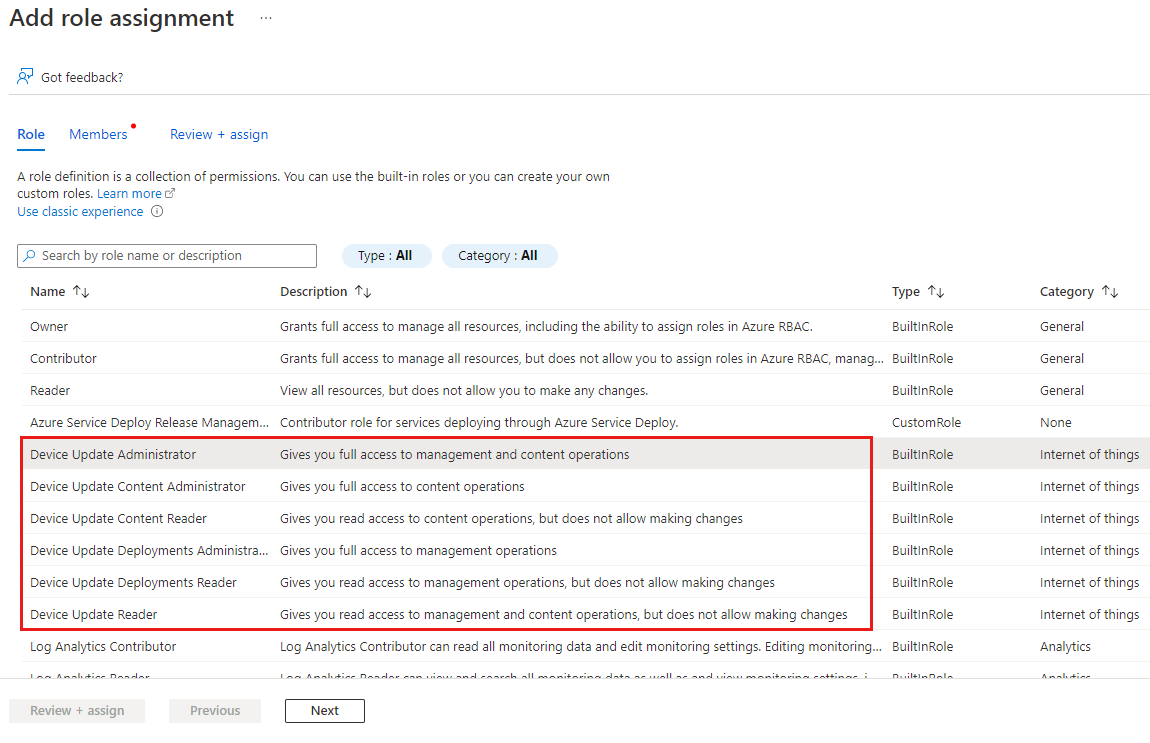
On the Role tab, select a Device Update role from the available options, and then select Next.
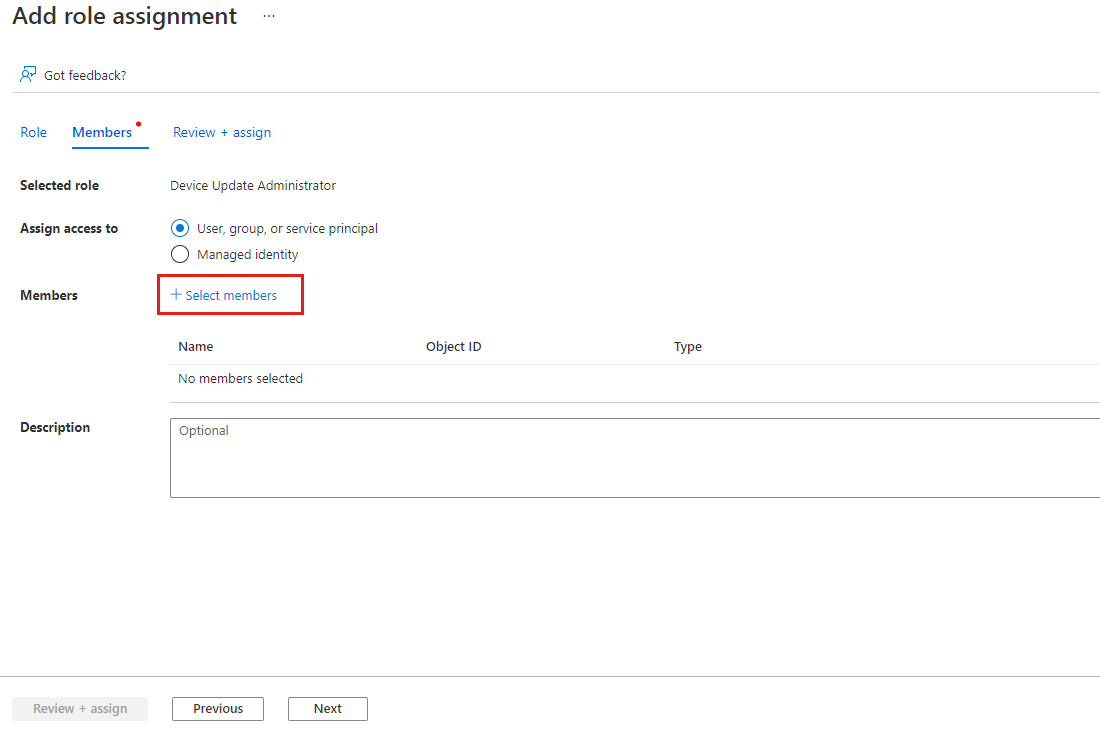
On the Members tab, select Select members, and add the users or groups that you want to assign the role to.
Select Review + assign.
Review the new role assignments and select Review + assign again.
Azure RBAC adds the role assignments, and the selected members can now use Device Update from within your IoT Hub.
Configure IoT hub access for the Device Update service principal
Device Update communicates with IoT Hub to manage deployments and updates and to get information about devices. To enable this communication, you need to give the Azure Device Update service principal access to the IoT hub with the IoT Hub Data Contributor role.
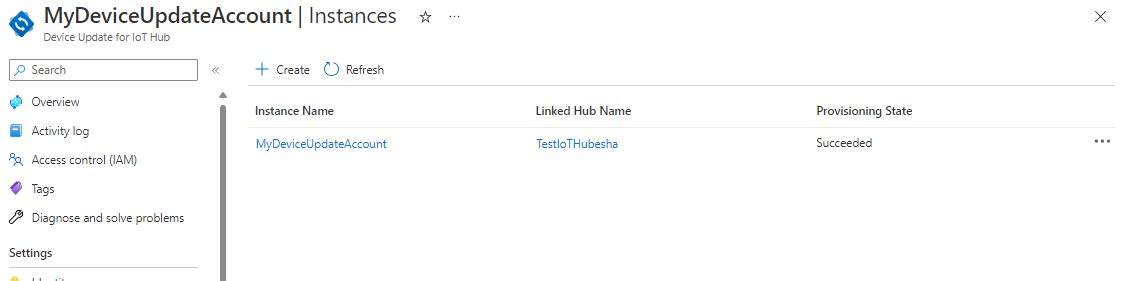
In your Device Update instance in the Azure portal, select the IoT hub connected to the instance.
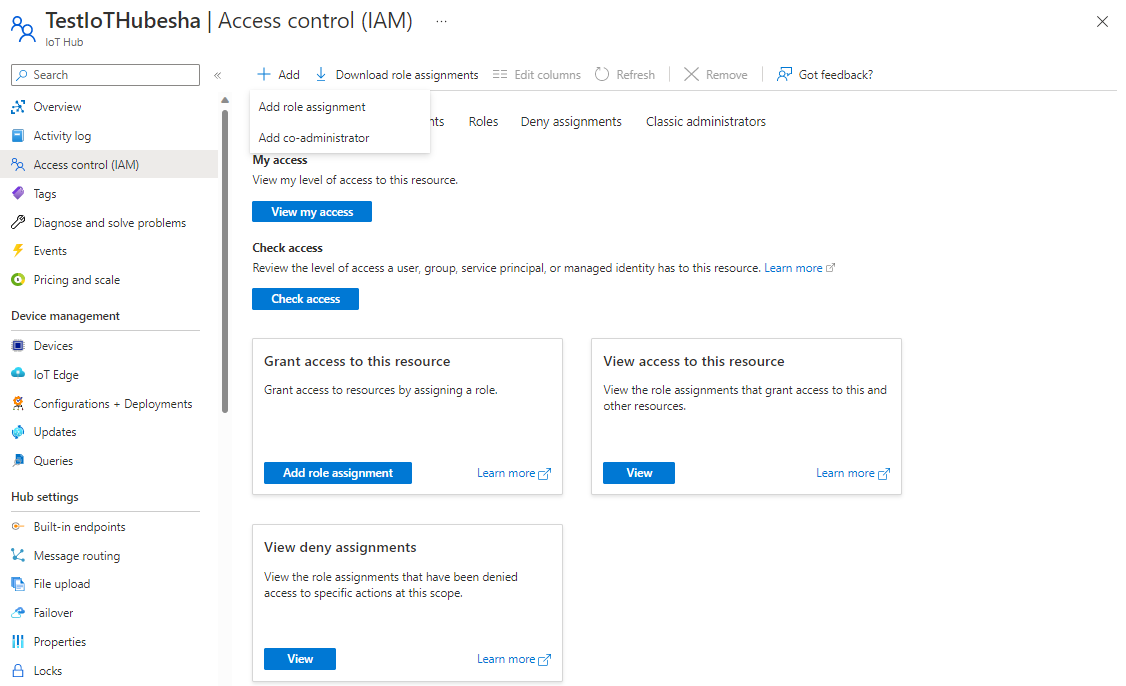
On the IoT hub page, select Access Control (IAM) from the left navigation menu.
Select Add > Add role assignment.
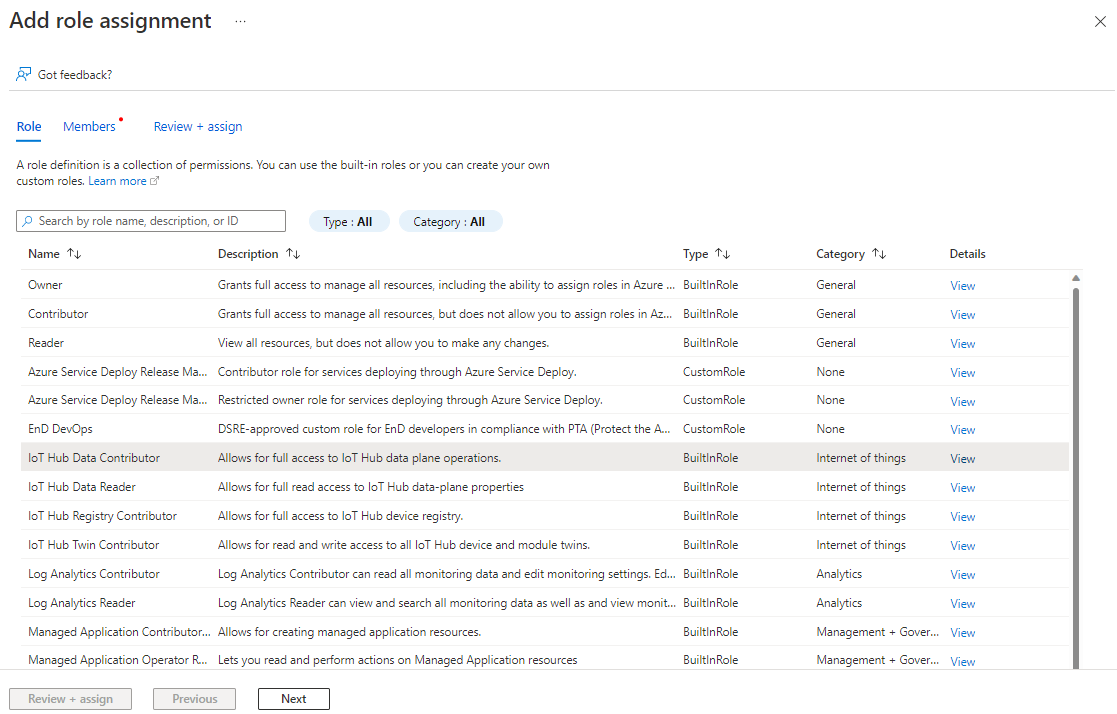
On the Role tab, select IoT Hub Data Contributor, and then select Next.
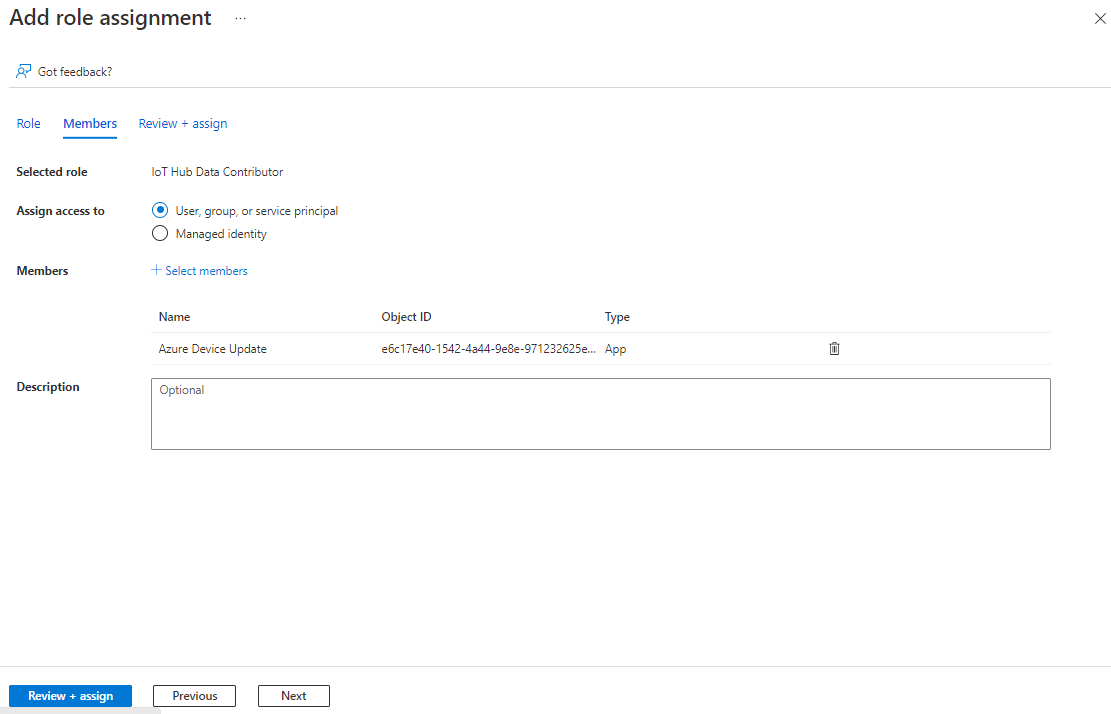
On the Members tab, select User, group, or service principal for Assign access to, and then select Select members.
On the Select members screen, search for and select Azure Device Update, and then select Select.
Select Review + assign and then select Review + assign again.
To validate that you set permissions correctly:
- In the Azure portal, navigate to the IoT hub connected to your Device Update instance.
- Select Access Control (IAM) from the left navigation menu.
- Select Check access.
- Select User, group, or service principal, and search for and select Azure Device Update.
- Verify that the IoT Hub Data Contributor role is listed under Role assignments.